internet overview lecture slides
... request goes to a root nameserver to find out where the appropriate top level domain server (.edu) is, then that server is queried as to where the host (buffalo) is, then the host is queried for the address of the actual computer in question (mediastudy) ...
... request goes to a root nameserver to find out where the appropriate top level domain server (.edu) is, then that server is queried as to where the host (buffalo) is, then the host is queried for the address of the actual computer in question (mediastudy) ...
CS 455: Computer Networks and Data Communication Sample Final Examination Points: 125
... b. An application produces output in terms of 2-Mbyte bursts. Each burst has a 20 milliseconds duration, and bursts occur at a constant interval of 500 milliseconds (i.e., 2 in a second). The application lasts for 2 seconds. It is connected to an 8-Mbps network through a token bucket. Suppose the to ...
... b. An application produces output in terms of 2-Mbyte bursts. Each burst has a 20 milliseconds duration, and bursts occur at a constant interval of 500 milliseconds (i.e., 2 in a second). The application lasts for 2 seconds. It is connected to an 8-Mbps network through a token bucket. Suppose the to ...
Chap 3 Layer 3 Protocol
... Router & local ARP table A typical device contains mapping information pertaining only to devices on its own network Routers build tables that describe all networks connected to them ...
... Router & local ARP table A typical device contains mapping information pertaining only to devices on its own network Routers build tables that describe all networks connected to them ...
CS335 Sample Questions for Exam #2
... 4.) What is the MTU and what does it have to do with datagrams? Answer: MTU is the Maximum Transmission Unit. It is the maximum size for data link layer frames. When a datagram will not fit inside a single frame, it must be fragmented (divided into smaller packets). 5.) If a datagram is fragmented ...
... 4.) What is the MTU and what does it have to do with datagrams? Answer: MTU is the Maximum Transmission Unit. It is the maximum size for data link layer frames. When a datagram will not fit inside a single frame, it must be fragmented (divided into smaller packets). 5.) If a datagram is fragmented ...
ILAFID+ (Live Fiber Monitoring)
... It monitors the link and acknowledges immediately through Sensor Traps the Dry Contacts or TTL level digital outputs as well as by e-mail the network supervisor for any optical power variation in the network caused at the physical layer of the installed infrastructure (e.g. cable breakage, faulty pa ...
... It monitors the link and acknowledges immediately through Sensor Traps the Dry Contacts or TTL level digital outputs as well as by e-mail the network supervisor for any optical power variation in the network caused at the physical layer of the installed infrastructure (e.g. cable breakage, faulty pa ...
LAN BASICS
... D-LinkAir DWL-650 PC Card Type-II 11Mbps Wireless LAN Adapter The D-Link DWL-650 is an IEEE 802.11b compliant PC Card Type-II 11Mbps wireless LAN adapter. The DWL-650 will operate in 2.4 GHz Direct Sequence Spread Spectrum (DSSS) for wireless networks in the home or office environment. It is designe ...
... D-LinkAir DWL-650 PC Card Type-II 11Mbps Wireless LAN Adapter The D-Link DWL-650 is an IEEE 802.11b compliant PC Card Type-II 11Mbps wireless LAN adapter. The DWL-650 will operate in 2.4 GHz Direct Sequence Spread Spectrum (DSSS) for wireless networks in the home or office environment. It is designe ...
Slide - Computer Science
... Node places message including destination address on bus. This message is received by all other nodes All nodes check address to see if message is for them. • Nodes who are not addressed discard message ...
... Node places message including destination address on bus. This message is received by all other nodes All nodes check address to see if message is for them. • Nodes who are not addressed discard message ...
End of module
... D-LinkAir DWL-650 PC Card Type-II 11Mbps Wireless LAN Adapter The D-Link DWL-650 is an IEEE 802.11b compliant PC Card Type-II 11Mbps wireless LAN adapter. The DWL-650 will operate in 2.4 GHz Direct Sequence Spread Spectrum (DSSS) for wireless networks in the home or office environment. It is designe ...
... D-LinkAir DWL-650 PC Card Type-II 11Mbps Wireless LAN Adapter The D-Link DWL-650 is an IEEE 802.11b compliant PC Card Type-II 11Mbps wireless LAN adapter. The DWL-650 will operate in 2.4 GHz Direct Sequence Spread Spectrum (DSSS) for wireless networks in the home or office environment. It is designe ...
Chapter 1 An Introduction to Networking
... the network (centralized security model) • Client/server network: uses a server to enable clients to share data, data storage space, and devices • To function as a server, a computer must be running a network operating system (NOS) • Most of the concepts on the Network+ exam pertain to client/server ...
... the network (centralized security model) • Client/server network: uses a server to enable clients to share data, data storage space, and devices • To function as a server, a computer must be running a network operating system (NOS) • Most of the concepts on the Network+ exam pertain to client/server ...
Slide 1
... source and a destination; synchronize data transfer. • Detect and handle end-to-end transmission errors; alter transmission rate when too much congestion is encountered. ...
... source and a destination; synchronize data transfer. • Detect and handle end-to-end transmission errors; alter transmission rate when too much congestion is encountered. ...
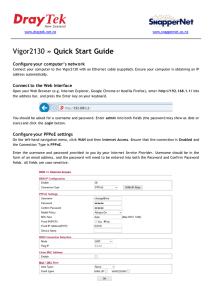
Vigor2130 » Quick Start Guide
... Configure your PPPoE settings On the left-hand navigation menu, click WAN and then Internet Access. Ensure that the connection is Enabled and the Connection Type is PPPoE. Enter the username and password provided to you by your Internet Service Provider. Username should be in the form of an email ad ...
... Configure your PPPoE settings On the left-hand navigation menu, click WAN and then Internet Access. Ensure that the connection is Enabled and the Connection Type is PPPoE. Enter the username and password provided to you by your Internet Service Provider. Username should be in the form of an email ad ...
Accessing Oakton`s Wireless Network
... including damage to computers resulting from software/hardware installation or Internet use. Please make sure that your computer is configured appropriately to prevent other users on the wireless network from accessing your laptop’s hard drive and files. Disk sharing should be turned off. Wireless n ...
... including damage to computers resulting from software/hardware installation or Internet use. Please make sure that your computer is configured appropriately to prevent other users on the wireless network from accessing your laptop’s hard drive and files. Disk sharing should be turned off. Wireless n ...
Slide 1
... • IP address and Port Number: IP address is a 32-bit quantity that uniquely identifies the host. Port number identifies the type of ...
... • IP address and Port Number: IP address is a 32-bit quantity that uniquely identifies the host. Port number identifies the type of ...
Chapter 5
... Hardware type: 1 for Ethernet Protocol type: 080016 for IP addresses ... Sender Hardware Address (6 octets), IP (4 octets) Target Hardware Address (6 octets), IP (4 octets) ...
... Hardware type: 1 for Ethernet Protocol type: 080016 for IP addresses ... Sender Hardware Address (6 octets), IP (4 octets) Target Hardware Address (6 octets), IP (4 octets) ...
Suraj September 14, 2013 The Genius Hour: Day 1/2 Hackers: a
... There are many different types of firewalls depending on where the communications is taking place or where it is intercepted Network Layer Firewalls/ Packet filters - allow packets to only go through if it meets it meets the established rule set. The firewall administrator may default or define the ...
... There are many different types of firewalls depending on where the communications is taking place or where it is intercepted Network Layer Firewalls/ Packet filters - allow packets to only go through if it meets it meets the established rule set. The firewall administrator may default or define the ...
TCPdump
... Window: the number of byte of receive buffer space Urg: indicates there is “urgent” data in the packet Options: tcp options enclosed in angle brackets ...
... Window: the number of byte of receive buffer space Urg: indicates there is “urgent” data in the packet Options: tcp options enclosed in angle brackets ...
Comp 100 Lecture Notes Chapter 7
... Wireless support – 253 devices – traffic limitations Wired support – 4 Ethernet ports Apple Airport Router – 50 wireless connections, 3 Ethernet wired ports (gigabit) ...
... Wireless support – 253 devices – traffic limitations Wired support – 4 Ethernet ports Apple Airport Router – 50 wireless connections, 3 Ethernet wired ports (gigabit) ...
Document
... As each packet is received at a host, it is examined to see if it needs to be processed or discarded. ...
... As each packet is received at a host, it is examined to see if it needs to be processed or discarded. ...
Home Networking
... Network Address Translation For packets crossing the router (in either direction) Router replaces local network IP address with ISP address Remembers the Internet destination (or source) Pairs that with the local network host for future packets ...
... Network Address Translation For packets crossing the router (in either direction) Router replaces local network IP address with ISP address Remembers the Internet destination (or source) Pairs that with the local network host for future packets ...
lecture_1
... Network Programming • Network allows arbitrary applications to communicate • Programmer does not need to understand network technologies • Network facilities accessed through an Application Program Interface ...
... Network Programming • Network allows arbitrary applications to communicate • Programmer does not need to understand network technologies • Network facilities accessed through an Application Program Interface ...
Interconnection networks 2, clusters
... • Key to protocol families is that communication occurs logically at the same level of the protocol, called peer-to-peer, but is implemented via services at the lower level • Danger is each level increases latency if implemented as hierarchy (e.g., multiple check sums) ...
... • Key to protocol families is that communication occurs logically at the same level of the protocol, called peer-to-peer, but is implemented via services at the lower level • Danger is each level increases latency if implemented as hierarchy (e.g., multiple check sums) ...
Intro to the Class
... The portquery tool is used to find the ports and services open at an IP address Available from Microsoft Command line or GUI tool ...
... The portquery tool is used to find the ports and services open at an IP address Available from Microsoft Command line or GUI tool ...
PPT
... any other form of network • The reason LANs are so popular is due to the principle of locality of reference – physical locality of reference - computers more likely to communicate with those nearby – temporal locality of reference - computer is more likely to communicate with the same computers repe ...
... any other form of network • The reason LANs are so popular is due to the principle of locality of reference – physical locality of reference - computers more likely to communicate with those nearby – temporal locality of reference - computer is more likely to communicate with the same computers repe ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.