A Performance Comparision of Multi
... Physical model – Attenuation of radio waves (free propagation and two-ray ground reflection model) Data link layer model – IEEE 802.11 MAC Address Resolution Protocol (ARP) model – IP address resolution Packet buffering in each node – 50 packet queue size in network interface. Additional 50 by routi ...
... Physical model – Attenuation of radio waves (free propagation and two-ray ground reflection model) Data link layer model – IEEE 802.11 MAC Address Resolution Protocol (ARP) model – IP address resolution Packet buffering in each node – 50 packet queue size in network interface. Additional 50 by routi ...
Power-Point
... data If the medium is quiet the node transmits else the node waits till the medium is quiet Nodes listen while transmitting data, therefore If two nodes try to transmit simultaneously a collision occurs and both nodes release the wire and wait a random amount of time before trying again Random time ...
... data If the medium is quiet the node transmits else the node waits till the medium is quiet Nodes listen while transmitting data, therefore If two nodes try to transmit simultaneously a collision occurs and both nodes release the wire and wait a random amount of time before trying again Random time ...
NHA-project
... device. Clicking a device icon will pop an information box containing its IP, name and level. Also, the box will present information about each device port such as speed, bandwidth (half or full), etc. ...
... device. Clicking a device icon will pop an information box containing its IP, name and level. Also, the box will present information about each device port such as speed, bandwidth (half or full), etc. ...
Quick Instruction Guide for Setting Up Remote Access
... Comcast is 10.1.10.1. Customer will need user/pass code info. It could be a default if not changed. Example: User: admin Pass: password. ...
... Comcast is 10.1.10.1. Customer will need user/pass code info. It could be a default if not changed. Example: User: admin Pass: password. ...
Week_Five_Network
... A check sum is created at the source computer and included in the packet. The check sum value is computed from data packet to check its integrity. Through integrity, we mean a check on whether the data received is error free or not. This is because while traveling on network a data packet can become ...
... A check sum is created at the source computer and included in the packet. The check sum value is computed from data packet to check its integrity. Through integrity, we mean a check on whether the data received is error free or not. This is because while traveling on network a data packet can become ...
Chapter 6 slides, Computer Networking, 3rd edition
... ARP: Address Resolution Protocol Question: how to determine MAC address of B knowing B’s IP address? ...
... ARP: Address Resolution Protocol Question: how to determine MAC address of B knowing B’s IP address? ...
slides - network systems lab @ sfu
... router i will return packets to sender sender times interval between transmission and reply. ...
... router i will return packets to sender sender times interval between transmission and reply. ...
Fastpass
... • Algorithm: arbiter greedily allocates a pair if allocating the pair does not violate bandwidth constraints. When it finishes processing all demands, it has a maximal matching, a matching in which none of the unallocated demands can be allocated while maintaining the bandwidth constraints. ...
... • Algorithm: arbiter greedily allocates a pair if allocating the pair does not violate bandwidth constraints. When it finishes processing all demands, it has a maximal matching, a matching in which none of the unallocated demands can be allocated while maintaining the bandwidth constraints. ...
Syllabi-Fall 2010 - Computer Science
... work must be neat and legible. Illegible or poorly formatted work receives no credit. The instructor reserves the right to define what is or is not legible or easily read. Exercises involving coding should contain the following files: well-documented source code for each module; an input file that y ...
... work must be neat and legible. Illegible or poorly formatted work receives no credit. The instructor reserves the right to define what is or is not legible or easily read. Exercises involving coding should contain the following files: well-documented source code for each module; an input file that y ...
d6828939f80d9f863813..
... Monitoring SQL 2012 Database back with Symantec Backup Exec 2012 and Sync Back software and DR Site also. Regularly check health checkup, performance, event logs and Backup of all Servers and firewalls and SQL Data backup and restore it in Test Environment. Support & help to implement Microsoft Dyna ...
... Monitoring SQL 2012 Database back with Symantec Backup Exec 2012 and Sync Back software and DR Site also. Regularly check health checkup, performance, event logs and Backup of all Servers and firewalls and SQL Data backup and restore it in Test Environment. Support & help to implement Microsoft Dyna ...
Reliable, Low Power Wireless Sensor Networks for the Internet of
... forces: the proven low power, highly reliable performance of time-synchronized mesh networks, and the ongoing IP standards efforts for seamless integration into the Internet. Together these forces will drive relatively small, low power sensors that communicate reliably and are IP-enabled. Wireless S ...
... forces: the proven low power, highly reliable performance of time-synchronized mesh networks, and the ongoing IP standards efforts for seamless integration into the Internet. Together these forces will drive relatively small, low power sensors that communicate reliably and are IP-enabled. Wireless S ...
Quality of Service in the Internet QoS Parameters
... • Necessary: establish a path through the network and reserve fixed amounts of network capacity, buffer capacity and CPU time with the routers. • Standardized by the IETF as Resource Reservation Protocol, RSVP RSVP is not a routing protocol, but only an “addition” to such one. A description of the r ...
... • Necessary: establish a path through the network and reserve fixed amounts of network capacity, buffer capacity and CPU time with the routers. • Standardized by the IETF as Resource Reservation Protocol, RSVP RSVP is not a routing protocol, but only an “addition” to such one. A description of the r ...
Slide 1
... Attackers flood the victim’s system with many SYN packets, using spoofed non-existing source addresses ...
... Attackers flood the victim’s system with many SYN packets, using spoofed non-existing source addresses ...
installation manual
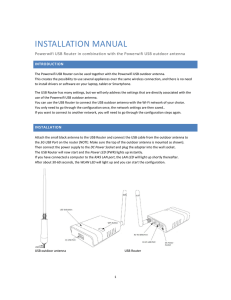
... configuration you should not enter a password, a username and password should be provided afterwards at a special Hotspot login page where you should be automatically redirected when launching a browser. Depending on the Hotspot settings you might need an extra password for every additional device. ...
... configuration you should not enter a password, a username and password should be provided afterwards at a special Hotspot login page where you should be automatically redirected when launching a browser. Depending on the Hotspot settings you might need an extra password for every additional device. ...
The Network Layer
... determine this delay is to send over the line a special ECHO packet that the other side is required to send back immediately. By measuring the round-trip time and dividing it by two, the sending router can get a reasonable estimate of the delay. An interesting issue is whether to take the load into ...
... determine this delay is to send over the line a special ECHO packet that the other side is required to send back immediately. By measuring the round-trip time and dividing it by two, the sending router can get a reasonable estimate of the delay. An interesting issue is whether to take the load into ...
Judul
... • The concept of layers is used to describe communication from one computer to another. • The OSI and TCP/IP models have layers that explain how data is communicated from one computer to another. • The models differ in the number and function of the layers. • However, each model can be used to help ...
... • The concept of layers is used to describe communication from one computer to another. • The OSI and TCP/IP models have layers that explain how data is communicated from one computer to another. • The models differ in the number and function of the layers. • However, each model can be used to help ...
Slide 1
... Wireless Packet Sniffing When in monitor mode a card can capture frames without first being associated with an AP Before Vista the Microsoft Windows Network Driver Interface Specification (NDIS) not support monitor mode so only data frames displayed Later versions of Windows (Vista and 7) lim ...
... Wireless Packet Sniffing When in monitor mode a card can capture frames without first being associated with an AP Before Vista the Microsoft Windows Network Driver Interface Specification (NDIS) not support monitor mode so only data frames displayed Later versions of Windows (Vista and 7) lim ...
Prince Mohammad Bin Fahd University Network Management
... through data DSP service providers licensed by the communications and information technology Commission. Or it can be defined as the company that provides its customers with access to the Internet. And associated Internet service provider to its customers using a data transmission technology appropr ...
... through data DSP service providers licensed by the communications and information technology Commission. Or it can be defined as the company that provides its customers with access to the Internet. And associated Internet service provider to its customers using a data transmission technology appropr ...
networks: communicating and sharing resources
... networks tend to slow down with heavy use, however, and keeping track of all the shared files and peripherals quickly becomes confusing. For this reason, peer-to-peer LANs are best used for simple networks connecting no more than 10 computers. The typical corporate LAN is a client/server network, wh ...
... networks tend to slow down with heavy use, however, and keeping track of all the shared files and peripherals quickly becomes confusing. For this reason, peer-to-peer LANs are best used for simple networks connecting no more than 10 computers. The typical corporate LAN is a client/server network, wh ...
CH3-MPLS-Multiprotocol
... network protocol. It was originally developed in the late 1990s to provide faster packet forwarding for IP routers (see RFC 3031). Since then its capabilities have expanded massively, for example to support service creation (VPNs), traffic engineering, network convergence, and increased resiliency. ...
... network protocol. It was originally developed in the late 1990s to provide faster packet forwarding for IP routers (see RFC 3031). Since then its capabilities have expanded massively, for example to support service creation (VPNs), traffic engineering, network convergence, and increased resiliency. ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.