* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Prince Mohammad Bin Fahd University Network Management
Deep packet inspection wikipedia , lookup
Net neutrality law wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Policies promoting wireless broadband in the United States wikipedia , lookup
Computer security wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Distributed firewall wikipedia , lookup
Computer network wikipedia , lookup
Wireless security wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
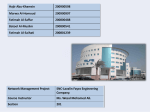
Prince Mohammad Bin Fahd University Network Management Project SNC-Lavalin Fayez Engineering Company Course Instructor: Ms. Wesal Mohamed Ali Course information: Network Management ITAP2431 Section: 201 Group members: Hajir Abu-Khamsin 200900598 Fatima Al-saffar 200800488 Batool Al-Muslim 200800541 Fatima Al-sehaty Marwa Al-Humood Introduction: On Sunday 2/12/2012 we went to SNC-Lavalin Fayez Engineering Company to write a report about the company’s infrastructure and network. SNV-Lavlin is one of the leading engineering and construction groups in the world and has offices across Canada and in other 40 countries around the world. SNC-Lavalin Fayez Engineering Company is engineering consultancy joint venture between SNC-Lavin and its local partners, recently the industrial division of Zuhair Fayez Partnered with the company. SLFE was formed partly in response to Saudi Aramco’s General Engineering service Plus initiative which aimed to develop engineering capabilities in the kingdom. Under this initiative SLFE will be invite to bit on front-end engineering and select detailed engineering services constricts to support the implementation of Saudi Aramco’s capital program. Projects will include both on and offshore oil and gas production and processing facilities infrastructure projects, as well as refining and petrochemical facilities. Network infrastructure: The company as mentioned above provides different consulting and designs to different companies such as Aramco and SATROP, thus it shares its servers with them. The company has eight floors and in total contains 600 computers connected in server-client connection. All the computers of each floor are connected together using switches then the floors are connected together using primary and secondary fiber optic cables This difference between secondary and primary fiber optics is that the first one is the main cable they relay on and the other one acts as a back up. A UTP/ copper caber link is also used in this network this cable is short for unshielded copper cable link that is a cable made of pairs of copper wires that are twisted around each other it is commonly used for the purposes of canceling out electromagnetic interference from external sources. UTP cables are found in many Ethernet networks and telephone systems. The switches also included access points to the Nortel WLAN. We’ve have been talking previously about Nortel access points this is because in the company they use Nortel Ethernet for the wireless communication in (WLAN), this technology is discussed in details later on in this report. All of the 600 computers are connected together to the network and internet servers in the main floor using also the primary and secondary optics cables. They also have an IP Tel switch in the main communication room which is connected to all the servers, floor switches, Juniber firewall and the secure router using UTP/copper cable link. The IP Telephony uses the internet protocol (IP) to transmit voice or fax traffic over privet or public data network, to ensure high quality voice communications IP Tel also called voice over IP requires sufficient bandwidth to ensure transmission delay is minimized. IP Tell capability can provide significant cost saving to businesses with branch locations by eliminating the need for long distance charges or by reducing the number of local access line required by the business. It can be integrated into other solutions like unified messaging to provide enhanced saving and service levels to companies using the internet for commerce or service application. Thus, this technology brings a lot of benefits to AL-Fayez Company since they have offshore servers and are connected with many different networks in the region. We must also distinguish the difference between a switch and a router although many might think they do the same job but they are different. A network switch is a small hardware device that joins multiple computers together within one local area network (LAN). Technically, network switches operate at layer two (Data Link Layer) of the OSI model. On the other hand, a router is a device that forwards data packets along networks. A router is connected to at least two networks, commonly two LANs or WANs or a LAN and its ISPs network. Routers are located at gateways, the places where two or more networks connect. AL-fayez company network is connected to another two networks in each network we can see that all of the floors commuters are connected using switch. SATROP in specific uses primary and secondary fiber optic cables to link between the switches they are connected to a core switch, a secure router and a Juniber firewall those three components are connected together using UTP/Copper cable link. As for Saudi Aramco network the switches are connected together using only primary fiber link they are connected to secure router and a switch using UTP/Copper cable link. Internet Service Providers (ISPs): It can be defined as the connecting customers, whether companies or individuals-Internet through data DSP service providers licensed by the communications and information technology Commission. Or it can be defined as the company that provides its customers with access to the Internet. And associated Internet service provider to its customers using a data transmission technology appropriate for delivering Internet data packages, such as dial-up, digital subscriber line (DSL), cable modem, wireless, ad hoc link high speed Internet service provider may provide e-mail accounts to users which allow them to communicate with each other by sending and receiving electronic messages through server (server) ISP (as part of the e-mail service is usually not save the user's ISP and e-mail client software package, developed either internally or Through an external contract arrangement). Internet service providers can offer us other services such as remote data storage on behalf of their customers, as well as other services unique to each ISP. Some examples of Internet service providers (ISPs) in our country KSA: Company name City Website Sahara network commercial Al-Dammam www.sahara.com.sa Saudi net Al-Riyadh www.saudi.net.sa Etihad Etisalat (Mobile) Al-Riyadh www.mobily.com.sa Island Foundation How to choose an ISP: One of the most difficult questions facing the Internet user: Is there an appropriate service provider for me and for my needs? There are a number of criteria that are building them chose Internet service provider both at the level of the home user interested get a link for Web browsing and e-mail or user at the level of companies or organizations that have their own websites and may run some online business, the most important of these criteria the number of different Internet connections required, prices and other variables. There are currently 20 companies with Kingdom of Internet services, and that number is expected to increase over the coming years. Ways to connect to the Internet: To connect computers to the Internet must connect this computer to another computer connected to the Internet permanently as a main institution or college computer service provider contact your ISP, and can connect to the Internet in two ways: 1. Technical Dial-up By direct contact Direct-Connection. 2. Through wireless technology All the methods above required an Internet Service Providers to connect to the Internet, without these services we cannot browse the Internet. Servers: The company has three email servers; one is inside the local network of the company which is connected to the Juniper firewall. The other is in Jeddah which is connected to the company through VPN connection with an additional STC connection as a backup; the third server is located in Jakarta also through VPN connection. A virtual private network (VPN) extends a private network and the resources contained in the network across public networks like the Internet. It enables a host computer to send and receive data across shared or public networks as if it were a private network with all the functionality, security and management policies of the private network. This is done by establishing a virtual point-to-point connection through the use of dedicated connections, encryption, or a combination of the two. The VPN connection across the Internet is technically a wide area network (WAN) link between the sites but appears to the user as a private network link. In the company they have other different servers they have different types of servers which are HP DL 380, HP DL 380DC 1 and HP DL 380 Cluster. The HP DL 380 is Exchanger Server. It is a mail server, calendaring software and contact manager developed by Microsoft. It is a server program that runs on Windows Server and is part of the Microsoft Servers line of products. The HP DL 380 DC 1 called Domain controller, it is a server on a Microsoft Windows that is responsible for allowing host access to Windows domain resources. The cluster alias acts as a single network node identifier for an OpenVMS Cluster system. Computers in the cluster can use the alias for communications with other computers in a DEC net network. Note that it is possible for nodes running DEC net for OpenVMS to have a unique and separate cluster alias from nodes running DEC net--Plus. In addition, clusters running DEC net--Plus can have one cluster alias for VAX, one for Alpha, and another for both. The protocols that company used are LAN and WAN. LAN is a local area network, which is computer network that interconnects computers in a limited area.WAN is a wide area network, which is a network covers abroad area. Backbone Backbone interconnects various pieces of network, providing a path for the exchange of information between different LANs. A backbone can tie together diverse networks in the same building, in different buildings or over wide areas. Normally, the backbone's capacity is greater than the networks connected to it. It uses high speed circuits to connect LANs and provide connections to other backbones, MANs and WANs. The company use collapsed Ethernet backbones. The advantage of collapsed Backbone is improved performance and it is simpler more easily managed network. Collapsed Backbone: The Ethernet is a type of architecture used in many local area networks (LANs). It sets of protocols which serves the physical and data link layers. It utilizes a linear bus or star topology. Also, it served as the basis for the IEEE 802.3 standard. Ethernet was commercially introduced in 1980. It has largely replaced competing wired LAN technologies. Ethernet networking is the most common physical networking standard. It supports TCP/IP networking seamlessly, and provides an inexpensive, simple, high bandwidth method for interconnection of local computers. The Ethernet standards comprise several wiring and signaling variants of the OSI physical layer in use with Ethernet. Systems communicating over Ethernet divide a stream of data into shorter pieces called frames. Each frame contains source and destination addresses and error checking data so that damaged data can be detected and retransmitted. Ethernet cables known as RJ-45 cables, they are used in computer networking and deliver data between computers on the Internet. Ethernet cables are the major pipeline of your home and office network. Ethernet cables connect network devices such as modems, routers, and adapters. They transmit data using the Ethernet protocol. Networking devices feed Internet data through the Ethernet cables which connect to a network port on your computer. In addition, each computer that requires a high speed Internet connection must be connected to an Ethernet cable. Furthermore, if you set up a wireless router at home, an Ethernet cable is still needed to feed the wireless antennas an Internet connection. There are three ways that make the data Travels over the Ethernet Cable. First, full duplex which the data can travels both directions at once. Second, half duplex which the data can only travels one direction at any instant. This is slower than full duplex. Third, Auto-negociation is when the network devices figure out whether both on either end of an Ethernet cable are full duplex. WLAN: WLAN stands for wireless LANs, usually companies do not use wired LANS actually 90% of company’s uses wireless LANS. A wireless local-area network (LAN) uses radio waves to connect devices such as laptops to the Internet and to your business network and its applications. When you connect a laptop to a WiFi hotspot at a cafe or other public place, you're connecting to that business's wireless network. In the past, some believed wired networks were faster and more secure than wireless networks. But continual enhancements to wireless networking standards and technologies have eroded those speed and security differences. The company they use Nortel wireless technology, Nortel Networks Corporation, formerly known as Northern Telecom Limited and sometimes known simply as Nortel, was a multinational telecommunications equipment manufacturer headquartered in Mississauga, Ontario, Canada. It was founded in Montreal. A wireless network can open up a whole new world of opportunities and extend access to information for their company well beyond the traditional confines of a PC tethered to a power outlet and Ethernet connection. Benefits: - Convenience. Access your network resources from any location within your wireless network's coverage area or from any WiFi hotspot. - Mobility, you’re no longer tied to your desk, as you were with a wired connection. You and your employees can go online in conference room meetings, for example. - Productivity, Wireless access to the Internet and to your company's key applications and resources helps your staff get the job done and encourages collaboration. - Easy setup, You don't have to string cables, so installation can be quick and cost-effective. - Expandable, You can easily expand wireless networks with existing equipment, while a wired network might require additional wiring. Components of WLAN: 1- Access point: (APs or WAPs) are specially configured nodes on wireless local area networks (WLANs). Access points act as a central transmitter and receiver of WLAN radio signals. 2- Network Interface Cards: NIC, an expansion board you insert into a computer so the computer can be connected to a network. Most NICs are designed for a particular type of network, protocol, and media, although some can serve multiple networks. 3- Core switch: that is connecter wirly to the access point to provide the network WLAN in the company: In Alfayez Company they use WLANs to connect between the floors and the core switch. In each floor we have two access points so in total of twelve access points are installed all of these access points are connected to the core switch. The access point and the core switch are from Nortel Ethernet Company. Network topology A network topology describes the arrangement of systems on a computer network. It defines how the computers, or nodes, within the network are arranged and connected to each other. Network topologies are categorized into the following basic types: bus star tree mesh Moreover, topology can be physical or logical. Physical Topology is the physical layout of nodes, workstations and cables in the network whereas logical topology is the way information flows between different components. In general, physical topology relates to a core network while logical topology relates to basic network. The company told us that they used a bus networks topology, which is the simplest way that uses a common backbone to connect all devices. A bus topology connects each computer (nodes) to a single segment trunk (a communication line, typically coax cable that is referred to as the 'bus'. The signal travels from one end of the bus to the other. This allows only one device to transmit at a time but may have problems when two clients want to transmit at the same time on the same bus. However, bus networks work best with a limited number of devices. If more than a few dozen computers are added to a network bus, performance problems will likely result. In addition, if the backbone cable fails, the entire network effectively becomes unusable. The company used bus networks topology for the following advantages: Bus is easy to use and understand and inexpensive simple network. It is easy to extend a network by adding cable with a repeater that boosts the signal and allows it to travel a longer distance. Allows relatively high rate of data transmitting Well suited for temporary networks that must be set up in a hurry Failure of one of the station does not affect others Nevertheless, bus networks topology have the following disadvantages that may affect on the performance of the company: A bus topology becomes slow by heavy network traffic with a lot of computer because networks do not coordinate with each other to reserve times to transmit. It is difficult to troubleshoot a bus because a cable break or loose connector will cause reflections and bring down the whole network. It requires a network to detect when two nodes are transmitting at the same time Its maintenance cost may be higher in the long run and the performance degrade as additional computers are added. Although the company told us that they are using bus topology, we are recommended that they use star topology since they use collapsed backbone and it is better to use star topology with collapsed backbone. In the star topology there is a central connection point called the hub, which is a computer hub or sometimes just a switch. In a Star Network, the best advantage is when there is a failure in cable then only one computer might get affected and not the entire network. In a Star Network, the entire network is dependent on the hub so if the entire network is not working then there could be a problem with the hub. This feature makes it easy to troubleshoot by offering a single point for error connection and at the same time, the dependency is also very high on that single point. Backup Ba cking-up is a crucial process that each company must do in order to have a fail-safe, for when the inevitable happens. The main purpose of back up is to make copies of particular data in order to use those copies for restoring the information in case of equipment failure occurs or other catastrophe (a data loss event due to deletion, corruption, theft, viruses etc.). Each company has its own approach in executing the backup but there are four common backup types implemented and generally used in most business company which are; full backup, differential backup, incremental backup and mirror backup. We approach the company and they said that the company has its own Server Backup Procedure Every business day, data backup must be performed on each server These are: Daily backup (ex. Monday to Thursday for most offices) At the end of each business day, differential or incremental backups must be performed. These backups will be retained for a period of 14 days. The company used these types as a daily backup because both differential and incremental backups are "smart" backups that save time and disk space by only backing up changed files. However, they differ significantly in how they do it, and how useful the result is. Weekly backup (ex. Friday for most offices) the last business day of the week, a full backup of all servers must be performed. These backups will be retained for a period of 15 weeks. Quarterly backup: The company said that on the first weekend of April, July and October, two full backups must be performed. The first full backup (weekly) will be retained for a period of 15 weeks. The second full backup, which is the “Quarterly”, will be retained for at least one year. Yearly backup: The company said that on the first weekend of January; two full backups must be performed. The first full backup, which is (weekly backup), will be retained for a period of 15 weeks. The second full backup, which is the (yearly backup), will be retained for at least one year. Backup tape storage The IT administrator said,” If it is not possible to store the tapes offsite, they should at least be kept in a secured place, other than the servers’ room.” In computing, off-site data protection is the strategy of sending critical data out of the main location (off the main site) as part of a disaster recovery plan. Data is usually transported off-site using removable storage media such as magnetic tape or optical storage.” The company does backup the system on daily base and D 2 D (disc to disc) backup. With D2D, a computer hard disk is backed up to another hard disk rather than to a tape or floppy. D2D is often confused with virtual tape, but differs in that it enables multiple backup and recovery operations to simultaneously access the disk directly by using a true file system. Network strength and weaknesses: As for every network there is always strength and weaknesses to them and here is a list of strength and weaknesses that we have found in the company. Strength: 1- The type of cabling used in this company is extraordinary. It Is very clear that they spent a lot of money on it since they use primary and secondary fiber optic cables to connect between the floors and this is not usual in companies to use fiber optics to connect between floors. They also used UTP/C cables which are also a very high quality cables. They didn’t use any cheap cables such as twisted pair cables which defiantly a plus to the company. 2- The company uses WLAN instead of usual wired LAN which is Of course a benefit to the company in terms of speed, convenient and expandability. 3- Security in the company is noticeably high since they use a very good back up system and they use juniper switch and firewalls which provide secure network to the company. 4- The company doesn’t use hubs which are poor kind of connectivity devices instead they use access points. 5- They use also Cisco backbone system and Nortel Ethernet technology which are very known companies and are huge competitors in the market. Weakness: 1- Although using fiber optic cables and UTP/C cables is a strength to the company it can also be some kind of weakness since it is highly expensive and also if one of them got corrupted or needed a replacement it surely going to be expansive. 2- The company only uses Bus topology which is a very huge disadvantage to the company it would’ve been better to use another types of topology and this was discussed in details in the topology part of the report. 3- The servers are stored in rooms that has windows and maybe it would be better to not use windows to prevent sun of rain to come in the servers room and it would provide better conditions to it. Network cost: The company spended ten million Saudi Reyals to install the network in the company. Data transmission Digital transmission is the sending of information over a physical communications media in the form of digital signals. (a digital bit stream) over a point-to-point or point-to-multipoint communication channel. Data transmission is a subset of the field of data communications, which also includes computer networking or computer communication applications and networking protocols. (erroneously decoded data from a transmitting station to a plurality of receiving stations is performed, where retransmitted data is sent via at least one communication channel, which is different from the one used for the initially transmitted data). Examples of such channels are copper wires, optical fibers, wireless communication channels, and storage media. The data are represented as an electromagnetic signal, such as an electrical voltage, radio wave, microwave, or infrared signal. Is the company they rely on fiber optic cables and UTP/C cables for transmitting data also transmit data wirelessly through the Ethernet. Types of Applications In SLFE Company they rely on Microsoft SQL server and Microsoft Dynamics GP for applications. Microsoft SQL Server, According to Internet market research and strategic consulting, continues as the database used by the company. It is a standard programming language for retrieving information from and updating databases and enables user to select, insert, update, and delete data from database. It is a standard language that all commercial databases .The IT manager in the company consultant to have a hands-on experience with SQL (as well as with any other Information Technologies). As for Microsoft Dynamics GP (formerly Great Plains) it is software that delivers comprehensive out-of-the-box business management functionality, from operations management and financial management to human resource management and manufacturing. It connects the many moving parts of them organization, giving them better visibility into and control over what’s going on them business. That increasing margins and improving them cash flow. Microsoft Dynamics GP helps them to grow and manage them distribution business better through: improve operational efficiency, save time, and reduce costs by transforming time-consuming manual processes into automated tasks that can be executed quickly and accurately. Also improved Visibility and Stronger Customer Service. Communication network wireless They use a wireless Ethernet bridge which converts a wired Ethernet device for use on a wireless computer network. Wireless Ethernet bridges and USB adapters are both sometimes called wireless media adapters as they enable devices for WiFi utilizing Ethernet or USB physical media and they use 1GB of Ethernet .The company they use Nortel wireless technology, Nortel Networks Corporation, formerly known as Northern Telecom Limited and sometimes known simply as Nortel, was a multinational telecommunications equipment manufacturer headquartered in Mississauga, Ontario, Canada. It was founded in Montreal. A wireless network can open up a whole new world of opportunities and extend access to information for their company well beyond the traditional confines of a PC tethered to a power outlet and Ethernet connection. Network security: Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security involves all activities that organizations, enterprises, and institutions undertake to protect the value and ongoing usability of assets and the integrity and continuity of operations. An effective network security strategy requires identifying threats and then choosing the most effective set of tools to combat them. Threats to network security include: Viruses, Trojan horse programs, Vandals, Attacks. Network security helps your company meet mandatory regulatory compliance. Because network security helps protect your customers' data, it reduces the risk of legal action from data theft. Ultimately, network security helps protect a business's reputation, which is one of its most important assets. In AL-fayez Company they have a very good security system where they use a Nortel secure router The Nortel Secure Router 3120 is a powerful modular system that converges routing, security and multimedia traffic forwarding in a single cost-effective platform for enterprises. Delivering fast, secure, reliable and scalable wide area network (WAN) access, the Secure Router 3120 is perfect for enterprises requiring high-speed IP or Internet access. Based on a simple-to-scale architecture, the Secure Router 3120 provides consistent wire-speed throughput even with advanced services enabled. The Secure Router 3120 combines high performance, robust routing and flexible WAN connectivity and is targeted at larger branch and regional enterprise environments. A rich suite of routing services and advanced WAN functionality makes the Secure Router 3120 ideal for high-speed Internet access, private line WAN connectivity, IP Telephony and multimedia, IPsec VPN, stateful firewall or data backup applications. Comprehensive, simple-to-use software tools enable sophisticated access and bandwidth management for dependable communications. They also use Juniper firewall system Juniper is a vendor or manufacturer of Firewall appliances. Juniper also manufactures and sells routers, switches, IDP/IDS devices and SSL-VPN appliances. A firewall is a set of related programs, located at a network gateway server that protects the resources of a private network from users from other networks. (The term also implies the security policy that is used with the programs.) An enterprise with an intranet that allows its workers access to the wider Internet installs a firewall to prevent outsiders from accessing its own private data resources and for controlling what outside resources its own users have access to. Surf control: to monitor internet activity The company use Surf Control to monitor internet activity which offers a total content security solution that combines Web and e-mail filtering technology with the industry's largest, most accurate and relevant content database and adaptive reasoning tools to automate content recognition. Surf Control's Internet monitoring and policy management solutions are flexible, saleable and interoperable to meet the diverse needs of all its markets -- corporate, education, home and OEM. Surf Control offers a choice of platform independent or integrated solutions, and the software can be installed in any network environment. Surf Control Web Filter provides Real-Time Monitoring, Reporting and Analysis, as well as Categorization of URL Content to allow organizations to effectively manage their employees' Internet Usage – Surf Control Web Filter is available as a stand-alone product for Windows NT & Windows 2000, or as an integrated product into Microsoft Proxy Server, Microsoft ISA Server 2000, Novell Border Manager as well as FireWall-1. Surf Control E-mail Filter manages content security of all inbound, outbound and internal email transmissions. Surf Control Email Filter allows for content rule definition in order to implement and enforce an organization's Acceptable Use Policy (AUP). Surf Control solutions Increase Employee Productivity, Increase Network Bandwidth, Reduce Legal Liability, Protect Intellectual Property & Improve Security. Screen shot of the device: Conclusion : SNV-Lavlin is one of the leading engineering and construction groups in the world and has offices across Canada and in other 40 countries around the world. SNC-Lavalin Fayez Engineering Company is engineering consultancy joint venture between SNC-Lavin and its local partners. The company as mentioned above provides different consulting and designs to different companies such as Aramco and SATROP, thus it shares its servers with them. and there is a list of strength and weaknesses that we have found in the company.one of strength that the security in the company is noticeably high since they use a very good back up system and they use juniper switch and firewalls which provide secure network to the company. Also they have good of application that they use such as Microsoft SQL server and Microsoft Dynamics GP for applications.finally SLFE Company will improve the weakness in company .such as will improve to use another types of topology and this was discussed in details in the topology part of the report, The company only uses Bus topology which is a very huge disadvantage to the company. Although they using fiber optic cables and UTP/C cables is a strength to the company it can also be some kind of weakness since it is highly expensive and also if one of them got corrupted or needed a replacement it surely going to be expansive. Sources: - - - - - - - - - Virtual private network - Wikipedia, the free encyclopedia. (n.d.). Wikipedia, the free encyclopedia. Retrieved December 14, 2012, from http://en.wikipedia.org/wiki/Virtual_private_network Bus Topology : Advantages and Disadvantages. (n.d.). I Answer 4 U. Retrieved December 14, 2012, from http://www.ianswer4u.com/2011/05/bus-topologyadvantages-and.html#axzz2EYPQeHYP Backup types. (n.d.). Backup Software - Protect your Data. Retrieved December 14, 2012, from http://www.backup4all.com/kb/backup-types-115.html Mitchell, B. (n.d.). Network Topology - Types of Network Topologies - Bus, Ring and Star. Networking - Computer and Wireless Networking Basics - Home Networks Tutorials. Retrieved December 14, 2012, from http://compnetworking.about.com/od/networkdesign/a/topologies.htm Network Topology Tips :: Lahitech.com. (n.d.). Web Design and Development for Internet and Intranet Websites :: LAHITECH Website. Retrieved December 14, 2012, from http://www.lahitech.com/networktips.asp Mesh Topology: Advantages and Disadvantages. (n.d.). I Answer 4 U. Retrieved December 14, 2012, from http://www.ianswer4u.com/2011/05/mesh-topologyadvantages-and.html#axzz2Ev9nk36u What Is a Wireless Network?: The Basics - Cisco Systems . (n.d.). Cisco Systems, Inc. Retrieved December 14, 2012, from http://www.cisco.com/cisco/web/solutions/small_business/resource_center/a rticles/work_from_anywhere/what_is_a_wireless_network/index.html Oranrigsupak, T. (n.d.). SQL by Theinchai Oranrigsupak. Home Page. Retrieved December 14, 2012, from http://theinchai.tripod.com/SQL.htm Supply Chain Management | Microsoft Dynamics GP (formerly Great Plains). (n.d.). Microsoft Corporation. Retrieved December 14, 2012, from http://www.microsoft.com/en-us/dynamics/erp-gp-overview.aspx Mitchell, B. (n.d.). Wireless Ethernet Bridge. Networking - Computer and Wireless Networking Basics - Home Networks Tutorials. Retrieved December 14, 2012, from http://compnetworking.about.com/od/hardwarenetworkgear/ss/wirelessadap ter_4.htm Point-to-multipoint communication - Wikipedia, the free encyclopedia. (n.d.).Wikipedia, the free encyclopedia. Retrieved December 14, 2012, from http://en.wikipedia.org/wiki/Point-to-multipoint_communication