1 - Binus Repository
... Notes from www.cisco.com • Traffic coming into the router is compared to ACL entries based on the order that the entries occur in the router. • New statements are added to the end of the list. • The router keeps looking until it has a match. • If no matches are found when the router reaches the end ...
... Notes from www.cisco.com • Traffic coming into the router is compared to ACL entries based on the order that the entries occur in the router. • New statements are added to the end of the list. • The router keeps looking until it has a match. • If no matches are found when the router reaches the end ...
03_tcom5272_tcpip
... Static routing means that the network administrator directly assigns the path router are to take to the destination Static routing is most often used with stub networks where only one path exists to the destination ...
... Static routing means that the network administrator directly assigns the path router are to take to the destination Static routing is most often used with stub networks where only one path exists to the destination ...
Packet Switching, ATM, switch Fabric
... Hosts can connect to the network directly or through LANs. ...
... Hosts can connect to the network directly or through LANs. ...
Software-Defined Networks: Incremental Deployment with
... • Automating and radically simplifying computer network management. • Increasingly view hybrid networks. • Transition to an SDN should meet several specific goals: 1. Provide clear and immediate benefits 2. Minimize disruption while establishing confidence 3. Respect budgetary constraints ...
... • Automating and radically simplifying computer network management. • Increasingly view hybrid networks. • Transition to an SDN should meet several specific goals: 1. Provide clear and immediate benefits 2. Minimize disruption while establishing confidence 3. Respect budgetary constraints ...
May 11
... In a internet with heterogeneous networks, MTU restrictions can be a problem Routers fragment or divide a datagram into smaller pieces to meet the MTU ...
... In a internet with heterogeneous networks, MTU restrictions can be a problem Routers fragment or divide a datagram into smaller pieces to meet the MTU ...
Building Survivable Systems based on Intrusion Detection and
... for capturing behaviors of processes and hosts as patterns over sequences of events such as system calls and network packets. Protection against Known and Unknown attacks: by enforcing security-relevant properties, we protect against known and unknown attacks. Enforcement of normal behaviors and ...
... for capturing behaviors of processes and hosts as patterns over sequences of events such as system calls and network packets. Protection against Known and Unknown attacks: by enforcing security-relevant properties, we protect against known and unknown attacks. Enforcement of normal behaviors and ...
Introduction - Wapanucka Public Schools
... considered of educational value in the context of the school setting. Wapanucka Public School has taken reasonable available precautions to restrict access by users to inappropriate material. The district network has blocking and filtering software installed which is designed to prevent access to us ...
... considered of educational value in the context of the school setting. Wapanucka Public School has taken reasonable available precautions to restrict access by users to inappropriate material. The district network has blocking and filtering software installed which is designed to prevent access to us ...
WLI-E – Software User Guide
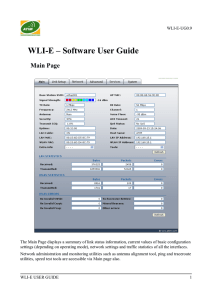
... mode. The represented value coincides with the graphical bar. Use antenna alignment tool to adjust the device antenna to get better link with the wireless device. The antenna of the wireless client has to be adjusted to get the maximum signal strength. Signal Strength is measured in dBm (the Decibel ...
... mode. The represented value coincides with the graphical bar. Use antenna alignment tool to adjust the device antenna to get better link with the wireless device. The antenna of the wireless client has to be adjusted to get the maximum signal strength. Signal Strength is measured in dBm (the Decibel ...
... it is in fact one of the most important steps. In the notification area on the taskbar there should be an icon like this or this if you are connected to the network. If the icon looks like this it means that the computer is not connected to the network. (If no such icons can be found you may still b ...
File - IT Essentials Pc: Hardware/ software
... 6. Explain what is Phishing and give an example: Phishing is where the attacker pretends to represent a legitimate outside organization, such as a bank. 7. How is a virus transferred to another computer? email, file transfers, and instant messaging. 8. Explain how does a virus typically work? The v ...
... 6. Explain what is Phishing and give an example: Phishing is where the attacker pretends to represent a legitimate outside organization, such as a bank. 7. How is a virus transferred to another computer? email, file transfers, and instant messaging. 8. Explain how does a virus typically work? The v ...
Optical Networking Leader Supports IEEE Standard PBB
... portfolio, service providers can construct a single universal optical infrastructure that aggregates both traditional TDM traffic and Ethernet traffic over a tightly integrated ROADM transport layer. Networks designed around packet optical networking platforms and PBB-TE make efficient use of metro ...
... portfolio, service providers can construct a single universal optical infrastructure that aggregates both traditional TDM traffic and Ethernet traffic over a tightly integrated ROADM transport layer. Networks designed around packet optical networking platforms and PBB-TE make efficient use of metro ...
Chap 18 - The University of Tulsa
... 18.4.4 DHCP Address assignment can be done manually or automatically using the Dynamic Host Configuration Protocol (DHCP). DHCP is an application-layer program, using the client-server paradigm, that helps TCP/IP at the network layer. ...
... 18.4.4 DHCP Address assignment can be done manually or automatically using the Dynamic Host Configuration Protocol (DHCP). DHCP is an application-layer program, using the client-server paradigm, that helps TCP/IP at the network layer. ...
Slide 1
... Send packets with limited TTL towards destination Packets will “expire” and cause ICMP error message Source of error message is intermediate hop Repeat with increasing TTL ...
... Send packets with limited TTL towards destination Packets will “expire” and cause ICMP error message Source of error message is intermediate hop Repeat with increasing TTL ...
continued - cgtechlab.us!
... Wide area networks Span larger geographical distances Connect multiple LANs using high-speed communication lines Expand beyond own premises Typically lease data lines from public carrier ...
... Wide area networks Span larger geographical distances Connect multiple LANs using high-speed communication lines Expand beyond own premises Typically lease data lines from public carrier ...
Computer Networks
... • Large businesses usually use a client/server network. • With this system, one powerful computer provides information and management services to the workstation computers, the clients. • In a client/server network, each workstation is a client connected to a central computer called a file server or ...
... • Large businesses usually use a client/server network. • With this system, one powerful computer provides information and management services to the workstation computers, the clients. • In a client/server network, each workstation is a client connected to a central computer called a file server or ...
Security Problems in the TCP/IP Protocol Suite
... Problem: Recursive zone transfer requests to download entire database Solution: Employ “refused” error code for any requests from unidentified servers ...
... Problem: Recursive zone transfer requests to download entire database Solution: Employ “refused” error code for any requests from unidentified servers ...
The Application Layer
... Multiple connections for high throughputs Multiplexing a connection among many session layers for reducing the cost ...
... Multiple connections for high throughputs Multiplexing a connection among many session layers for reducing the cost ...
Networking BASICS
... Summary (continued) • Wireless local area networks (WLANs) are found anywhere a user needs mobility but still must remain connected to a network. The list of components necessary for a WLAN is short. Only wireless network interface cards and access points are needed for communication to take place. ...
... Summary (continued) • Wireless local area networks (WLANs) are found anywhere a user needs mobility but still must remain connected to a network. The list of components necessary for a WLAN is short. Only wireless network interface cards and access points are needed for communication to take place. ...
ITNW 1358 - Network+
... Make-up Exam Policy: You are expected to take all exams on the scheduled days. Make-up exams are NOT guaranteed, but are granted at the discretion of the instructor. If make-up exams are necessary, it is necessary to make arrangements with the instructor PRIOR to exam date. NOTE: There is NO make-up ...
... Make-up Exam Policy: You are expected to take all exams on the scheduled days. Make-up exams are NOT guaranteed, but are granted at the discretion of the instructor. If make-up exams are necessary, it is necessary to make arrangements with the instructor PRIOR to exam date. NOTE: There is NO make-up ...
Chapter 1: Introducing Networks
... Physical: encoding, bit transmission, signal Data Link: frame, MAC address, access method Network: packet, routing, best path Transport: segmentation, connection-oriented vs. connectionless, error-free delivery Session: synchronization, half-duplex/full duplex, communications setup and teardown Pres ...
... Physical: encoding, bit transmission, signal Data Link: frame, MAC address, access method Network: packet, routing, best path Transport: segmentation, connection-oriented vs. connectionless, error-free delivery Session: synchronization, half-duplex/full duplex, communications setup and teardown Pres ...
Overview of TCP/IP reference model
... 5. Transport layer breaks the message (data) into small units so that they are handled more efficiently by the network layer. 6. Transport layer also arrange the packets to be sent, in sequence. ...
... 5. Transport layer breaks the message (data) into small units so that they are handled more efficiently by the network layer. 6. Transport layer also arrange the packets to be sent, in sequence. ...
Integrating Cisco Press Resources into the Academy Classroom
... Step 2 For one router, use a serial DTE cable. The connector on one end of the cable should be connected to one of the router’s serial interfaces. Step 3 For the other router, use a serial DCE cable. The connector on one end of the cable should connect to the second router’s serial interface. Step 4 ...
... Step 2 For one router, use a serial DTE cable. The connector on one end of the cable should be connected to one of the router’s serial interfaces. Step 3 For the other router, use a serial DCE cable. The connector on one end of the cable should connect to the second router’s serial interface. Step 4 ...
Computer Security and Penetration Testing
... network or the private LAN • All hardware adapters on the LAN can view the frame • Every adapter then compares the destination MAC address in the frame with its own MAC address ...
... network or the private LAN • All hardware adapters on the LAN can view the frame • Every adapter then compares the destination MAC address in the frame with its own MAC address ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.