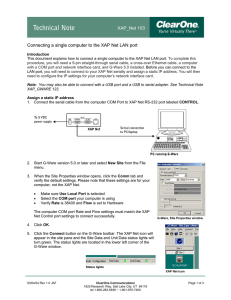
Connecting a Single Computer to the XAP Net LAN Port
... and Unit Data status lights in the lower left corner of the G-Ware window will turn green. To make a crossover Ethernet cable An Ethernet crossover cable is an unshielded twisted pair Category 5 (UTP-CAT 5) network cable. The XAP Net has a 10/100Mbps NIC and can connect at either speed, depending on ...
... and Unit Data status lights in the lower left corner of the G-Ware window will turn green. To make a crossover Ethernet cable An Ethernet crossover cable is an unshielded twisted pair Category 5 (UTP-CAT 5) network cable. The XAP Net has a 10/100Mbps NIC and can connect at either speed, depending on ...
00_Bootcamp
... • Learns which MAC addr is on which port • If it knows the destination MAC address, will send it out only on that port • Broadcast frames must be sent out of all ports, just like a hub • Doesn’t look any further than L2 header ...
... • Learns which MAC addr is on which port • If it knows the destination MAC address, will send it out only on that port • Broadcast frames must be sent out of all ports, just like a hub • Doesn’t look any further than L2 header ...
Communication Network Protocols ---
... 1. A layer should be created where a different abstraction is needed. 2. Each layer should perform a well-defined function. 3. The function of each layer should be chosen with an eye toward defining internationally standardized protocols. 4. The layer boundaries should be chosen to minimize the info ...
... 1. A layer should be created where a different abstraction is needed. 2. Each layer should perform a well-defined function. 3. The function of each layer should be chosen with an eye toward defining internationally standardized protocols. 4. The layer boundaries should be chosen to minimize the info ...
WLAN and IEEE 802.11 Security
... nodes transmit over the air and hence anyone within the radio range can eavesdrop on the communication. So conventional security measures that apply to a wired network do not work in this case. ...
... nodes transmit over the air and hence anyone within the radio range can eavesdrop on the communication. So conventional security measures that apply to a wired network do not work in this case. ...
Wi-Fi Protected Setup - TP-Link
... Main Network Both 2.4GHz and 5GHz extended networks share the same Wi-Fi password as your main network, but may have different wireless network names if you customize the names during the configuration. ...
... Main Network Both 2.4GHz and 5GHz extended networks share the same Wi-Fi password as your main network, but may have different wireless network names if you customize the names during the configuration. ...
Top-Down Network Design
... you referring to bytes per second, regardless of whether the bytes are user data bytes or packet header bytes ...
... you referring to bytes per second, regardless of whether the bytes are user data bytes or packet header bytes ...
Composing Software-Defined Networks Christopher Monsanto , Joshua Reich , Nate Foster
... each application controls its own slice—a disjoint portion of traffic, over which the tenant or application module has (the illusion of) complete visibility and control [21, 8]. In addition to traffic isolation, such a platform may also support subdivision of network resources (e.g., link bandwidth, ...
... each application controls its own slice—a disjoint portion of traffic, over which the tenant or application module has (the illusion of) complete visibility and control [21, 8]. In addition to traffic isolation, such a platform may also support subdivision of network resources (e.g., link bandwidth, ...
Document
... usually connected to at least two networks • Switch: a switch is a device that receive data packets and send them to their intended nodes on the same network ( not between different networks ) ...
... usually connected to at least two networks • Switch: a switch is a device that receive data packets and send them to their intended nodes on the same network ( not between different networks ) ...
ppt - Course Website Directory
... Each packet contains a sequence number that is incremented for each new LSA packet sent. Each router keeps track of all the (source router, sequence) pairs it sees. When a new LSA packet comes in, it is checked against the pairs. If the received packet is new, it is forwarded on all the links except ...
... Each packet contains a sequence number that is incremented for each new LSA packet sent. Each router keeps track of all the (source router, sequence) pairs it sees. When a new LSA packet comes in, it is checked against the pairs. If the received packet is new, it is forwarded on all the links except ...
Lesson 1 Slides - Introdction
... client host requests, receives service from always-on server e.g. Web browser/server; email client/server ...
... client host requests, receives service from always-on server e.g. Web browser/server; email client/server ...
Advanced Networking Concepts & Troubleshooting
... 1. The destination address of a frame will be the _______________________ 2. The destination IP address of a packet will be the IP address of the ________________________________ 3. The destination port number in a segment header will have a value of __ © Wiley Inc. 2006. All Rights Reserved. ...
... 1. The destination address of a frame will be the _______________________ 2. The destination IP address of a packet will be the IP address of the ________________________________ 3. The destination port number in a segment header will have a value of __ © Wiley Inc. 2006. All Rights Reserved. ...
Flexible, Managed SDH Multiplexers
... The TN-1X has field proven reliability based on: • Experience, with over 25,000 synchronous elements deployed worldwide • Automated remote software download • In service upgrade • Integrated Network Management to contain whole life costs Features of the TN-1X • Point and click end path management sy ...
... The TN-1X has field proven reliability based on: • Experience, with over 25,000 synchronous elements deployed worldwide • Automated remote software download • In service upgrade • Integrated Network Management to contain whole life costs Features of the TN-1X • Point and click end path management sy ...
MANET auto-configuration using the 802.11 SSID field in Android
... or access point to provide configuration support, the complexity involved in configuring a MANET can become a limiting factor for most users. Recently, a solution was proposed to solve the MANET auto-configuration problem using the 802.11 SSID field (Villanueva et al., 2013). The aim of the proposed ...
... or access point to provide configuration support, the complexity involved in configuring a MANET can become a limiting factor for most users. Recently, a solution was proposed to solve the MANET auto-configuration problem using the 802.11 SSID field (Villanueva et al., 2013). The aim of the proposed ...
MAC Protocols, Ethernet, Token Ring
... Local Area Network (LAN) : Three or more machines are physically connected and communicating. Problems: ...
... Local Area Network (LAN) : Three or more machines are physically connected and communicating. Problems: ...
Semester 2 Chapter 12 - Institute of Technology Sligo
... entries about networks or subnets that are directly connected to it. Each interface must be configured with an IP address and a mask. The Cisco IOS software learns about this IP address and mask information from configuration information that has been input from some source. The initial source of ad ...
... entries about networks or subnets that are directly connected to it. Each interface must be configured with an IP address and a mask. The Cisco IOS software learns about this IP address and mask information from configuration information that has been input from some source. The initial source of ad ...
Supported technologies in a nutshell
... Deployment scenarios According to general recommendations and best practices in network security NBA should be deployed together with traditional signature based solutions (anti-virus, anti-malware or intrusion detection and prevention) to monitor the network traffic for unknown or unusual deviation ...
... Deployment scenarios According to general recommendations and best practices in network security NBA should be deployed together with traditional signature based solutions (anti-virus, anti-malware or intrusion detection and prevention) to monitor the network traffic for unknown or unusual deviation ...
ppt
... source addresses • Link testing – how routers either explicitly identify which hops are involved in attack or use controlled flooding and a network map to perturb attack traffic • Logging – log packets at key routers and post-process to identify attacker’s path • ICMP traceback – sample occasional p ...
... source addresses • Link testing – how routers either explicitly identify which hops are involved in attack or use controlled flooding and a network map to perturb attack traffic • Logging – log packets at key routers and post-process to identify attacker’s path • ICMP traceback – sample occasional p ...
HY3313681373
... industrial control equipment or network devices. With the continuous expansion of network scale and the increase of service, the embedded Internet has played an increasingly important role. Ethernet is the most widely used LAN technology in the present day world. With the increasing use of embedded ...
... industrial control equipment or network devices. With the continuous expansion of network scale and the increase of service, the embedded Internet has played an increasingly important role. Ethernet is the most widely used LAN technology in the present day world. With the increasing use of embedded ...
PDF
... the private (in this case the 10.0.0.0 network) addresses in the internal network to the legal (in this case 172.18.0.1) addresses before the packets are forwarded to another network. As apart of this function, NAT is configured to advertise only one address (172.18.0.1) for the entire network. This ...
... the private (in this case the 10.0.0.0 network) addresses in the internal network to the legal (in this case 172.18.0.1) addresses before the packets are forwarded to another network. As apart of this function, NAT is configured to advertise only one address (172.18.0.1) for the entire network. This ...
Liberty-i Wireless Glossary
... An IEEE specification for Power over Ethernet (PoE). The standard provides the capability to deliver both power and data over standard Ethernet cabling. Power over Ethernet enables remote devices (such as VoIP phones or Wireless Access Points) to operate without a separate power source, which simpli ...
... An IEEE specification for Power over Ethernet (PoE). The standard provides the capability to deliver both power and data over standard Ethernet cabling. Power over Ethernet enables remote devices (such as VoIP phones or Wireless Access Points) to operate without a separate power source, which simpli ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.























