* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download ITEC275v2
Internet protocol suite wikipedia , lookup
Distributed firewall wikipedia , lookup
Parallel port wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
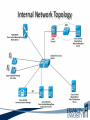
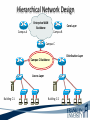
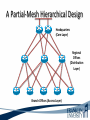
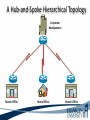
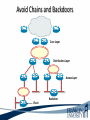
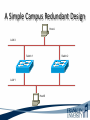
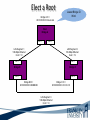
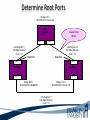
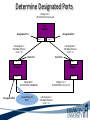
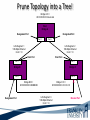
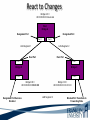
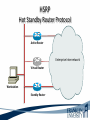
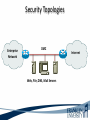
ITEC 275 Computer Networks – Switching, Routing, and WANs Week 5 Robert D’Andrea Some slides provide by Priscilla Oppenheimer and used with permission • Learning Activities Agenda – Network Design Document, logical design, and top-down network design methodology. – Hierarchical Network Design, network topology consisting of many interrelated components. This task might be easier to divide and conquer the problem and develop it. – Spanning Tree Protocol, fast convergence network routers. – VLANs, small bandwidths to switches rather than broadcasting. – Redundancy, provides availability, performance, and scalability. – VPNs, use a third party communication media securring data. Documenting Your Design • If you are given a request for proposal (RFP), respond to the request in the exact format that the RFP specifies • If no RFP, you should still write a design document – Describe your customer’s requirements and how your design meets those requirements – Document the budget for the project – Explain plans for implementing the design Typical RFP Response Topics • A network topology for the new design • Information on the protocols, technologies, and products that form the design • An implementation plan • A training plan • Support and service information and plan • Prices and payment options • Qualifications of the responding vendor or supplier • Recommendations from other customers • Legal contractual terms and conditions Contents of a Network Design Document • • • • • • • • • Executive summary Project goal Project scope Design requirements Current state of the network New logical and physical design Results of network design testing Implementation plan Project budget Design Requirements • Business goals explain the role the network design will play in helping an organization succeed • Technical goals include scalability, performance, security, manageability, usability, adaptability, and affordability Logical and Physical Design • Logical design – Topology – Models for addressing and naming – Switching and routing protocols – Security strategies – Network management strategies • Physical design – Actual technologies and devices Implementation Plan • Recommendations for deploying the network design • Project schedule – Including any dates and times for service provider installations • • • • • Any plans for outsourcing Training Risks A fallback plan if the implementation should fail A plan for evolving the design as new requirements arise Possible Appendixes • • • • • • • Detailed topology maps Device configurations Addressing and naming details Network design testing results Contact information Pricing and payment options More information about the company that is presenting the design – Annual reports, product catalogs, press releases • Legal contractual terms and conditions Topology • A branch of mathematics concerned with those properties of geometric configurations that are unaltered by elastic deformations such as stretching or twisting • A term used in the computer networking field to describe the structure of a network What is a Topology? Definition of Topology A topology is a map of an internetwork that indicates network, segments, interconnection points, and user communities. The purpose of the map is to show the geometry of the network, not the physical geography or technical implementation. External Network Topology Internal Network Topology Detail Description of External Network Topology What is Convergence? Definition of Convergence The speed and ability of a group of internetworking devices running a specific routing protocol to agree on the topology of an un-internetwork after a change in the topology. Convergence is Voice, Data, and Video Scope of Convergence Network Topology Design Themes • • • • • Hierarchy Redundancy Modularity Well-defined entries and exits Protected perimeters Why Use a Hierarchical Model? • Reduces workload on network devices – Avoids devices having to communicate with too many other devices (reduces “CPU adjacencies”) • • • • Constrains broadcast domains Enhances simplicity and understanding Facilitates changes Facilitates scaling to a larger size Why Use a Hierarchical Model? When networks grow without a plan or purpose, they develop into an unstructured format. According to Dr. Peter Welcher, the author of network design and technology articles for Cisco World, the unstructured design becomes a fur-ball network. Why Use a Hierarchical Model? What are the disadvantages of fur-ball topology? • Too many CPU adjacencies – the network devices communicate with too many other devices (broadcast packets). • Workload required of the CPU on the device can be overloading. • Affected devices are routers, workstations, and servers. Why Use a Hierarchical Model? When trying to meet a customers business and technical goals for a corporate network design, it might be necessary to recommend a network topology of many interrelated components. The task is made easier if you can “divide and conquer” the job and develop the design in independent layers. Network design experts can develop a hierarchical network design model in layers to better understand and select the discrete layers. Hierarchical Network Design Enterprise WAN Backbone Campus A Core Layer Campus B Campus C Campus C Backbone Access Layer Building C-1 Building C-2 Distribution Layer Cisco’s Hierarchical Design Model • A core layer of high-end routers and switches that are optimized for availability and speed. Avoid connecting packet filters or network monitors at this layer. • A distribution layer of routers and switches that implement policies and segment traffic. This is a demarcation point between access and core layer of the network. Cisco’s Hierarchical Design Model • An access layer that connects users via hubs, switches, routers, and other devices. Switches are usually implemented at the access layer in campus networks to divide up bandwidth domains to meet the demands of applications that need a lot of bandwidth or cannot handle the delay associated with sharing a bandwidth. A network design guideline would be to design the access layer first, then the distribution, and core layer. Cisco’s Hierarchical Design Model • Controlling a Network Diameter Provides low and predictable latency. Predict routing paths Traffic flows Capacity requirements Flat Versus Hierarchy Headquarters in Medford Headquarters in Medford Grants Pass Branch Office Klamath Falls Branch Office Ashland Branch Office Flat Loop Topology Grants Pass Branch Office Klamath Falls Branch Office Ashland Branch Office White City Branch Office Hierarchical Redundant Topology Flat Network Topology Mesh Versus Hierarchical-Mesh Topologies • Mesh Topologies Full-mesh topology provides complete redundancy and good performance. There is only a single link delay between two sites. Costly to implement a full-mesh topology. Partial-mesh topology has fewer connections between sites. To reach another switch or router, traffic flow would experience more traversing of intermediate links. Mesh Designs Full-Mesh Topology Partial-Mesh Topology A Partial-Mesh Hierarchical Design Headquarters (Core Layer) Regional Offices (Distribution Layer) Branch Offices (Access Layer) Company Structure • Small and Medium-Sized Companies Recommend a hierarchical model that reflects a hub-and-spoke topology. Usually, corporate headquarters or a data center form the center hub. Links extended from the hub connect to remote offices and telecommuters’ locations. See slide Hub-and-Spoke Hierarchical Topology A Hub-and-Spoke Hierarchical Topology Corporate Headquarters Branch Office Home Office Branch Office Scope of Access • Control Access Layer Diameter The most likely place for network design violations to occur are at the access layer. Users and network administrators are more likely to add networks to the internetwork and connect remote networks together. This is known as adding a chain. Avoid backdoors. A backdoor connection is a connection between devices in the same layer. A hub is considered a backdoor. Avoid Chains and Backdoors Core Layer Distribution Layer Access Layer Backdoor Chain How Do You Know When You Have a Good Design? • When you already know how to add a new building, floor, WAN link, remote site, e-commerce service, and so on • When new additions cause only local change, to the directly-connected devices • When your network can double or triple in size without major design changes • When troubleshooting is easy because there are no complex protocol interactions to wrap your brain around Flat Network Use • A flat network topology is adequate for small networks. Each network device functions the same, and the network is not divided into layers or modules. A flat network is easy to design. Flat network designers are most difficult when there is network growth, and the lack of hierarchy makes trouble shooting more difficult. Flat WAN Networks • Flat WAN Topologies A WAN for a small company consists of a few sites connected in a loop. Each site has it’s own WAN router, routing protocols can converge quickly, and communication with any other site can recover when a link fails. Caveat: If only one link fails, recovery is possible. If two or more links fail, recovery is more difficult. The flat loop topology goals are low cost and reasonably good availability. See slide -Flat verses Hierarchical. Flat LAN Networks • Flat LAN Topologies In the 1990s, a typical LAN configuration was to connect PCs and servers to one or more hubs. The PCs and servers implemented a media-access control process like token passing or carrier sense multiple access with collision detection (CSMA/CD) to control access to a shared bandwidth. This configuration had the potential to negatively affect delay and throughput for other devices. Today, designers recommend connecting PCs and servers to the data link layer (Layer 2) switches . Layer 2 Configuration • Characterizing Layer 2 Network Traffic Devices connected in a switched or bridged network are all in the same broadcast domain. Switches forward broadcasting frames out from every port. Routers on the other hand, separate segments into separate broadcast domains. The recommended limit for devices connected to one single broadcast domain is a couple hundred devices. Broadcasted traffic needs to be limited and watched closely on flat loop topologies, otherwise frames can be dropped or lost. Rule of Thumb – limit broadcast traffic to 20% of the traffic on each link. CISCO SAFE Security Architecture Cisco SAFE is a security reference architecture that provides prescriptive validated design guides that address how organizations can plan, design, and deploy security solutions that meet the unique requirements of different places in the network, such as campuses, the Internet edge, branches, and data centers. These defense-in-depth blueprints also provide best practices for securing critical data and transactions as they travers the entire networked infrastructure. Cisco’s SAFE Security Reference Architecture Campus Topology Design • • • • Use a hierarchical, modular approach Minimize the size of bandwidth domains Minimize the size of broadcast domains Provide redundancy – Backup paths – Mirrored servers – Mirror stored data – Multiple ways for workstations to reach a router for off-net communications Campus Topology Design • Cisco SAFE Security Reference Architecture - Used to simplify the complexity of a large internetwork - SAFE is concerned with security - Defense-in-depth approach were multiple layers of protection are strategically located through-out the network. - See page 134 for major design modules A Simple Campus Redundant Design Host A LAN X Switch 1 Switch 2 LAN Y Host B Bridges and Switches use Spanning-Tree Protocol (STP) to Avoid Loops Host A LAN X X Switch 2 Switch 1 LAN Y Host B What is Spanning Tree Protocol? Spanning Tree Protocol (STP) is a layer2 protocol that prevents logical loops in switched networks that have redundant links. Redundancy in a network may appear to be harmless and needed to maintain connectivity with other devices. One problem occurs when a broadcast frame is sent on the network. Device A sends an ARP request to find the MAC address of device B. The ARP request is sent as a broadcast. Both switches receive the broadcast and both switches flood the broadcast to all of its other connected ports. The end result is a broadcast storm. What is Spanning Tree Protocol? A second problem occurs with redundant topologies is a single device will receive multiple copies of the same frame. The third problem occurs within the switch itself. The MAC address table can change rapidly and contain wrong information. What happens when neither switch has learned about devices A and B’s location? Device A sends data to device B. Each switch learns about device A is on port 1, and each records this in its MAC address table. The switches haven’t learned about device B yet. Both switches flood the frame to discover device B on their port 2. What is Spanning Tree Protocol? As a result, the MAC address table is overwritten. The switches previously had device A connected to port 1. Because the table changed rapidly, it might be considered unstable. Bridges (Switches) Running STP • Participate with other bridges in the election of a single bridge as the Root Bridge. • Calculate the distance of the shortest path to the Root Bridge and choose a port (known as the Root Port) that provides the shortest path to the Root Bridge. • For each LAN segment, elect a Designated Bridge and a Designated Port on that bridge. The Designated Port is a port on the LAN segment that is closest to the Root Bridge. (All ports on the Root Bridge are Designated Ports.) • Select bridge ports to be included in the spanning tree. The ports selected are the Root Ports and Designated Ports. These ports forward traffic. Other ports block traffic. Elect a Root Bridge A ID = 80.00.00.00.0C.AA.AA.AA Lowest Bridge ID Wins! Root Bridge A Port 1 Port 2 LAN Segment 1 100-Mbps Ethernet Cost = 19 LAN Segment 2 100-Mbps Ethernet Cost = 19 Port 1 Port 1 Bridge B Bridge C Port 2 Port 2 Bridge B ID = 80.00.00.00.0C.BB.BB.BB Bridge C ID = 80.00.00.00.0C.CC.CC.CC LAN Segment 3 100-Mbps Ethernet Cost = 19 Determine Root Ports Bridge A ID = 80.00.00.00.0C.AA.AA.AA Root Bridge A Port 1 Lowest Cost Wins! Port 2 LAN Segment 1 100-Mbps Ethernet Cost = 19 LAN Segment 2 100-Mbps Ethernet Cost = 19 Root Port Root Port Port 1 Port 1 Bridge B Bridge C Port 2 Port 2 Bridge B ID = 80.00.00.00.0C.BB.BB.BB Bridge C ID = 80.00.00.00.0C.CC.CC.CC LAN Segment 3 100-Mbps Ethernet Cost = 19 Determine Designated Ports Bridge A ID = 80.00.00.00.0C.AA.AA.AA Root Bridge A Designated Port Designated Port Port 1 Port 2 LAN Segment 1 100-Mbps Ethernet Cost = 19 LAN Segment 2 100-Mbps Ethernet Cost = 19 Root Port Root Port Port 1 Port 1 Bridge B Bridge C Port 2 Port 2 Bridge B ID = 80.00.00.00.0C.BB.BB.BB Designated Port Lowest Bridge ID Wins! Bridge C ID = 80.00.00.00.0C.CC.CC.CC LAN Segment 3 100-Mbps Ethernet Cost = 19 Prune Topology into a Tree! Bridge A ID = 80.00.00.00.0C.AA.AA.AA Root Bridge A Designated Port Designated Port Port 1 Port 2 LAN Segment 1 100-Mbps Ethernet Cost = 19 LAN Segment 2 100-Mbps Ethernet Cost = 19 Root Port Root Port Port 1 Port 1 Bridge B Bridge C Port 2 Port 2 Bridge B ID = 80.00.00.00.0C.BB.BB.BB Designated Port Bridge C ID = 80.00.00.00.0C.CC.CC.CC LAN Segment 3 100-Mbps Ethernet Cost = 19 X Blocked Port React to Changes Bridge A ID = 80.00.00.00.0C.AA.AA.AA Root Bridge A Designated Port Designated Port Port 1 Port 2 LAN Segment 1 LAN Segment 2 Root Port Root Port Port 1 Port 1 Bridge B Bridge C Port 2 Port 2 Bridge B ID = 80.00.00.00.0C.BB.BB.BB Designated Port Becomes Disabled Bridge C ID = 80.00.00.00.0C.CC.CC.CC LAN Segment 3 Blocked Port Transitions to Forwarding State Scaling the Spanning Tree Protocol • Keep the switched network small – It shouldn’t span more than seven switches • Use Bridge Protocol Data Units (BPDU) skew detection on Cisco switches • Use IEEE 802.1w – Provides rapid reconfiguration of the spanning tree – Also known as RSTP Rapid Spanning Tree Protocol • Bridge port states - Discarding is a port that is neither learning MAC addresses nor forwarding user’s frames. - Learning is a port that is learning MAC addresses to populate the MAC address table, but has not yet forwarded user frames - Forwarding is a port that is learning MAC addresses and forwarding user frames. Rapid Spanning Tree Protocol • Converged switched network Bridge port roles - Root port assigned on a non-root bridge, provides lowest cost path to the root bridge. - Designated assigned on a port attached to a LAN, provides lowest cost path to the root bridge. - Alternate assigned to a port that offers an alternative path in the direction of the root bridge to that provided by the bridge’s root port. Considered a discarded port Rapid Spanning Tree Protocol - Backup assigned to a port on a designated bridge that acts as a backup path provided by a designated port in the direction of the leaves of the spanning tree. - Disabled assigned to a port that is not operational or is excluded from the active topology by network management. Considered a discarded port. Rapid Spanning Tree Protocol RSTP converges quicker than STP (50 seconds) to a tree topology where the lowestcost paths are forwarding frames. RSTP archives rapid transition to the forwarding state on edge ports, root ports, and point-topoint links. Edge and root ports can transition to forwarding without transmitting or receiving messages from other bridges. Rapid Spanning Tree Protocol • Port Modes Full-duplex mode port assumed to be point-to-point. Modern switched networks utilize this mode mostly. Half-duplex mode port considered a shared port by default. Rapid Spanning Tree Protocol • Root Bridge High speed Reliable Centered in network topology A switch with the lowest bridge ID Priority field MAC address the lowest MAC address of a switch or bridge Selecting a Root Bridge Control which switch becomes the root bridge. • Reliable • High-speed switch in the center of the topology • If switches are to elect the root on their own, you will have little control of the direction that traffic flows and the amount of frame-forwarding delay in your network. Selecting a Root Bridge Control which switch becomes the root bridge. • Control of the root bridge is critical because a slow bridge can become the root bridge. • If high-speed ports are accidentally removed from the spanning tree it is possible for low-speed ports to take their place because they are closer to the root bridge. Selecting a Root Bridge The root bridge is the switch with the lowest bridge ID. There are two parts to the bridge ID. 1. Priority field 2. MAC address of the switch If all priorities are set to their default value, the switch with the lowest MAC address becomes root. Manual control of the root bridge is important to maintain high throughput on switched networks. Virtual LANs (VLANs) • An emulation of a standard LAN that allows data transfer to take place without the traditional physical restraints placed on a network • A set of devices that belong to an administrative group • Designers use VLANs to constrain broadcast traffic VLANs versus Real LANs Switch A Station A1 Station A2 Network A Switch B Station A3 Station B1 Station B2 Network B Station B3 A Switch with VLANs VLAN A Station A1 Station B1 Station A2 Station B2 VLAN B Station A3 Station B3 VLANs Span Switches VLAN A Station A1 Station A2 VLAN A Station A3 Station A4 Station A5 Switch A Station B1 Station A6 Switch B Station B2 VLAN B Station B3 Station B4 Station B5 VLAN B Station B6 WLANs and VLANs • A wireless LAN (WLAN) is often implemented as a VLAN • Facilitates roaming • Users remain in the same VLAN and IP subnet as they roam, so there’s no need to change addressing information • Also makes it easier to set up filters (access control lists) to protect the wired network from wireless users Workstation-to-Router Communication • Proxy ARP (not a good idea) • Listen for route advertisements (not a great idea either) • ICMP router solicitations (not widely used) • Default gateway provided by DHCP (better idea but no redundancy) – Use Hot Standby Router Protocol (HSRP) for redundancy HSRP Hot Standby Router Protocol Active Router Enterprise Internetwork Virtual Router Workstation Standby Router Week Five What is Multi-homing? Multi-homing is to provide more than one connection for a system to access and offer network services. In an enterprise network, multi-homing provides access to more than one entry into the Internet. Example: WAN backup and ISP redundancy If a server has more than one network layer address. Multi-homing the Internet Connection ISP 1 ISP 1 Enterprise Option A ISP 1 ISP 2 Enterprise Paris ISP 1 Paris Option B Enterprise Enterprise NY Option C ISP 2 NY Option D Security Topologies Enterprise Network DMZ Web, File, DNS, Mail Servers Internet Security Topologies Internet Firewall DMZ Web, File, DNS, Mail Servers Enterprise Network Network Security Definition of Firewall A firewall is a system or combination of systems that enforces a boundary between two or more networks. Router with ACL Firewall should be placed within the network topology so that all traffic from outside the protected network must pass through the firewall. NAT (Network Address Translation) Definitions ARP (Address Resolution Protocol) used to find a remote station. Traces IP addresses to MAC addresses. RARP (Reverse Address Resolution Protocol) the protocol within TCP/IP stack that maps MAC addresses to IP addresses. RIP (Routing Information Protocol) is commonly used interior gateway protocol in the Internet. RIP employees hop count as a routing metric. Root bridge is used with STP to stop network loops from occurring. The root bridge is elected to have the lowest bridge ID. Definitions Static routing occurs when an administrator manually adds routes in each router’s routing table. Dynamic routing is when protocols are used to find and update routing tables on routers. Routing Protocols Distance vector – RIP and IGRP Link state - OSPF Hybrid - EIGRP Summary • When a customer provides an RFP, make sure to follow the prescribed format • When not bound by an RFP, develop a design document that describes requirements, the existing network, the logical and physical design, an implementation plan, and the budget • Be sure to include an executive summary • In some cases, you should also include appendixes with detailed information Summary • Use a systematic, top-down approach • Plan the logical design before the physical design • Topology design should feature hierarchy, redundancy, modularity, and security Review Questions • Why is it important to document your network design? • Why is it important to submit an RFP proposal in the exact format prescribed? • What are the major topics in a design document? • What are some possible appendixes for a design document? Review Questions • Why are hierarchy and modularity important for network designs? • What are the three layers of Cisco’s hierarchical network design? • What are the major components of Cisco’s enterprise composite network model? • What are the advantages and disadvantages of the various options for multihoming an Internet connection? This Week’s Outcomes • • • • • • Network Design Document Hierarchical Network Design Spanning Tree Protocol VLANs Redundancy VPNs Due this week • 4-2-1 – Simulator Tutorial and Basic IOS Command Exploration Next week • Read chapter 6 in Top-Down Network Design • Read chapter 6 in Designing Cisco Internetwork Solutions • 5-1 – Concept questions 4 • 1-5-1 – Network Design Project 1 – Switches Q&A • Questions, comments, concerns?