ECE544 - WINLAB
... – “Hello” message exchange between neighbors – Does not receive the expected periodical routing updates for the last few update cycles. • Receive an update from another router that causes it to change its routing table Each update is a list of pairs: – (Destination, Cost) Update local table if recei ...
... – “Hello” message exchange between neighbors – Does not receive the expected periodical routing updates for the last few update cycles. • Receive an update from another router that causes it to change its routing table Each update is a list of pairs: – (Destination, Cost) Update local table if recei ...
Virtual Classroom Course Description Integrated Drives Control over an EtherNet/IP™ Network
... network topology and relevant components, configure controllers and axes, and add Kinetix® 6500 and PowerFlex® 755 drives for control over an EtherNet/IP network (also known as CIP™ motion). This course will also show you how to start up the network, run hookup tests, autotune axes, and test axes wi ...
... network topology and relevant components, configure controllers and axes, and add Kinetix® 6500 and PowerFlex® 755 drives for control over an EtherNet/IP network (also known as CIP™ motion). This course will also show you how to start up the network, run hookup tests, autotune axes, and test axes wi ...
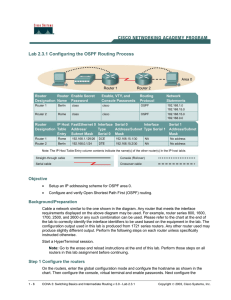
Lab 2.3.1 Configuring the OSPF Routing Process Objective
... FastEthernet 0/1 (FA0/1) Serial 0/0 (S0/0) Serial 0/1 (S0/1) (FA0/0) In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations f ...
... FastEthernet 0/1 (FA0/1) Serial 0/0 (S0/0) Serial 0/1 (S0/1) (FA0/0) In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations f ...
Module 4: Processes
... for host B (which might be quite large, being a global identifier on the network), each data packet contains only a small identifier, which is only unique on one link. Thus the per-packet overhead caused by the header is reduced ...
... for host B (which might be quite large, being a global identifier on the network), each data packet contains only a small identifier, which is only unique on one link. Thus the per-packet overhead caused by the header is reduced ...
Network Operating Systems (NOS) - csi-fx
... . Network operating systems (NOS) for Intermediary Device A specialized OS embedded in router or switch 4 Cisco Internetworking Operating System (IOS) ...
... . Network operating systems (NOS) for Intermediary Device A specialized OS embedded in router or switch 4 Cisco Internetworking Operating System (IOS) ...
Network Programming - Computer Systems: A Programmer`s
... The crucial property of an internet is that it can consist of different LANs and WANs with radically different and incompatible technologies. Each host is physically connected to every other host, but how is it possible for some source host to send data bits to another destination host across all of ...
... The crucial property of an internet is that it can consist of different LANs and WANs with radically different and incompatible technologies. Each host is physically connected to every other host, but how is it possible for some source host to send data bits to another destination host across all of ...
Layers of Network Communication
... • MAC (media access control) address is a unique 48-bit hexadecimal number hard-coded on the card by the manufacturer • Also known as hardware address, physical address, adapter address, or Ethernet address ...
... • MAC (media access control) address is a unique 48-bit hexadecimal number hard-coded on the card by the manufacturer • Also known as hardware address, physical address, adapter address, or Ethernet address ...
Troubleshooting LSP Failure in MPLS VPN
... by this router for the same subnet/subnet mask pair, these labels will not be used by upstream neighbors and the Label Switched Path (LSP) between these devices will fail. This document gives an example of this kind of LSP failure and several possible solutions. The document covers one scenario wher ...
... by this router for the same subnet/subnet mask pair, these labels will not be used by upstream neighbors and the Label Switched Path (LSP) between these devices will fail. This document gives an example of this kind of LSP failure and several possible solutions. The document covers one scenario wher ...
PARAM Padma SuperComputer
... HPCC Software continued C-FPS is a client-server and user level parallel file system that addresses high I/O throughput ...
... HPCC Software continued C-FPS is a client-server and user level parallel file system that addresses high I/O throughput ...
Chapter 3: Internetworking (part 1)
... All bridges would start off by claiming to be the root Denote a configuration message from node X in which it claims to be distance d from the root node Y as (Y, d, X) ...
... All bridges would start off by claiming to be the root Denote a configuration message from node X in which it claims to be distance d from the root node Y as (Y, d, X) ...
Lesson_Powerpoint_Notes
... “To transfer information across the Internet, you send it through the networks. To accomplish this, the Information is broken up into what is known as IP Packets. IP packets are the “items” that are transferred across the networks. The diagram illustrates what the Packets contains: - As we can see i ...
... “To transfer information across the Internet, you send it through the networks. To accomplish this, the Information is broken up into what is known as IP Packets. IP packets are the “items” that are transferred across the networks. The diagram illustrates what the Packets contains: - As we can see i ...
Running Head: ABBREVIATED TITLE IN CAPS
... terminated at each end with an eight-pin RJ-45 connector. The pair connected to pins 1 and 2 is used for transmitting, and the pair connected to pins 3 and 6 is used for receiving. 2. Replacing hubs with switches in 10BASE-T networks has greatly increased the throughout available to these networks a ...
... terminated at each end with an eight-pin RJ-45 connector. The pair connected to pins 1 and 2 is used for transmitting, and the pair connected to pins 3 and 6 is used for receiving. 2. Replacing hubs with switches in 10BASE-T networks has greatly increased the throughout available to these networks a ...
8 - 1 - WVU College of Business and Economics
... • Process L3 messages (no changes made) • Form new L2 messages for outgoing packets – Processes only messages specifically addressed to it Copyright 2005 John Wiley & Sons, Inc ...
... • Process L3 messages (no changes made) • Form new L2 messages for outgoing packets – Processes only messages specifically addressed to it Copyright 2005 John Wiley & Sons, Inc ...
Aalborg Universitet Wei, Mu; Chen, Zhe
... have been used as the basis for ISO standards. Moreover, since all of the protocol specifications associated with TCP/IP are in the public domain, and hence no license fees are payable, they have been used extensively by commercial and public authorities for creating open system networking environme ...
... have been used as the basis for ISO standards. Moreover, since all of the protocol specifications associated with TCP/IP are in the public domain, and hence no license fees are payable, they have been used extensively by commercial and public authorities for creating open system networking environme ...
PPT_ch10
... Earlier and less sophisticated than PPP Can only carry IP packets Requires significant amount of setup Does not support data encryption Asynchronous transmission ...
... Earlier and less sophisticated than PPP Can only carry IP packets Requires significant amount of setup Does not support data encryption Asynchronous transmission ...
ppt
... • Key to protocol families is that communication occurs logically at the same level of the protocol, called peer-topeer, but is implemented via services at the lower level • Danger is each level increases latency if implemented as JR.S00 42 hierarchy (e.g., multiple check sums) ...
... • Key to protocol families is that communication occurs logically at the same level of the protocol, called peer-topeer, but is implemented via services at the lower level • Danger is each level increases latency if implemented as JR.S00 42 hierarchy (e.g., multiple check sums) ...
The phenomenon of blurring time dependencies may be used to find
... processor and 12 GB of RAM, an operating system launched on this machine was Ubuntu 14.04 LTS. The main and most important part of the environment was the server which dealt with the setup of hosts and a virtualizer, but was also responsible for defining experiments, sending commands and collecting ...
... processor and 12 GB of RAM, an operating system launched on this machine was Ubuntu 14.04 LTS. The main and most important part of the environment was the server which dealt with the setup of hosts and a virtualizer, but was also responsible for defining experiments, sending commands and collecting ...
Chapter 6 slides, Computer Networking, 3rd edition
... AP admin chooses frequency for AP interference possible: channel can be same as that chosen by neighboring AP! ...
... AP admin chooses frequency for AP interference possible: channel can be same as that chosen by neighboring AP! ...
EIGRP
... Router One becomes unavailable, Router Two examines its topology table and, finding a feasible successor, begins using the path through Three immediately. ...
... Router One becomes unavailable, Router Two examines its topology table and, finding a feasible successor, begins using the path through Three immediately. ...
Troubleshooting Your Verizon FiOS® Internet Quick Reference Guide
... When you visit our online help tool, you can find out about: ...
... When you visit our online help tool, you can find out about: ...
KR2518691873
... devices to dynamically self organize into arbitrary and temporary wireless topologies without fixed communication infrastructure. One of the most popular MAC layer protocol used in Ad hoc network is 802.11b. Since the IEEE 802.11 standard support multiple data rates at the physical layer, many rate ...
... devices to dynamically self organize into arbitrary and temporary wireless topologies without fixed communication infrastructure. One of the most popular MAC layer protocol used in Ad hoc network is 802.11b. Since the IEEE 802.11 standard support multiple data rates at the physical layer, many rate ...
Restricting Access in the network
... forwarded out on S0/0/0. Traffic from networks other than 192.168.10.0 is blocked. The first line identifies the ACL as access list 1. It permits traffic that matches the selected parameters. access-list 1 permit 192.168.10.0 ...
... forwarded out on S0/0/0. Traffic from networks other than 192.168.10.0 is blocked. The first line identifies the ACL as access list 1. It permits traffic that matches the selected parameters. access-list 1 permit 192.168.10.0 ...
Chapter 10 - Computer Science Technology
... Protecting a Network from Worms, Viruses, and Rootkits • Malware is SW designed to cause harm/disruption to a computer system or perform activities on a computer without the consent of its owner – A virus spreads by replicating itself into other programs or documents – A worm is similar to a virus, ...
... Protecting a Network from Worms, Viruses, and Rootkits • Malware is SW designed to cause harm/disruption to a computer system or perform activities on a computer without the consent of its owner – A virus spreads by replicating itself into other programs or documents – A worm is similar to a virus, ...
Recurrent Security Gaps In 802.11ac Routers
... the wireless devices or clients in a WLAN in Infrastructure mode will connect to the wireless router. A wireless router is a communication hardware that provides a single connection point for wireless connectivity in a network. It uses transmit/receive antennas for wireless connection and uses WAN/L ...
... the wireless devices or clients in a WLAN in Infrastructure mode will connect to the wireless router. A wireless router is a communication hardware that provides a single connection point for wireless connectivity in a network. It uses transmit/receive antennas for wireless connection and uses WAN/L ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.