300Mbps Dual-Band 802.11n Wireless Gigabit Router
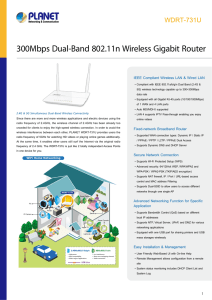
... radio frequency of 5GHz for watching HD videos or playing online games additionally. At the same time, it enables other users still surf the Internet via the original radio frequency of 2.4 GHz. The WDRT-731U is just like 2 totally independent Access Points in one device for you. ...
... radio frequency of 5GHz for watching HD videos or playing online games additionally. At the same time, it enables other users still surf the Internet via the original radio frequency of 2.4 GHz. The WDRT-731U is just like 2 totally independent Access Points in one device for you. ...
ppt
... • Explicit Loss/Congestion Notification (ELN, ECN), • ACKs include flag indicating wireless loss ...
... • Explicit Loss/Congestion Notification (ELN, ECN), • ACKs include flag indicating wireless loss ...
Route Explorer™ EIGRP Technical Note Introduction
... uses an authentication server, all you need to do is set up an account for Route Explorer on the server and provide the user name and password for that account as input parameters to Route Explorer. The account should be set up so that it allows only “login” access and not “enable” access. If your n ...
... uses an authentication server, all you need to do is set up an account for Route Explorer on the server and provide the user name and password for that account as input parameters to Route Explorer. The account should be set up so that it allows only “login” access and not “enable” access. If your n ...
Inter and intra AS, RIP - Cornell Computer Science
... Security: all OSPF messages authenticated (to prevent malicious intrusion); TCP connections used Multiple same-cost paths can be used at once (single path need not be chosen as in RIP) For each link, multiple cost metrics for different TOS (eg, high BW, high delay satellite link cost may set “low” f ...
... Security: all OSPF messages authenticated (to prevent malicious intrusion); TCP connections used Multiple same-cost paths can be used at once (single path need not be chosen as in RIP) For each link, multiple cost metrics for different TOS (eg, high BW, high delay satellite link cost may set “low” f ...
Firewalls
... Firewalls • Effective means of protection a local system or network of systems from network-based security threats while affording access to the outside world via WANs or the Internet • Information systems undergo a steady evolution (from small LAN`s to Internet connectivity) • Strong security feat ...
... Firewalls • Effective means of protection a local system or network of systems from network-based security threats while affording access to the outside world via WANs or the Internet • Information systems undergo a steady evolution (from small LAN`s to Internet connectivity) • Strong security feat ...
Exploring the Arista 7010T
... or legacy devices. In addition the SFP+ ports allow for dual speed connection at both 1G using a choice of SFP’s or at 10G using a wide range of copper and fiber SFP+ that support up to 10km over single-mode fiber. Optics available are fully compliant to IEEE specifications which allows for easy int ...
... or legacy devices. In addition the SFP+ ports allow for dual speed connection at both 1G using a choice of SFP’s or at 10G using a wide range of copper and fiber SFP+ that support up to 10km over single-mode fiber. Optics available are fully compliant to IEEE specifications which allows for easy int ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... Fast and reliable communications is a basic requirement in almost all modern applications, but the real time systems take it to extreme and require real time responses from the network. In some cases, the requirements are so tough that may require special hardware to achieve desired performance .In ...
... Fast and reliable communications is a basic requirement in almost all modern applications, but the real time systems take it to extreme and require real time responses from the network. In some cases, the requirements are so tough that may require special hardware to achieve desired performance .In ...
Networking.
... Routers – more detail • Routers connect two or more LANs: Multiple network interface cards (NIC) Each NIC has its own MAC address Each NIC has its own IP address! ...
... Routers – more detail • Routers connect two or more LANs: Multiple network interface cards (NIC) Each NIC has its own MAC address Each NIC has its own IP address! ...
Protocol management
... Netflow was first introduced by Cisco and is geared toward collecting data about networking traffic from a device. You can use this data to answer questions such as the following: Who are the top “talkers” in the network ? How much traffic is being exchanged between two destinations? ...
... Netflow was first introduced by Cisco and is geared toward collecting data about networking traffic from a device. You can use this data to answer questions such as the following: Who are the top “talkers” in the network ? How much traffic is being exchanged between two destinations? ...
Secure Routing and Intrusion Detection in Ad-Hoc
... – Real time traffic monitor – Traffic control – Route maintenance module ...
... – Real time traffic monitor – Traffic control – Route maintenance module ...
APRICOT 2001
... Each is 32-bit number AID associated with interface RID 1. Explicitly specified RID 2. Loopback address 3. Highest interface IP address ...
... Each is 32-bit number AID associated with interface RID 1. Explicitly specified RID 2. Loopback address 3. Highest interface IP address ...
CAR-2-X Communication for Safety and Infotainment in Europe
... 64bits MIPS microprocessor, 512MB NAND-Flash, 16MB Nor-Flash and 128MB SDRAM. It supports Linux operation systems, currently with the kernel version 2.6.19. In addition, it provides test program modes and hardware diagnosis functions. With physical dimensions of 153.5mm(W) × 118mm(D) × 43mm(H), the ...
... 64bits MIPS microprocessor, 512MB NAND-Flash, 16MB Nor-Flash and 128MB SDRAM. It supports Linux operation systems, currently with the kernel version 2.6.19. In addition, it provides test program modes and hardware diagnosis functions. With physical dimensions of 153.5mm(W) × 118mm(D) × 43mm(H), the ...
DVoIP: DYNAMIC VOICE-OVER-IP TRANSFORMATIONS FOR QUALITY OF SERVICE IN
... further bandwidth reduction by compressing sequential audio frames into a single packet, reducing network overhead through a negligible increase in stream latency. Either one or both of these actuators can be used at any given time, and each has parameters that can be adjusted to achieve the desired ...
... further bandwidth reduction by compressing sequential audio frames into a single packet, reducing network overhead through a negligible increase in stream latency. Either one or both of these actuators can be used at any given time, and each has parameters that can be adjusted to achieve the desired ...
3rd Edition: Chapter 4
... host broadcasts “DHCP discover” msg [optional] DHCP server responds with “DHCP offer” msg [optional] host requests IP address: “DHCP request” msg DHCP server sends address: “DHCP ack” msg ...
... host broadcasts “DHCP discover” msg [optional] DHCP server responds with “DHCP offer” msg [optional] host requests IP address: “DHCP request” msg DHCP server sends address: “DHCP ack” msg ...
circuit-level gateway
... • In this situation, an intermediate system can be plugged between the private network and the public network to establish a controlled link, and to erect a security wall or perimeter • The aim of the intermediate system is to protect the private network from network-based attacks that may originate ...
... • In this situation, an intermediate system can be plugged between the private network and the public network to establish a controlled link, and to erect a security wall or perimeter • The aim of the intermediate system is to protect the private network from network-based attacks that may originate ...
TCP Details - CSE - University of South Carolina
... Who sends the first FIN - the server or the client? Once the connection is established, what is the difference between the operation of the server’s TCP layer and the client’s TCP layer? What happens if a bad guy can guess ...
... Who sends the first FIN - the server or the client? Once the connection is established, what is the difference between the operation of the server’s TCP layer and the client’s TCP layer? What happens if a bad guy can guess ...
Chapter 2 Lecture Presentation
... connection. It also deals with electrical specifications, collision control and other lowlevel functions. •The physical layer is the most basic network layer, providing only the means of transmitting raw bits. The shapes of the electrical connectors, which frequencies to broadcast on, and similar lo ...
... connection. It also deals with electrical specifications, collision control and other lowlevel functions. •The physical layer is the most basic network layer, providing only the means of transmitting raw bits. The shapes of the electrical connectors, which frequencies to broadcast on, and similar lo ...
CSC311_UNIT1_Part2
... The layers in the TCP/IP protocol suite do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having four layers: host-tonetwork, internet, transport, and application. However, when TCP/IP is compared to OSI, we can say that the TCP/IP protocol suite is made ...
... The layers in the TCP/IP protocol suite do not exactly match those in the OSI model. The original TCP/IP protocol suite was defined as having four layers: host-tonetwork, internet, transport, and application. However, when TCP/IP is compared to OSI, we can say that the TCP/IP protocol suite is made ...
Control System Network
... Must also support access from the existing SLC network for SLC-aware IOCs (SAI). A proxy server on the SLC network must have access to all SAIs on the operations network SAIs must also be fully accessible from the operations network, as would any normal IOC. ...
... Must also support access from the existing SLC network for SLC-aware IOCs (SAI). A proxy server on the SLC network must have access to all SAIs on the operations network SAIs must also be fully accessible from the operations network, as would any normal IOC. ...
Slide 1
... • Port scanning allows you to find: – IP addresses and open ports of live hosts – Operating systems and system architecture – Services running on hosts ...
... • Port scanning allows you to find: – IP addresses and open ports of live hosts – Operating systems and system architecture – Services running on hosts ...
HSMM-Mesh - W7AIA, Clark County Amateur Radio Club
... • Unix systems inherited this terminology. • Daemons are also characters in Greek mythology, some of whom handled tasks that the gods could not be bothered with. CCARES/RACES ...
... • Unix systems inherited this terminology. • Daemons are also characters in Greek mythology, some of whom handled tasks that the gods could not be bothered with. CCARES/RACES ...
Towards Resilient Networks using Programmable Networking
... • Challenges to normal operation will rapidly change over time and space • Prescribed solutions cannot be deployed • Therefore, resilient networks must: ...
... • Challenges to normal operation will rapidly change over time and space • Prescribed solutions cannot be deployed • Therefore, resilient networks must: ...
Distance Vector Algorithm Bellman
... routes via neighbor invalidated new advertisements sent to neighbors neighbors in turn send out new advertisements (if ...
... routes via neighbor invalidated new advertisements sent to neighbors neighbors in turn send out new advertisements (if ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.























