No Slide Title - Syzygy Engineering
... Route optimization is a fundamental part of the protocol Mobile IPv6 route optimization can operate securely even without pre-arranged security associations Route optimization coexists efficiently with routers that perform "ingress filtering" The movement detection mechanism in Mobile IPv6 provides ...
... Route optimization is a fundamental part of the protocol Mobile IPv6 route optimization can operate securely even without pre-arranged security associations Route optimization coexists efficiently with routers that perform "ingress filtering" The movement detection mechanism in Mobile IPv6 provides ...
356961: Internet Protocols
... the frame payload. CRC is based upon the idea that it is highly unlikely for an uncorrupted packet to be perfectly divisible by the CRC polynomial. Random access MAC protocols tend to perform very well at low loads in terms of channel multiplexing; but suffer from high delay at high loads. ...
... the frame payload. CRC is based upon the idea that it is highly unlikely for an uncorrupted packet to be perfectly divisible by the CRC polynomial. Random access MAC protocols tend to perform very well at low loads in terms of channel multiplexing; but suffer from high delay at high loads. ...
Modular Components for Network Address Translation - PDOS-MIT
... Basic NAT was introduced in the early nineties to reduce the pressure for globally allocated IP addresses [9]. With NAT, an organization could assign unique, private IP addresses to each of its hosts, reserving just a few globallyallocated addresses to be shared among the hosts. All packets leaving ...
... Basic NAT was introduced in the early nineties to reduce the pressure for globally allocated IP addresses [9]. With NAT, an organization could assign unique, private IP addresses to each of its hosts, reserving just a few globallyallocated addresses to be shared among the hosts. All packets leaving ...
Development of Network Interface Card (NIC) RT
... Linux is playing a significant role in the embedded applications, and Device drivers take a major responsibility in developing the Linux kernel. This thesis is aimed at the design and implementation of a device driver for Network Interface Card (NIC) RT-8139C to transfer data from PC to the physical ...
... Linux is playing a significant role in the embedded applications, and Device drivers take a major responsibility in developing the Linux kernel. This thesis is aimed at the design and implementation of a device driver for Network Interface Card (NIC) RT-8139C to transfer data from PC to the physical ...
9781133608196_PPT_ch04
... • Network layer protocol – How and where data delivered, including: • Data’s source and destination addresses ...
... • Network layer protocol – How and where data delivered, including: • Data’s source and destination addresses ...
3rd Edition: Chapter 4
... order bits) host part (low order bits) What’s a subnet ? device interfaces with same subnet part of IP address can physically reach each other without intervening router ...
... order bits) host part (low order bits) What’s a subnet ? device interfaces with same subnet part of IP address can physically reach each other without intervening router ...
designing network infrastructure for an e-learning cloud
... Network management, monitoring and security Implementation of the adequate system for network management is an important factor for achieving this goal. Proactive network management leads to shorter time of network unavailability, prompt problem solving, higher availability of services and lower cos ...
... Network management, monitoring and security Implementation of the adequate system for network management is an important factor for achieving this goal. Proactive network management leads to shorter time of network unavailability, prompt problem solving, higher availability of services and lower cos ...
Using CIDR Notation to Determine the Subnet Mask
... The CIDR number is typically preceded by a slash “/” and follows the IP address. For example, an IP address of 131.10.55.70 with a subnet mask of 255.0.0.0 (which has 8 network bits) would be represented as 131.10.55.70 /8. CIDR notation is more concise method for designating the subnet mask. Compar ...
... The CIDR number is typically preceded by a slash “/” and follows the IP address. For example, an IP address of 131.10.55.70 with a subnet mask of 255.0.0.0 (which has 8 network bits) would be represented as 131.10.55.70 /8. CIDR notation is more concise method for designating the subnet mask. Compar ...
Lecture 2 Protocol Layers
... translation - connect different application protocols encrpyption - could be done by a gateway typically implemented in software so that they ...
... translation - connect different application protocols encrpyption - could be done by a gateway typically implemented in software so that they ...
Certified Wireless Network Administrator (CWNA) PW0-105
... capabilities at both the core and edge • Allows for the combined management of the wireless and wired network • Access is no longer defined by the PHY, providing ...
... capabilities at both the core and edge • Allows for the combined management of the wireless and wired network • Access is no longer defined by the PHY, providing ...
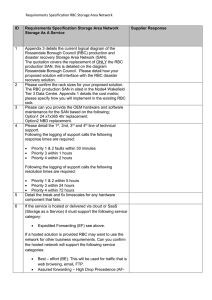
Appendix 2. Requirements Specification RBC Storage Area Network
... to perform the complete set up of any on premise solution. A build plan, configuration list and testing plan including timescales will be required. Disaster Recovery / Business Continuity Management ...
... to perform the complete set up of any on premise solution. A build plan, configuration list and testing plan including timescales will be required. Disaster Recovery / Business Continuity Management ...
Chapter 6
... TCP/IP Internet Layer Protocols • Internet Control Message Protocol (ICMP) is part of the Internet layer and uses IP datagram delivery to send its messages • ICMP uses the basic support of IP as if it was higher-level protocol, but it is actually an integrated part of IP • ICMP is a protocol meant ...
... TCP/IP Internet Layer Protocols • Internet Control Message Protocol (ICMP) is part of the Internet layer and uses IP datagram delivery to send its messages • ICMP uses the basic support of IP as if it was higher-level protocol, but it is actually an integrated part of IP • ICMP is a protocol meant ...
Link
... dest, frame contains A-to-B IP datagram A’s NIC sends frame R’s NIC receives frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get _____’s MAC address R creates frame containing A-to-B IP datagram sends to __ 88-B2-2F-54-1A-0F ...
... dest, frame contains A-to-B IP datagram A’s NIC sends frame R’s NIC receives frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get _____’s MAC address R creates frame containing A-to-B IP datagram sends to __ 88-B2-2F-54-1A-0F ...
CB23474480
... numbers (48-bits) flat address burned into the ROM of the NIC card which is a Layer1 device of the OSI model. This is divided into 24-bit vendor code and 24-bit serial address. This is unique for each system and cannot be changed. In computing, a physical address, also real address, is the memory ad ...
... numbers (48-bits) flat address burned into the ROM of the NIC card which is a Layer1 device of the OSI model. This is divided into 24-bit vendor code and 24-bit serial address. This is unique for each system and cannot be changed. In computing, a physical address, also real address, is the memory ad ...
Export To Word
... 21.14 Verify network connectivity (including: using ping, traceroute, and telnet or SSH). 21.15 Troubleshoot routing issues. 21.16 Verify router hardware and software operation using SHOW & DEBUG commands. 21.17 Implement basic router security. 22.0 Explain and select the appropriate administrative ...
... 21.14 Verify network connectivity (including: using ping, traceroute, and telnet or SSH). 21.15 Troubleshoot routing issues. 21.16 Verify router hardware and software operation using SHOW & DEBUG commands. 21.17 Implement basic router security. 22.0 Explain and select the appropriate administrative ...
Smart Defense Technical White Paper
... The “Ping of Death” is a malformed PING request that some operating systems are unable to correctly process. The attacker sends a fragmented PING request that exceeds the maximum IP packet size (64KB), causing vulnerable systems to crash. SmartDefense blocks this attack even if the checkbox is not s ...
... The “Ping of Death” is a malformed PING request that some operating systems are unable to correctly process. The attacker sends a fragmented PING request that exceeds the maximum IP packet size (64KB), causing vulnerable systems to crash. SmartDefense blocks this attack even if the checkbox is not s ...
Software Architecture Design of Wireless Sensor Networks
... communication between nodes. Therefore the choice of protocols and network configuration are key in terms of network lifespan [1]. Protocol related energy savings are directly related to the physical, link, and network layers [1]. Additional power savings come from an operation system (OS) for the n ...
... communication between nodes. Therefore the choice of protocols and network configuration are key in terms of network lifespan [1]. Protocol related energy savings are directly related to the physical, link, and network layers [1]. Additional power savings come from an operation system (OS) for the n ...
Static Routing
... – 2 types of cables can be used: Straight through and Crossover = RJ45 • Straight through used to connect: – Switch-to-Router, Switch-to-PC, Router-to-Server, Hub-to-PC, Hub-to-Server • Cross-over used to connect: – Switch-to-Switch, PC-to-PC, Switch-to-Hub, Hub-toHub, Router-to-Router, PC-to-Router ...
... – 2 types of cables can be used: Straight through and Crossover = RJ45 • Straight through used to connect: – Switch-to-Router, Switch-to-PC, Router-to-Server, Hub-to-PC, Hub-to-Server • Cross-over used to connect: – Switch-to-Switch, PC-to-PC, Switch-to-Hub, Hub-toHub, Router-to-Router, PC-to-Router ...
Service Set Identification (SSID)
... • Configure the same SSIC on all nodes and the access point • You may also configure DHCP options, filtering, client channels, and more ...
... • Configure the same SSIC on all nodes and the access point • You may also configure DHCP options, filtering, client channels, and more ...
Network Deployment Guide for NovoPRO
... enable this routing feature, devices on the WiFi Hotspot side will be able to access intranet or Internet resources via the LAN connection. Notes on Network Security: before you enable this routing feature, 1) You may consult your organization IT administrators to avoid compromising your network sec ...
... enable this routing feature, devices on the WiFi Hotspot side will be able to access intranet or Internet resources via the LAN connection. Notes on Network Security: before you enable this routing feature, 1) You may consult your organization IT administrators to avoid compromising your network sec ...
Networking for Everyone
... devices that are fully compliant with IEEE 802.11b/g wireless networking standards. SMC’s products integrate seamlessly with cabled ethernet networks and they also serve as stand-alone wireless LANs for small office or home office environments. SMC offers a range of PCMCIA, PCI bus and USB wireless ...
... devices that are fully compliant with IEEE 802.11b/g wireless networking standards. SMC’s products integrate seamlessly with cabled ethernet networks and they also serve as stand-alone wireless LANs for small office or home office environments. SMC offers a range of PCMCIA, PCI bus and USB wireless ...
Chapter 20 IP Datagrams and Datagram Forwarding
... Individual packets travel independently and contains information that identifies the intended recipient A reliable connection-oriented service is added on top of the underlying connectionless service ...
... Individual packets travel independently and contains information that identifies the intended recipient A reliable connection-oriented service is added on top of the underlying connectionless service ...
Performance analysis of a power transmission system under
... paths, the betweenness of a vertex measures how much flow will pass through that particular vertex. In most networks, as in power transmission networks, however, flow does not occur only along geodesic paths; in some cases, flow may not follow the ideal route to get from one place to another, and “w ...
... paths, the betweenness of a vertex measures how much flow will pass through that particular vertex. In most networks, as in power transmission networks, however, flow does not occur only along geodesic paths; in some cases, flow may not follow the ideal route to get from one place to another, and “w ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.