Network
... Examine Network datagrams for addressing and routing Treat Transport segment as meaningless data Computer Networks — Hadassah College — Fall 2015 ...
... Examine Network datagrams for addressing and routing Treat Transport segment as meaningless data Computer Networks — Hadassah College — Fall 2015 ...
Chapter 7 - Home | Georgia State University
... – Messages are delivered between any two nodes in the network, regardless of where they are located ...
... – Messages are delivered between any two nodes in the network, regardless of where they are located ...
GPSR: Greedy Perimeter Stateless Routing for Wireless Networks
... packets for all stations within radio range. At a small cost in bytes (twelve bytes per packet), this scheme allows all packets to serve as beacons. When any node sends a data packet, it can then reset its inter-beacon timer. This optimization reduces beacon traffic in regions of the network activel ...
... packets for all stations within radio range. At a small cost in bytes (twelve bytes per packet), this scheme allows all packets to serve as beacons. When any node sends a data packet, it can then reset its inter-beacon timer. This optimization reduces beacon traffic in regions of the network activel ...
ch01_CE - SaigonTech
... workstations rely on several network servers • Your knowledge of a server’s unique hardware requirements and the many roles it can play in a network is essential to being able to design and support today’s computer networks ...
... workstations rely on several network servers • Your knowledge of a server’s unique hardware requirements and the many roles it can play in a network is essential to being able to design and support today’s computer networks ...
IPv6 Notes - e
... New IPv6 mechanism allows for resource reservation! A router can associate with each datagram a given resource allocation ...
... New IPv6 mechanism allows for resource reservation! A router can associate with each datagram a given resource allocation ...
Why Big Data Needs Big Buffer Switches
... Why would small buffer switches create such a wide range of bandwidth for different flows? The answer to this is inherent in the way TCP/IP works and TCP/IP flows interact when packets are dropped. The TCP/IP protocol relies on ACK packets from the receiver to pace the speed of transmission of packe ...
... Why would small buffer switches create such a wide range of bandwidth for different flows? The answer to this is inherent in the way TCP/IP works and TCP/IP flows interact when packets are dropped. The TCP/IP protocol relies on ACK packets from the receiver to pace the speed of transmission of packe ...
powerpoint [] slides
... Protocol layering and data Each layer takes data from above adds header information to create new data unit passes new data unit to layer below source ...
... Protocol layering and data Each layer takes data from above adds header information to create new data unit passes new data unit to layer below source ...
GPSR: Greedy Perimeter Stateless Routing for Wireless Networks
... packets for all stations within radio range. At a small cost in bytes (twelve bytes per packet), this scheme allows all packets to serve as beacons. When any node sends a data packet, it can then reset its inter-beacon timer. This optimization reduces beacon traffic in regions of the network activel ...
... packets for all stations within radio range. At a small cost in bytes (twelve bytes per packet), this scheme allows all packets to serve as beacons. When any node sends a data packet, it can then reset its inter-beacon timer. This optimization reduces beacon traffic in regions of the network activel ...
Chapter 2
... widespread use of personal computers in homes and businesses. In the mid-1980s users with stand-alone computers started to share files using modems to connect to other computers. This was referred to as point-to-point, or dial-up communication. This concept was expanded by the use of computers that ...
... widespread use of personal computers in homes and businesses. In the mid-1980s users with stand-alone computers started to share files using modems to connect to other computers. This was referred to as point-to-point, or dial-up communication. This concept was expanded by the use of computers that ...
intrusion detection system for manet
... will integrate this technology are police and fire vehicles to communicate with each other for safety purposes. Internet Based Mobile Ad-hoc Networks (iMANET): Internet Based Mobile Ad-hoc Networks are ad-hoc networks that link mobile nodes and fixed Internet-gateway nodes. In such type of networks ...
... will integrate this technology are police and fire vehicles to communicate with each other for safety purposes. Internet Based Mobile Ad-hoc Networks (iMANET): Internet Based Mobile Ad-hoc Networks are ad-hoc networks that link mobile nodes and fixed Internet-gateway nodes. In such type of networks ...
click here
... enable MAC (Media Access Control) filtering. This creates an access control allowing only registered devices to access the wireless network. ...
... enable MAC (Media Access Control) filtering. This creates an access control allowing only registered devices to access the wireless network. ...
Dual Band (2.4 GHz, 5 GHz) Ethernet Bridge/Router, Serial Server
... applications. AirborneM2MTM multi-layered security approach addresses the requirements of Enterprise-class networks and corporate IT departments. These advanced security features include wireless security (801.11i/WPA2 Enterprise); network security (EAP authentication and certificate support); commu ...
... applications. AirborneM2MTM multi-layered security approach addresses the requirements of Enterprise-class networks and corporate IT departments. These advanced security features include wireless security (801.11i/WPA2 Enterprise); network security (EAP authentication and certificate support); commu ...
chapter5d
... In the BGP routing algorithm, each AS advertises to its neighbors its estimates of the shortest distances from the AS to all possible destination ASs. Suppose you computer has been configured with an IP address, and you move (along with your computer) to an office down the hall. If afterwards your c ...
... In the BGP routing algorithm, each AS advertises to its neighbors its estimates of the shortest distances from the AS to all possible destination ASs. Suppose you computer has been configured with an IP address, and you move (along with your computer) to an office down the hall. If afterwards your c ...
Modul 1 - YOKIhack
... • routing table • link state table • ARP table 7 In which of the following tables does the EIGRP DUAL algorithm store the primary route to a destination? (Choose two.) • routing • topology • neighbor • path • shortest path 8 Which of the following are found in the EIGRP neighbor table? (Choose two.) ...
... • routing table • link state table • ARP table 7 In which of the following tables does the EIGRP DUAL algorithm store the primary route to a destination? (Choose two.) • routing • topology • neighbor • path • shortest path 8 Which of the following are found in the EIGRP neighbor table? (Choose two.) ...
3 Assumption on the firewall architecture
... A packet filter is a router designed for filtering packets as they pass between the router's interfaces. A packet filtering router usually can filter IP packets based on the destination and/or source IP addresses and port numbers. This router looks in its configuration files to see if the datagrams ...
... A packet filter is a router designed for filtering packets as they pass between the router's interfaces. A packet filtering router usually can filter IP packets based on the destination and/or source IP addresses and port numbers. This router looks in its configuration files to see if the datagrams ...
1 - Cisco Support Community
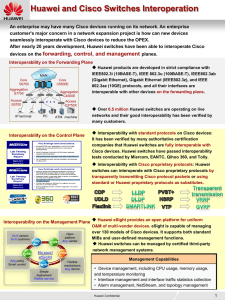
... China Telcom's HQ campus network ODS upgrade project: The gateway originally deployed on Cisco C3560 was moved to the S9300 CSS system newly deployed on the network. The S9300 switches worked as aggregation switches and used CSS technology to improve network reliability. Cisco 3560 and Huawei S9300 ...
... China Telcom's HQ campus network ODS upgrade project: The gateway originally deployed on Cisco C3560 was moved to the S9300 CSS system newly deployed on the network. The S9300 switches worked as aggregation switches and used CSS technology to improve network reliability. Cisco 3560 and Huawei S9300 ...
Europa: Efficient User Mode Packet Forwarding in Network Virtualization
... performance of the platform can closely approach the full potential of the underlying hardware. Achieving both high degree of flexibility and high performance is challenging. To guarantee the isolation between virtual networks so as to provide the flexibility to do customization, both control plane ...
... performance of the platform can closely approach the full potential of the underlying hardware. Achieving both high degree of flexibility and high performance is challenging. To guarantee the isolation between virtual networks so as to provide the flexibility to do customization, both control plane ...
Cisco Router Forensics
... > What can be done in enable engineer mode (Catalyst) ? > Is it possible to upload a modified IOS image and start it without a reboot ? > A lot of different images exists and are in use - what kind of tool would be needed ? > What will happen with IOS-NG (support for loadable modules) ? ...
... > What can be done in enable engineer mode (Catalyst) ? > Is it possible to upload a modified IOS image and start it without a reboot ? > A lot of different images exists and are in use - what kind of tool would be needed ? > What will happen with IOS-NG (support for loadable modules) ? ...
dbtma
... BTMA (Busy Tone Multiple Access, F. A. Tobagi & L. Kleinrock 1975): Using two channels: data channel & control channel A control center - basestation When base station senses the transmission of a terminal, it broadcasts a busy tone signal to all terminals, keeping them (except the current tra ...
... BTMA (Busy Tone Multiple Access, F. A. Tobagi & L. Kleinrock 1975): Using two channels: data channel & control channel A control center - basestation When base station senses the transmission of a terminal, it broadcasts a busy tone signal to all terminals, keeping them (except the current tra ...
Chapter 6 - UniMAP Portal
... Networks Part II: Local Area Networks Overview of LANs Ethernet 802.11 Wireless LAN LAN Bridges ...
... Networks Part II: Local Area Networks Overview of LANs Ethernet 802.11 Wireless LAN LAN Bridges ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.







![powerpoint [] slides](http://s1.studyres.com/store/data/008753039_1-19f22e77ac6be2b6e051d3872ceee1d0-300x300.png)