GPRS - MobiHealth
... – Only used when data are sent or received. – Uses a packet-mode technique to transfer data and signalling in an efficient manner. • GPRS data transfer is based on the Internet Protocol (IP). The packet data transmission is carried out on an end-to-end basis, including the air interface. • GPRS oper ...
... – Only used when data are sent or received. – Uses a packet-mode technique to transfer data and signalling in an efficient manner. • GPRS data transfer is based on the Internet Protocol (IP). The packet data transmission is carried out on an end-to-end basis, including the air interface. • GPRS oper ...
CRLF - Computer and Internet Architecture Laboratory
... – Internet layer protocol – Governs transmission between router and host – Governs transmission between pairs of routers – Gives end-to-end route across many routers ...
... – Internet layer protocol – Governs transmission between router and host – Governs transmission between pairs of routers – Gives end-to-end route across many routers ...
document
... • Contact between two network devices – Communications traverse layered stack in each device – Each layer handles specific tasks – Each layer communicates with next layer using protocol Hands-on Networking Fundamentals ...
... • Contact between two network devices – Communications traverse layered stack in each device – Each layer handles specific tasks – Each layer communicates with next layer using protocol Hands-on Networking Fundamentals ...
hierarchical routing
... Our routing study thus far has been an idealization r all routers identical r network “flat” … not true in practice scale: with 200 million destinations: r ...
... Our routing study thus far has been an idealization r all routers identical r network “flat” … not true in practice scale: with 200 million destinations: r ...
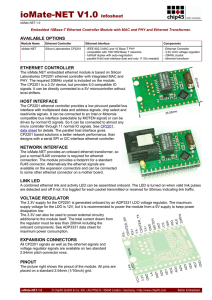
ioMate-NET V1.0 Infosheet
... In this manual are descriptions for copyrighted products that are not explicitly indicated as such. The absence of the trademark (™) and copyright (©) symbols does not imply that a product is not protected. Additionally, registered patents and trademarks are similarly not expressly indicated in this ...
... In this manual are descriptions for copyrighted products that are not explicitly indicated as such. The absence of the trademark (™) and copyright (©) symbols does not imply that a product is not protected. Additionally, registered patents and trademarks are similarly not expressly indicated in this ...
paper
... Abstract—Parallel transmission is a known technique of transmitting flows over multiple paths from a source towards the same destination. In high-speed Ethernet standards, for instance, large bandwidth flows are inverse-multiplexed into multiple lowerspeed flows and transmitted in parallel. However, ...
... Abstract—Parallel transmission is a known technique of transmitting flows over multiple paths from a source towards the same destination. In high-speed Ethernet standards, for instance, large bandwidth flows are inverse-multiplexed into multiple lowerspeed flows and transmitted in parallel. However, ...
Chapter 6 - Towson University
... Replicates some options in all fragments Places some in only one fragment Ex: Recording the datagram route Not all fragments will follow the same route Reassembly would produce conflicting lists Only put in one fragment ...
... Replicates some options in all fragments Places some in only one fragment Ex: Recording the datagram route Not all fragments will follow the same route Reassembly would produce conflicting lists Only put in one fragment ...
Ethernet basics
... • The amount of traffic directly effects the bandwidth utilization of that device. • The bandwidth utilized on the device effects the device’s ability to transmit and receive data in an efficient manner. • Network performance will degrade if too much bandwidth is used because of too much of the wron ...
... • The amount of traffic directly effects the bandwidth utilization of that device. • The bandwidth utilized on the device effects the device’s ability to transmit and receive data in an efficient manner. • Network performance will degrade if too much bandwidth is used because of too much of the wron ...
Basics of network lab - PolyU
... notation with four numbers ranging from 0 to 255 separated by periods. The numbers currently used in IP addresses range from 1.0.0.0 to 255. 255. 255. 255, though some of these values are reserved for specific purposes. The decimals represent Octets of the bits in the binary representation of the IP ...
... notation with four numbers ranging from 0 to 255 separated by periods. The numbers currently used in IP addresses range from 1.0.0.0 to 255. 255. 255. 255, though some of these values are reserved for specific purposes. The decimals represent Octets of the bits in the binary representation of the IP ...
EVOLUTION OF COMPUTER NETWORKS
... data using such links was rather low, hundreds of Kilobits per second (Kbps), the set of services provided by such networks was limited to file transfer, mainly in background mode, and to e-mail. In addition to the low transmission rate, such channels had another drawback they introduced significa ...
... data using such links was rather low, hundreds of Kilobits per second (Kbps), the set of services provided by such networks was limited to file transfer, mainly in background mode, and to e-mail. In addition to the low transmission rate, such channels had another drawback they introduced significa ...
1.01 - BRAUDE
... permitting hosts to send packets into any network and have them travel independently to the destination, potentially on a different network. ...
... permitting hosts to send packets into any network and have them travel independently to the destination, potentially on a different network. ...
Switching Concepts and LAN Design
... • The PCs sense the collision by being unable to deliver the entire frame (coming soon) onto the network. (This is why there are minimum frame lengths along with cable distance and speed limitations. This includes the 5-4-3 rule.) • When a collision occurs, a jamming signal is sent out by the first ...
... • The PCs sense the collision by being unable to deliver the entire frame (coming soon) onto the network. (This is why there are minimum frame lengths along with cable distance and speed limitations. This includes the 5-4-3 rule.) • When a collision occurs, a jamming signal is sent out by the first ...
Home Networking activities in TTC
... Strategic Direction • There are no synthetically Recommendation between WAN, Access, Home-GW, and Intra-HN NW. – QoS – Operation – Connection ...
... Strategic Direction • There are no synthetically Recommendation between WAN, Access, Home-GW, and Intra-HN NW. – QoS – Operation – Connection ...
Overview of the ORBIT Radio Grid Testbed for Evaluation of Next
... support both application/protocol evaluations. These include common libraries for traffic generation, measurement collection etc. and also provide easy hooks to enable "expert" users to develop their own applications, protocol stacks, MAC layer modifications and/or other experiments on the testbed. ...
... support both application/protocol evaluations. These include common libraries for traffic generation, measurement collection etc. and also provide easy hooks to enable "expert" users to develop their own applications, protocol stacks, MAC layer modifications and/or other experiments on the testbed. ...
FO35991995
... protocol is network type flexibility. A packet using DSR routing protocol can reach its destination even when the intermediate nodes are using different type of network. DSR make it possible that nodes with different network types can participate in ad hoc networks, DSR protocol consider them as Ad ...
... protocol is network type flexibility. A packet using DSR routing protocol can reach its destination even when the intermediate nodes are using different type of network. DSR make it possible that nodes with different network types can participate in ad hoc networks, DSR protocol consider them as Ad ...
document
... Autonomous system - group of router exchanging routing info using same routing protocol Area - set of routers and networks that have the same area designation, each router in an area has same info Neighbors - two routers that share a common network, discover and exchange routing info across it Hello ...
... Autonomous system - group of router exchanging routing info using same routing protocol Area - set of routers and networks that have the same area designation, each router in an area has same info Neighbors - two routers that share a common network, discover and exchange routing info across it Hello ...
l2-1 - Heyook Lab
... ISP1 announces one address prefix 128.0.0.0./8 to ISP2 ISP2 can use one routing entry to reach all networks connected to ISP1 ...
... ISP1 announces one address prefix 128.0.0.0./8 to ISP2 ISP2 can use one routing entry to reach all networks connected to ISP1 ...
Capturing and Processing One Million Network Flows Per Second
... • This pipeline is NOT “real time” or even “near real time” • Front end UDP Netflow Router and parallel flowcap processes must keep up without packet drops • No “stock” instrumentation or monitoring for network interface card (NIC), operating system buffers, or collector software • Streaming data re ...
... • This pipeline is NOT “real time” or even “near real time” • Front end UDP Netflow Router and parallel flowcap processes must keep up without packet drops • No “stock” instrumentation or monitoring for network interface card (NIC), operating system buffers, or collector software • Streaming data re ...
18739A-AnonymityProtocols
... • Routing info for each link encrypted with router’s public key • Each router learns only the identity of the next router slide 14 ...
... • Routing info for each link encrypted with router’s public key • Each router learns only the identity of the next router slide 14 ...
IP address of a network
... • Suppose a client requires 800 host addresses • With classful addresses: need to assign a class B address (and waste ~64,700 addresses) or four individual Class Cs (and introducing 4 new routes into the global Internet routing tables) ...
... • Suppose a client requires 800 host addresses • With classful addresses: need to assign a class B address (and waste ~64,700 addresses) or four individual Class Cs (and introducing 4 new routes into the global Internet routing tables) ...
EtherLink 10 Mbps Desktop Network Interface Cards
... Transcend are registered trademarks, and AutoLink, AutoIQ, DynamicAccess, More connected, and PACE are trademarks of 3Com Corporation or its subsidiaries. 3ComFacts is a service mark of 3Com Corporation or its subsidiaries. OS/2 is a trademark of International Business Machines Corporation. LANQuest ...
... Transcend are registered trademarks, and AutoLink, AutoIQ, DynamicAccess, More connected, and PACE are trademarks of 3Com Corporation or its subsidiaries. 3ComFacts is a service mark of 3Com Corporation or its subsidiaries. OS/2 is a trademark of International Business Machines Corporation. LANQuest ...
AV Phoneline Ethernet Bridge
... 1. Plug the supplied telephone cable to the HPNA port of your device and connect it to the phone jack on the wall. If there was a telephone connected to the phone jack on the wall, please connect it to the Phone port of the device. 2. Plug the supplied Ethernet cable to one of the LAN ports of your ...
... 1. Plug the supplied telephone cable to the HPNA port of your device and connect it to the phone jack on the wall. If there was a telephone connected to the phone jack on the wall, please connect it to the Phone port of the device. 2. Plug the supplied Ethernet cable to one of the LAN ports of your ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.