IPv6 network management
... • CISCO-IETF-IP-MIB and CISCO-IETF-IP-FORWARDING-MIB are IPv6 MIBs that are defined as being protocol-independent, but are implemented only for IPv6 objects and tables tables. • In Cisco IOS Release 12.2(33)SRC, IP-MIB and IP-FORWARDMIB were updated to RFC 4293 and RFC 4292 standards • Also, informa ...
... • CISCO-IETF-IP-MIB and CISCO-IETF-IP-FORWARDING-MIB are IPv6 MIBs that are defined as being protocol-independent, but are implemented only for IPv6 objects and tables tables. • In Cisco IOS Release 12.2(33)SRC, IP-MIB and IP-FORWARDMIB were updated to RFC 4293 and RFC 4292 standards • Also, informa ...
Deploying Safe User-Level Network Services with icTCP Abstract {
... thus, TCP backs-off appropriately. The final set of variables (i.e., dupthresh, RTO, and retransmits) control thresholds and timeouts; these variables can be set independently of the original values. For example, both increasing and decreasing dupthresh is believed to be safe [57]. Changing these va ...
... thus, TCP backs-off appropriately. The final set of variables (i.e., dupthresh, RTO, and retransmits) control thresholds and timeouts; these variables can be set independently of the original values. For example, both increasing and decreasing dupthresh is believed to be safe [57]. Changing these va ...
IP: Addresses and Forwarding - RPI ECSE
... Contrast this to “connectionless, best-effort” Internet ...
... Contrast this to “connectionless, best-effort” Internet ...
Network Analysis Module
... This figure shows Cisco Prime NAM’s role as a mediation layer tool—collecting and analyzing network data from a variety of sources and displaying the results on an integrated management and reporting console, for instance, NAM web GUI, and also providing data to Cisco Prime Infrastructure via repres ...
... This figure shows Cisco Prime NAM’s role as a mediation layer tool—collecting and analyzing network data from a variety of sources and displaying the results on an integrated management and reporting console, for instance, NAM web GUI, and also providing data to Cisco Prime Infrastructure via repres ...
document
... The newest wireless standards which has not been ratified yet is 802.11n. It runs on both frequency (2.4GHz and 5.0GHz). D-Link products do support 802.11n standard for both frequencies. The speed for this standard can be up to 300Mbps and provides the ...
... The newest wireless standards which has not been ratified yet is 802.11n. It runs on both frequency (2.4GHz and 5.0GHz). D-Link products do support 802.11n standard for both frequencies. The speed for this standard can be up to 300Mbps and provides the ...
MAC address
... href="http://en.wikipedia.org/wiki/Media_Access_Control">Media Access Controlprotocol sub-layer of the OSI reference model.
... href="http://en.wikipedia.org/wiki/Media_Access_Control">Media Access Controlprotocol sub-layer of the OSI reference model.
MAC addresses are most often assigned by the manu ...
VESR90x Serial Server
... Slim line DIN rail mountable case Accepts DC power over a wide voltage range 10/100 Mbps Ethernet with Auto Selection LAN and WAN Communications TCP Client or Server, or UDP operation - configurable Virtual COM port and Paired Mode capabilities Firmware Upload for future revisions/upgrades Software ...
... Slim line DIN rail mountable case Accepts DC power over a wide voltage range 10/100 Mbps Ethernet with Auto Selection LAN and WAN Communications TCP Client or Server, or UDP operation - configurable Virtual COM port and Paired Mode capabilities Firmware Upload for future revisions/upgrades Software ...
Cross-Domain and Cross-Layer Coarse Grained Quality of
... load and its rising usage for time and loss critical services, such as voice over IP, video streaming and gaming, consists of about 30,000 interconnected service provider networks. Those interconnections are based on the Internet Protocol (IP) and do not distinguish the mixed traffic types within th ...
... load and its rising usage for time and loss critical services, such as voice over IP, video streaming and gaming, consists of about 30,000 interconnected service provider networks. Those interconnections are based on the Internet Protocol (IP) and do not distinguish the mixed traffic types within th ...
Effective communication - Docbox
... Where Smart Grids meet M2M Smart grids needs a reliable and gridwide monitoring infrastructure “Most utilities don't know that users have lost power until customers pick up the phone and call them” WASA: Monitoring and display of power-system components and performance across interconnections ...
... Where Smart Grids meet M2M Smart grids needs a reliable and gridwide monitoring infrastructure “Most utilities don't know that users have lost power until customers pick up the phone and call them” WASA: Monitoring and display of power-system components and performance across interconnections ...
Demystifying Layer 2 and Layer 3 VPNs
... 4.2.16 Less Vulnerable to Internet-Borne Security Threats .......................................................................................................................................................... 35 4.2.17 Multi-Homing for WAN Redundancy.............................................. ...
... 4.2.16 Less Vulnerable to Internet-Borne Security Threats .......................................................................................................................................................... 35 4.2.17 Multi-Homing for WAN Redundancy.............................................. ...
Brocade ICX 7450 Switch Data Sheet
... 7450 switches help deliver continuous availability to optimize the user experience. Brocade stacking technology delivers high availability, performing real-time state synchronization across the stack and enabling instantaneous hitless failover to a standby controller in the unlikely event of a failu ...
... 7450 switches help deliver continuous availability to optimize the user experience. Brocade stacking technology delivers high availability, performing real-time state synchronization across the stack and enabling instantaneous hitless failover to a standby controller in the unlikely event of a failu ...
IP Migration & Activation - P6
... IP addresses are allocated IP backbone is prepared ATM RBS is equipped with CBU There is a slot available for adding an ET-MFX O&M network is prepared for migrating Mub to IP over Ethernet, including configuration in the O&M router – RNC is prepared for IP-based Iub – Network sync server is configur ...
... IP addresses are allocated IP backbone is prepared ATM RBS is equipped with CBU There is a slot available for adding an ET-MFX O&M network is prepared for migrating Mub to IP over Ethernet, including configuration in the O&M router – RNC is prepared for IP-based Iub – Network sync server is configur ...
IBM Networking OS Application Guide for the IBM Flex System
... Configuring SSH/SCP Features on the Switch . . . . Configuring the SCP Administrator Password. . . . . Using SSH and SCP Client Commands . . . . . . . SSH and SCP Encryption of Management Messages . Generating RSA Host and Server Keys for SSH Access SSH/SCP Integration with RADIUS Authentication . . ...
... Configuring SSH/SCP Features on the Switch . . . . Configuring the SCP Administrator Password. . . . . Using SSH and SCP Client Commands . . . . . . . SSH and SCP Encryption of Management Messages . Generating RSA Host and Server Keys for SSH Access SSH/SCP Integration with RADIUS Authentication . . ...
Firewall/VPN PDF
... inside the company network. 7—An employee requests non-web content; the Web Security Service is not involved in the process. You can also enable captive portal over IPsec authentication for on-premise Wi-Fi connections. ...
... inside the company network. 7—An employee requests non-web content; the Web Security Service is not involved in the process. You can also enable captive portal over IPsec authentication for on-premise Wi-Fi connections. ...
Fit AP networking
... On the preceding network, APs function as mesh points (MPs) and are fully-meshed to establish an auto-configured and self-healing wireless mesh network (WMN). APs with the gateway function can work as the mesh portal points (MPPs) through which the WMN can provide access to the Internet. Terminals ...
... On the preceding network, APs function as mesh points (MPs) and are fully-meshed to establish an auto-configured and self-healing wireless mesh network (WMN). APs with the gateway function can work as the mesh portal points (MPPs) through which the WMN can provide access to the Internet. Terminals ...
Sonicwall - Shalimar Infonet
... delivers powerful firewall throughput and 3DES/AES VPN concentration. An upgrade on the PRO 2040, SonicOS Enhanced provides hardware failover, WAN/ISP failover and the ability to fail over to a secondary VPN gateway, ensuring continuous network uptime. Four configurable 10/100 Ethernet interfaces al ...
... delivers powerful firewall throughput and 3DES/AES VPN concentration. An upgrade on the PRO 2040, SonicOS Enhanced provides hardware failover, WAN/ISP failover and the ability to fail over to a secondary VPN gateway, ensuring continuous network uptime. Four configurable 10/100 Ethernet interfaces al ...
Attack Detection and Defense Mechanisms
... The terms and conditions for using this software are described in the software license contained in the acknowledgment to your purchase order or, to the extent applicable, to any reseller agreement or end-user purchase agreement executed between you and Juniper Networks. By using this software, you ...
... The terms and conditions for using this software are described in the software license contained in the acknowledgment to your purchase order or, to the extent applicable, to any reseller agreement or end-user purchase agreement executed between you and Juniper Networks. By using this software, you ...
Commissioning Guide
... methods, login by using the console interface, Telnet, and SSH, are introduced. 2.1 Logging In to the NE80E/40E by Using the Console Interface When setting up a local configuration environment with the console interface being used, you can log in to the NE80E/40E by using the HyperTerminal in Window ...
... methods, login by using the console interface, Telnet, and SSH, are introduced. 2.1 Logging In to the NE80E/40E by Using the Console Interface When setting up a local configuration environment with the console interface being used, you can log in to the NE80E/40E by using the HyperTerminal in Window ...
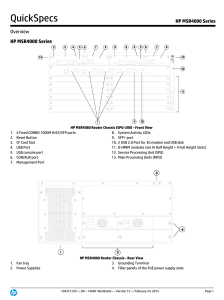
HP MSR4000 Series
... part of the comprehensive HP FlexNetwork architecture. These routers feature a modular design that delivers unmatched application services for extra-large branch offices, headquarters, and campuses. This gives your IT personnel the benefit of reduced complexity, and simplified configuration, deploym ...
... part of the comprehensive HP FlexNetwork architecture. These routers feature a modular design that delivers unmatched application services for extra-large branch offices, headquarters, and campuses. This gives your IT personnel the benefit of reduced complexity, and simplified configuration, deploym ...
slides 3
... – Competing Goals: Memory is expensive – and the amount of interface buffer is not always clear from looking at hardware configurations. Science flows need large buffers to push more data into the network (TCP windows are dependent upon RTT and bottleneck capacity – TCP is bursty). – Read your manua ...
... – Competing Goals: Memory is expensive – and the amount of interface buffer is not always clear from looking at hardware configurations. Science flows need large buffers to push more data into the network (TCP windows are dependent upon RTT and bottleneck capacity – TCP is bursty). – Read your manua ...
wireless mesh networks
... C. E. Perkins, E. M. Belding-Royer, I. D. Chakeres, “Ad hoc OnDemand Distance Vector (AODV) Routing”, IETF Draft, Jan. 2004. ...
... C. E. Perkins, E. M. Belding-Royer, I. D. Chakeres, “Ad hoc OnDemand Distance Vector (AODV) Routing”, IETF Draft, Jan. 2004. ...
TDMoIP : IPR
... if message destination address does not match receiver’s address message ignored (except in promiscuous mode) if message destination address matches receiver’s address message processed ...
... if message destination address does not match receiver’s address message ignored (except in promiscuous mode) if message destination address matches receiver’s address message processed ...
Basic Configuration
... datagram protocol, which means that each packet contains all the information necessary to deliver it to the final destination. The PPP specification defines many Network Control Protocols (NCP) for establishing various network layer protocols. IPX Control Protocol (IPXCP) is one such network control ...
... datagram protocol, which means that each packet contains all the information necessary to deliver it to the final destination. The PPP specification defines many Network Control Protocols (NCP) for establishing various network layer protocols. IPX Control Protocol (IPXCP) is one such network control ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.