User Manual Wireless Controller
... About this User Manual .......................................................................................... 14 ...
... About this User Manual .......................................................................................... 14 ...
VPN-B
... • RD is only used to extend the IP prefix such that overlapping address are unique • Simple VPN topologies require single RD per customer • In some cases multiple RDs may be required ...
... • RD is only used to extend the IP prefix such that overlapping address are unique • Simple VPN topologies require single RD per customer • In some cases multiple RDs may be required ...
Quality of Service in mobile ad hoc networks: a
... Quality of Service (QoS) means that the network should provide some kind of guarantee or assurance about the level or grade of service provided to an application. The actual form of QoS and the QoS parameter to be considered depends upon specific requirements of an application. For example, an applic ...
... Quality of Service (QoS) means that the network should provide some kind of guarantee or assurance about the level or grade of service provided to an application. The actual form of QoS and the QoS parameter to be considered depends upon specific requirements of an application. For example, an applic ...
Introduction to VLANs
... not have the destination MAC address in its source address table. This can be especially true for large flat networks where switches cannot contain all of the MAC addresses. – MAC address table can be 1,024 (or less) and more than 16,000 addresses depending upon vendor and model Addresses will also ...
... not have the destination MAC address in its source address table. This can be especially true for large flat networks where switches cannot contain all of the MAC addresses. – MAC address table can be 1,024 (or less) and more than 16,000 addresses depending upon vendor and model Addresses will also ...
IPv6 at Monash University
... It's just not evenly distributed. - Apologies to William Gibson • First IPv6 RFCs in 1996 • Monash has had native IPv6 since 2003 • Windows Vista, Mac OS X, Linux already come with IPv6 enabled • Some Web sites are now IPv6 enabled – On 23-Jan-2009, Google enable AAAA DNS replies for uses on AARNet ...
... It's just not evenly distributed. - Apologies to William Gibson • First IPv6 RFCs in 1996 • Monash has had native IPv6 since 2003 • Windows Vista, Mac OS X, Linux already come with IPv6 enabled • Some Web sites are now IPv6 enabled – On 23-Jan-2009, Google enable AAAA DNS replies for uses on AARNet ...
Aalborg Universitet Adaptive Capacity Management in Bluetooth Networks Son, L.T.
... cost VLSI device evolution, short range wireless communications have become more and more popular, especially Bluetooth. Bluetooth is a new short range radio technology that promises to be very convenient, low power, and low cost mobile ad hoc solution for the global interconnection of all mobile de ...
... cost VLSI device evolution, short range wireless communications have become more and more popular, especially Bluetooth. Bluetooth is a new short range radio technology that promises to be very convenient, low power, and low cost mobile ad hoc solution for the global interconnection of all mobile de ...
Introduction to IPv6
... IPv6 can offer new opportunities as it eliminates NAT: Example: AJAX applications, Multimedia. You would need to give IPv6 Support to Software that runs on top of IP or that handle IP addresses. Example: ODBC, JDBC drivers upgrade, Database tables, log. ...
... IPv6 can offer new opportunities as it eliminates NAT: Example: AJAX applications, Multimedia. You would need to give IPv6 Support to Software that runs on top of IP or that handle IP addresses. Example: ODBC, JDBC drivers upgrade, Database tables, log. ...
Serial Server Installation Guide
... terminal protocol, supported on most UNIX systems, is an easy-touse interface that creates terminal connections to any network host supporting Telnet. Rlogin is a protocol that allows users to initiate a TCP/IP login session. UDP (User Datagram Protocol) is a connectionless protocol that results in ...
... terminal protocol, supported on most UNIX systems, is an easy-touse interface that creates terminal connections to any network host supporting Telnet. Rlogin is a protocol that allows users to initiate a TCP/IP login session. UDP (User Datagram Protocol) is a connectionless protocol that results in ...
Host-to-host congestion control for TCP
... control for networks with high levels of packet reordering), Low et al. [8] (current up to 2002 TCP variants and their analytical models), Hasegawa and Murata [9] (fairness issues in congestion control), and others researchers. Unlike previous studies, in this survey we tried to collect, classify, a ...
... control for networks with high levels of packet reordering), Low et al. [8] (current up to 2002 TCP variants and their analytical models), Hasegawa and Murata [9] (fairness issues in congestion control), and others researchers. Unlike previous studies, in this survey we tried to collect, classify, a ...
IP Multicasting: Concepts, Algorithms, and Protocols
... which a host needs to find out whether a certain type of service is available or not. Internet protocols such as Bootstrap Protocol (BOOTP) and Open Shortest path First (OSPF) protocol are among these applications. Using multicast messages and sending the query to those hosts which are potentially c ...
... which a host needs to find out whether a certain type of service is available or not. Internet protocols such as Bootstrap Protocol (BOOTP) and Open Shortest path First (OSPF) protocol are among these applications. Using multicast messages and sending the query to those hosts which are potentially c ...
Analysis of Reliable Multicast Protocols
... 13 : The host is unreachable because the administrator has put a filter on it 14 : The host is unreachable because the host precedence is violated 15 : The host is unreachable because the host precedence was cut off ...
... 13 : The host is unreachable because the administrator has put a filter on it 14 : The host is unreachable because the host precedence is violated 15 : The host is unreachable because the host precedence was cut off ...
SwitchPlusIP Advanced Maintenance Training Presentation
... - In this situation, should any piece of equipment’s connection to a switch fail, its resources are not lost as it will still have a network connection. Audio may be lost temporarily as the equipment switches from using LAN A to LAN B. The impact is minimal. Note that in order to maintain a dual-red ...
... - In this situation, should any piece of equipment’s connection to a switch fail, its resources are not lost as it will still have a network connection. Audio may be lost temporarily as the equipment switches from using LAN A to LAN B. The impact is minimal. Note that in order to maintain a dual-red ...
What Is a Virtual Private Network?
... The Secure Sockets Layer (SSL)—SSL is a security protocol that was originally developed by Netscape Communications (SSL versions 1, 2, and 3), and it provides secure remote access for mobile users or home users. Functionality may be limited (when compared with L2F, PPTP, L2TPv2, or IPsec) if clientl ...
... The Secure Sockets Layer (SSL)—SSL is a security protocol that was originally developed by Netscape Communications (SSL versions 1, 2, and 3), and it provides secure remote access for mobile users or home users. Functionality may be limited (when compared with L2F, PPTP, L2TPv2, or IPsec) if clientl ...
Configuring VoIP for SonicOS Enhanced
... VoIP encompasses a number of complex standards that leave the door open for bugs and vulnerabilities within the software implementation. The same types of bugs and vulnerabilities that hamper every operating system and application available today also apply to VoIP equipment. Many of today's VoIP ca ...
... VoIP encompasses a number of complex standards that leave the door open for bugs and vulnerabilities within the software implementation. The same types of bugs and vulnerabilities that hamper every operating system and application available today also apply to VoIP equipment. Many of today's VoIP ca ...
The Java and Jini Technologies for Distance Education in
... Policy is that an ISP allocates a /48 prefix to each end customer ...
... Policy is that an ISP allocates a /48 prefix to each end customer ...
Top-Down Network Design
... All terms mentioned in this book that are known to be trademarks or service marks have been appropriately capitalized. Cisco Press or Cisco Systems, Inc., cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark o ...
... All terms mentioned in this book that are known to be trademarks or service marks have been appropriately capitalized. Cisco Press or Cisco Systems, Inc., cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark o ...
for DOS and Windows 3.x
... Before reading the installation instructions for your operating system, get the following information from your network administrator: User name and password The client must have a user name and password for security authentication. If the Perle 833 is configured for a third party security service, ...
... Before reading the installation instructions for your operating system, get the following information from your network administrator: User name and password The client must have a user name and password for security authentication. If the Perle 833 is configured for a third party security service, ...
General Information - HauteSpot Networks
... 802.1q Trunk extension over Wireless P2P Link ...................................................................................................................76 Access and bandwidth limitation ........................................................................................................ ...
... 802.1q Trunk extension over Wireless P2P Link ...................................................................................................................76 Access and bandwidth limitation ........................................................................................................ ...
Configuring VoIP for SonicOS Standard
... VoIP encompasses a number of complex standards that leave the door open for bugs and vulnerabilities within the software implementation. The same types of bugs and vulnerabilities that hamper every operating system and application available today also apply to VoIP equipment. Many of today's VoIP ca ...
... VoIP encompasses a number of complex standards that leave the door open for bugs and vulnerabilities within the software implementation. The same types of bugs and vulnerabilities that hamper every operating system and application available today also apply to VoIP equipment. Many of today's VoIP ca ...
HPE 3800 Switch Series data sheet
... Provides OSPFv2 for IPv4 routing and OSPFv3 for IPv6 routing • Policy-based routing Makes routing decisions based on policies set by the network administrator • IPv4 border gateway routing protocol Is scalable, robust, and flexible Security • NEW Private VLAN Provides network security by restricting ...
... Provides OSPFv2 for IPv4 routing and OSPFv3 for IPv6 routing • Policy-based routing Makes routing decisions based on policies set by the network administrator • IPv4 border gateway routing protocol Is scalable, robust, and flexible Security • NEW Private VLAN Provides network security by restricting ...
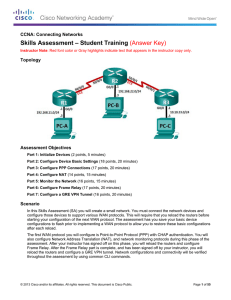
Skills Assessment – Student Training (Answer Key)
... Instructor Note: Sample scoring and estimated times for each exam part are provided. These can be adjusted by the instructor as necessary to suit the testing environment. Total points for the exam are 100 and total time is estimated at 115 minutes. The instructor may elect to deduct points if excess ...
... Instructor Note: Sample scoring and estimated times for each exam part are provided. These can be adjusted by the instructor as necessary to suit the testing environment. Total points for the exam are 100 and total time is estimated at 115 minutes. The instructor may elect to deduct points if excess ...
Contents - Heliodyne
... another commercially-available surge protector, be sure that the device is marked as a surge protector or surge suppressor. It is not required that the device include a circuit breaker or an ON / OFF switch. Note that hardware stores provide 6-way outlets with circuit breakers that do not provide su ...
... another commercially-available surge protector, be sure that the device is marked as a surge protector or surge suppressor. It is not required that the device include a circuit breaker or an ON / OFF switch. Note that hardware stores provide 6-way outlets with circuit breakers that do not provide su ...
Overview of Provider Backbone Bridging and Integration
... providers and integration with virtual private LAN service (VPLS) are discussed. Interoperability scenarios of PBB with VPLS are covered with emphasis on how the combined solution addresses existing challenges in VPLS. ...
... providers and integration with virtual private LAN service (VPLS) are discussed. Interoperability scenarios of PBB with VPLS are covered with emphasis on how the combined solution addresses existing challenges in VPLS. ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.