Week 5
... dest. network unreachable dest host unreachable dest protocol unreachable dest port unreachable dest network unknown dest host unknown source quench (congestion control - not used) ...
... dest. network unreachable dest host unreachable dest protocol unreachable dest port unreachable dest network unknown dest host unknown source quench (congestion control - not used) ...
Introduction - Suraj @ LUMS
... 1. To arrange or place (troops, for example) in line for a parade, maneuver, or review. 2. To arrange, place, or set in methodical order. 3. To enlist and organize. 4. To guide ceremoniously; conduct or usher. ...
... 1. To arrange or place (troops, for example) in line for a parade, maneuver, or review. 2. To arrange, place, or set in methodical order. 3. To enlist and organize. 4. To guide ceremoniously; conduct or usher. ...
LTEC 4550 Assignement 3
... efficient as several kilometers for fiber optic. A typical, small 4-5 port unmanaged hub costs between $10 – $20. The range is dependent on the type and speed of the needed install application. Historically, the main reason for purchasing hubs rather than switches was their price. This motivator has ...
... efficient as several kilometers for fiber optic. A typical, small 4-5 port unmanaged hub costs between $10 – $20. The range is dependent on the type and speed of the needed install application. Historically, the main reason for purchasing hubs rather than switches was their price. This motivator has ...
Network Interface Cards - Stanford Secure Computer Systems Group
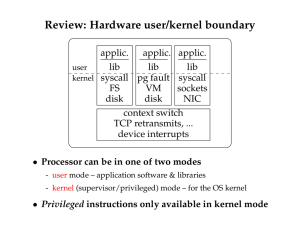
... Socket implementation: buffering • Need to be able to encapsulate data easily - E.g., add UDP header to data - Add IP header to UDP packet - Add Ethernet header to IP packet ...
... Socket implementation: buffering • Need to be able to encapsulate data easily - E.g., add UDP header to data - Add IP header to UDP packet - Add Ethernet header to IP packet ...
01_NF_CH07_DataLinkLayer
... Data Link Layer – Connecting Upper Layer Services to the Media The two common LAN sublayers are: Logical Link Control - Logical Link Control (LLC) places information in the frame that identifies which Network layer protocol is being used for the frame. This information allows multiple Layer 3 pro ...
... Data Link Layer – Connecting Upper Layer Services to the Media The two common LAN sublayers are: Logical Link Control - Logical Link Control (LLC) places information in the frame that identifies which Network layer protocol is being used for the frame. This information allows multiple Layer 3 pro ...
Q and A slides
... that “IP is designed to run over any type of network”? And, how is IP “best-effort”? A: It means that IP was designed to operate over networks that provide few guarantees. It does not require absolutely perfect, fast, robust layer 2 hardware/protocols. It just requires that the lower layer do its be ...
... that “IP is designed to run over any type of network”? And, how is IP “best-effort”? A: It means that IP was designed to operate over networks that provide few guarantees. It does not require absolutely perfect, fast, robust layer 2 hardware/protocols. It just requires that the lower layer do its be ...
IEEE C802.16ppc-10/0055r1 Project Title
... transmitting short bursts of data for intermittent and delay tolerant traffic. In particular, it assumes that most devices present in the network will be in the idle state, due to a variety of reasons such as a) limited address space for supporting a large number of simultaneously active connections ...
... transmitting short bursts of data for intermittent and delay tolerant traffic. In particular, it assumes that most devices present in the network will be in the idle state, due to a variety of reasons such as a) limited address space for supporting a large number of simultaneously active connections ...
Slide 1
... The mission of Layer 3 is to transport the packets between the hosts while placing as little burden on the network as possible. Speed over reliability Layer 3 is not concerned with or even aware of the type of data contained inside of a packet. This responsibility is the role of the upper la ...
... The mission of Layer 3 is to transport the packets between the hosts while placing as little burden on the network as possible. Speed over reliability Layer 3 is not concerned with or even aware of the type of data contained inside of a packet. This responsibility is the role of the upper la ...
Ch.10 - Emerging Wireless Networks
... - Operates at layer 1, thus is independent of any protocols and can support Ethernet or any other higher-level protocols - Requires clear line of sight between the source and the destination ...
... - Operates at layer 1, thus is independent of any protocols and can support Ethernet or any other higher-level protocols - Requires clear line of sight between the source and the destination ...
homework - Kendriya Vidyalaya Dhanpuri
... Switches : Switches are smart hubs that send data directly to the destination rather than everywhere within network. When the switch receive a packet, the switch examines the destination and source hardware address and compare them to a table of a network segments and addresses. If the segments are ...
... Switches : Switches are smart hubs that send data directly to the destination rather than everywhere within network. When the switch receive a packet, the switch examines the destination and source hardware address and compare them to a table of a network segments and addresses. If the segments are ...
Albanian Mine Action Executive
... data entered into the IMSMA FM are analyzed in a graphical environment. IMSMA GIS receives mine action data from the IMSMA FM database and provides a geographical (map) view of the data. The IMSMA GIS is a very powerful tool for quality control of data entry into the IMSMA FM, preparing task dossier ...
... data entered into the IMSMA FM are analyzed in a graphical environment. IMSMA GIS receives mine action data from the IMSMA FM database and provides a geographical (map) view of the data. The IMSMA GIS is a very powerful tool for quality control of data entry into the IMSMA FM, preparing task dossier ...
Follow this link to Network
... 4. Cell switching is sometimes considered as a special packet switching method. Like with packet switching, cell switching requires that the data to be transmitted is broken into data packets, but these packets are of a fixed, small size, the cells. Because cells are fixed- length, they can be proc ...
... 4. Cell switching is sometimes considered as a special packet switching method. Like with packet switching, cell switching requires that the data to be transmitted is broken into data packets, but these packets are of a fixed, small size, the cells. Because cells are fixed- length, they can be proc ...
extra file - TNC16
... circuit between Los Angeles and Tokyo. A second set of passive data can be acquired by means of packet header inspection tools that examine the headers of a network flow and pulls out valuable data from them, without touching the payload of the message. Initially, the NetSage project studied the pos ...
... circuit between Los Angeles and Tokyo. A second set of passive data can be acquired by means of packet header inspection tools that examine the headers of a network flow and pulls out valuable data from them, without touching the payload of the message. Initially, the NetSage project studied the pos ...
EEE521 - Universiti Sains Malaysia
... Q8: Which 2 statements are TRUE for the datagrams processed by the network layer protocol A: Datagrams are checked for errors and corrupted datagrams are corrected B: Datagrams can travel through different routes inside the interconnection of multiple networks C: Datagrams may arrive out of sequenc ...
... Q8: Which 2 statements are TRUE for the datagrams processed by the network layer protocol A: Datagrams are checked for errors and corrupted datagrams are corrected B: Datagrams can travel through different routes inside the interconnection of multiple networks C: Datagrams may arrive out of sequenc ...
PPT - Computer Science and Engineering
... Networks are Complex! • Many “pieces”: – Hosts – Routers – Links of various media – Applications – Protocols – Hardware, software ...
... Networks are Complex! • Many “pieces”: – Hosts – Routers – Links of various media – Applications – Protocols – Hardware, software ...
A Web-Based Data Mining Application for the Contraceptive Method
... – A and B are dependent on each other if we know something about C or D (or both). – A and C are dependent on each other no matter what we know and what we don't know about B or D (or both). – B and C are dependent on each other no matter what we know and what we don't know about A or D (or both). – ...
... – A and B are dependent on each other if we know something about C or D (or both). – A and C are dependent on each other no matter what we know and what we don't know about B or D (or both). – B and C are dependent on each other no matter what we know and what we don't know about A or D (or both). – ...
Sensor Networks
... An array of sensors networked to communicate and share information about the data that they are collecting Sensor field ...
... An array of sensors networked to communicate and share information about the data that they are collecting Sensor field ...
SEMESTER 1 Chapter 5
... o The representation of how the media is used to interconnect the devices is the physical topology. A logical topology is the way a network transfers frames from one node to the next. This arrangement consists of virtual connections between the nodes of a network independent of their physical layo ...
... o The representation of how the media is used to interconnect the devices is the physical topology. A logical topology is the way a network transfers frames from one node to the next. This arrangement consists of virtual connections between the nodes of a network independent of their physical layo ...
Qualitative and Quantitative Evaluation of A Proposed Circuit
... bursty traffic pattern such multimedia. Packet switching typically requires large buffer resources at network nodes to ease traffic congestion. This buffer requirement can be reduced via properly designed and selected routing schemes. Circuit switching does not require any buffer, thus consumes less ...
... bursty traffic pattern such multimedia. Packet switching typically requires large buffer resources at network nodes to ease traffic congestion. This buffer requirement can be reduced via properly designed and selected routing schemes. Circuit switching does not require any buffer, thus consumes less ...
Lecture18 - Philadelphia University
... • Environmental applications: forest fire detection, biocomplexity mapping of the environment, greenhouses monitoring and control, flood detection, alarming and control, weather forecasting and others. • Health applications: monitoring of human physiological data, monitoring and tracking patients an ...
... • Environmental applications: forest fire detection, biocomplexity mapping of the environment, greenhouses monitoring and control, flood detection, alarming and control, weather forecasting and others. • Health applications: monitoring of human physiological data, monitoring and tracking patients an ...
ICN lecture1 - OSI & TCP_IP
... protocols in the telecoms world. All telecommunications technologies are underpinned by protocols that should be recognised internationally managed by established standards bodies. A protocol has three aspects: Syntax ...
... protocols in the telecoms world. All telecommunications technologies are underpinned by protocols that should be recognised internationally managed by established standards bodies. A protocol has three aspects: Syntax ...