Metro WDM Networks: Performance Comparison of , Senior Member, IEEE
... We note that with the control channel approach there is an additional wavelength channel for control on each fiber, for a comwavelength channels in the single-fiber ring bined total of network and wavelength channels in the dual-fiber ring network. In addition, there is a fixed-tuned transceiver (FT ...
... We note that with the control channel approach there is an additional wavelength channel for control on each fiber, for a comwavelength channels in the single-fiber ring bined total of network and wavelength channels in the dual-fiber ring network. In addition, there is a fixed-tuned transceiver (FT ...
Convergence Rates of Distributed Average Consensus With
... computing the second order statistics of the variance of the deviation from average, and we use these methods to study the behavior of various network examples as a function of link failure probability. Although there has been work that gives conditions for convergence with communication failures, t ...
... computing the second order statistics of the variance of the deviation from average, and we use these methods to study the behavior of various network examples as a function of link failure probability. Although there has been work that gives conditions for convergence with communication failures, t ...
Text String Activation
... For single Message Center connection use RS232 wiring method. For multiple Message Center operation use RS485 wiring method. A PLC can be used to send a complete message to one or more Message Centers. Or the PLC can activate a previously loaded message in one or more Message Centers. A PLC can be u ...
... For single Message Center connection use RS232 wiring method. For multiple Message Center operation use RS485 wiring method. A PLC can be used to send a complete message to one or more Message Centers. Or the PLC can activate a previously loaded message in one or more Message Centers. A PLC can be u ...
Hughes 9502 BGAN Terminal & Service
... is defined as having an active PDP context but the UE has already transitioned back to the regional beam due to 90 seconds of data inactivity. In idle mode the UE is still accessible by IP traffic from the network. • There are two ways to put the UE into an “Off” state for even more power savings: • ...
... is defined as having an active PDP context but the UE has already transitioned back to the regional beam due to 90 seconds of data inactivity. In idle mode the UE is still accessible by IP traffic from the network. • There are two ways to put the UE into an “Off” state for even more power savings: • ...
Real-time communication protocols: an overview
... network using the CSMA/CD (Carrier Sense Multiple Access with Collision Detect) technique [70]. The CSMA/CD algorithm does not define a collision resolvance protocol of its own. Ethernet uses the BEB (Binary Exponential Back-Off) algorithm. This algorithm resolves collisions in a non-deterministic m ...
... network using the CSMA/CD (Carrier Sense Multiple Access with Collision Detect) technique [70]. The CSMA/CD algorithm does not define a collision resolvance protocol of its own. Ethernet uses the BEB (Binary Exponential Back-Off) algorithm. This algorithm resolves collisions in a non-deterministic m ...
NSF_Vehicles_and_Internet_role-jan_16_Claudio
... Vehicle communications are becoming increasingly popular, propelled by navigation safety requirements and by the investments of car manufacturers and Public Transport Authorities. As a consequence many of the essential vehicle grid components (radios, Access Points, spectrum, standards, etc.) will s ...
... Vehicle communications are becoming increasingly popular, propelled by navigation safety requirements and by the investments of car manufacturers and Public Transport Authorities. As a consequence many of the essential vehicle grid components (radios, Access Points, spectrum, standards, etc.) will s ...
ECE 467 Network Implementation Lab Manual
... List of Figures Figure 1 OSI layer communication............................................................................................... 12 Figure 2 RJ-48C cross-over .......................................................................................................... 21 Figure 3 RJ-45 ...
... List of Figures Figure 1 OSI layer communication............................................................................................... 12 Figure 2 RJ-48C cross-over .......................................................................................................... 21 Figure 3 RJ-45 ...
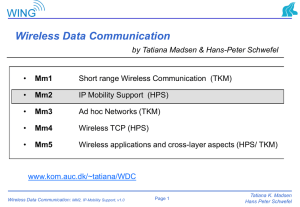
Wireless Data Communication
... • IP-in-IP-encapsulation (support in MIP mandatory, RFC 2003) – tunnel between HA and COA ...
... • IP-in-IP-encapsulation (support in MIP mandatory, RFC 2003) – tunnel between HA and COA ...
ALCATEL 4400
... integrated compression. This is the right way to reduce costs and increase availability. Full VPN architectures require only one permanent low speed connection for signalling. The whole voice traffic is handled by public switched digital connections with or without integrated compression. ● Complian ...
... integrated compression. This is the right way to reduce costs and increase availability. Full VPN architectures require only one permanent low speed connection for signalling. The whole voice traffic is handled by public switched digital connections with or without integrated compression. ● Complian ...
Networks09
... Efficient, less expensive, and reliable Will function if part of the network is down ...
... Efficient, less expensive, and reliable Will function if part of the network is down ...
Solving the Jumbo Frame Challenge
... Applications Driving the Need for Larger Packets Today, the sales of Gigabit Ethernet ports have now surpassed Fast Ethernet. The wide adoption of Gigabit Ethernet has enabled several new applications driving the need for wire-speed, jumbo-frame processing. While the speed of links and processing c ...
... Applications Driving the Need for Larger Packets Today, the sales of Gigabit Ethernet ports have now surpassed Fast Ethernet. The wide adoption of Gigabit Ethernet has enabled several new applications driving the need for wire-speed, jumbo-frame processing. While the speed of links and processing c ...
pdf - AstroGrid-D
... – VObs aims to enable external users to use resources – Heterogeneous world: Interoperate with resources outside of AstroGrid-D (but within IVOA standards) ...
... – VObs aims to enable external users to use resources – Heterogeneous world: Interoperate with resources outside of AstroGrid-D (but within IVOA standards) ...
Lecture 1: Course Introduction and Overview
... – Packet discarding: If packet arrives at switch and no room in buffer, packet is discarded (e.g., UDP) – Flow control: between pairs of receivers and senders; use feedback to tell sender when allowed to send next packet » Back-pressure: separate wires to tell to stop » Window: give original sender ...
... – Packet discarding: If packet arrives at switch and no room in buffer, packet is discarded (e.g., UDP) – Flow control: between pairs of receivers and senders; use feedback to tell sender when allowed to send next packet » Back-pressure: separate wires to tell to stop » Window: give original sender ...
Controller
... • Change the egress VLAN of the frame • Change the original Smac of the frame • Change the original Dmac of the frame ...
... • Change the egress VLAN of the frame • Change the original Smac of the frame • Change the original Dmac of the frame ...
Link Layer
... o seldom used on low bit error link (fiber, some twisted pair) o wireless links: high error rates • Q: why both link-level and end-end reliability? ...
... o seldom used on low bit error link (fiber, some twisted pair) o wireless links: high error rates • Q: why both link-level and end-end reliability? ...
WLAN Site Surveys and Security Considerations
... for Port Based Network Access Control” 802.1x applies to wired and wireless networks 802.1x defines methods for authentication and key distribution plus other things 802.1x is usable with currently standardized authentication/key distribution schemes (i.e. - RADIUS/ Kerberos) 802.1x is a wor ...
... for Port Based Network Access Control” 802.1x applies to wired and wireless networks 802.1x defines methods for authentication and key distribution plus other things 802.1x is usable with currently standardized authentication/key distribution schemes (i.e. - RADIUS/ Kerberos) 802.1x is a wor ...
Chapter 10: Circuit Switching and Packet Switching Switching
... • Long distance transmission is typically done over a network of switched nodes • Nodes not concerned with content of data • End devices are stations ...
... • Long distance transmission is typically done over a network of switched nodes • Nodes not concerned with content of data • End devices are stations ...
routing101
... - a) determine whether to forward the packet at all, and - b) which port(s) to forward the packet to. Filtering makes the network operation more efficient by reducing the number of “output ports” to which the packet needs to be sent to. For example: - Unicast packets need to go to only one output po ...
... - a) determine whether to forward the packet at all, and - b) which port(s) to forward the packet to. Filtering makes the network operation more efficient by reducing the number of “output ports” to which the packet needs to be sent to. For example: - Unicast packets need to go to only one output po ...
EURESCOM - SALTAMONTES
... same manner (over the same path with the same forwarding treatment) Characteristics: Set of IP packets Is eventually encoded as the label Is not a route or path. However, packets in a FEC and originating at a given point follow a route (or one set of routes) FEC gives greater control over ...
... same manner (over the same path with the same forwarding treatment) Characteristics: Set of IP packets Is eventually encoded as the label Is not a route or path. However, packets in a FEC and originating at a given point follow a route (or one set of routes) FEC gives greater control over ...