IPO-10
... Customers contract for specific set network resources such as link bandwidth, wavelength, and/or optical connection ports. Closed User Group (CUS) and virtual network Optical connection can be based on signaled or static provisioning Customer may have limited visibility and control of contra ...
... Customers contract for specific set network resources such as link bandwidth, wavelength, and/or optical connection ports. Closed User Group (CUS) and virtual network Optical connection can be based on signaled or static provisioning Customer may have limited visibility and control of contra ...
15-744: Computer Networking
... • The Network Security Monitor developed at the University of California Davis was the first IDS to work directly with network data as opposed to log data • Essentially a packet sniffer feeding data to an analysis engine ...
... • The Network Security Monitor developed at the University of California Davis was the first IDS to work directly with network data as opposed to log data • Essentially a packet sniffer feeding data to an analysis engine ...
Development of DNS
... DNS (mistakes learnt on a usability engineering POV) • People who use your product are going to abuse it (play outside the boundaries) – bad inputs – Laziness – If it works – fail to optimize - System designers should anticipate that maintainers and administrators will only do the least possible to ...
... DNS (mistakes learnt on a usability engineering POV) • People who use your product are going to abuse it (play outside the boundaries) – bad inputs – Laziness – If it works – fail to optimize - System designers should anticipate that maintainers and administrators will only do the least possible to ...
Trust Based Algorithm for Candidate Node Selection in Hybrid
... rithms are based on link state algorithm for the unconstrained selection based on the Dijkstra algorithm [7]. Fig. 2: Trust computation models for hybrid MANET-DTN. Most methods are based on generalizing the BellmanFord algorithm and they prove its optimality [8], [9]. In this article the trust base ...
... rithms are based on link state algorithm for the unconstrained selection based on the Dijkstra algorithm [7]. Fig. 2: Trust computation models for hybrid MANET-DTN. Most methods are based on generalizing the BellmanFord algorithm and they prove its optimality [8], [9]. In this article the trust base ...
a security survey of authenticated routing protocol (aran)
... E. Byzantine robustness:It should be able tofunction properly even if some participating nodes inrouting are intentionally obstructing its operation. Byzantinerobustness can be thought as self-stabilizationproperty’s severe version. The routing protocol must not onlyautomatically recuperate from an ...
... E. Byzantine robustness:It should be able tofunction properly even if some participating nodes inrouting are intentionally obstructing its operation. Byzantinerobustness can be thought as self-stabilizationproperty’s severe version. The routing protocol must not onlyautomatically recuperate from an ...
Routing Information Protocol 2 (RIP2)
... authentication, CIDR aggregation, route tags and multicast transmission Subnet support: RIPv1 supports subnet routes only within the subnet network while RIPv2 includes subnet mask in the messages. This allows for subnet knowledge outside subnet. More convenient partitioning using variable length su ...
... authentication, CIDR aggregation, route tags and multicast transmission Subnet support: RIPv1 supports subnet routes only within the subnet network while RIPv2 includes subnet mask in the messages. This allows for subnet knowledge outside subnet. More convenient partitioning using variable length su ...
web.cs.sunyit.edu
... – Cutting off group from rest of network • Correct by using router or Layer 3 switch ...
... – Cutting off group from rest of network • Correct by using router or Layer 3 switch ...
Understanding Computers, Chapter 7
... for wired LANs – Typically used a bus or star topology and twistedpair, coaxial, or fiber-optic cables – Original (10Base-T) Ethernet networks run at 10 ...
... for wired LANs – Typically used a bus or star topology and twistedpair, coaxial, or fiber-optic cables – Original (10Base-T) Ethernet networks run at 10 ...
Lecture 1: Course Introduction and Overview
... full packet to arrive in switch before sending to the next switch (good for WAN) • Cut-through routing or worm hole routing: switch examines the header, decides where to send the message, and then starts forwarding it immediately – In worm hole routing, when head of message is blocked, message stays ...
... full packet to arrive in switch before sending to the next switch (good for WAN) • Cut-through routing or worm hole routing: switch examines the header, decides where to send the message, and then starts forwarding it immediately – In worm hole routing, when head of message is blocked, message stays ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... nodes and then each node independently calculates the next best logical path from it to every possible destination in the network. The collection of best paths will then form the node's routing table [1]. The OSPF protocol is based on the short path first algorithm known as class inter domain routin ...
... nodes and then each node independently calculates the next best logical path from it to every possible destination in the network. The collection of best paths will then form the node's routing table [1]. The OSPF protocol is based on the short path first algorithm known as class inter domain routin ...
例外(exception)とは何か
... Motivation for Change from IPv4 to IPv6 - Current version of IPv4 - is more than 30 years old - IPv4 has shown remarkable success !!! - Then why change? Address space - 32 bit address space allows for over a million networks - But...most are Class C and too small for many organizations - 214 = 163 ...
... Motivation for Change from IPv4 to IPv6 - Current version of IPv4 - is more than 30 years old - IPv4 has shown remarkable success !!! - Then why change? Address space - 32 bit address space allows for over a million networks - But...most are Class C and too small for many organizations - 214 = 163 ...
High-Performance Object Access in OSD Storage Subsystem
... Programming abstract: VI(queue pair) Components: consumer,VI ...
... Programming abstract: VI(queue pair) Components: consumer,VI ...
- IEEE Mentor
... duration of QP for a given BS varies over time and follows Normal distribution with mean value of 3 and standard deviation of 2. The changes of QP are independent among BSs and the interval follows an exponential distribution with mean value of 60 seconds. We set the values of Intra-frame Sensing Cy ...
... duration of QP for a given BS varies over time and follows Normal distribution with mean value of 3 and standard deviation of 2. The changes of QP are independent among BSs and the interval follows an exponential distribution with mean value of 60 seconds. We set the values of Intra-frame Sensing Cy ...
cs2307-computer networks lab manual
... What is more important to gaming applications is the prompt delivery of data. UDP allows applications to send IP datagrams to other applications without having to establish a connection and than having to release it later, which increases the speed of communication. UDP is described in RFC 768. The ...
... What is more important to gaming applications is the prompt delivery of data. UDP allows applications to send IP datagrams to other applications without having to establish a connection and than having to release it later, which increases the speed of communication. UDP is described in RFC 768. The ...
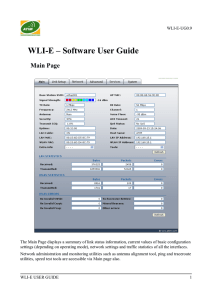
WLI-E – Software User Guide
... Tx/Rx Rate represents the data rates of the last transmitted and received packets; Tx/Rx Packets value represents the total amount of packets transmitted to and received from the Station during the connection uptime; Tx/Rx Packet Rate (packets per second) represents the mean value of the transmitted ...
... Tx/Rx Rate represents the data rates of the last transmitted and received packets; Tx/Rx Packets value represents the total amount of packets transmitted to and received from the Station during the connection uptime; Tx/Rx Packet Rate (packets per second) represents the mean value of the transmitted ...
MPLS-TP - Dspcsp.com
... Originally developed by Juniper and Cisco to detect failures in the bidirectional path between routers faster than via routing protocol hellos thus reducing routing processing load as hello rates can be reduced ...
... Originally developed by Juniper and Cisco to detect failures in the bidirectional path between routers faster than via routing protocol hellos thus reducing routing processing load as hello rates can be reduced ...
Chapter 1: A First Look at Windows 2000 Professional
... The Growth of the Internet Initially, Internet was small and limited to researchers In 1990s, Internet grew immensely as governments, universities, corporations, and the general public began to use it Organizations and Internet now experiencing problems managing IP addresses ...
... The Growth of the Internet Initially, Internet was small and limited to researchers In 1990s, Internet grew immensely as governments, universities, corporations, and the general public began to use it Organizations and Internet now experiencing problems managing IP addresses ...
Introduction, Data link layer issues, Ethernet, Hubs,Switches
... “MAC” addresses used in frame headers to identify source, dest • different from IP address! ...
... “MAC” addresses used in frame headers to identify source, dest • different from IP address! ...
1 - IC Intracom
... The MDI/MDI-X push button alleviates the worry of the type of cable to use when connecting the converter with another 10Base-T device. Simply follow these instructions below when ...
... The MDI/MDI-X push button alleviates the worry of the type of cable to use when connecting the converter with another 10Base-T device. Simply follow these instructions below when ...