EURESCOM - SALTAMONTES
... same manner (over the same path with the same forwarding treatment) Characteristics: Set of IP packets Is eventually encoded as the label Is not a route or path. However, packets in a FEC and originating at a given point follow a route (or one set of routes) FEC gives greater control over ...
... same manner (over the same path with the same forwarding treatment) Characteristics: Set of IP packets Is eventually encoded as the label Is not a route or path. However, packets in a FEC and originating at a given point follow a route (or one set of routes) FEC gives greater control over ...
Page 1 - EECS Instructional Support Group Home Page
... Needs synchronization between sender and receiver In case of non-permanent conversations - Needs to dynamic bind a slot to a conservation - How to do this? ...
... Needs synchronization between sender and receiver In case of non-permanent conversations - Needs to dynamic bind a slot to a conservation - How to do this? ...
CH4-SDNbasics
... • Networks are much more primitive and less understood than other computer systems ...
... • Networks are much more primitive and less understood than other computer systems ...
Controls for the Credit Card Environment
... approved by the Responsible Authority as a legitimate business need. 4. Stored CC data in all media (including on-line, backups, logs, etc.) shall be rendered unreadable by one or more of the following methods: (a) One-way hashes (hashed indexes), such as SHA-1 (b) Truncation (c) Index tokens and PA ...
... approved by the Responsible Authority as a legitimate business need. 4. Stored CC data in all media (including on-line, backups, logs, etc.) shall be rendered unreadable by one or more of the following methods: (a) One-way hashes (hashed indexes), such as SHA-1 (b) Truncation (c) Index tokens and PA ...
CROSS-ROAD: CROSS-layer Ring Overlay for AD hoc networks
... workload on nodes taking part to the service The subject-based routing defines a logarithmic lookup cost on the network dimension (O(log N)) A lot of application can adapt their contents to this routing strategy ...
... workload on nodes taking part to the service The subject-based routing defines a logarithmic lookup cost on the network dimension (O(log N)) A lot of application can adapt their contents to this routing strategy ...
LANMAR: Landmark Routing for Large Scale Wireless Ad Hoc
... Existing wireless routing schemes can be classified into two categories according to their design philosophy: (a) proactive (e.g., distance vector or link state based); and (b) reactive (e.g., on demand). Proactive schemes compute global routes in the background. Historically, the first routing sche ...
... Existing wireless routing schemes can be classified into two categories according to their design philosophy: (a) proactive (e.g., distance vector or link state based); and (b) reactive (e.g., on demand). Proactive schemes compute global routes in the background. Historically, the first routing sche ...
MIHIN Generic Use Case 9116922_1 v7 03-11-14
... [This section is to describe how the Message Content is to be used for this specific use case. Message Content is a defined term in the Agreement, which is the primary agreement between all of the Participating Organizations, as is defined as: “‘Message Content’ means information which is requested ...
... [This section is to describe how the Message Content is to be used for this specific use case. Message Content is a defined term in the Agreement, which is the primary agreement between all of the Participating Organizations, as is defined as: “‘Message Content’ means information which is requested ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... node, through the HTTP server. The communication between the EWS node and the hub is outside of the scope of this paper. It is implemented as an extension of the regular communication protocol used by the specific WSN. The implementation details can be found in [9]. used to collect the actual sensor ...
... node, through the HTTP server. The communication between the EWS node and the hub is outside of the scope of this paper. It is implemented as an extension of the regular communication protocol used by the specific WSN. The implementation details can be found in [9]. used to collect the actual sensor ...
Coruscations and Requirements for Quality of Services in Mobile Ad
... actually seeking for highest priority, because then this model would result in a similar model with IntServ which have per flow provisioning for all packets. Therefore, FQMM applies a hybrid provisioning where both IntServ and DiffServ scheme are used separately. The FQMM hybrid model defines three ...
... actually seeking for highest priority, because then this model would result in a similar model with IntServ which have per flow provisioning for all packets. Therefore, FQMM applies a hybrid provisioning where both IntServ and DiffServ scheme are used separately. The FQMM hybrid model defines three ...
FREE Sample Here
... cable. If a packet is detected, the nonsending nodes go into “defer” mode. The Ethernet protocol permits only one node to transmit at a time. Transmission is accomplished by sending a carrier signal. Carrier sense is the process of checking communication media for a specific voltage level indicating ...
... cable. If a packet is detected, the nonsending nodes go into “defer” mode. The Ethernet protocol permits only one node to transmit at a time. Transmission is accomplished by sending a carrier signal. Carrier sense is the process of checking communication media for a specific voltage level indicating ...
Networking for Everyone
... networked home and small offices. It is composed of wireless LAN solutions, a full range of network adapters for desktop and notebook use, unmanaged, dual-speed standalone switches, as well as internet connectivity products which include a line of ADSL (USB & PCI) modems. The Barricade™ line up is c ...
... networked home and small offices. It is composed of wireless LAN solutions, a full range of network adapters for desktop and notebook use, unmanaged, dual-speed standalone switches, as well as internet connectivity products which include a line of ADSL (USB & PCI) modems. The Barricade™ line up is c ...
RFID Applications for School Campuses
... Asset Management Web Service API Client (ApiTestWeb, ShowTagPos, ShowTagCourse) ...
... Asset Management Web Service API Client (ApiTestWeb, ShowTagPos, ShowTagCourse) ...
ppt
... Topology: The Internet is a complex mesh of different AS’s with very little structure. Autonomy of AS’s: Each AS defines link costs in different ways, so not possible to find lowest cost paths. Trust: Some AS’s can’t trust others to advertise good routes (e.g. two competing backbone providers), ...
... Topology: The Internet is a complex mesh of different AS’s with very little structure. Autonomy of AS’s: Each AS defines link costs in different ways, so not possible to find lowest cost paths. Trust: Some AS’s can’t trust others to advertise good routes (e.g. two competing backbone providers), ...
Enabling a “RISC” Approach for Software
... view of many traffic metrics for tasks such as traffic engineering (e.g., heavy hitters), anomaly detection (e.g., entropy of source addresses), and security (e.g., DDoS detection). Obtaining an accurate estimate of these metrics while using little router CPU and memory is challenging. This in turn ...
... view of many traffic metrics for tasks such as traffic engineering (e.g., heavy hitters), anomaly detection (e.g., entropy of source addresses), and security (e.g., DDoS detection). Obtaining an accurate estimate of these metrics while using little router CPU and memory is challenging. This in turn ...
Layer 2 Fundamentals
... slaves wether they have to transmit data or not) • is concerned with physical naming (addressing); defines MAC addressing; • The NIC uses the MAC address to assess whether the message is destined for that host and therefore should be passed onto the upper layers of the OSI model. • The NIC makes thi ...
... slaves wether they have to transmit data or not) • is concerned with physical naming (addressing); defines MAC addressing; • The NIC uses the MAC address to assess whether the message is destined for that host and therefore should be passed onto the upper layers of the OSI model. • The NIC makes thi ...
交大資工蔡文能計概
... authentic and has access rights to establish a connection. (Layer 5) • Transport Layer: This layer provides transparent transfer of data between end systems, or hosts, and is responsible for end-to-end error recovery and flow control. (Layer 4) • Network Layer: This Layer determines the path that wi ...
... authentic and has access rights to establish a connection. (Layer 5) • Transport Layer: This layer provides transparent transfer of data between end systems, or hosts, and is responsible for end-to-end error recovery and flow control. (Layer 4) • Network Layer: This Layer determines the path that wi ...
White Paper
... because all these frame sizes are used in the network and so the results for each must be known. The tests that are mentioned in RFC 2544 are Throughput, Latency, Frame Loss and Back-to-back frames. The first three are mentioned previously in this paper. Back-to-back frame testing involves sending a ...
... because all these frame sizes are used in the network and so the results for each must be known. The tests that are mentioned in RFC 2544 are Throughput, Latency, Frame Loss and Back-to-back frames. The first three are mentioned previously in this paper. Back-to-back frame testing involves sending a ...
How a Switch Works
... With cut-through switching, the LAN switch copies into its memory only the destination MAC address, which is located in the first 6 bytes of the frame following the preamble. The switch looks up the destination MAC address in its switching table, determines the outgoing interface port, and forwards t ...
... With cut-through switching, the LAN switch copies into its memory only the destination MAC address, which is located in the first 6 bytes of the frame following the preamble. The switch looks up the destination MAC address in its switching table, determines the outgoing interface port, and forwards t ...
슬라이드 1
... Communications take place between the wireless nodes and AP, not directly between nodes. can use different access schemes collision wireless nodes and AP are not coordinated ...
... Communications take place between the wireless nodes and AP, not directly between nodes. can use different access schemes collision wireless nodes and AP are not coordinated ...
1 - Cisco Support Community
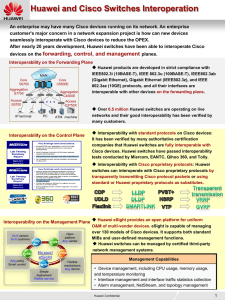
... C3560 was moved to the S9300 CSS system newly deployed on the network. The S9300 switches worked as aggregation switches and used CSS technology to improve network reliability. Cisco 3560 and Huawei S9300 switches ran standard MSTP protocol to realize redundancy protection on the Layer 2 network, en ...
... C3560 was moved to the S9300 CSS system newly deployed on the network. The S9300 switches worked as aggregation switches and used CSS technology to improve network reliability. Cisco 3560 and Huawei S9300 switches ran standard MSTP protocol to realize redundancy protection on the Layer 2 network, en ...
NIST Menu
... This document has been prepared to assist the IEEE 802.21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) res ...
... This document has been prepared to assist the IEEE 802.21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) res ...
Systems Programming 8 (Connection
... – As n increases, # of dead things does also (link down) – As n increases, # of overloaded things does also (msg lost) GWU CS 259 Brad Taylor Spring 2004 ...
... – As n increases, # of dead things does also (link down) – As n increases, # of overloaded things does also (msg lost) GWU CS 259 Brad Taylor Spring 2004 ...
Routing
... between the router and its neighbours (to reduce traffic) Each router builds map of the entire network, uses a shortest-path algorithm (usually Dijkstra algorithm) to compute a shortest path between itself and any other node in the area (creates the routing table) OSPF (Open Shortest Path first ...
... between the router and its neighbours (to reduce traffic) Each router builds map of the entire network, uses a shortest-path algorithm (usually Dijkstra algorithm) to compute a shortest path between itself and any other node in the area (creates the routing table) OSPF (Open Shortest Path first ...
C. Wireless Communications Security
... in the electric power industry communicate over copper wire, fiber, radio frequency (RF), or Ethernet. When older legacy communications protocols were established, little to no emphasis was placed on security. Due to their simplicity, these legacy protocols are still widely used. Without proper safe ...
... in the electric power industry communicate over copper wire, fiber, radio frequency (RF), or Ethernet. When older legacy communications protocols were established, little to no emphasis was placed on security. Due to their simplicity, these legacy protocols are still widely used. Without proper safe ...
paper
... Most spike sorting algorithms don’t address the presented difficulties at all, as they assume full stationarity of the data. Some methods [4, 11] try to cope with the lack of stationarity by grouping data into many small clusters and identifying the clusters that can be combined to represent the act ...
... Most spike sorting algorithms don’t address the presented difficulties at all, as they assume full stationarity of the data. Some methods [4, 11] try to cope with the lack of stationarity by grouping data into many small clusters and identifying the clusters that can be combined to represent the act ...