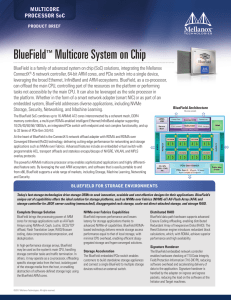
BlueField™ Multicore System on Chip
... storage controller for JBOF, server caching (memcached), disaggregated rack storage, scale-out direct-attached storage, and storage RAID. Complete Storage Solution BlueField brings the processing power of ARM cores for storage applications such as All-Flash Arrays using NVMe-oF, Ceph, Lustre, iSCSI/ ...
... storage controller for JBOF, server caching (memcached), disaggregated rack storage, scale-out direct-attached storage, and storage RAID. Complete Storage Solution BlueField brings the processing power of ARM cores for storage applications such as All-Flash Arrays using NVMe-oF, Ceph, Lustre, iSCSI/ ...
WDM Optical Fiber Transmission Systems
... Generally speaking, in high-power optical fiber transmission, positive pre-chirping is useful for compensating for the waveform degradation caused by self phase modulation (SPM). SPM is a negative chirping in the optical fiber due to the optical Kerr effect, which is an effect of optical fiber non-l ...
... Generally speaking, in high-power optical fiber transmission, positive pre-chirping is useful for compensating for the waveform degradation caused by self phase modulation (SPM). SPM is a negative chirping in the optical fiber due to the optical Kerr effect, which is an effect of optical fiber non-l ...
Lesson 1 The PSTN
... Transport Component Of The PSTN Transport Means Transmission – Taking Voice, Data, And Video Signals From One Subscriber’s Access Line And Delivering Them To Another Customer’s Access Line. The End-Office, Or Class 5 Central Office Is The Point Where All Customer Access Lines Connect. The Trunks Wi ...
... Transport Component Of The PSTN Transport Means Transmission – Taking Voice, Data, And Video Signals From One Subscriber’s Access Line And Delivering Them To Another Customer’s Access Line. The End-Office, Or Class 5 Central Office Is The Point Where All Customer Access Lines Connect. The Trunks Wi ...
Project 9 - 2015: Real- Time Data transfer
... • Unpatched third-party OPC components • Components must be configured to recommendations made by the third-party vendor • Asset owners need supply-chain assurance © 2016 LOGIIC APPROVED FOR PUBLIC RELEASE — ...
... • Unpatched third-party OPC components • Components must be configured to recommendations made by the third-party vendor • Asset owners need supply-chain assurance © 2016 LOGIIC APPROVED FOR PUBLIC RELEASE — ...
EN_C3_ENG - BCS Koolitus
... In the circuit switched network, each single communication uses a dedicated channel that is allocated for the entire communication length. This requires: a preliminary phase to setup the circuit during which network reserves in each nodes all the resources needed to create and maintain the circuit ...
... In the circuit switched network, each single communication uses a dedicated channel that is allocated for the entire communication length. This requires: a preliminary phase to setup the circuit during which network reserves in each nodes all the resources needed to create and maintain the circuit ...
Intro_to_SS7_Tutorial_Intro to SS7 Signalling
... The SS7 protocol is designed to both facilitate these functions and to maintain the network over which they are provided. Like most modern protocols, the SS7 protocol is layered. ...
... The SS7 protocol is designed to both facilitate these functions and to maintain the network over which they are provided. Like most modern protocols, the SS7 protocol is layered. ...
Chap 4 Router Components
... Tests each step along the way Takes advantage of the error messages generated by routers when a packet exceeds its Time To Live (TTL) value ...
... Tests each step along the way Takes advantage of the error messages generated by routers when a packet exceeds its Time To Live (TTL) value ...
PPT, 1.7M - Feng Xia
... shared by other devices (e.g., phone); devices (motors) interfere as well multipath propagation: radio signal reflects off objects ground, arriving ad destination at slightly different times ...
... shared by other devices (e.g., phone); devices (motors) interfere as well multipath propagation: radio signal reflects off objects ground, arriving ad destination at slightly different times ...
IOSR Journal of Computer Engineering (IOSRJCE) ISSN: 2278-0661, ISBN: 2278-8727
... problem at its data link layer, it removes the route from its route cache and generates a route error message. The route error message is sent to each node that has sent a packet routed over the broken link. When a node receives a route error message, it removes the hop in error from its route cache ...
... problem at its data link layer, it removes the route from its route cache and generates a route error message. The route error message is sent to each node that has sent a packet routed over the broken link. When a node receives a route error message, it removes the hop in error from its route cache ...
Ch4. Network Layer and Routing
... running one the host wants to join a specific multicast group Joining a multicast group is receiver-driven Coordinate the multicast routers so that multicast datagrams are routed to their final destinations ...
... running one the host wants to join a specific multicast group Joining a multicast group is receiver-driven Coordinate the multicast routers so that multicast datagrams are routed to their final destinations ...
04_XMesh_RtControls_LowPower
... Motivation – Battery How long will motes last on 2 AA alkaline* batteries? ...
... Motivation – Battery How long will motes last on 2 AA alkaline* batteries? ...
TORA (Cont`d)
... characteristics of large metropolis and blocks of this data is transmitted in rapid sequence to a vehicle to visualize needed environment ahead of time Education via the internet: Educational opportunities on Internet to K-12 students and other interested individuals. Possible to have last-mile wire ...
... characteristics of large metropolis and blocks of this data is transmitted in rapid sequence to a vehicle to visualize needed environment ahead of time Education via the internet: Educational opportunities on Internet to K-12 students and other interested individuals. Possible to have last-mile wire ...
CCNA 3
... • The purpose of VLSM is to alleviate the shortage of IP addresses • VLSM allows: • More than one subnet mask within the same NW • Or . . . Multiple SNMasks with ONE IP Address • Use of long mask on networks with few hosts • Use of short mask on networks with many hosts • In order to use VLSM, the r ...
... • The purpose of VLSM is to alleviate the shortage of IP addresses • VLSM allows: • More than one subnet mask within the same NW • Or . . . Multiple SNMasks with ONE IP Address • Use of long mask on networks with few hosts • Use of short mask on networks with many hosts • In order to use VLSM, the r ...
CPS221 Lecture: Layered Network Architecture last revised 9/8/14
... to one another, information is typically transmitted between systems via a series of hops involving various intermediate systems. a) Compare traveling Gordon to the airport - a friend might drive you to the train station, from where you take a commuter rail train to North Station, from where you tak ...
... to one another, information is typically transmitted between systems via a series of hops involving various intermediate systems. a) Compare traveling Gordon to the airport - a friend might drive you to the train station, from where you take a commuter rail train to North Station, from where you tak ...
CCNA 3
... • The purpose of VLSM is to alleviate the shortage of IP addresses • VLSM allows: • More than one subnet mask within the same NW • Or . . . Multiple SNMasks with ONE IP Address • Use of long mask on networks with few hosts • Use of short mask on networks with many hosts • In order to use VLSM, the r ...
... • The purpose of VLSM is to alleviate the shortage of IP addresses • VLSM allows: • More than one subnet mask within the same NW • Or . . . Multiple SNMasks with ONE IP Address • Use of long mask on networks with few hosts • Use of short mask on networks with many hosts • In order to use VLSM, the r ...
ppt
... DSR Implementation Mechanism – Promiscuous Mode •S sends message X with source route C-B-A-D •C forwards message to B •A hears message on physical channel •A reads header and finds self X – CBAD •A broadcasts Gratuitous Reply B •Message X continues to D X – CBAD X – CBAD ...
... DSR Implementation Mechanism – Promiscuous Mode •S sends message X with source route C-B-A-D •C forwards message to B •A hears message on physical channel •A reads header and finds self X – CBAD •A broadcasts Gratuitous Reply B •Message X continues to D X – CBAD X – CBAD ...
LumiNOC: A Power-Efficient, High-Performance, Photonic Network
... all tiles are interconnected by two different subnets, one horizontal and one vertical. If a sender and receiver do not reside in the same subnet, transmission requires a hop through an intermediate node’s electrical router. In this case, transmission experiences longer delay due to the extra O/E-E/ ...
... all tiles are interconnected by two different subnets, one horizontal and one vertical. If a sender and receiver do not reside in the same subnet, transmission requires a hop through an intermediate node’s electrical router. In this case, transmission experiences longer delay due to the extra O/E-E/ ...
ppt
... Pragmatic General Multicast (RFC 3208) • Similar approach as SRM: IP multicast + NAKs – … but more techniques for scalability ...
... Pragmatic General Multicast (RFC 3208) • Similar approach as SRM: IP multicast + NAKs – … but more techniques for scalability ...
JuNIPEr FLOw MONITOrINg J-Flow on J Series Services routers and 1
... such as routers, firewalls, and switches collect flow data and export that information to flow collectors. The collected data provides critical information about traffic in the network and aids in tasks such as billing, traffic engineering, capacity planning, and traffic analysis for peering policy ...
... such as routers, firewalls, and switches collect flow data and export that information to flow collectors. The collected data provides critical information about traffic in the network and aids in tasks such as billing, traffic engineering, capacity planning, and traffic analysis for peering policy ...
Elektronischer Hšrsaal - univ
... could ping. You could get a UDP packet through. Telnet and FTP would fail after a while. And it depended on where you were going (some hosts were just fine, others flaky) and time of day (I did a lot of work on weekends in the late 1980s and the network was wonderfully free then). Around 1pm was bad ...
... could ping. You could get a UDP packet through. Telnet and FTP would fail after a while. And it depended on where you were going (some hosts were just fine, others flaky) and time of day (I did a lot of work on weekends in the late 1980s and the network was wonderfully free then). Around 1pm was bad ...
TCP Congestion Control
... could ping. You could get a UDP packet through. Telnet and FTP would fail after a while. And it depended on where you were going (some hosts were just fine, others flaky) and time of day (I did a lot of work on weekends in the late 1980s and the network was wonderfully free then). Around 1pm was bad ...
... could ping. You could get a UDP packet through. Telnet and FTP would fail after a while. And it depended on where you were going (some hosts were just fine, others flaky) and time of day (I did a lot of work on weekends in the late 1980s and the network was wonderfully free then). Around 1pm was bad ...
MobileMAN meeting
... • During this period we have implemented the node classification (i.e. smart, dummy nodes) for creating Ad Hoc backbone to support other constrained devices and extend the network lifetime. • Classification criteria is based on – Link stability, Mobility, Battery power and User preferences • This no ...
... • During this period we have implemented the node classification (i.e. smart, dummy nodes) for creating Ad Hoc backbone to support other constrained devices and extend the network lifetime. • Classification criteria is based on – Link stability, Mobility, Battery power and User preferences • This no ...
Chapter5link
... wireless links: high error rates • Q: why both link-level and end-end reliability? half-duplex and full-duplex with half duplex, nodes at both ends of link can transmit, but not at same time ...
... wireless links: high error rates • Q: why both link-level and end-end reliability? half-duplex and full-duplex with half duplex, nodes at both ends of link can transmit, but not at same time ...























