SPECIFICATION FOR: TWISTED PAIR VIDEO SYSTEM
... The Outdoor Rated Ethernet Extender Single Twisted Pair System shall comprise NEMA TS-2 rated Transmitter and Receiver Units.,. The Transmitter shall be enclosed in a NEMA4X enclosure., The Transmitter and Receiver units shall be in selfcontained aluminum extruded cases 1.1"H x 1.6"W x 5.1"D. The 5. ...
... The Outdoor Rated Ethernet Extender Single Twisted Pair System shall comprise NEMA TS-2 rated Transmitter and Receiver Units.,. The Transmitter shall be enclosed in a NEMA4X enclosure., The Transmitter and Receiver units shall be in selfcontained aluminum extruded cases 1.1"H x 1.6"W x 5.1"D. The 5. ...
Improving Tor using a TCP-over-DTLS Tunnel Joel Reardon Ian Goldberg Google Zurich
... connections The sender is used to demultiplex the proper connection that is used to decrypt the DTLS payload Nodes that do not offer a UDP socket will use the existing transport, assuring backwards compatibility ...
... connections The sender is used to demultiplex the proper connection that is used to decrypt the DTLS payload Nodes that do not offer a UDP socket will use the existing transport, assuring backwards compatibility ...
Part I: Introduction
... encapsulate datagram into frame, adding header, trailer implement channel access if shared medium, ‘physical addresses’ used in frame headers to identify source, dest • different from IP address! ...
... encapsulate datagram into frame, adding header, trailer implement channel access if shared medium, ‘physical addresses’ used in frame headers to identify source, dest • different from IP address! ...
ppt
... • The size of the set is the window size • Assume window size is n • Let A be the last ack’d packet of sender without gap; ...
... • The size of the set is the window size • Assume window size is n • Let A be the last ack’d packet of sender without gap; ...
RouterA(config)# ip route
... When complex networks have multiple interconnections, static routes are not a practical solution – they can’t react to changes in the topology When all routers in an internetwork are operating with the same knowledge of the routes in a network is said to have converged. Fast convergence is desirable ...
... When complex networks have multiple interconnections, static routes are not a practical solution – they can’t react to changes in the topology When all routers in an internetwork are operating with the same knowledge of the routes in a network is said to have converged. Fast convergence is desirable ...
Balancing Systematic and Flexible Exploration of Social Networks
... Several approaches attempt to more efficiently use available display space by distorting the graph. Fisheye techniques allow users to examine a focus area in great detail, but also tend to obscure the global structure of networks, e.g. [21, 23]. Multiscale graph abstraction is another technique that ...
... Several approaches attempt to more efficiently use available display space by distorting the graph. Fisheye techniques allow users to examine a focus area in great detail, but also tend to obscure the global structure of networks, e.g. [21, 23]. Multiscale graph abstraction is another technique that ...
Chapter 2 - Chabot College
... protocol field to identify the network-layer protocol. – ISDN: a set of digital services that transmits voice and data over existing phone lines. – Link Access Procedure, Balanced (LAPB): For packet-switched networks used to encapsulate packets at Layer 2 of the X.25 stack. Provides reliability and ...
... protocol field to identify the network-layer protocol. – ISDN: a set of digital services that transmits voice and data over existing phone lines. – Link Access Procedure, Balanced (LAPB): For packet-switched networks used to encapsulate packets at Layer 2 of the X.25 stack. Provides reliability and ...
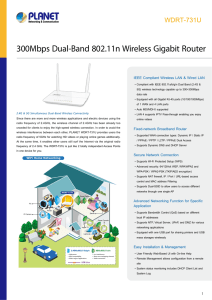
300Mbps Dual-Band 802.11n Wireless Gigabit Router
... •• Remote Management allows configuration from a remote site •• System status monitoring includes DHCP Client List and System Log ...
... •• Remote Management allows configuration from a remote site •• System status monitoring includes DHCP Client List and System Log ...
Delay-sensitive and multimedia communication in cognitive radio
... Limited resource nature of CRSN nodes bring consequential constraints on the transport layer protocol design [3]. Moreover, opportunistic spectrum access challenge emerges in CRSN, and brings additional link delays and losses as an expected outcome of variations in spectrum availability due to spect ...
... Limited resource nature of CRSN nodes bring consequential constraints on the transport layer protocol design [3]. Moreover, opportunistic spectrum access challenge emerges in CRSN, and brings additional link delays and losses as an expected outcome of variations in spectrum availability due to spect ...
Oracle-Data-Encryption
... External large objects (BFILE) Materialized View Logs Transportable Tablespaces Original import/export utilities ...
... External large objects (BFILE) Materialized View Logs Transportable Tablespaces Original import/export utilities ...
Exploiting Route Redundancy via Structured Peer to Peer
... Resilient Overlay Networks (SOSP 01) Internet Indirection Infrastructure (SIGCOMM 02) Secure Overlay Services (SIGCOMM 02) ...
... Resilient Overlay Networks (SOSP 01) Internet Indirection Infrastructure (SIGCOMM 02) Secure Overlay Services (SIGCOMM 02) ...
CCL Advanced Applications (Cont`d)
... • Implement native (not tunneled) IPv6-over-ATM on the vBNS ...
... • Implement native (not tunneled) IPv6-over-ATM on the vBNS ...
Network-INT201-05 - Department of Computer Engineering
... E.g. timestamp, record route taken, specify list of routers to visit. ...
... E.g. timestamp, record route taken, specify list of routers to visit. ...
Spin Palace Casino Mobile - Spin Palace Mobile Flash Casino
... section II. On WSNs, the sensor nodes are provided with specific requirements like low memory, limited energy availability, reduced processing power, and energy efficiency which is a main issue for designing the routing for WSNs or any network. Routing protocols of WSNs are based on clustering; thei ...
... section II. On WSNs, the sensor nodes are provided with specific requirements like low memory, limited energy availability, reduced processing power, and energy efficiency which is a main issue for designing the routing for WSNs or any network. Routing protocols of WSNs are based on clustering; thei ...
BSR 64000
... routing, QoS, and CMTS functions and it scales economically to meet ever-increasing subscriber demands and the introduction of new services. The BSR 64000 design is based on centralized routing table calculations and distributed forwarding, and it provides the benefits of simple configuration (singl ...
... routing, QoS, and CMTS functions and it scales economically to meet ever-increasing subscriber demands and the introduction of new services. The BSR 64000 design is based on centralized routing table calculations and distributed forwarding, and it provides the benefits of simple configuration (singl ...
C - University of Arizona
... Highly loaded link never shows a cost more than three times its idle cost The most expensive link is only seven times the cost of the least expensive A high–speed satellite link is more attractive than a low speed terrestrial link Cost is a function of link utilization only at moderate to high loads ...
... Highly loaded link never shows a cost more than three times its idle cost The most expensive link is only seven times the cost of the least expensive A high–speed satellite link is more attractive than a low speed terrestrial link Cost is a function of link utilization only at moderate to high loads ...
3rd Edition: Chapter 4
... (max.transfer size) largest possible link-level frame. large IP datagram divided (“fragmented”) within net one datagram becomes several datagrams “reassembled” only at final destination IP header bits used to ...
... (max.transfer size) largest possible link-level frame. large IP datagram divided (“fragmented”) within net one datagram becomes several datagrams “reassembled” only at final destination IP header bits used to ...
DICOM IMAGE SECURE COMMUNICATIONS WITH INTERNET
... First, the American College of Radiology (ACR) standard for teleradiology, adopted in 1994, defines guidelines for qualifications of both physician and non physician personnel, equipment specifications, quality improvement, licensure, staff credentialing, and liability the DICOM Standard specifies s ...
... First, the American College of Radiology (ACR) standard for teleradiology, adopted in 1994, defines guidelines for qualifications of both physician and non physician personnel, equipment specifications, quality improvement, licensure, staff credentialing, and liability the DICOM Standard specifies s ...
Token Ring Cards - Personal.psu.edu
... mechanism of ownership and access restrictions. It is one of the most commonly used protocols over the internet now days ...
... mechanism of ownership and access restrictions. It is one of the most commonly used protocols over the internet now days ...
Introduction to Classless Routing CCNA 3/Module 1 1
... • The purpose of VLSM is to alleviate the shortage of IP addresses • VLSM allows: • More than one subnet mask within the same network • Or . . . Multiple SNMasks with ONE IP Address • Use of long mask on networks with few hosts • Use of short mask on networks with many hosts • In order to use VLSM, ...
... • The purpose of VLSM is to alleviate the shortage of IP addresses • VLSM allows: • More than one subnet mask within the same network • Or . . . Multiple SNMasks with ONE IP Address • Use of long mask on networks with few hosts • Use of short mask on networks with many hosts • In order to use VLSM, ...
SIP and accounting - Columbia University
... model fits traditional CDR model Signaling services require accounting to prevent RTPover-SIP cloaking ...
... model fits traditional CDR model Signaling services require accounting to prevent RTPover-SIP cloaking ...