S-72.423 Telecommunication Systems
... connection-oriented service for transporting data across computer networks. In both technologies connections are signaled between endpoints, connection state is maintained at each node in the path and encapsulation techniques are used to carry data across the connection. Excluding differences in the ...
... connection-oriented service for transporting data across computer networks. In both technologies connections are signaled between endpoints, connection state is maintained at each node in the path and encapsulation techniques are used to carry data across the connection. Excluding differences in the ...
Explain how the TCP/IP protocols correlate to layers of
... Developed by Department of Defense ARPANET (1960s) Internet precursor Popularity Low cost Communicates between dissimilar platforms Open nature Routable Spans more than one LAN (LAN segment) Flexible Runs on combinations of network operating systems or network media Disadvantage: require ...
... Developed by Department of Defense ARPANET (1960s) Internet precursor Popularity Low cost Communicates between dissimilar platforms Open nature Routable Spans more than one LAN (LAN segment) Flexible Runs on combinations of network operating systems or network media Disadvantage: require ...
FrameSaver SLV 9126 Router Quick Reference - 9126-A2
... If you have not yet installed and set up the FrameSaver SLV Router, do so now. Refer to the FrameSaver SLV 9126-II Router Installation Instructions, Document Number 9126-A2-GN12, that came with the unit. Before starting to use the FrameSaver SLV Router, it is recommended that you download the User’s ...
... If you have not yet installed and set up the FrameSaver SLV Router, do so now. Refer to the FrameSaver SLV 9126-II Router Installation Instructions, Document Number 9126-A2-GN12, that came with the unit. Before starting to use the FrameSaver SLV Router, it is recommended that you download the User’s ...
Energy - Purdue University :: Computer Science
... AES both for its strength against cryptanalysis and for its lower computation complexity than the other candidates [17]. Hardware implementations of the Rijndael cipher can encrypt and decrypt at disk transfer speeds. Rijndael is a block cipher. The block size and the key length can be chosen indepe ...
... AES both for its strength against cryptanalysis and for its lower computation complexity than the other candidates [17]. Hardware implementations of the Rijndael cipher can encrypt and decrypt at disk transfer speeds. Rijndael is a block cipher. The block size and the key length can be chosen indepe ...
Network Monitoring
... WO = outbound queueing delay SO = outbound service time TO = outbound terminal delay ...
... WO = outbound queueing delay SO = outbound service time TO = outbound terminal delay ...
Dell Networking S4810 Data Sheet
... Ultra-low-latency, data center optimized The Dell Networking S-Series S4810 is an ultra-low-latency 10/40GbE switch purpose-built for applications in highperformance data center and computing environments. Leveraging a non-blocking, cut-through switching architecture, the S4810 delivers line-rate L2 ...
... Ultra-low-latency, data center optimized The Dell Networking S-Series S4810 is an ultra-low-latency 10/40GbE switch purpose-built for applications in highperformance data center and computing environments. Leveraging a non-blocking, cut-through switching architecture, the S4810 delivers line-rate L2 ...
Cloud Computing and Security
... significant. Interoute makes use of the necessary minimal subset of these features in order to provide an assured level of availability to private network customers while still making the economic gains associated with a shared network asset. IS-IS and LDP operate in order to propagate essential inf ...
... significant. Interoute makes use of the necessary minimal subset of these features in order to provide an assured level of availability to private network customers while still making the economic gains associated with a shared network asset. IS-IS and LDP operate in order to propagate essential inf ...
Metrics for Degree of Reordering in Packet Sequences
... bit-rate of 128 kbps and a packet size of 200 bytes, DT value can be determined as follows. Assume that the application can wait maximum 50 ms for expected packet, and that the packets arrive at a constant rate. That means within 50 ms, the application can receive (128 * 1000 * 0.05) / (200 * 8) i.e ...
... bit-rate of 128 kbps and a packet size of 200 bytes, DT value can be determined as follows. Assume that the application can wait maximum 50 ms for expected packet, and that the packets arrive at a constant rate. That means within 50 ms, the application can receive (128 * 1000 * 0.05) / (200 * 8) i.e ...
Chapter 12 Exterior Routing Protocols and Multicasting
... — Address field multicast address of group — Sent in IP datagram with Group Address field of IGMP message and Destination Address encapsulating IP header same — Current members of group will receive learn of new member — Routers listen to all IP multicast addresses to hear all reports ...
... — Address field multicast address of group — Sent in IP datagram with Group Address field of IGMP message and Destination Address encapsulating IP header same — Current members of group will receive learn of new member — Routers listen to all IP multicast addresses to hear all reports ...
TMO-100 - Funk- Electronic Piciorgros GmbH
... Performance Test with SDS-Gateway on FOUR SCCH/MCCH: Infrastructure: TETRA with one carrier TETRA Data Link: MCCH plus three SCCH Data Compression: OFF Data nodes: One or more polling nodes, polling 10 TMO-100 each Protocol: Modbus RTU Polling Target: Polling different numbers of bytes from inside ...
... Performance Test with SDS-Gateway on FOUR SCCH/MCCH: Infrastructure: TETRA with one carrier TETRA Data Link: MCCH plus three SCCH Data Compression: OFF Data nodes: One or more polling nodes, polling 10 TMO-100 each Protocol: Modbus RTU Polling Target: Polling different numbers of bytes from inside ...
CONNECTRIX VDX-6740B
... The Connectrix® VDX-6740B Top-of-Rack (ToR) switch redefines IP storage connectivity as the first Ethernet fabric switch purpose-built for IP storage. Designed for storage workloads it offers the network availability, deterministic performance and agility required for today’s business-critical appli ...
... The Connectrix® VDX-6740B Top-of-Rack (ToR) switch redefines IP storage connectivity as the first Ethernet fabric switch purpose-built for IP storage. Designed for storage workloads it offers the network availability, deterministic performance and agility required for today’s business-critical appli ...
GI3112131218
... destination node is multi-hop away from the source. Thus each node here acts as a router when the situation demands. In an ad hoc network, one of the major concerns is how to decrease the power usage or battery depletion level of each node among the network so that the overall lifetime of the networ ...
... destination node is multi-hop away from the source. Thus each node here acts as a router when the situation demands. In an ad hoc network, one of the major concerns is how to decrease the power usage or battery depletion level of each node among the network so that the overall lifetime of the networ ...
Week_Five_Network
... How packets travel in a network? A check sum is created at the source computer and included in the packet. The check sum value is computed from data packet to check its integrity. Through integrity, we mean a check on whether the data received is error free or not. This is because while traveling on ...
... How packets travel in a network? A check sum is created at the source computer and included in the packet. The check sum value is computed from data packet to check its integrity. Through integrity, we mean a check on whether the data received is error free or not. This is because while traveling on ...
Aalborg Universitet Morten Videbæk
... using random linear network coding, then it stores them in the MAC layer queue. Once the coded packets are buffered in the MAC queue for transmission, they cannot be removed from the MAC queue because we design the PlayNCool protocol to be independent from the upper and the lower layers. The source ...
... using random linear network coding, then it stores them in the MAC layer queue. Once the coded packets are buffered in the MAC queue for transmission, they cannot be removed from the MAC queue because we design the PlayNCool protocol to be independent from the upper and the lower layers. The source ...
Ethernet - Computer Science Technology
... 802.3ae Standard • Defined to run only on fiber-optic cabling, both SMF and MMF, on a maximum distance of 40 km – Provides bandwidth that can transform how WAN speeds are thought of ...
... 802.3ae Standard • Defined to run only on fiber-optic cabling, both SMF and MMF, on a maximum distance of 40 km – Provides bandwidth that can transform how WAN speeds are thought of ...
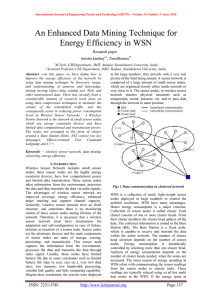
An Enhanced Data Mining Technique for Energy Efficiency
... forward it to the special node called sink or base station. This acts as interface between the sensor nodes and users. The uniqueness of the sensor node lies in its small size and the light weight. However, there are lots of constraints such as limits on resources in terms of energy, bandwidth compu ...
... forward it to the special node called sink or base station. This acts as interface between the sensor nodes and users. The uniqueness of the sensor node lies in its small size and the light weight. However, there are lots of constraints such as limits on resources in terms of energy, bandwidth compu ...
connect-and-protect: building a trust-based
... Starting with physical layer (PHY) connectivity and extending through protocol conversion, authentication, encryption, secure tunneling, role- and policy-based access, and ending with analytics, the Connect-and-Protect methodology shifts the point of demarcation based on the design and capabilities ...
... Starting with physical layer (PHY) connectivity and extending through protocol conversion, authentication, encryption, secure tunneling, role- and policy-based access, and ending with analytics, the Connect-and-Protect methodology shifts the point of demarcation based on the design and capabilities ...
- Rich`s Cabrillo College CIS Classes
... creates a table in a local area network's gateway router that maps the physical machine (or Media Access Control - MAC address) addresses to corresponding Internet Protocol addresses (IP address). When a new machine is set up, its RARP client program requests from the RARP server on the router to be ...
... creates a table in a local area network's gateway router that maps the physical machine (or Media Access Control - MAC address) addresses to corresponding Internet Protocol addresses (IP address). When a new machine is set up, its RARP client program requests from the RARP server on the router to be ...
23anon
... Guarantees information-theoretic anonymity for message senders • This is an unusually strong form of security: defeats adversary who has unlimited computational power ...
... Guarantees information-theoretic anonymity for message senders • This is an unusually strong form of security: defeats adversary who has unlimited computational power ...
CMU Kick-off Meeting - Carnegie Mellon University
... Avoiding lane change collision Vehicle brakes hard ...
... Avoiding lane change collision Vehicle brakes hard ...
bca501 : core – 18 : computer networks
... 33. The technique of temporarily delaying outgoing acknowledgements so that they can be hooked onto the next outgoing data frame is called a) piggybacking b) cyclic redundancy check c) fletcher’s checksum d) none of the mentioned Answer: a. 34. Transport layer aggregates data from different applicat ...
... 33. The technique of temporarily delaying outgoing acknowledgements so that they can be hooked onto the next outgoing data frame is called a) piggybacking b) cyclic redundancy check c) fletcher’s checksum d) none of the mentioned Answer: a. 34. Transport layer aggregates data from different applicat ...
Router - UStudy.in
... • The work a router does it called routing, which is somewhat like switching, but a router is different from a switch. • The latter is simply a device to connect machines to form a LAN. ...
... • The work a router does it called routing, which is somewhat like switching, but a router is different from a switch. • The latter is simply a device to connect machines to form a LAN. ...