VPNs
... Could have different tariffs • Company didn’t have to pay for individual long distance calls ...
... Could have different tariffs • Company didn’t have to pay for individual long distance calls ...
IETF GEOPRIV Status - Emergency Services Workshop
... Configuring endpoints with location Transmitting location between points Requesting location information ...
... Configuring endpoints with location Transmitting location between points Requesting location information ...
2 What is a VPN
... the distinction is that they operate in a discrete fashion across a shared infrastructure, providing exclusive communications environments which do not share any points of interconnection. The combination of these terms produces VPN – a private network , where the privacy is introduced by some metho ...
... the distinction is that they operate in a discrete fashion across a shared infrastructure, providing exclusive communications environments which do not share any points of interconnection. The combination of these terms produces VPN – a private network , where the privacy is introduced by some metho ...
ECE 467 Network Implementation Lab Manual
... Figure 22 IP RIP packet consists of nine fields. ........................................................................... 49 Figure 23 IP RIP 2 packet consists of fields similar to those of an IP RIP packet. ...................... 50 Figure 24 Lab 3 Frame Relay Network diagram.................... ...
... Figure 22 IP RIP packet consists of nine fields. ........................................................................... 49 Figure 23 IP RIP 2 packet consists of fields similar to those of an IP RIP packet. ...................... 50 Figure 24 Lab 3 Frame Relay Network diagram.................... ...
CCNPv5 Module 5 Lesson 1
... DNS queries can reveal information such as who owns a particular domain and what addresses have been assigned to that domain Ping sweeps of addresses revealed by DNS queries can present a picture of the live hosts in a particular environment After such a list is generated, port scanning tools ca ...
... DNS queries can reveal information such as who owns a particular domain and what addresses have been assigned to that domain Ping sweeps of addresses revealed by DNS queries can present a picture of the live hosts in a particular environment After such a list is generated, port scanning tools ca ...
Internet Control Message Protocol
... normally restricted only to trusted sources of information because of potential security problems that uncontrolled acceptance of such messages can ...
... normally restricted only to trusted sources of information because of potential security problems that uncontrolled acceptance of such messages can ...
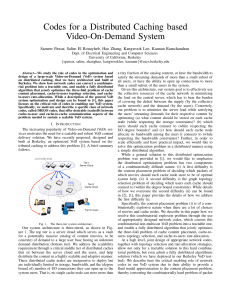
Codes for a Distributed Caching based Video-On
... To minimize the server’s total upload, we have to optimally leverage the resources of the cache nodes in order to maximize their contribution to the system. To illustrate the problem, let us consider a simple example depicted in the Fig. 2. Server has two movies, A and B, each of size 1GB and stream ...
... To minimize the server’s total upload, we have to optimally leverage the resources of the cache nodes in order to maximize their contribution to the system. To illustrate the problem, let us consider a simple example depicted in the Fig. 2. Server has two movies, A and B, each of size 1GB and stream ...
Chapter 4 slides
... router knows physicallyconnected neighbors, link costs to neighbors iterative process of computation, exchange of ...
... router knows physicallyconnected neighbors, link costs to neighbors iterative process of computation, exchange of ...
Multi-Protocol Label Switch (MPLS)
... travel around the overloaded segments. Traffic engineering, then, enables an administrator to define a policy for forwarding frames rather than depending upon dynamic routing protocols. • Traffic engineering is similar to source-routing in that an explicit path is defined for the frame to travel. Ho ...
... travel around the overloaded segments. Traffic engineering, then, enables an administrator to define a policy for forwarding frames rather than depending upon dynamic routing protocols. • Traffic engineering is similar to source-routing in that an explicit path is defined for the frame to travel. Ho ...
Network-INT201-06 - Department of Computer Engineering
... OSPF (Open Shortest Path First) “open”: publicly available ...
... OSPF (Open Shortest Path First) “open”: publicly available ...
CCNA3
... B. Full duplex Ethernet requires a point-to-point connection when only two nodes are present C. Ethernet switches can use full duplex mode to connect multiple nodes to a single pod of a switch D. Half duplex is a cut through packet processing method that is vow fast little error correction Full dupl ...
... B. Full duplex Ethernet requires a point-to-point connection when only two nodes are present C. Ethernet switches can use full duplex mode to connect multiple nodes to a single pod of a switch D. Half duplex is a cut through packet processing method that is vow fast little error correction Full dupl ...
NeoGate TE100 User Manual
... If your ISP says that you are connecting through a static or fixed IP address from your ISP, perform these steps: Step1: Select Static IP Address as the WAN Connection Type. Step2: Enter the IP Address. Step3: Enter the Subnet Mask. Step4: Enter the Gateway Address. Step5: Enter the Primary DNS and ...
... If your ISP says that you are connecting through a static or fixed IP address from your ISP, perform these steps: Step1: Select Static IP Address as the WAN Connection Type. Step2: Enter the IP Address. Step3: Enter the Subnet Mask. Step4: Enter the Gateway Address. Step5: Enter the Primary DNS and ...
I-CSCF - Computer Science and Engineering
... Advantages over free VoIP Quality of Service : The network offers no guarantees about the amount of bandwidth a user gets for a particular connection or about the delay the packets experience. Charging of multimedia services : Videoconferences can transfer a large amount of information. Some busines ...
... Advantages over free VoIP Quality of Service : The network offers no guarantees about the amount of bandwidth a user gets for a particular connection or about the delay the packets experience. Charging of multimedia services : Videoconferences can transfer a large amount of information. Some busines ...
M051055
... attached networks. Routers must also discover when their neighbors becomeunreachable or inoperative. This process is achieved with low overhead by periodically sendingsmall hello packets. As long as a router receives hello packets from a neighboring router, itassumes that the neighbor is functioning ...
... attached networks. Routers must also discover when their neighbors becomeunreachable or inoperative. This process is achieved with low overhead by periodically sendingsmall hello packets. As long as a router receives hello packets from a neighboring router, itassumes that the neighbor is functioning ...
Application Layer Functionality and Protocols
... Some servers may require authentication of user control information to verify the user has access rights rely on a central list of user accounts and authorization ...
... Some servers may require authentication of user control information to verify the user has access rights rely on a central list of user accounts and authorization ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... peripheral devices, cellular phones, and smartphones, whereas 802.11 is a higher-power, medium-range, higherrate access technology. For this reason, 802.15.1 networks are sometimes referred to as wireless personal area networks (WPANs). The link and physical layers of 802.15.1 are based on the earli ...
... peripheral devices, cellular phones, and smartphones, whereas 802.11 is a higher-power, medium-range, higherrate access technology. For this reason, 802.15.1 networks are sometimes referred to as wireless personal area networks (WPANs). The link and physical layers of 802.15.1 are based on the earli ...
Internet Big Bang Theory
... These routers were capable of supporting first OC-12c (655 Mb/s) and later OC-48c (2.5 Gb/s) interfaces. The first interfaces were not capable of forwarding at anywhere near full line rate, particularly if the routers were fully populated with high-speed interfaces. Later these routers supported mul ...
... These routers were capable of supporting first OC-12c (655 Mb/s) and later OC-48c (2.5 Gb/s) interfaces. The first interfaces were not capable of forwarding at anywhere near full line rate, particularly if the routers were fully populated with high-speed interfaces. Later these routers supported mul ...
3rd Edition: Chapter 4
... path from source to destination VC numbers, one number for each link along ...
... path from source to destination VC numbers, one number for each link along ...
Network Address Translation (NAT) Virtual Private Networks (VPN)
... • Hosts on private IP networks need to access public Internet • All traffic travels through a gateway to/from public Internet • Traffic needs to use IP address of gateway ...
... • Hosts on private IP networks need to access public Internet • All traffic travels through a gateway to/from public Internet • Traffic needs to use IP address of gateway ...
Leading the 10T era TextStart Dialogue with Chen Junhua, VP of
... multiple services. We will add multi-service bearing capabilities on our cluster routers to cater to network and service developments. Such capabilities include security monitoring, multi-protocol label switch (MPLS) L3/L2 provider edge (PE), next generation network (NGN)/3G gateway access, dedicate ...
... multiple services. We will add multi-service bearing capabilities on our cluster routers to cater to network and service developments. Such capabilities include security monitoring, multi-protocol label switch (MPLS) L3/L2 provider edge (PE), next generation network (NGN)/3G gateway access, dedicate ...
Networks
... Firewall Server that determines which connections may be established between two networks It typically works at network and transport layers In general application details are not known ...
... Firewall Server that determines which connections may be established between two networks It typically works at network and transport layers In general application details are not known ...
Toolbox - PlanetOne Communications
... company can create new “virtual” presences with telephone numbers from cities within the U.S. and internationally. ...
... company can create new “virtual” presences with telephone numbers from cities within the U.S. and internationally. ...