module_42 - Faculty Personal Homepage
... Alice sends invite message to her proxy server contains address sip:[email protected] Proxy responsible for routing SIP messages to callee ...
... Alice sends invite message to her proxy server contains address sip:[email protected] Proxy responsible for routing SIP messages to callee ...
ISDN over IP
... Should your access be charged by Time or Volume, then we would suggest the setting of Dial Up "on Demand": This option offers a targeted connection to the Internet and makes sense to use if your internet connection is charged by time or data volume. Please note that some software may, now and then, ...
... Should your access be charged by Time or Volume, then we would suggest the setting of Dial Up "on Demand": This option offers a targeted connection to the Internet and makes sense to use if your internet connection is charged by time or data volume. Please note that some software may, now and then, ...
TKN Dynamic shortcut circuits - concept and case study for static scenarios
... circuit capacity is ∼ 50% of the link capacity (in both Scenarios). If circuit capacity is too small, transmission delay of the CSPN increases - there is insufficient bandwidth reserved for packets that are to be sent via the circuit, so they have to traverse a highly filled buffer which shapes burs ...
... circuit capacity is ∼ 50% of the link capacity (in both Scenarios). If circuit capacity is too small, transmission delay of the CSPN increases - there is insufficient bandwidth reserved for packets that are to be sent via the circuit, so they have to traverse a highly filled buffer which shapes burs ...
ppt - UW Courses Web Server
... e.g. timestamp, record route taken, specify list of routers to visit. ...
... e.g. timestamp, record route taken, specify list of routers to visit. ...
Chapter 6
... – TCP Tahoe + Fast Recovery – Observation: packet loss can be inferred not only by timeouts, but also by duplicate ACKs – Widely deployed on most UNIX systems, though SACK-TCP is now gaining prominence Prof. Rick Han, University of Colorado at Boulder ...
... – TCP Tahoe + Fast Recovery – Observation: packet loss can be inferred not only by timeouts, but also by duplicate ACKs – Widely deployed on most UNIX systems, though SACK-TCP is now gaining prominence Prof. Rick Han, University of Colorado at Boulder ...
Memphis - Andrew.cmu.edu - Carnegie Mellon University
... scanner”) traffic on the Internet. As an initial trial, we identified sources sending between 1 and 3 packets of TCP (non-Web) traffic per day into the client’s networks. We applied this to the period September 1-11, finding that 0.00001% of the traffic matched this pattern. Further analysis yielded ...
... scanner”) traffic on the Internet. As an initial trial, we identified sources sending between 1 and 3 packets of TCP (non-Web) traffic per day into the client’s networks. We applied this to the period September 1-11, finding that 0.00001% of the traffic matched this pattern. Further analysis yielded ...
Support for Real-Time Traffic in a SAHN
... Throughput degraded by 35% (1.7 Mbps) End-to-end delay increased by 550% (559 ms) ...
... Throughput degraded by 35% (1.7 Mbps) End-to-end delay increased by 550% (559 ms) ...
Mobile IP Principals, Cont…
... —Open: AP does not challenge the identity of the node. —Password: upon association, the AP demands a password from the node. —Public Key: Each node has a public key. Upon association, the AP sends an encrypted message using the nodes public key. The node needs to respond correctly using it private k ...
... —Open: AP does not challenge the identity of the node. —Password: upon association, the AP demands a password from the node. —Public Key: Each node has a public key. Upon association, the AP sends an encrypted message using the nodes public key. The node needs to respond correctly using it private k ...
Management
... after sending informs. If a managed device does not receive an acknowledgement after sending an inform, it will resend the inform to the NM station and generate alarm logs. Even if the NM station restarts, it can still synchronize the informs sent during the restart process. If the device does not r ...
... after sending informs. If a managed device does not receive an acknowledgement after sending an inform, it will resend the inform to the NM station and generate alarm logs. Even if the NM station restarts, it can still synchronize the informs sent during the restart process. If the device does not r ...
Chapter5_4th - Computer Science Division
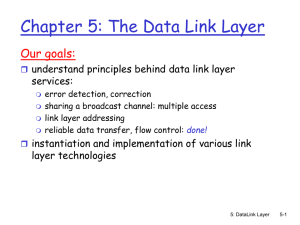
... seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? 5: DataLink Layer ...
... seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? 5: DataLink Layer ...
chapter5 - Computer Science Division
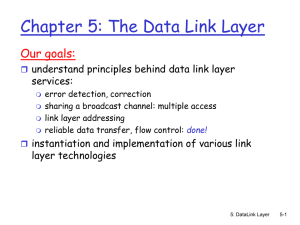
... seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? 5: DataLink Layer ...
... seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? 5: DataLink Layer ...
Security+ Guide to Network Security Fundamentals, Fourth Edition
... – Monitors network traffic to immediately block a malicious attack – NIPS sensors located in line on firewall itself ...
... – Monitors network traffic to immediately block a malicious attack – NIPS sensors located in line on firewall itself ...
Broadband Open Access: Lessons from Municipal Network Case
... to price discriminate is not important since most households subscribe to the bundle, and wholesaler can extract the same rent. If there is a large fraction of the population with no interest in broadband data, then vertically integrated firm can do 25% better than a dark fiber wholesaler, but still ...
... to price discriminate is not important since most households subscribe to the bundle, and wholesaler can extract the same rent. If there is a large fraction of the population with no interest in broadband data, then vertically integrated firm can do 25% better than a dark fiber wholesaler, but still ...
CX600 Metro Services Platform
... Future-Oriented IPv6-Compatible Solutions The CX600 supports a variety of IPv6 features including IPv6 lease line, NAT, dual stack, tunneling, and translation. The CX600 supports Next Hop Separation to optimize the IPv6 convergence time and larger IPv6 FIB to improve the scalability. All of them hel ...
... Future-Oriented IPv6-Compatible Solutions The CX600 supports a variety of IPv6 features including IPv6 lease line, NAT, dual stack, tunneling, and translation. The CX600 supports Next Hop Separation to optimize the IPv6 convergence time and larger IPv6 FIB to improve the scalability. All of them hel ...
Networking Overview
... Reserved --- reserved for future use (or for clever attackers…) Window --- controls number of outstanding packets; prevents one side from sending too fast (flow control) Checksum --- error detection (uses CRC) ...
... Reserved --- reserved for future use (or for clever attackers…) Window --- controls number of outstanding packets; prevents one side from sending too fast (flow control) Checksum --- error detection (uses CRC) ...
No Slide Title
... Internet Society (ISOC): a professional membership organization that comments on policies, practices, and oversees others dealing with network policy issues. Internet Architecture Board (IAB): responsible for defining overall architecture of the Internet with guidance and broad direction to the ...
... Internet Society (ISOC): a professional membership organization that comments on policies, practices, and oversees others dealing with network policy issues. Internet Architecture Board (IAB): responsible for defining overall architecture of the Internet with guidance and broad direction to the ...
6781_MPLS_Lecture2 - Computer Science and Engineering
... • LDP session establishment between P and PE routers • Exchange of label mappings between neighbors ...
... • LDP session establishment between P and PE routers • Exchange of label mappings between neighbors ...
COMP211_Topic6_Link
... framing, link access: encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” addresses used in frame headers to identify source, dest • different from IP address! ...
... framing, link access: encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” addresses used in frame headers to identify source, dest • different from IP address! ...
High-Performance Object Access in OSD Storage Subsystem
... Connection splitting (mobile) Explicit congestion control protocol (XCP) ...
... Connection splitting (mobile) Explicit congestion control protocol (XCP) ...
Spirent Journal of IEEE 802.3ba 40/100 GB Ethernet PASS
... Imprecise clocking between systems at 40/100 GB can increase latency and packet loss. Testing with backwards compatible system is critical. Latency issue is an important issue. At 10 GB, especially at high densities, the specification allows for a little variance for clocks. As you aggregate traffic ...
... Imprecise clocking between systems at 40/100 GB can increase latency and packet loss. Testing with backwards compatible system is critical. Latency issue is an important issue. At 10 GB, especially at high densities, the specification allows for a little variance for clocks. As you aggregate traffic ...
V.MoIP - D-002-I2 - Telecommunications Industry Association
... Recommendations, or with national regulatory requirements, and shall be interpreted accordingly. In order to be compliant with this Recommendation an implementation must provide functionality that is defined as being mandatory. ...
... Recommendations, or with national regulatory requirements, and shall be interpreted accordingly. In order to be compliant with this Recommendation an implementation must provide functionality that is defined as being mandatory. ...