Chapter 15 - William Stallings, Data and Computer
... Break up flat networks into separate networks Connect two LANs that may not share common medium access control. Operates at Layer 3 (OSI Network Layer) Hardware with embedded software: 1. Hardware -- can be network server/special device 2. Software – Network Operating System (NOS) and routing protoc ...
... Break up flat networks into separate networks Connect two LANs that may not share common medium access control. Operates at Layer 3 (OSI Network Layer) Hardware with embedded software: 1. Hardware -- can be network server/special device 2. Software – Network Operating System (NOS) and routing protoc ...
Protection And Restoration In MPLS Networks
... determined by the initial label value. Such a path is called a Label Switched Path (LSP). MPLS may also be applied to data switching technologies that are not packet based. The path followed by data through the network is still defined by the transition of switching labels and so is still legitimate ...
... determined by the initial label value. Such a path is called a Label Switched Path (LSP). MPLS may also be applied to data switching technologies that are not packet based. The path followed by data through the network is still defined by the transition of switching labels and so is still legitimate ...
ms225 series - Cisco Meraki
... safeguards to help prevent misconfigurations and reduce convergence time • Per port VLAN configuration • Multiple administrative roles with sophisticated security policy management ...
... safeguards to help prevent misconfigurations and reduce convergence time • Per port VLAN configuration • Multiple administrative roles with sophisticated security policy management ...
Spanning Tree Protocol (STP)
... • The LCP has a role in establishing, configuring, and testing the data-link connection. • The LCP provides automatic configuration of the interfaces at each end, including: – Handling varying limits on packet size – Detecting common misconfiguration errors – Terminating the link – Determining when ...
... • The LCP has a role in establishing, configuring, and testing the data-link connection. • The LCP provides automatic configuration of the interfaces at each end, including: – Handling varying limits on packet size – Detecting common misconfiguration errors – Terminating the link – Determining when ...
Cisco Application Centric Infrastructure and Cisco Application Virtual
... environment, the policies attached to the workloads are enforced transparently and consistently within the infrastructure. When the packet leaves the fabric, the VXLAN header is deencapsulated, and the packet is encapsulated with any tag of the tenant’s choice: VLAN, VXLAN, or NVGRE. Virtual machine ...
... environment, the policies attached to the workloads are enforced transparently and consistently within the infrastructure. When the packet leaves the fabric, the VXLAN header is deencapsulated, and the packet is encapsulated with any tag of the tenant’s choice: VLAN, VXLAN, or NVGRE. Virtual machine ...
Evaluating the Eifel Algorithm for TCP in a GPRS Network
... Apparently, Reno with Eifel suffers from lengthy nonspurious timeouts caused by packet losses. Figure 7 shows an example of the poor performance of Reno with Eifel when packet losses occur. The first timeout at second 30 is caused by a delay and is spurious. The Eifel algorithm successfully detects ...
... Apparently, Reno with Eifel suffers from lengthy nonspurious timeouts caused by packet losses. Figure 7 shows an example of the poor performance of Reno with Eifel when packet losses occur. The first timeout at second 30 is caused by a delay and is spurious. The Eifel algorithm successfully detects ...
Routing Protocols - Austin Community College
... • The most common nonroutable protocol is NetBEUI • Other protocols were designed with the ability to move between multiple networks via Network layer addressing • The most common routed protocol suite is TCP/IP ...
... • The most common nonroutable protocol is NetBEUI • Other protocols were designed with the ability to move between multiple networks via Network layer addressing • The most common routed protocol suite is TCP/IP ...
Solving remote access problems
... • Receive connect from PFL and verify access to resource is allowed • Connect to application server using selected protocol • Act as network layer gateway • Send data back to PFL over SSL ...
... • Receive connect from PFL and verify access to resource is allowed • Connect to application server using selected protocol • Act as network layer gateway • Send data back to PFL over SSL ...
The Tenet Architecture for Tiered Sensor Networks
... data fusion on small-form-factor, resource-poor nodes, or motes. We argue that this principle leads to fragile and unmanageable systems and explore an alternative. The Tenet architecture is motivated by the observation that future largescale sensor network deployments will be tiered, consisting of m ...
... data fusion on small-form-factor, resource-poor nodes, or motes. We argue that this principle leads to fragile and unmanageable systems and explore an alternative. The Tenet architecture is motivated by the observation that future largescale sensor network deployments will be tiered, consisting of m ...
Chapter 10: Circuit Switching and Packet Switching Switching
... — Note that if node(i,j) is connected to node(i-1,m), then node(i,m) is connected to node(i-1,j). — Benes network is consisting of two butterflies back to back ...
... — Note that if node(i,j) is connected to node(i-1,m), then node(i,m) is connected to node(i-1,j). — Benes network is consisting of two butterflies back to back ...
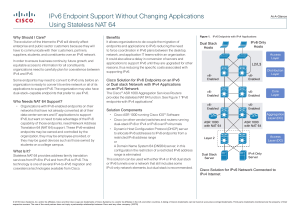
IPv6 Endpoint Support Without Changing Applications Using Stateless NAT 64
... site or campus can still provide access to and from the IPv4 Internet. One important restriction of this solution is that it requires each host in the IPv6 network that needs to communicate with the IPv4 Internet to have a routable IPv4 address at the Cisco ASR 1000, so it does not currently solve t ...
... site or campus can still provide access to and from the IPv4 Internet. One important restriction of this solution is that it requires each host in the IPv6 network that needs to communicate with the IPv4 Internet to have a routable IPv4 address at the Cisco ASR 1000, so it does not currently solve t ...
Network Working Group G. Gross Request for
... PAP/CHAP authentication protocols that are already widely in use for Internet dial up access are leveraged. As a consequence, PPP over FUNI security is at parity with those practices already established by the existing Internet infrastructure. Those applications that require stronger security are en ...
... PAP/CHAP authentication protocols that are already widely in use for Internet dial up access are leveraged. As a consequence, PPP over FUNI security is at parity with those practices already established by the existing Internet infrastructure. Those applications that require stronger security are en ...
Architecting ARINC 664, Part 7 (AFDX) Solutions Summary
... reliance of fly-by-wire and the associated avionics. As more systems are designed into airframes, traditional point-to-point wiring schemes are no longer practical. The designers of the Airbus A380 searched for a solution to reduce the amount of wiring, increase bandwidth, and make use of commercial ...
... reliance of fly-by-wire and the associated avionics. As more systems are designed into airframes, traditional point-to-point wiring schemes are no longer practical. The designers of the Airbus A380 searched for a solution to reduce the amount of wiring, increase bandwidth, and make use of commercial ...
static routing
... • Classful routing protocols do not send subnet mask information in routing updates. • This was at a time when network addresses were allocated based on classes, class A, B, or C. • A routing protocol did not need to include the subnet mask in the routing update because the network mask could be det ...
... • Classful routing protocols do not send subnet mask information in routing updates. • This was at a time when network addresses were allocated based on classes, class A, B, or C. • A routing protocol did not need to include the subnet mask in the routing update because the network mask could be det ...
The Importance of Cybersecurity
... Cybersecurity monitoring has become a key element in the layered security architecture of most enterprise-class networks. It can be used to provide 24 x 7 monitoring of both internal and perimeter networks, detecting and alerting on a range of potential cyber threats. Most cybersecurity monitoring s ...
... Cybersecurity monitoring has become a key element in the layered security architecture of most enterprise-class networks. It can be used to provide 24 x 7 monitoring of both internal and perimeter networks, detecting and alerting on a range of potential cyber threats. Most cybersecurity monitoring s ...
Raising BACnet® to the Next Level
... DIN-rail BAS Router provides a lowcost method of connecting isolated islands of BACnet MS/TP devices to a BACnet/IP Ethernet network. The half-wave rectified low-voltage power supply allows for the sharing of power with other 24 VAC/VDC control devices. The MS/TP port is optically-isolated and is ca ...
... DIN-rail BAS Router provides a lowcost method of connecting isolated islands of BACnet MS/TP devices to a BACnet/IP Ethernet network. The half-wave rectified low-voltage power supply allows for the sharing of power with other 24 VAC/VDC control devices. The MS/TP port is optically-isolated and is ca ...
American Messaging Services Network Interface Guide
... non-secure nature of the Internet. There are several e-mail addresses (domain names) that can be used to send messages to a American Messaging paging device. The different domain names control what parts of the email message are sent to the pager (i.e., “From”, Subject, Date and Message Body). The t ...
... non-secure nature of the Internet. There are several e-mail addresses (domain names) that can be used to send messages to a American Messaging paging device. The different domain names control what parts of the email message are sent to the pager (i.e., “From”, Subject, Date and Message Body). The t ...
Document
... Set up manually, do not change; requires administration Works when traffic predictable & network is simple Used to override some routes set by dynamic algorithm Used to provide default router ...
... Set up manually, do not change; requires administration Works when traffic predictable & network is simple Used to override some routes set by dynamic algorithm Used to provide default router ...
NETWORK LAN PLANNER
... each client shares their resources with Other workstations in the network. Examples of peer-to-peer networks are: Small office networks where resource use is minimal and a home network. A client-server network is where every client is connected to the server and each other. Client-server networks us ...
... each client shares their resources with Other workstations in the network. Examples of peer-to-peer networks are: Small office networks where resource use is minimal and a home network. A client-server network is where every client is connected to the server and each other. Client-server networks us ...
NetScreen-Remote VPN and Security Client Software
... secure, mobile access to private networks has caused network security administrators to place additional requirements on client software. Remote access clients must now provide secure authentication and VPN policy retrieval while remaining easy to deploy and seamless to end users. The software must ...
... secure, mobile access to private networks has caused network security administrators to place additional requirements on client software. Remote access clients must now provide secure authentication and VPN policy retrieval while remaining easy to deploy and seamless to end users. The software must ...
Safe & Secure Environment for Students
... the most of its computing technology – while receiving only appropriate Internet content – Previous filtering solution provided inadequate integration with user directories, ...
... the most of its computing technology – while receiving only appropriate Internet content – Previous filtering solution provided inadequate integration with user directories, ...
signaling transfer point
... talk to Tokyo immediately. If you are lucky, you might be able to do it in an hour, perhaps longer. Waiting hours to complete one phone call in this information era? This era would not have arrived if we still had people sitting at switchboard. The process of establishing connections became automate ...
... talk to Tokyo immediately. If you are lucky, you might be able to do it in an hour, perhaps longer. Waiting hours to complete one phone call in this information era? This era would not have arrived if we still had people sitting at switchboard. The process of establishing connections became automate ...
Aalborg Universitet Planning broadband infrastructure - a reference model
... Document Version Publisher's PDF, also known as Version of record Link to publication from Aalborg University ...
... Document Version Publisher's PDF, also known as Version of record Link to publication from Aalborg University ...