ppt3
... at each layer interacts only with adjacent layers (fig. 16.2) Each frame is nested in next one, from lower layer of stack (fig. 16.4) Each layer at destination receives frame sent from corresponding layer at origin (fig. 16.5) ...
... at each layer interacts only with adjacent layers (fig. 16.2) Each frame is nested in next one, from lower layer of stack (fig. 16.4) Each layer at destination receives frame sent from corresponding layer at origin (fig. 16.5) ...
William Stallings, Cryptography and Network Security 3/e
... Source and destination transport-level address: The transport level (e.g., TCP or UDP) port number, which defines applications such as SNMP or TELNET ...
... Source and destination transport-level address: The transport level (e.g., TCP or UDP) port number, which defines applications such as SNMP or TELNET ...
CS335 Networking & Network Administration
... physical addressing prevent connecting bridged networks with arbitrary technologies ...
... physical addressing prevent connecting bridged networks with arbitrary technologies ...
William Stallings, Cryptography and Network Security 3/e
... Source and destination transport-level address: The transport level (e.g., TCP or UDP) port number, which defines applications such as SNMP or TELNET ...
... Source and destination transport-level address: The transport level (e.g., TCP or UDP) port number, which defines applications such as SNMP or TELNET ...
幻灯片 1 - University of New South Wales
... And it shows the performance obtained by the complete M3Omon system. It also shows the overall performance when instantiating two forensic (offline) applications—one for packets and one for flows—and using all of the available cores for real-time flow record processing. ...
... And it shows the performance obtained by the complete M3Omon system. It also shows the overall performance when instantiating two forensic (offline) applications—one for packets and one for flows—and using all of the available cores for real-time flow record processing. ...
Network
... Location of current fragment in message Number of frame to be acknowledged next Number of 32 bit words in header ...
... Location of current fragment in message Number of frame to be acknowledged next Number of 32 bit words in header ...
What is the internet - New Mexico State University
... Who Pays for It? No one pays for "it"; there is no Internet, Inc. that collects fees from all Internet networks or users. Everyone pays for their part. The NSF pays for NSFNET. NASA pays for the NASA Science Internet. Networks get together and decide how to connect themselves together and f ...
... Who Pays for It? No one pays for "it"; there is no Internet, Inc. that collects fees from all Internet networks or users. Everyone pays for their part. The NSF pays for NSFNET. NASA pays for the NASA Science Internet. Networks get together and decide how to connect themselves together and f ...
Internet Architecture and Assumptions
... • Circuit Switching: Signaling protocol sets up entire path out-ofband. (cf. the phone network) • Virtual Circuits: Hybrid approach. Packets carry “tags” to indicate path, forwarding over IP • Source routing: Complete route is contained in each data packet ...
... • Circuit Switching: Signaling protocol sets up entire path out-ofband. (cf. the phone network) • Virtual Circuits: Hybrid approach. Packets carry “tags” to indicate path, forwarding over IP • Source routing: Complete route is contained in each data packet ...
Security Fundamentals
... (may be confidential data on the way out) • Review network traffic that was blocked and investigate the source of this traffic ...
... (may be confidential data on the way out) • Review network traffic that was blocked and investigate the source of this traffic ...
Firewall
... • imposes security by limiting which such connections are allowed • once created usually relays traffic without examining contents • typically used when trust internal users by allowing general outbound connections • SOCKS commonly used for this ...
... • imposes security by limiting which such connections are allowed • once created usually relays traffic without examining contents • typically used when trust internal users by allowing general outbound connections • SOCKS commonly used for this ...
Firewalking
... • All the work of first gen firewalls but now with more transport layer • Examine each packet as well as its position in the data stream • Records the “state” of the connection ...
... • All the work of first gen firewalls but now with more transport layer • Examine each packet as well as its position in the data stream • Records the “state” of the connection ...
Networks
... The message is split up into packets using notecards: Five words to a packet Each packet also contains the name of the sender and the receiver, as well as the packet number. The routers transmit these packets to the receiving host. They may lose packets or corrupt them by scribbling out or rewri ...
... The message is split up into packets using notecards: Five words to a packet Each packet also contains the name of the sender and the receiver, as well as the packet number. The routers transmit these packets to the receiving host. They may lose packets or corrupt them by scribbling out or rewri ...
Foundations of Networking Networking CS 3470, Section 1 Sarah Diesburg
... Nodes on the inside of the cloud implement the network [switches] Nodes on the outside of the cloud use the ...
... Nodes on the inside of the cloud implement the network [switches] Nodes on the outside of the cloud use the ...
Introduction - Jigar Pandya
... Packet switching is more efficient and robust for data that can withstand some delays in transmission, such as e-mail messages and Web pages. ...
... Packet switching is more efficient and robust for data that can withstand some delays in transmission, such as e-mail messages and Web pages. ...
15-744: Computer Networking
... Goals and Objectives • Understand state-of-the-art in network protocols, architectures, and applications • Understand process of networking research • Typical constraints and thought processes used in networking research ...
... Goals and Objectives • Understand state-of-the-art in network protocols, architectures, and applications • Understand process of networking research • Typical constraints and thought processes used in networking research ...
Welcome to CS 444/544!
... • The Internet’s primary network-level services (used by network programmers): – Connectionless packet delivery • Break messages up into small chunks (called packets) • Route each packet separately through the network • Reassemble message when all packets reach destination ...
... • The Internet’s primary network-level services (used by network programmers): – Connectionless packet delivery • Break messages up into small chunks (called packets) • Route each packet separately through the network • Reassemble message when all packets reach destination ...
Computer Networking
... • The Internet allows distributed applications running on its end-systems to exchange data with each other • The Internet provides two services to its distributed applications: a connection-oriented service and a connectionless service. • Currently the Internet does not provide a service that makes ...
... • The Internet allows distributed applications running on its end-systems to exchange data with each other • The Internet provides two services to its distributed applications: a connection-oriented service and a connectionless service. • Currently the Internet does not provide a service that makes ...
Slides
... DNS is the Internet’s “directory assistance” linking IP names to IP addresses A computer’s IP name tells you a lot; e.g., the type of organization supporting the Web site Top-level domain: the last part of IP names, e.g., ...
... DNS is the Internet’s “directory assistance” linking IP names to IP addresses A computer’s IP name tells you a lot; e.g., the type of organization supporting the Web site Top-level domain: the last part of IP names, e.g., ...
Circuit Switched vs. Packet Switched Technology
... Is used for modem connections across PSTN, ISDN, and T-carriers ...
... Is used for modem connections across PSTN, ISDN, and T-carriers ...
glossary - Homework Market
... (IP). The IP part of TCP/IP; the protocol used to route a data packet from its source to its destination over the Internet. The unique 32 bit number assigned to each computer connected to the Internet and used by the TCP/IP protocol to route packets of data to their destinations. The number is usual ...
... (IP). The IP part of TCP/IP; the protocol used to route a data packet from its source to its destination over the Internet. The unique 32 bit number assigned to each computer connected to the Internet and used by the TCP/IP protocol to route packets of data to their destinations. The number is usual ...
15-744: Computer Networking
... Class Topic Coverage • Little on physical and data link layer • Little on undergraduate material • Supposedly you already know this, though some revisiting/overlap is unavoidable • Focus on the why, not the what ...
... Class Topic Coverage • Little on physical and data link layer • Little on undergraduate material • Supposedly you already know this, though some revisiting/overlap is unavoidable • Focus on the why, not the what ...
Lecture 1 - Department Of Computer Science
... – FDM/TDM: wasteful – the ubiquitous telephone networks Packet switching – store-and-forward: resources are used on demand – queuing delay, packet loss – send/receive messages (packets) – today’s Internet Fall 2005 ...
... – FDM/TDM: wasteful – the ubiquitous telephone networks Packet switching – store-and-forward: resources are used on demand – queuing delay, packet loss – send/receive messages (packets) – today’s Internet Fall 2005 ...
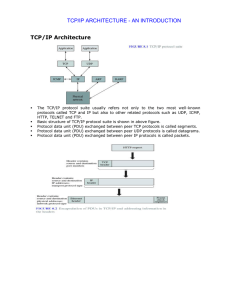
TCP/IP Architecture TCP/IP ARCHITECTURE
... It provides best effort, connectionless packet delivery, packets may be lost, out of order, or even duplicated, so it is the responsibility of higher layer protocols to deal with these, if necessary. The header is of fixed-length component of 20 bytes plus variable-length consisting of options that ...
... It provides best effort, connectionless packet delivery, packets may be lost, out of order, or even duplicated, so it is the responsibility of higher layer protocols to deal with these, if necessary. The header is of fixed-length component of 20 bytes plus variable-length consisting of options that ...