Connected Devices Interfacing (CDI)
... Network Information and Control (NetIC) Generic Enabler will provide to FI-WARE chapters as well as Usage Area applications and services the means to optimally exploit the network capabilities, by means of the implementation of APIs towards networking elements NetIC will provide an abstraction of t ...
... Network Information and Control (NetIC) Generic Enabler will provide to FI-WARE chapters as well as Usage Area applications and services the means to optimally exploit the network capabilities, by means of the implementation of APIs towards networking elements NetIC will provide an abstraction of t ...
Basic Networking Concepts
... -An IP address identifies a host machine on the Internet. -An IP port will identify a specific application running on an Internet host machine. -A port is identified by a number, the port number. -The number of ports is not functionally limited, in contrast to serial communications where only 4 port ...
... -An IP address identifies a host machine on the Internet. -An IP port will identify a specific application running on an Internet host machine. -A port is identified by a number, the port number. -The number of ports is not functionally limited, in contrast to serial communications where only 4 port ...
02-design
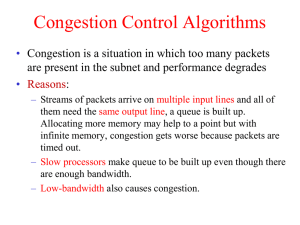
... • Yes, but only to improve performance • If network is highly unreliable • Adding some level of reliability helps performance, not correctness • Don’t try to achieve perfect reliability! • Implementing a functionality at a lower level should have minimum performance impact on the applications that d ...
... • Yes, but only to improve performance • If network is highly unreliable • Adding some level of reliability helps performance, not correctness • Don’t try to achieve perfect reliability! • Implementing a functionality at a lower level should have minimum performance impact on the applications that d ...
Traffic Modeling (1)
... Packet size distribution is bimodal Lots of small packets for interactive traffic and ...
... Packet size distribution is bimodal Lots of small packets for interactive traffic and ...
(P2) Protocols
... SUMMARY – describe why protocols are important (in your words not mine) Eg. Protocols are needed so that different networks and computer system can talk to each other otherwise the Internet would not exist and there would be no such thing as a WAN. As each system is designed, such as email then in o ...
... SUMMARY – describe why protocols are important (in your words not mine) Eg. Protocols are needed so that different networks and computer system can talk to each other otherwise the Internet would not exist and there would be no such thing as a WAN. As each system is designed, such as email then in o ...
1 - Portal UniMAP
... 1. Which layer in the internet model are the network support layers?. The network support layers are the physical, data link, and network layers. 2. What is the difference between network layer delivery and transport layer delivery? The transport layer is responsible for process-to-process delivery ...
... 1. Which layer in the internet model are the network support layers?. The network support layers are the physical, data link, and network layers. 2. What is the difference between network layer delivery and transport layer delivery? The transport layer is responsible for process-to-process delivery ...
15. - 건국대학교
... • With the technologies of multicast or multipoint communication, multi-party calls are not much more difficult than two-party calls. • With advanced multimedia data compression techniques, various degrees of QoS can be supported according to the network traffic. • Good graphics user interfaces can ...
... • With the technologies of multicast or multipoint communication, multi-party calls are not much more difficult than two-party calls. • With advanced multimedia data compression techniques, various degrees of QoS can be supported according to the network traffic. • Good graphics user interfaces can ...
Chapter 5
... Also called flow-based algorithms It was aimed at both unicast and multicast applications. Unicast Example :single user streaming a video clip from a news site ...
... Also called flow-based algorithms It was aimed at both unicast and multicast applications. Unicast Example :single user streaming a video clip from a news site ...
$doc.title
... e. Strict priority scheduling can lead to one flow consuming the entire output rate of a router link. f. Fair queuing protocols try to ensure that each flow (or class of flows) gets to send an eq ...
... e. Strict priority scheduling can lead to one flow consuming the entire output rate of a router link. f. Fair queuing protocols try to ensure that each flow (or class of flows) gets to send an eq ...
Presentation_Sharmistha_Roy
... What is Denial of Service? Attempts to make a Web resources unavailable to legitimate users Attacks flooding a network , creating congestion and blocking Disrupting connections between two machines Why are such attacks launched? Purpose is often to knock web services off Hacker may need to ...
... What is Denial of Service? Attempts to make a Web resources unavailable to legitimate users Attacks flooding a network , creating congestion and blocking Disrupting connections between two machines Why are such attacks launched? Purpose is often to knock web services off Hacker may need to ...
02-Protocols and TCP-IP
... Physical Layer • Physical interface between data transmission device (e.g. computer) and transmission medium or network • Characteristics of transmission medium • Signal levels • Data rates ...
... Physical Layer • Physical interface between data transmission device (e.g. computer) and transmission medium or network • Characteristics of transmission medium • Signal levels • Data rates ...
Selling an Idea or a Product
... Workstations: In a few years, open up a workstation, will see its CPU connected to memory and graphics engine by a switched network, instead of a bus. Multiprocessors are already connected by hooking together lots of small-scale switches. – For instance, in a 2-D mesh, or in a hypercube. ...
... Workstations: In a few years, open up a workstation, will see its CPU connected to memory and graphics engine by a switched network, instead of a bus. Multiprocessors are already connected by hooking together lots of small-scale switches. – For instance, in a 2-D mesh, or in a hypercube. ...
Internet Layer Protocols
... – Process used to track which packets have been received by the destination host ...
... – Process used to track which packets have been received by the destination host ...
TE Solutions
... – Enough resources are allocated to keep the risk of burstlevel overload at the output multiplexer within tolerable limits – Both short- and long-term correlations are important 28 ...
... – Enough resources are allocated to keep the risk of burstlevel overload at the output multiplexer within tolerable limits – Both short- and long-term correlations are important 28 ...
Introduction to the World Wide Web
... Packets (units of information) are routed between nodes over data links shared with other traffic Contrasts with circuit switching, which sets up a dedicated connection between the two nodes for their exclusive use for the duration of the communication like telephone call connection. ...
... Packets (units of information) are routed between nodes over data links shared with other traffic Contrasts with circuit switching, which sets up a dedicated connection between the two nodes for their exclusive use for the duration of the communication like telephone call connection. ...
Overview/Questions Network Addresses Network Addresses
... DNS is updated by an administrator making changes to one DNS server, which are then propagated between servers. ...
... DNS is updated by an administrator making changes to one DNS server, which are then propagated between servers. ...
Practice questions for exam
... 52. What are the four layers of the TCP/IP Model? 53. List four multiple access methods/technologies. 54. Besides bandwidth and latency, what other parameter is needed to give a good characterization of the quality of service offered by a network used for (i) digitized voice traffic? (ii) video traf ...
... 52. What are the four layers of the TCP/IP Model? 53. List four multiple access methods/technologies. 54. Besides bandwidth and latency, what other parameter is needed to give a good characterization of the quality of service offered by a network used for (i) digitized voice traffic? (ii) video traf ...
The Application Layers :On Demand Lecture (Part I)
... private network that uses public telecommunication, such as the Internet, instead of leased lines to communicate. Became popular as more employees worked in remote locations. Terminologies to understand how VPNs ...
... private network that uses public telecommunication, such as the Internet, instead of leased lines to communicate. Became popular as more employees worked in remote locations. Terminologies to understand how VPNs ...
Computer Networks: LANs, WANs The Internet
... packets from different users are multiplexed on links between packet switches ...
... packets from different users are multiplexed on links between packet switches ...
Wireless Networks
... routers adjust their entries, these are stable for a longer time (HA responsible for a MN over a longer period of time) packets to the MN are sent to the HA, independent of changes in COA/FA ...
... routers adjust their entries, these are stable for a longer time (HA responsible for a MN over a longer period of time) packets to the MN are sent to the HA, independent of changes in COA/FA ...
EECS 700: Network Security
... – What if we never receive the last piece – Overlapping fragment – The reassembled packet is larger than the allowed IP packet size (how can attackers do this) ...
... – What if we never receive the last piece – Overlapping fragment – The reassembled packet is larger than the allowed IP packet size (how can attackers do this) ...
AOSDistributedOSCommunication
... delay. Each circuit cannot be used by other callers until the circuit is released and a new connection is set up. Even if no actual communication is taking place, the channel remains unavailable to other users. Channels that are available for new calls are said to be idle. Virtual circuit switching ...
... delay. Each circuit cannot be used by other callers until the circuit is released and a new connection is set up. Even if no actual communication is taking place, the channel remains unavailable to other users. Channels that are available for new calls are said to be idle. Virtual circuit switching ...
Lecture 4a: Communication and Networking
... location to another, a signal must travel along a physical path The physical path that is used to carry a signal between a signal transmitter and a signal receiver is called the "transmission medium" ...
... location to another, a signal must travel along a physical path The physical path that is used to carry a signal between a signal transmitter and a signal receiver is called the "transmission medium" ...
Computer Networks BITS ZC481
... peer by passing messages to some lower level protocol, which in turn delivers the message to its peer. ...
... peer by passing messages to some lower level protocol, which in turn delivers the message to its peer. ...