High Speed Network Traffic Analysis with Commodity Multi
... scheduling, users can manipulate the CPU affinity to make sure that both threads are executed on cores or HyperThreads sharing levels of caches. In this way, multi-core architectures can be fully exploited by leveraging high bandwidth and low-latency inter-core communications. We decided not to imp ...
... scheduling, users can manipulate the CPU affinity to make sure that both threads are executed on cores or HyperThreads sharing levels of caches. In this way, multi-core architectures can be fully exploited by leveraging high bandwidth and low-latency inter-core communications. We decided not to imp ...
True/False: • When a client browser requests a web page and the
... tradition telephone network, which is based on the concept of packet switching. F LANs provide global connections for thousands of computers. F Twisted-pair can achieve very high bandwidth data communication. F Wireless transmission media include cellular telephones, microwave transmission, and fibe ...
... tradition telephone network, which is based on the concept of packet switching. F LANs provide global connections for thousands of computers. F Twisted-pair can achieve very high bandwidth data communication. F Wireless transmission media include cellular telephones, microwave transmission, and fibe ...
CS 497C - Lecture 12
... operating system. – The delivery of data in multiple packets – Ability to divert data immediately through other routines if one or more parts of the network went down. – One hundred percent reliability of transmission with facilities for full error control. ...
... operating system. – The delivery of data in multiple packets – Ability to divert data immediately through other routines if one or more parts of the network went down. – One hundred percent reliability of transmission with facilities for full error control. ...
Aalborg Universitet Algorithm
... One of the most important challenges in network monitoring is how to measure performance of high-speed Multi-hop Networks in a centralized manner. Each network carries data for numerous different kinds of applications, which have different performance requirements. Therefore providing information ab ...
... One of the most important challenges in network monitoring is how to measure performance of high-speed Multi-hop Networks in a centralized manner. Each network carries data for numerous different kinds of applications, which have different performance requirements. Therefore providing information ab ...
A method for classification of network - VBN
... One of the most important challenges in network monitoring is how to measure performance of high-speed Multi-hop Networks in a centralized manner. Each network carries data for numerous different kinds of applications, which have different performance requirements. Therefore providing information ab ...
... One of the most important challenges in network monitoring is how to measure performance of high-speed Multi-hop Networks in a centralized manner. Each network carries data for numerous different kinds of applications, which have different performance requirements. Therefore providing information ab ...
PPT
... Public peering: Traffic is swapped in a specific location, called Internet exchange points (IXPs) Private peering: Two networks establish a direct link to each other. ...
... Public peering: Traffic is swapped in a specific location, called Internet exchange points (IXPs) Private peering: Two networks establish a direct link to each other. ...
network_layer
... • Services provided to TL, receive from DL – Connectionless and connection oriented services – Identifying source and destination uniquely and thereby use NL address. Fragments TL data if necessary. Uses packet switching (store and forward) with datagram approach. – In the router NL finds the approp ...
... • Services provided to TL, receive from DL – Connectionless and connection oriented services – Identifying source and destination uniquely and thereby use NL address. Fragments TL data if necessary. Uses packet switching (store and forward) with datagram approach. – In the router NL finds the approp ...
Data Link Layer
... received signals: easy in wired LANs difficult in wireless LANs: receiver shut off while transmitting Most used protocol in Ethernet ...
... received signals: easy in wired LANs difficult in wireless LANs: receiver shut off while transmitting Most used protocol in Ethernet ...
10-Circuit-Packet
... Must have switching capacity and channel capacity between each pair of switching nodes on path to establish connection Switches must have intelligence to make allocations and device route through network ...
... Must have switching capacity and channel capacity between each pair of switching nodes on path to establish connection Switches must have intelligence to make allocations and device route through network ...
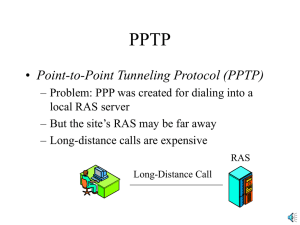
PPTP
... packet, which has the destination IP address of the access concentrator – Adds a new IP header with the IP address of the RAS – Adds an enhanced general routing encapsulation (GRE) header for security Original IP Packet ...
... packet, which has the destination IP address of the access concentrator – Adds a new IP header with the IP address of the RAS – Adds an enhanced general routing encapsulation (GRE) header for security Original IP Packet ...
SUPA - IETF
... 1. The user defined policy received by Service Management, is a high-level (abstracted) one: in the case of a certain event occurs, the adjustment on some objects is needed. E.g., if bandwidth capacity in the link is larger than 80%, detour the traffic flow to other link, like (a) in the figure. ...
... 1. The user defined policy received by Service Management, is a high-level (abstracted) one: in the case of a certain event occurs, the adjustment on some objects is needed. E.g., if bandwidth capacity in the link is larger than 80%, detour the traffic flow to other link, like (a) in the figure. ...
Factsheet - KFSensor
... means of detecting attacks. However they do have significant weaknesses. The increasing quantity and diversity of legitimate network traffic has resulted in ever increasing hardware costs and the large number of false positive alerts generated can be too much to analyse ...
... means of detecting attacks. However they do have significant weaknesses. The increasing quantity and diversity of legitimate network traffic has resulted in ever increasing hardware costs and the large number of false positive alerts generated can be too much to analyse ...
Basic Networking Hardware
... are relatively easy to install and manage, but bottlenecks can occur because all data must pass through the hub. This is not much of a problem anymore with the widespread deployment of switches. ring topology: All devices are connected to one another in the shape of a closed loop, so that each devic ...
... are relatively easy to install and manage, but bottlenecks can occur because all data must pass through the hub. This is not much of a problem anymore with the widespread deployment of switches. ring topology: All devices are connected to one another in the shape of a closed loop, so that each devic ...
Chap 3
... Recording authentication messages from a legitimate user Reissuing those messages in order to impersonate the user and gain access to systems ...
... Recording authentication messages from a legitimate user Reissuing those messages in order to impersonate the user and gain access to systems ...
Domain name - 3.LF UK 2015
... and IP(Internet Protocol) are the most commonly-used protocols for using the Internet. (But there are others at lower levels.) The combination is simply known as TCP/IP. The Internet is a packet switching system. Any message is broken (by TCP) into packets that are transmitted independently across t ...
... and IP(Internet Protocol) are the most commonly-used protocols for using the Internet. (But there are others at lower levels.) The combination is simply known as TCP/IP. The Internet is a packet switching system. Any message is broken (by TCP) into packets that are transmitted independently across t ...
Broadband A to Z Glossary
... Digital Access and Carrier System is when BT provision two lines down the same copper line in order to save space. This can lead to problems as broadband services require a single dedicated line in order to work. When the broadband order is placed, the existence of a DACS line will be highlighted an ...
... Digital Access and Carrier System is when BT provision two lines down the same copper line in order to save space. This can lead to problems as broadband services require a single dedicated line in order to work. When the broadband order is placed, the existence of a DACS line will be highlighted an ...
Chapter 02 - Communicating Over The Network
... Communication in networks is governed by pre-defined rules called protocols. A group of inter-related protocols that are necessary to perform a communication function is called a protocol suite. These protocols are implemented in software and hardware that is loaded on each host and network device N ...
... Communication in networks is governed by pre-defined rules called protocols. A group of inter-related protocols that are necessary to perform a communication function is called a protocol suite. These protocols are implemented in software and hardware that is loaded on each host and network device N ...
click here to
... Port 80 is the standard port number used with HTTP 31. Which characteristics are parts of TCP? TCP is a reliable, connection-oriented protocol. ...
... Port 80 is the standard port number used with HTTP 31. Which characteristics are parts of TCP? TCP is a reliable, connection-oriented protocol. ...
SinoCDN LinkEasy Solution
... infrastructure service provider, they can control the revenue of new service by themselves – New value-added services can leverage the core business and generate more revenue – Hotel, Hotspots & Cafe can promote their core business services in promotion web page through LE-SP ...
... infrastructure service provider, they can control the revenue of new service by themselves – New value-added services can leverage the core business and generate more revenue – Hotel, Hotspots & Cafe can promote their core business services in promotion web page through LE-SP ...
Follow this link to lec1d handout
... First end-to-end layer Uses the network to (most often) provide higher layers with a connection oriented, reliable, error free channel that delivers messages (or byte stream) in order May provide other types of services Often performs multiplexing of multiple transport connections over one or more n ...
... First end-to-end layer Uses the network to (most often) provide higher layers with a connection oriented, reliable, error free channel that delivers messages (or byte stream) in order May provide other types of services Often performs multiplexing of multiple transport connections over one or more n ...
Rapid Deployment of IP-based VSAT Networks - ITU
... – NOC Technicians provide first- and second-level RF, data and network troubleshooting – Full-time degreed engineers support third-level data and network support – As a value-added feature, MTN gives customers access to Web-Based monitoring tools that provides real-time system status and bandwidth u ...
... – NOC Technicians provide first- and second-level RF, data and network troubleshooting – Full-time degreed engineers support third-level data and network support – As a value-added feature, MTN gives customers access to Web-Based monitoring tools that provides real-time system status and bandwidth u ...
User News Network
... A local area network is a collection of computers that share hardware, software, and data over a shorter geographical area than a WAN. (Usually limited to a single building or compound). A LAN can also be very small. Example: LAN in my apartment contains one PC, one printer, and two laptops. ...
... A local area network is a collection of computers that share hardware, software, and data over a shorter geographical area than a WAN. (Usually limited to a single building or compound). A LAN can also be very small. Example: LAN in my apartment contains one PC, one printer, and two laptops. ...