Fluke Networks gives you valuable insight into Cisco
... Cisco Performance Routing (PfR) utilizes NetFlow and IP SLA data and the intelligence of the Cisco IOS infrastructure to improve application performance and availability. PfR can automatically identify the best path for each application based on advanced criteria such as, reachability, delay, loss, ...
... Cisco Performance Routing (PfR) utilizes NetFlow and IP SLA data and the intelligence of the Cisco IOS infrastructure to improve application performance and availability. PfR can automatically identify the best path for each application based on advanced criteria such as, reachability, delay, loss, ...
pptx
... proxy server, which evaluates the request. If it is determined to be valid, the proxy server makes the service request on behalf of the client. The proxy server can be disabled for specific applications (HTTP, Database, Email, etc.) ...
... proxy server, which evaluates the request. If it is determined to be valid, the proxy server makes the service request on behalf of the client. The proxy server can be disabled for specific applications (HTTP, Database, Email, etc.) ...
Basic Concepts
... Figure 1-11: Internets • Single LANs Versus Internets – In single networks (LANs and WANs), all devices connect to one another by switches—our focus so far. – In contrast, an internet is a group of networks connected by routers so that any application on any host on any single network can communica ...
... Figure 1-11: Internets • Single LANs Versus Internets – In single networks (LANs and WANs), all devices connect to one another by switches—our focus so far. – In contrast, an internet is a group of networks connected by routers so that any application on any host on any single network can communica ...
8. managing data resources
... Protocol flaws Impersonation Spoofing Message Confidentiality / Integrity threats Web Site Defacement Denial of Service (DOS) Distributed Denial of Service (DDOS) Active or Mobile Code Threats Complex Attacks Source: Pfleeger & Pfleeger ...
... Protocol flaws Impersonation Spoofing Message Confidentiality / Integrity threats Web Site Defacement Denial of Service (DOS) Distributed Denial of Service (DDOS) Active or Mobile Code Threats Complex Attacks Source: Pfleeger & Pfleeger ...
ZMS - TSC Innovation Co.,Ltd.
... In today’s competitive landscape, service providers recognize that to attract new subscribers, they need to be able to quickly roll out and provision new services. ZMS Configuration Manager allows service providers to completely automate the provisioning of subscribers and various network objects. T ...
... In today’s competitive landscape, service providers recognize that to attract new subscribers, they need to be able to quickly roll out and provision new services. ZMS Configuration Manager allows service providers to completely automate the provisioning of subscribers and various network objects. T ...
Courseware Outline
... certified and 91% of hiring managers indicate CompTIA certifications are valuable in validating IT employee skills and expertise. Dell, HP, Sharp, Xerox and Ricoh are among the companies that employ Network+ certified staff and it is supported by top organizations, such as Apple, Best Buy, Canon, Ci ...
... certified and 91% of hiring managers indicate CompTIA certifications are valuable in validating IT employee skills and expertise. Dell, HP, Sharp, Xerox and Ricoh are among the companies that employ Network+ certified staff and it is supported by top organizations, such as Apple, Best Buy, Canon, Ci ...
Quality of Service on JANET
... – Clash of flows in some output interface is allowed (flows’ routes are not under control) – Reasonable hierarchical design of a network decreases the clash probability ...
... – Clash of flows in some output interface is allowed (flows’ routes are not under control) – Reasonable hierarchical design of a network decreases the clash probability ...
Basic Concepts
... Figure 1-11: Internets • Single LANs Versus Internets – In single networks (LANs and WANs), all devices connect to one another by switches—our focus so far. – In contrast, an internet is a group of networks connected by routers so that any application on any host on any single network can communica ...
... Figure 1-11: Internets • Single LANs Versus Internets – In single networks (LANs and WANs), all devices connect to one another by switches—our focus so far. – In contrast, an internet is a group of networks connected by routers so that any application on any host on any single network can communica ...
Heterogeneity-aware Ad hoc Networking
... – Node Heterogeneity: There exist various types of mobile hosts with different characteristics, roles, capacities, and mobility patterns. • e.g.) In the military scenarios, the troop leader usually have more capable networking equipment than the private soldiers. ...
... – Node Heterogeneity: There exist various types of mobile hosts with different characteristics, roles, capacities, and mobility patterns. • e.g.) In the military scenarios, the troop leader usually have more capable networking equipment than the private soldiers. ...
356961: Internet Protocols - ECSE - Rensselaer Polytechnic Institute
... They’re fast, but they’re custom-made for each application and expensive to build. Time to market for new implementations is extremely long, since algorithms must be implemented at the transistor/gate level. Network processors look to avoid these pitfalls by introducing specialized, software control ...
... They’re fast, but they’re custom-made for each application and expensive to build. Time to market for new implementations is extremely long, since algorithms must be implemented at the transistor/gate level. Network processors look to avoid these pitfalls by introducing specialized, software control ...
Serverland Clean-up
... • Interior Gateway Routing Protocol (IGRP) – IGRP was developed by Cisco in the mid 80s – The goal was to provide a robust routing protocol with an autonomous system – Autonomous system is collection of networks under a common administration sharing a common routing strategy – Can also be thought of ...
... • Interior Gateway Routing Protocol (IGRP) – IGRP was developed by Cisco in the mid 80s – The goal was to provide a robust routing protocol with an autonomous system – Autonomous system is collection of networks under a common administration sharing a common routing strategy – Can also be thought of ...
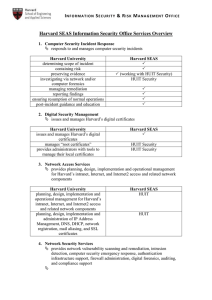
Harvard SEAS Information Security Office Services Overview
... monitors network traffic in real-time to detect anomalous behavior that may indicate computer attack, compromised machine, data breach, etc Harvard University monitors network traffic in real-time aggregates and correlates security data from network and system infrastructure ...
... monitors network traffic in real-time to detect anomalous behavior that may indicate computer attack, compromised machine, data breach, etc Harvard University monitors network traffic in real-time aggregates and correlates security data from network and system infrastructure ...
END TERM EXAMINATION (MODELQUESTION PAPER WITH
... that the packets can be sent quickly and easily. ATM is connection oriented, which means that data sent through the ATM network will always follow the same pre-defined path with the data arriving in the order it was sent. Advantages of ATM Network The high-level benefits delivered through ATM servic ...
... that the packets can be sent quickly and easily. ATM is connection oriented, which means that data sent through the ATM network will always follow the same pre-defined path with the data arriving in the order it was sent. Advantages of ATM Network The high-level benefits delivered through ATM servic ...
Detecting Flood-based Denial-of-Service Attacks with SNMP/RMON Abstract
... packet size, and packet transmission error events. Using RMON data polled from a live enterprise network, we have developed a detection algorithm for simulated flood-based DoS attacks that achieves a high detection rate and low false alarm rate. The detection algorithm relies not only on the raw RMO ...
... packet size, and packet transmission error events. Using RMON data polled from a live enterprise network, we have developed a detection algorithm for simulated flood-based DoS attacks that achieves a high detection rate and low false alarm rate. The detection algorithm relies not only on the raw RMO ...
IPSec
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
Péter Hága - Department of Physics of Complex Systems
... • DAG cards for precise timing in dispersion curves • Appropriate neural network was used (due to the different scale than the simulations) • Experiments series performed between 11 ETOMIC nodes in all-to-all fashion • Periodically collected data since the autumn of 2006 ...
... • DAG cards for precise timing in dispersion curves • Appropriate neural network was used (due to the different scale than the simulations) • Experiments series performed between 11 ETOMIC nodes in all-to-all fashion • Periodically collected data since the autumn of 2006 ...
Mapping of scalable RDMA protocols to ASIC/FPGA platforms
... Master Channel Multiplexer To coding blocks (e.g. Turbo-coding/BCH) 2005 MAPLD/1006 ...
... Master Channel Multiplexer To coding blocks (e.g. Turbo-coding/BCH) 2005 MAPLD/1006 ...
JA2315061508
... aspects. OBS burst immediately follow their request headers without waiting for a reservation acknowledgement. Burst may use bandwidth along several links and still be blocked and lost without completing their routers. In circuit switching, transmission starts after end to end reservation is acknowl ...
... aspects. OBS burst immediately follow their request headers without waiting for a reservation acknowledgement. Burst may use bandwidth along several links and still be blocked and lost without completing their routers. In circuit switching, transmission starts after end to end reservation is acknowl ...
Chapter 7
... – An Internet service provider is a company that offers Internet access to individuals, businesses, and smaller ISPs – Data is exchanged using TCP/IP, which is a protocol that divides information into packets of data • Packets are sent to their destinations through routers Practical PC, 7th Edition ...
... – An Internet service provider is a company that offers Internet access to individuals, businesses, and smaller ISPs – Data is exchanged using TCP/IP, which is a protocol that divides information into packets of data • Packets are sent to their destinations through routers Practical PC, 7th Edition ...
No Slide Title
... • Extensive data applications capability • Inter-working with public networks • Use of control room gateways in public safety and other sectors ...
... • Extensive data applications capability • Inter-working with public networks • Use of control room gateways in public safety and other sectors ...
the network and its role in digital imaging and communications in
... points create entry points for outside equipment. Wardriving is the practice of driving around a neighborhood with network sensing gear and high-gain antennas, looking for unsecured access points.7 Once an unauthorized individual has a connection through an access point, he can perform illegal netwo ...
... points create entry points for outside equipment. Wardriving is the practice of driving around a neighborhood with network sensing gear and high-gain antennas, looking for unsecured access points.7 Once an unauthorized individual has a connection through an access point, he can perform illegal netwo ...
Module 9 VLAN Trunking Protocol
... VLANs help manage broadcast domains VLANs can be defined on port groups, users or protocols LAN switches and network management software provide a mechanism to create VLANs ...
... VLANs help manage broadcast domains VLANs can be defined on port groups, users or protocols LAN switches and network management software provide a mechanism to create VLANs ...
old_Ch1
... will be 51.2 microsecs. This is the maximum roundtrip delay that can be incurred on an 802.3 LAN operating at 10Mbps, 2.5Km long and using 4 repeaters (introduce approx. a 20 bit delay) and includes a safety factor to makeup for node detection delays. Recall that collision detection takes at least t ...
... will be 51.2 microsecs. This is the maximum roundtrip delay that can be incurred on an 802.3 LAN operating at 10Mbps, 2.5Km long and using 4 repeaters (introduce approx. a 20 bit delay) and includes a safety factor to makeup for node detection delays. Recall that collision detection takes at least t ...
Lectures 26&27 - Electrical and Computer Engineering
... infrastructure to employ “open” interfaces at appropriate points, so that portions of it can be provided by different suppliers; and so that we can accommodate multiple types of physical layer transmission media: wires, coaxial cable, fiber, wireless • We would like our local communication infrastru ...
... infrastructure to employ “open” interfaces at appropriate points, so that portions of it can be provided by different suppliers; and so that we can accommodate multiple types of physical layer transmission media: wires, coaxial cable, fiber, wireless • We would like our local communication infrastru ...