* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download old_Ch1
Net neutrality wikipedia , lookup
Distributed firewall wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Net neutrality law wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Computer network wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Deep packet inspection wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Internet protocol suite wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Zero-configuration networking wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
ICS 156: Networking Lab
Magda El Zarki
Professor, ICS
UC, Irvine
Course Outline
Ch 1: Introduction
Ch 2:Bridges
Ch 3:Routers
Ch 4: Transport Protocols
Ch. 1 Introduction (1/2)
Layered Architectures
The TCP/IP (or Internet) Architecture
A Networking Example
IP Addressing
Packet Encapsulation
Port Numbers
Internet Standards
802.3/Ethernet
IP
Ch 1. Introduction. (2/2)
Address Resolution Protocol
Internet Control Message Protocol
Ping
Traceroute
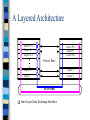
1.1 Layered Architectures
Networking protocols are developed in layers
so as to simplify the task of 1) developing
new services and 2) upgrading and
maintaining the system.
Each layer performs a well defined function.
The internals of a layer can be changed
without affecting the neighboring layers.
Layers exchange information via clearly
specified interfaces.
Layers communicate on a peer to peer basis.
A Layered Architecture
Layer N+1
Layer N
Layer N-1
Layer N+1
Layer N
Layer N-1
Peer to Peer
Layer 2
Layer 2
Layer 1
Layer 1
NETWORK
Inter Layer Data Exchange Interface
The 5 Basic Layers
Layer 1: Physical Layer - mechanical and
electrical network interface definitions
Layer 2: Data Link Layer - framing, data
transparency, error control over one link/trunk
Layer 3: Network Layer - routing, addressing, call
set-up and clearing across the data network, flow
control (internal and external)
Layer 4: Transport Layer - end-to-end message
transfer, connection management, error control
Layer 5: Application Layer – user processes
Ch. 1 Introduction
Layered Architectures
The TCP/IP (or Internet) Architecture
A Networking Example
IP Addressing
Packet Encapsulation
Port Numbers
Internet Standards
802.3/Ethernet
IP
1.2 The TCP/IP Suite
File Transfer Protocol (FTP)
Remote terminal login (TELNET)
Simple Mail Transfer Protocol (SMTP)
Name Server Protocol (NSP)
Simple Network Mmgt. Protocol (SNMP)
Transport Control
User Datagram
Protocol (TCP)
Protocol (UDP)
Internet Protocol (IP)
IEEE 802.X or X.25 or Token Ring
NETWORK Media
Ch. 1 Introduction
Layered Architectures
The TCP/IP (or Internet) Architecture
A Networking Example
IP Addressing
Packet Encapsulation
Port Numbers
Internet Standards
802.3/Ethernet
IP
1.3 A Networking Example
COMPUTER A
COMPUTER B
Application
Application
5
5
4
3
2
1
4
3
2
1
2
1
Router
NETWORK
3
2
1
Ch. 1 Introduction
Layered Architectures
The TCP/IP (or Internet) Architecture
A Networking Example
IP Addressing
Packet Encapsulation
Port Numbers
Internet Standards
802.3/Ethernet
IP
1.4 IP Addressing
Every device on an internet must have a
unique address (just like everyone on
the phone network has a unique
telephone number!).
Each network element and attached
host has two addresses:
– Physical Address and Network Address
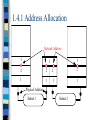
1.4.1 Address Allocation
Network Address
3
3
3
2
2
1
1
2
2
1
1
Physical Address
Subnet 1
Subnet 2
1.4.2 Addresses and Names
The physical address is generally a flat address
whereas the network address is generally
hierarchical.
The network address is referred to as an IP
address, and is the address of the network
interface.
In addition to network addresses, hosts are often
given a name too. The name makes it easier for
people to remember. They are generally
hierarchical too, identifying subnet and net where
host is located.
Addressing Example
Host A
Host A:
Name: pender.ee.upenn.edu
Net Address: 130.91.5.20
Phy Address: AC-12-34-E3-D2-45
Host B Host B:
Name: pongo.ee.upenn.edu
Net Address: 130.91.5.21
Phy Address: 12-AE-01-D3-87-11
Multiple addresses per Device
A network device that connects to several
networks, will have a network address for each
network it is connected to and it will also have a
physical address per network interface.
A Router is a perfect example of a device that has
more than one network address.
A Multiple Interface Device
Network Addresses
Net 1
128.3.2
Net 2
128.3.4
128.3.4.1
128.3.2.3
AC-DA-14-53-28-00
128.3.1.2
AC-DA-14-57-61-02
128.3.3.1
Physical Addresses
Net 3 128.3.3
Net 4
128.3.1
1.4.3 Address Mapping
Tables map names to network addresses.
Domain Name Servers are used to help find
adresses.
Tables also map network addresses to physical
addresses. If a physical address is not found in
the table, a protocol is used to locate the host
and obtain its physical address (ARP and
RARP).
1.4.4 Structure of IP Addresses
IPv4 uses 32 bits for addressing, whereas IPv6
has assigned 128 bits.
Both IPv4 and IPv6 have a particular structure for
their address space: it is partially hierarchical, it
has an internet routing part and a local routing
part.
Subnet addressing was introduced to facilitate
the routing and administration within
organizations. If forms part of the local part and
does not affect the internet routing.
IPv4 has 5 address classes. An organization is
assigned an address space in a class based upon
its size.
1.4.5 IPv4 Address Classes
0 Net ID 7 bits Host ID 24 bits
10
Net ID 14 bits
110
Class A
Host ID 16 bits
Net ID 21 bits
Class B
Host ID 8 bits Class C
11 1 0
Multicast
1 1 1 1
Reserved
Internet Routing part
1 0 Net ID
Local Routing Part
Subnet ID
Host ID
Class A/B/C
Class B with subnet
1.4.6 Addressing Formats
IP addresses are represented in dotted decimal
format. Each 8 bits (byte) is represented by a
decimal number. The 4 bytes are separated by
dots:
– 00001010 00000000 00000000 00000000 =
10.0.0.0 = Class A, net ID: 10
– 10000000 00000011 00000010 00000011 =
128.3.2.3 = Class B, net ID: 128.3, host ID: 2.3
– 11000000 00000000 00000001 11111111 =
192.0.1.255 = Class C, net ID: 192.0.1, host ID:
all hosts (broadcast)
Ch. 1 Introduction
Layered Architectures
The TCP/IP (or Internet) Architecture
A Networking Example
IP Addressing
Packet Encapsulation
Port Numbers
Internet Standards
802.3/Ethernet
IP
1.5 Encapsulation
User data -> application header/trailer -> TCP
(or UDP) header/trailer -> IP header/trailer ->
data link layer header (e.g. Ethernet
header)/trailer.
When the TCP/UDP header is attached the
packet is called the TCP/UDP segment.
When the IP header is attached it is referred
to as the IP datagram.
When the data link layer header is attached, it
is called the link frame (e.g., Ethernet frame)
Ch. 1 Introduction
Layered Architectures
The TCP/IP (or Internet) Architecture
A Networking Example
IP Addressing
Packet Encapsulation
Port Numbers
Internet Standards
802.3/Ethernet
IP
1.6 Port Numbers
TCP and UDP use port numbers to identify the
application.
The port numbers are 16 bits.
Servers are assigned well known port numbers,
e.g., FTP is assigned TCP port number 21, telnet
is assigned TCP port number 23.
These port numbers are assigned by the Internet
Assigned Numbers Authority (IANA).
Ports 1 to 1023 are all well known (listed in
/etc/services).
Clients are allocated ephemeral port numbers
between 1024 and 5000. They are short lived.
Ch. 1 Introduction
Layered Architectures
The TCP/IP (or Internet) Architecture
A Networking Example
IP Addressing
Packet Encapsulation
Port Numbers
Internet Standards
802.3/Ethernet
IP
1.7 Internet Standards
The Internet is run by several standards
organizations.
The Internet Engineering Task Force (IETF) is
responsible for near term planning and
develops the specifications that become the
Internet standards.
The Internet Research Task Force (IRTF) is
responsible for long term planning. They do not
produce any standards.
The Internet Architecture Board (IAB) oversees
the work of the IETF and IRTF. It makes sure that
all the standards are coherent and correct
before final approval.
The Internet Society (ISOC) is responsible for
the overall growth and global reach of the
Internet. It oversees the IAB.
1.7.1 Request for Comments
(RFCs)
All Internet related standards are published
as RFCs.
An RFC index indicates the latest version of
an RFC.
An RFC, called the IAB Official Protocol
Standards, specifies the status of all the
RFCs, i.e., whether or not it is a standard,
and what its recommendation is.
The meaning of RFCs
Each protocol has a standardization
state: standard, draft standard,
proposed standard, experimental,
informational, or historic.
Each protocol also has a requirement
level: required, recommended, elective,
limited use or not recommended.
Ch. 1 Introduction
Layered Architectures
The TCP/IP (or Internet) Architecture
A Networking Example
IP Addressing
Packet Encapsulation
Port Numbers
Internet Standards
802.3/Ethernet
IP
1.8 Ethernet/802.3
LAN Architecture
Topology
CSMA/CD Media Access Control (MAC)
The Frame: Format and Structure and
Uses.
1.8.1 The 802.3 and Ethernet
Architectures
Ethernet only consists of one single layer, the
Media Access Control (MAC) layer
IEEE 802.3 has two sublayers:
– The Media Access Control sub-layer (MAC):
responsible for gaining access to the shared
medium. It is topology dependent.
– The Logical Link Control sub-layer (LLC):
responsible for reliable communications over a
LAN and provides a unified interface to the
network layer, i.e., hides the underlying LAN
from the upper layers.
The 802.3 Layers
Logical Link Control
Data Link Layer
Media Access Control
Physical Layer
Slight Differences in Format
Ehternet was developed by Xerox in the late 70’s
and was so popular that it developed into the
IEEE 802.3 standard.
Ethernet and 802.3 are very similar except for the
LLC sublayer and one field in the header. The
length field in 802.3 is used for packet type in
Ethernet. The type field in 802.3 is contained in
the 8 extra bytes of header of the LLC.
The IEEE 802.3 standard refers to a whole family
of CSMA/CD systems that range from 1 to
10Mbps on various media.
1.8.2 Ethernet/802.3 Topologies
Bus Topology
Hub Topology
Hosts or Nodes
Two way Broadcast Bus
Passive Bus Connectors
Internal Broadcast Bus
1.8.3 The MAC: Based on
CSMA/CD
A broadcast bus - stations transmit in both
directions
Stations sense the channel before they transmit
When channel is sensed idle they transmit
Stations listen while transmitting
Two stations or more could start transmission at
approx. the same time -> a collision results
CSMA/CD
When a collision is detected, stations
abort their transmission. Note only
transmitting stations can detect a
collision (compare signal they detect
on the bus to what they are sending)!
Stations involved in the collision wait
a random period of time and repeat
the process starting with 2 above.
Operation of CSMA/CD 1/2
Inter transmission Gap 9.7microsecs
Successful
Collisions
Contention Periods
Idle
Operation of CSMA/CD2/2
The vulnerable period on the bus is defined as
the time from when a station transmits its first bit
to the time when the furthest station on the bus
has sensed the transmission (the worst case is
one propagation delay on the bus, related to the
two stations attached to the end points of the
bus).
A contention period consists of: one propagation
delay for vulnerable period plus another
propagation delay for the transmitting station to
detect the collision (worst case!).
1.8.4 Types of CSMA/CD
When channel is sensed busy, stations wait till it
becomes idle and then schedule their
transmission. If length of busy period is long,
several stations could become active during that
period and a collision becomes inevitable when
the channel becomes idle again. This is called
persistent CSMA/CD. (IEEE 802.3 and Ethernet)
Non persistent CSMA/CD has stations wait a
random period whenever the channel is sensed
busy, i.e, not grab it immediately it becomes
available. Non persistent gives better throughput
under heavy loading, persistent gives better
throughput under light loads.
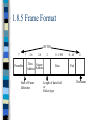
1.8.5 Frame Format
BYTES
1
7
Preamble
2-6
2-6
2
Dest. Source
Address Address
Start of Frame
Delimiter
0 - 1500
Data
Length of data field
or
Packet type
0 - 46
4
Pad
Checksum
Frame Fields (1/2)
Preamble is 7 bytes of 10101010 and Start of
Frame is 10101011
Addresses:
– first bit =1 -> group address - multicast,
– all address bits 1’s -> broadcast to whole system,
– second bit =1 -> global address - set by IEEE,
– second bit =0 local address set by network
administrator.
Frame Fields 2/2
Length field used by 802.3 standard, packet type
field used by Ethernet, indicates whether network
layer is IP, IPX, AppleTalk, etc. In 802.3 the type
field is included in the LLC header.
Data field can be anywhere from 0 to 1500 bytes.
PAD field used by MAC to make ensure that
minimum frame length is 64 bytes. (when data
=0bytes, pad =46 or 38 bytes)
Frame Requirements
Why do we need a minimum length? Minimum
length of 64 bytes guarantees that frame length
will be 51.2 microsecs. This is the maximum
roundtrip delay that can be incurred on an 802.3
LAN operating at 10Mbps, 2.5Km long and using
4 repeaters (introduce approx. a 20 bit delay) and
includes a safety factor to makeup for node
detection delays. Recall that collision detection
takes at least two roundtrip delays for worst case
scenario! If a station transmits a shorter frame, it
will have terminated its transmission before
discovering that it was involved in a collision.
Checksum used to detect errors (discarded)
1.8.5 Collisions
When a collision is detected by the transmitting
station it aborts its transmission and transmits a
JAM signal. This signal is 32-48 bits long.
The NIC then computes a random wait period
according to the following algorithm (binary
exponential backoff):
After n collisions, choose K at random from
{0,1,2,3,...,2m-1}, where m = min{n,10}. The node
waits K x 512 bit times before scheduling a
transmission.
Ch. 1 Introduction
Layered Architectures
The TCP/IP (or Internet) Architecture
A Networking Example
IP Addressing
Packet Encapsulation
Port Numbers
Internet Standards
802.3/Ethernet
IP
1.9 The Internet Protocol - IP
Provides connectionless service - Datagram
It has evolved over time, currently version 6 is
being deployed (IPv6).
The IP layer is responsible for routing over
subnets. It operates end to end over a subnet.
Routers are devices that operate at layer 3 and are
used to interconnect subnets. They are responsible
for routing.
1.9.1 IP in Operation
Network Address
3
IP
2
2
1
1
Subnet 1
3
3
2
IP
1
2
1
Subnet 2
IP and Routers
Host
Host
End-to-End Transport
4
Router
Router
Router
4
3
3
3
3
3
2
2
2
2
2
1
1
1
1
1
Subnet 1
Subnet 2
Subnet 3
Subnet 4
1.9.2 IP Packet Format
16 bits
Version No.
Header Length
Type of Service
Total Length
Identification
Fragment Offset
D M
Time-to-live
Protocol
Header Checksum
Source IP Address
Destination IP Address
Options (0-40 bytes)
Data
1.9.3 Packet Fields 1/5
Version No.: Identifies version of IP used
Header Length: Minimum 5 32 bit words
(without options)
Type of Service: Precedence - Priority 0-7
• D: Low Delay
• T: High Throughput
• R: High reliability
IP Packet Fields 2/5
Total length of IP Datagram: Max 65,535 bytes
Identification: When datagrams are fragmented,
this field is used to uniquely identify the datagram
fragments
Flags -3bits: First is unused, 2nd is D bit
indicating that IP packet/datagram should not be
fragmented, 3rd is M bit indicating whether this is
last fragment of a datagram or not (more bit!).
IP Packet Fields 3/5
Fragment Offset: 13 bits used to indicate position
of this fragment in the original unfragmented
packet. Measured in 8 byte units.
Time to live: Set by source and decremented by
routers as the packet passes though them. When is
reaches 0 packet is discarded. This prevents
eternal looping of packets.
Protocal: Indicates the Transport Layer protocol
being used. E.g., UDP 17, TCP 6, OSPF 89, etc.
IP Packet Fields 4/5
Header Checksum: Adds all the 16 bit fields of the
header using 1’s complement and then obtains the
inverse. Can be set to all 0’s if underlying subnet
uses error detection.
Source IP Address: 32 bits
Destination IP Address: 32 bits
Options: Can be used to enhance the capability of
IP. Must be a multiple of 4 bytes,if not padding
used. Allows the following:
IP Packet Fields 5/5
Strict source routing: identifies path to be
followed
Loose source routing: identifies some nodes to be
passed
Record route: records all nodes it passed through
Time stamping: Nodes append address and time
packet was processed
Stream Identification: indicates type of data
carried, e.g., voice
Data: Transport layer information
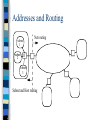
1.9.4 Addresses, Subnetting and
Subnet Masks
When a router is introduced into a network, a
new subnet is created.
Recall that each network interface on a router
has a unique network (IP) address.
The addresses must be on a different (sub)
network.
Routers and hosts use subnet masks to
identify which part of the address to use for
routing.
Addresses and Routing
Net routing
subnet
1
subnet
2
R
subnet
3
Subnet and Host routing
Subnetting and Routers
Network Addresses
Net 1
128.3.2
Net 2
128.3.4
128.3.4.1
128.3.2.3
AC-DA-14-53-28-00
128.3.1.2
AC-DA-14-57-61-02
128.3.3.1
Physical Addresses
Net 3 128.3.3
Net 4
128.3.1
Subnets and Subnet Masks
The previous example showed 4 network
interfaces with the following addresses:
128.3.2.3, 128.3.4.1, 128.3.1.2, 128.3.3.1
This is a class B address, 128.3 indicates the
internet routing part.
The 2.3, 4.2, 1.2 and 3.1 digits at the end of
the address form the host and subnet
address. The subnet and the host address
consist of 8 bits each in this example.
Subnets and Addresses 1/2
Can you think of an example where the
subnet address consists of 4 bits and the host
address of 12 bits?
– 16.1, 32.1, 17.1
Why?
– 16.1 = 00010000.00000001 (subnet 1, host 1)
– 32.1 = 00100000.00000001 (subnet 2, host 1)
– 17.1 = 00010001.00000001 (subnet 1, host 257)
What is the subnet mask in this case?
255.255.240.0 (11111111.11111111.11110000.00000000)
Subnet Masks and Addresses 2/2
New Format for Subnet Masks:
– 130.91.66.100/24, or 130.91.66.100/22
If we use 4 bits for subnetting how many
subnets can we have?
– > 24=16. Note that this is true for the new Internet
routing protocols (RIP II, OSPF, etc.) called
classless routing algorithms. The old classfull
routing algorithms did not allow all 1’s or all 0’s.
New routing algortihms send subnet mask along
with IP address, old algorithms relied on IP
address class recognition (A, B, C, etc.)
Subnet Masks
If we have the following two addresses and
corresponding subnet masks:
130.91.17.17/24 and 130.91.17.49/28
– How would host “1” with its subnet mask of 24
interpret the address of host “2”?
• Would recognize it as a host on the same subnet (subnet
ID=17) with host ID 49!
– How would host “2” with its subnet mask of 28
interpret the address of host “1”?
• Would recognize it as a host on a different subnet. Its
subnet ID is 275 whilst other subnet ID is 273!
Ch 1. Introduction
Address Resolution Protocol
Internet Control Message Protocol
Ping and Traceroute
1.10 ARP 1/3
When a network device wants to transmit a packet
to another device it needs to know both the IP
address and the physical address of the destination.
IP address to physical address mapping is
maintained in the ARP cache.
The ARP cache is constantly updated.
Network devices can identify local and remote
addresses using the subnet mask.
1.10 ARP 2/3
For a remote address the IP address of the default
router is used for looking up a physical address. (IP
routing table)
• The IP module will look up the IP address in the ARP cache. If
it does not find an entry then it uses ARP to find the physical
address.
The ARP module will send a broadcast message asking
for the destination physical address. As all network
devices read broadcasts, the destination will read the
request and respond to the source with its physical
address.
1.10 ARP 3/3
Note that for a remote address the router will
respond to the ARP message. Routers recognize
remote addresses by using subnet masks. This is
called a Proxy ARP.
The router will assume responsibility for all
packets addressed to the remote host and forward
them accordingly. In other words, the router will
pretend to be the host to the ARP request and send
its physical address so that all packets will be
directed to it.
Ch 1. Introduction
Address Resolution Protocol
Internet Control Message Protocol
Ping and Traceroute
1.11 Internet Control Message
Protocol (ICMP) 1/3
This protocol is used by the IP layer to carry out
certain functions associated with network
management/status.
Functions of the ICMP:
– Error reporting: why a datagram that was not
discarded due to errors was not delivered to the
destination
– Reachability testing: sometimes certain destinations
don’t respond, an echo message is sent to which the
host must respond if it is up.
1.11 ICMP 2/3
– Congestion control: when datagrams are dropped
because of buffer overflow, a source quench message is
sent.
– Route-change information: when a router realizes that
a host should be using a different router to reach a
destination it sends a message with the updated routing
information.
– Performance measuring: a network manager can
check the time it takes to send datagrams to particular
locations.
– Subnet addressing: a host can request for the subnet
mask of its local network from the router.
1.11 ICMP 3/3
ICMP messages are carried (encapsulated)
within IP datagrams.
The ICMP message has a common 4 byte
header:
– 1 byte indicates message type
– 1 byte indicates the code
– 2 bytes are used for checksum
When reporting error messages, its data field
contains the IP header (incl. Options) and the
8 bytes that follow the IP header (indicating
TCP, or UDP, port numbers, etc.) of the
message in error.
Ch 1. Introduction
Address Resolution Protocol
Internet Control Message Protocol
Ping and Traceroute
1.12 Ping and Traceroute
Ping: Packet Internet Groper (PING)
– Used to test whether hosts are alive
– The host sends an ICMP echo message
and expects one back from the remote
end.
Traceroute
– Used for diagnostic purposed to report on
paths that datagrams take through the
network for specified: source – destination
pair(s), source(s) or destination(s).