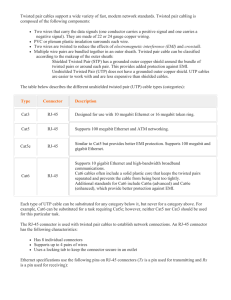
Forrestville Valley School District #221
... 3. The "fair use" rules governing student reports in classrooms are less stringent and permit limited use of graphics and text. 4. Material from software owned by the Forrestville Valley School District #221 or school may not be used without permission or unless the licensing agreement specifically ...
... 3. The "fair use" rules governing student reports in classrooms are less stringent and permit limited use of graphics and text. 4. Material from software owned by the Forrestville Valley School District #221 or school may not be used without permission or unless the licensing agreement specifically ...
lecture - (www.CUNY.edu).
... Internet transport protocol “best effort” service, UDP segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
... Internet transport protocol “best effort” service, UDP segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
3rd Edition, Chapter 5
... just like dialup link is really part of separate network (telephone network) ...
... just like dialup link is really part of separate network (telephone network) ...
CCNA testout unit 2
... Regardless of the method used, changes in routing information take time to propagate to all routers on the network. The term convergence is used to describe the condition when all routers have the same (or correct) routing information. Routers provide more functionality than either switches or bridg ...
... Regardless of the method used, changes in routing information take time to propagate to all routers on the network. The term convergence is used to describe the condition when all routers have the same (or correct) routing information. Routers provide more functionality than either switches or bridg ...
Cross-layer Visibility as a Service
... data. For example, a customer could inquire about a performance problem that started ten minutes ago, and the service could report whether a failure forced the customer’s traffic onto a path with a longer round-trip time. The management system can also implement explicit policies to control what kin ...
... data. For example, a customer could inquire about a performance problem that started ten minutes ago, and the service could report whether a failure forced the customer’s traffic onto a path with a longer round-trip time. The management system can also implement explicit policies to control what kin ...
Document
... The most popular open source NIDS on IA platform. It identifies intrusion by matching the coming packets with the signatures (ruleset) ...
... The most popular open source NIDS on IA platform. It identifies intrusion by matching the coming packets with the signatures (ruleset) ...
DQSA
... Institute of Technology. • Basis of DQSA is almost ideal MAC (medium access control) that is effective regardless of speed, distance, or medium. • Ether2 Corp. has acquired the exclusive rights to this patented technology. May 25, 2017 ...
... Institute of Technology. • Basis of DQSA is almost ideal MAC (medium access control) that is effective regardless of speed, distance, or medium. • Ether2 Corp. has acquired the exclusive rights to this patented technology. May 25, 2017 ...
Campus Network Best Practices: Core and Edge Networks
... effectively utilize high bandwidth connections • Many make heavy use of NAT and firewalls that limit performance • Many are built with unmanaged network equipment that provide no ability for monitoring or tuning the network ...
... effectively utilize high bandwidth connections • Many make heavy use of NAT and firewalls that limit performance • Many are built with unmanaged network equipment that provide no ability for monitoring or tuning the network ...
Slide 1
... Route determined by table lookup Routing decision involves finding next hop in route to given destination Routing table has an entry for each destination specifying output port that leads to next hop Size of table becomes impractical for very large number of destinations ...
... Route determined by table lookup Routing decision involves finding next hop in route to given destination Routing table has an entry for each destination specifying output port that leads to next hop Size of table becomes impractical for very large number of destinations ...
ppt
... use feedback to tell sender when allowed to send next packet » Back-pressure: separate wires to tell to stop » Window: give original sender right to send N packets before getting permission to send more; overlaps latency of interconnection with overhead to send & receive packet (e.g., TCP), adjustab ...
... use feedback to tell sender when allowed to send next packet » Back-pressure: separate wires to tell to stop » Window: give original sender right to send N packets before getting permission to send more; overlaps latency of interconnection with overhead to send & receive packet (e.g., TCP), adjustab ...
Multicasting_Presentation
... Multicasting at Transport Layer • Multicasting uses UDP (User Datagram Protocol) as its underlying transport protocol. No retransmission of packets or acknowledgment in the TL . Any reliability must be engineered-in at higher level. ...
... Multicasting at Transport Layer • Multicasting uses UDP (User Datagram Protocol) as its underlying transport protocol. No retransmission of packets or acknowledgment in the TL . Any reliability must be engineered-in at higher level. ...
CPS221 Lecture: The Network Layer last revised 10/9/2014
... This is, of course governed by the IP of the destination system. B. There are two cases 1. The destination system is on the same subnet as the sending system. 2. The destination system is on a different subnet 3. The sending system can easily distinguish these two cases by comparing the subnet prefi ...
... This is, of course governed by the IP of the destination system. B. There are two cases 1. The destination system is on the same subnet as the sending system. 2. The destination system is on a different subnet 3. The sending system can easily distinguish these two cases by comparing the subnet prefi ...
Document
... D advertises its minimum costs as: ∞, 1, 2, 0 Show the first update on C’s table if C simultaneously receives packets with the minimum cost information from the routers A, B and D ...
... D advertises its minimum costs as: ∞, 1, 2, 0 Show the first update on C’s table if C simultaneously receives packets with the minimum cost information from the routers A, B and D ...
01_NF_CH06_AddressingTheNetwork
... explained earlier, within each network the first and last addresses cannot be assigned to hosts. These are the network address and the broadcast address, respectively. Default Route - Also presented earlier, we represent the IPv4 default route as 0.0.0.0. The default route is used as a "catch all" r ...
... explained earlier, within each network the first and last addresses cannot be assigned to hosts. These are the network address and the broadcast address, respectively. Default Route - Also presented earlier, we represent the IPv4 default route as 0.0.0.0. The default route is used as a "catch all" r ...
Release
... announced the launch of its IPX (Internet Protocol Exchange) solution for carriers, mobile operators and content providers. IPX enables secure and high quality connectivity between networks using IP technology. An IPX solution can be compare to a big pipe in which there are many smaller pipes that c ...
... announced the launch of its IPX (Internet Protocol Exchange) solution for carriers, mobile operators and content providers. IPX enables secure and high quality connectivity between networks using IP technology. An IPX solution can be compare to a big pipe in which there are many smaller pipes that c ...
Introduction to computer netw
... • A model defines the stages or tasks of a protocol as it prepares to send data ▫ Open meaning standards available to all. ...
... • A model defines the stages or tasks of a protocol as it prepares to send data ▫ Open meaning standards available to all. ...
Essentials of Broadband Technology
... designers and installers because using these topologies makes it simple to add network devices anywhere. In most cases, you can simply install one new cable between the central connection point and the desired location of the new network device, without moving or adding to a trunk cable or making th ...
... designers and installers because using these topologies makes it simple to add network devices anywhere. In most cases, you can simply install one new cable between the central connection point and the desired location of the new network device, without moving or adding to a trunk cable or making th ...
IP Optical Networks - City University of New York
... Cost Reduction - integrating optics and eliminating mux stages Operation Efficiency - elimination of redundant protocol layers Transport Efficiency - elimination of transport protocol overhead Emergent technology is evolving WDM from optical transport (point-topoint line systems) to true optical net ...
... Cost Reduction - integrating optics and eliminating mux stages Operation Efficiency - elimination of redundant protocol layers Transport Efficiency - elimination of transport protocol overhead Emergent technology is evolving WDM from optical transport (point-topoint line systems) to true optical net ...
Module 6: Configuring Routing by Using Routing and Remote Access
... Why Use the Windows Server 2003 Routing and Remote Access Service? Windows Server 2003 Routing and Remote Access is a service that performs routing as one of its multiple processes ...
... Why Use the Windows Server 2003 Routing and Remote Access Service? Windows Server 2003 Routing and Remote Access is a service that performs routing as one of its multiple processes ...
Simpilify networking for Container
... Links and termination points define network or service topologies ...
... Links and termination points define network or service topologies ...
Chapter 1
... • Because several customers are sharing the link, the cost to each is generally less than the cost of a direct link of the same capacity. • Frame Relay may also be used for delay-sensitive traffic, often using QoS mechanisms to give priority to the more sensitive data. • ATM has been designed to pro ...
... • Because several customers are sharing the link, the cost to each is generally less than the cost of a direct link of the same capacity. • Frame Relay may also be used for delay-sensitive traffic, often using QoS mechanisms to give priority to the more sensitive data. • ATM has been designed to pro ...
EN 2346467
... VANET or Vehicular Adhoc Networks are popular among the research community. VANETs are different from other ad hoc networks by their mixed network architectures, movement of nodes, and other new applications. Every participating vehicles are turn into a wireless router or node by VANET, the vehicles ...
... VANET or Vehicular Adhoc Networks are popular among the research community. VANETs are different from other ad hoc networks by their mixed network architectures, movement of nodes, and other new applications. Every participating vehicles are turn into a wireless router or node by VANET, the vehicles ...