IN (2)
... The Working Group began evaluating the two commonly used tr ansport protocols, User Datagram Protocol (UDP) and Transport Control Protocol (TCP) against these requirements. UDP was quickly ruled out because it did not meet the basic req uirements for reliable, in-order transport. TCP met the b ...
... The Working Group began evaluating the two commonly used tr ansport protocols, User Datagram Protocol (UDP) and Transport Control Protocol (TCP) against these requirements. UDP was quickly ruled out because it did not meet the basic req uirements for reliable, in-order transport. TCP met the b ...
[PDF]
... no wonder that man can take advantage of wireless network almost everywhere in China, ranging from the prosperous commercial street, high and new technology industry development zone, the university campus, scientific research units, the government and police and troops subordinate organizations, to ...
... no wonder that man can take advantage of wireless network almost everywhere in China, ranging from the prosperous commercial street, high and new technology industry development zone, the university campus, scientific research units, the government and police and troops subordinate organizations, to ...
Slide 1
... MTU: verify MTU. Fragments: check for fragment offsets 0 or > 0, more fragments flag set or not set. Unicast or Multicast destinations in RIP frames. Learn about ports and TCP. Use netstat –an | less to check and see which ports are open (LISTEN) and which TCP connections are established. ...
... MTU: verify MTU. Fragments: check for fragment offsets 0 or > 0, more fragments flag set or not set. Unicast or Multicast destinations in RIP frames. Learn about ports and TCP. Use netstat –an | less to check and see which ports are open (LISTEN) and which TCP connections are established. ...
Slides
... View the Internet in two ways: 1. Humans see a hierarchy of domains relating computers—logical network 2. Computers see groups of four number IP addresses— physical network Both are ideal for the “user's” needs ...
... View the Internet in two ways: 1. Humans see a hierarchy of domains relating computers—logical network 2. Computers see groups of four number IP addresses— physical network Both are ideal for the “user's” needs ...
OSI Model Review Layer 1
... • A router is a Layer 3 networking device that connects network segments or entire networks. • It is considered more intelligent than Layer 2 devices because it makes decisions based on information received about the network as a whole. • A router examines the IP address of the destination computer ...
... • A router is a Layer 3 networking device that connects network segments or entire networks. • It is considered more intelligent than Layer 2 devices because it makes decisions based on information received about the network as a whole. • A router examines the IP address of the destination computer ...
6LoWPAN adaptation layer (cont.)
... Wireless sensor network (WSN) is one of the fastest growing segments in the ubiquitous networking today. In order to morph WSN from personal area network (PAN) into low power personal area network (LoWPAN), IEEE standard 802.15.4 is introduced. Currently some sensor network protocols have non-IP ...
... Wireless sensor network (WSN) is one of the fastest growing segments in the ubiquitous networking today. In order to morph WSN from personal area network (PAN) into low power personal area network (LoWPAN), IEEE standard 802.15.4 is introduced. Currently some sensor network protocols have non-IP ...
Router - UStudy.in
... broadband router to connect your Internet to your phone. • These are often a special type of modem that will have both Ethernet and phone jacks. ...
... broadband router to connect your Internet to your phone. • These are often a special type of modem that will have both Ethernet and phone jacks. ...
WSDLite: A Lightweight Alternative to Windows Sockets Direct Path
... sending or receiving side. SANs may be used for enterprise applications such as databases, web servers, reservation systems, and small to medium scale parallel computing environments. System area networks have not yet enjoyed wide adoption, in part because of the difficulty associated with writing a ...
... sending or receiving side. SANs may be used for enterprise applications such as databases, web servers, reservation systems, and small to medium scale parallel computing environments. System area networks have not yet enjoyed wide adoption, in part because of the difficulty associated with writing a ...
www.c-jump.com
... – Ensure that only authorized parties can view transmitted wireless information – Encrypts information into ciphertext – Contains a serious flaw – Attacker can discover a WEP key in less than one minute ...
... – Ensure that only authorized parties can view transmitted wireless information – Encrypts information into ciphertext – Contains a serious flaw – Attacker can discover a WEP key in less than one minute ...
EAP
... A client device connects to a port on an 802.1x switch and AP The switch port can determine the authenticity of the devices The services offered by the switch can be made available on that port Only EAPOL frames can be sent and received on that port until authentication is complete. When the device ...
... A client device connects to a port on an 802.1x switch and AP The switch port can determine the authenticity of the devices The services offered by the switch can be made available on that port Only EAPOL frames can be sent and received on that port until authentication is complete. When the device ...
Chapter 5
... SSID. While to the average user there does not appear to be a network in use, a network protected in this way is still easily accessed by crackers using the appropriate tools. Other forms of encryption and authentication should also be used, at a minimum WEP but preferably WPA. Today, some newer wir ...
... SSID. While to the average user there does not appear to be a network in use, a network protected in this way is still easily accessed by crackers using the appropriate tools. Other forms of encryption and authentication should also be used, at a minimum WEP but preferably WPA. Today, some newer wir ...
1 - Cisco Support Community
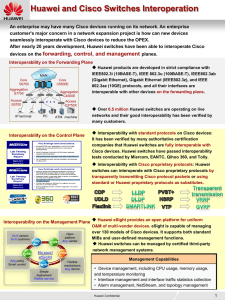
... Interoperability with standard protocols on Cisco devices: It has been verified by many authoritative certification companies that Huawei switches are fully interoperable with Cisco devices. Huawei switches have passed interoperability tests conducted by Miercom, EANTC, Qihoo 360, and Tolly. ...
... Interoperability with standard protocols on Cisco devices: It has been verified by many authoritative certification companies that Huawei switches are fully interoperable with Cisco devices. Huawei switches have passed interoperability tests conducted by Miercom, EANTC, Qihoo 360, and Tolly. ...
Presentation
... DoS attackers will attempt to stop communication to the target target difficult to replicate (e.g., info highly dynamic) legitimate users may be mobile (source IP address may ...
... DoS attackers will attempt to stop communication to the target target difficult to replicate (e.g., info highly dynamic) legitimate users may be mobile (source IP address may ...
chap2_2ed_5July02 - Computer Science
... network “below”. within same host, two processes communicate implements user using interprocess interface & communication (defined application-level by OS). protocol Web: browser processes running in E-mail: mail reader different hosts streaming audio/video: communicate with an media pla ...
... network “below”. within same host, two processes communicate implements user using interprocess interface & communication (defined application-level by OS). protocol Web: browser processes running in E-mail: mail reader different hosts streaming audio/video: communicate with an media pla ...
Solutions Brief - Coriant Transcend™ SDN Solution
... architectures, technologies, and business models. Video and other traffic generated from cloud-based applications and online services such as cloud storage, IPTV, and music downloads creates significant and agile traffic patterns in mobile and fixed networks. Network operators are driven by ever-inc ...
... architectures, technologies, and business models. Video and other traffic generated from cloud-based applications and online services such as cloud storage, IPTV, and music downloads creates significant and agile traffic patterns in mobile and fixed networks. Network operators are driven by ever-inc ...
Computer Networks and Internets
... IGMP is used both by the client computer and the adjacent network switches to connect the client to a local multicast router. Protocol Independent Multicast (PIM) is then used between the local and remote multicast routers, to direct multicast traffic from the video server to many multicast clients ...
... IGMP is used both by the client computer and the adjacent network switches to connect the client to a local multicast router. Protocol Independent Multicast (PIM) is then used between the local and remote multicast routers, to direct multicast traffic from the video server to many multicast clients ...
Transport Control Protocol (TCP) & Applications
... • Uses multiple threads of control • Core part of server accepts new requests and dynamically creates new server processes as separate service threads to handle them • Each thread deals with its client’s requests ...
... • Uses multiple threads of control • Core part of server accepts new requests and dynamically creates new server processes as separate service threads to handle them • Each thread deals with its client’s requests ...
Wireless Glossary
... AC (Authentication Center)—A system that authenticates a mobile station that attempts to gain access to the cellular network AC Barring Access Class Barring Access Channel In CDMA and 1xEV-DO, a reverse-link (uplink) channel upon which any mobile may transmit to register or request to make or receiv ...
... AC (Authentication Center)—A system that authenticates a mobile station that attempts to gain access to the cellular network AC Barring Access Class Barring Access Channel In CDMA and 1xEV-DO, a reverse-link (uplink) channel upon which any mobile may transmit to register or request to make or receiv ...
web.cs.sunyit.edu
... Operate at Data Link OSI model layer Single input and single output ports Protocol independent Filtering database – Contains known MAC addresses and network locations ...
... Operate at Data Link OSI model layer Single input and single output ports Protocol independent Filtering database – Contains known MAC addresses and network locations ...
Gnutella Network - University of Chicago
... connections with nodes that are already in the network. In the dynamic environment where Gnutella operates, nodes often join and leave and network connections are unreliable. To cope with this environment, after joining the network, a node periodically PINGs its neighbors to discover other participa ...
... connections with nodes that are already in the network. In the dynamic environment where Gnutella operates, nodes often join and leave and network connections are unreliable. To cope with this environment, after joining the network, a node periodically PINGs its neighbors to discover other participa ...
Improving VPN Performance over Multiple Access Links Larry Roberts
... maintain separate links; one for enterprise access and one for internet access or personal use. In many such cases one link remains idle even while the second link serves as the choke point for the active VPN connection. But for those cases where additional links may be used, we have developed new t ...
... maintain separate links; one for enterprise access and one for internet access or personal use. In many such cases one link remains idle even while the second link serves as the choke point for the active VPN connection. But for those cases where additional links may be used, we have developed new t ...
MIS 4850 Systems Security
... 4. What would be the possible consequences of making the rule you created when answering Question 3 (above) the very first rule of the ACL? a. This may decrease the likelihood of being attacked b. This may allow an attacker using IP spoofing with a Class A IP address in the private range to get to ...
... 4. What would be the possible consequences of making the rule you created when answering Question 3 (above) the very first rule of the ACL? a. This may decrease the likelihood of being attacked b. This may allow an attacker using IP spoofing with a Class A IP address in the private range to get to ...
Network_LAN - faculty at Chemeketa
... workstation and file server has some sort of transceiver/antenna to send and receive data as if they were physically connected. ...
... workstation and file server has some sort of transceiver/antenna to send and receive data as if they were physically connected. ...
![[PDF]](http://s1.studyres.com/store/data/008812149_1-3b4a796a6bb782026ebeb65f734ec49f-300x300.png)