Network_LAN - faculty at Chemeketa
... workstation and file server has some sort of transceiver/antenna to send and receive data as if they were physically connected. ...
... workstation and file server has some sort of transceiver/antenna to send and receive data as if they were physically connected. ...
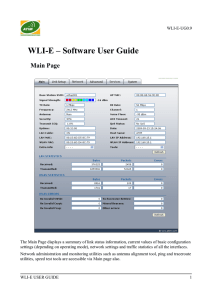
WLI-E – Software User Guide
... link speeds to better service particular customers and/or particular applications like VoIP and video which require greater consistency, stability, and lower latency performance. Uptime: This is the running total of time the device has been running since last power up (hardreboot) or software upgrad ...
... link speeds to better service particular customers and/or particular applications like VoIP and video which require greater consistency, stability, and lower latency performance. Uptime: This is the running total of time the device has been running since last power up (hardreboot) or software upgrad ...
bgp header
... • Default routes => partial information • Routers/hosts with default routes rely on other routers to complete the picture. • In general routing information should be: – Consistent, I.e., if packet is sent off in one direction then another direction should not be more optimal – Complete, I.e., should ...
... • Default routes => partial information • Routers/hosts with default routes rely on other routers to complete the picture. • In general routing information should be: – Consistent, I.e., if packet is sent off in one direction then another direction should not be more optimal – Complete, I.e., should ...
Architecture Intégrée | Sécurité et protection de la propriété
... a new malicious against andthat SCADA never is to scan local area networks forICS devices respondsystems to OPC (Open Platform Communications) became a reality, making the new Havex requests. campaigns a rare occurrence, but possibly The Havex component leverages the OPC standard to gather informati ...
... a new malicious against andthat SCADA never is to scan local area networks forICS devices respondsystems to OPC (Open Platform Communications) became a reality, making the new Havex requests. campaigns a rare occurrence, but possibly The Havex component leverages the OPC standard to gather informati ...
Service Electric Cablevision Broadband Internet Service
... applications such as voice and video under normal operating conditions. SECV’s internet service is designed to be a low latency, ‘always on’ service ideal for a wide variety of demanding internet applications, including real-time applications such as gaming, work-at-home, video streaming, plus the s ...
... applications such as voice and video under normal operating conditions. SECV’s internet service is designed to be a low latency, ‘always on’ service ideal for a wide variety of demanding internet applications, including real-time applications such as gaming, work-at-home, video streaming, plus the s ...
Evolving Toward a Self-Managing Network Jennifer Rexford Princeton University
... – New algorithms for selecting paths within an AS – New approaches to inter-AS routing ...
... – New algorithms for selecting paths within an AS – New approaches to inter-AS routing ...
Network Standards
... • Error messages, such as ACKs, can refer to specific messages according to the sequence numbers of these messages – Long messages can be fragmented into many smaller messages that can fit inside of packets • The fragments will be given sequence numbers so that they can be assembled at the other end ...
... • Error messages, such as ACKs, can refer to specific messages according to the sequence numbers of these messages – Long messages can be fragmented into many smaller messages that can fit inside of packets • The fragments will be given sequence numbers so that they can be assembled at the other end ...
Multicasting in Mobile ad hoc networks
... Fast Handoff aims to reduce the handoff latency by using interaction between the radio and IP layers to detect the mobile movements. This can work only if the radio technology allows such interaction between layers.( its not solution for heterogenous wireless network) The packet loss during the hand ...
... Fast Handoff aims to reduce the handoff latency by using interaction between the radio and IP layers to detect the mobile movements. This can work only if the radio technology allows such interaction between layers.( its not solution for heterogenous wireless network) The packet loss during the hand ...
EMC SMARTS NETWORK PROTOCOL MANAGER Management That Enables Service Assurance for
... routing protocols to construct end-to-end paths, Network Protocol Manager provides insight into routing process and adjacency failures, pinpointing root-cause problems in routing protocol domains and correlating these events with problems in the underlying IP network. Network Protocol Manager provid ...
... routing protocols to construct end-to-end paths, Network Protocol Manager provides insight into routing process and adjacency failures, pinpointing root-cause problems in routing protocol domains and correlating these events with problems in the underlying IP network. Network Protocol Manager provid ...
Generalized Multiprotocol Label Switching (GMPLS)
... packet, primarily by examining the destination address in the header of the packet. MPLS has greatly simplified this operation by basing the forwarding decision on a simple label. Another major feature of MPLS is its ability to place IP traffic on a defined path through the network. This capability ...
... packet, primarily by examining the destination address in the header of the packet. MPLS has greatly simplified this operation by basing the forwarding decision on a simple label. Another major feature of MPLS is its ability to place IP traffic on a defined path through the network. This capability ...
Internet Protocol
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
InternetOverview
... web browser) and a server application (i.e. a web server) Describes how clients and servers communicate with each other ...
... web browser) and a server application (i.e. a web server) Describes how clients and servers communicate with each other ...
Chapter3transport
... ACK: segment received (a good thing!), network not congested, so increase sending rate lost segment: assume loss due to congested network, so decrease sending rate ...
... ACK: segment received (a good thing!), network not congested, so increase sending rate lost segment: assume loss due to congested network, so decrease sending rate ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... The proposed solution depends on k-Nearest Neighbour (K-NN) technique and we have developed a packet drop guesser module that considering only two parameters i.e. time and congestion window. Of course, we can take other parameters, but that‟s not considered for this work as the two chosen parameters ...
... The proposed solution depends on k-Nearest Neighbour (K-NN) technique and we have developed a packet drop guesser module that considering only two parameters i.e. time and congestion window. Of course, we can take other parameters, but that‟s not considered for this work as the two chosen parameters ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... A Wireless ad hoc network is a collection of self organized wireless mobile nodes dynamically forming a temporary network without the aid of any established or fixed infrastructure and centralized administration control stations, unlike cellular wireless networks. The surrounding physical environmen ...
... A Wireless ad hoc network is a collection of self organized wireless mobile nodes dynamically forming a temporary network without the aid of any established or fixed infrastructure and centralized administration control stations, unlike cellular wireless networks. The surrounding physical environmen ...
plaNET - Semantic Scholar
... system processor can directly send and receive data from the network interface. A native access point has a potential performance advantage as it is possible for the transmitting programs to format the data in a manner that is matched to the plaNET/ORBIT network, thereby eliminating the need for any ...
... system processor can directly send and receive data from the network interface. A native access point has a potential performance advantage as it is possible for the transmitting programs to format the data in a manner that is matched to the plaNET/ORBIT network, thereby eliminating the need for any ...
routing_algorithms
... Multiple same-cost paths allowed (only one path in RIP) For each link, multiple cost metrics for different TOS (e.g., satellite link cost set “low” for best effort; high for real time) Integrated uni- and multicast support: Multicast OSPF (MOSPF) uses same topology data base as OSPF Hierarchical O ...
... Multiple same-cost paths allowed (only one path in RIP) For each link, multiple cost metrics for different TOS (e.g., satellite link cost set “low” for best effort; high for real time) Integrated uni- and multicast support: Multicast OSPF (MOSPF) uses same topology data base as OSPF Hierarchical O ...
Fundamentals of Multimedia 2 nd ed., Chapter 15
... Mbps, which is faster than most DSL accesses that are up to 10 Mbps. • In most areas, both DSL and cable accesses are available, although some areas may have only one choice. ...
... Mbps, which is faster than most DSL accesses that are up to 10 Mbps. • In most areas, both DSL and cable accesses are available, although some areas may have only one choice. ...
SNMP and Beyond - Washington University in St. Louis
... SolarWinds provides a variety of network management solutions ranging from individual monitoring tools to complete, full-featured monitoring platforms. Orion is their comprehensive monitoring solution built on SNMP. The Orion management application features a web interface with real-time monitoring ...
... SolarWinds provides a variety of network management solutions ranging from individual monitoring tools to complete, full-featured monitoring platforms. Orion is their comprehensive monitoring solution built on SNMP. The Orion management application features a web interface with real-time monitoring ...
Internet In A Slice - Princeton University
... Ingress: local I2 node Egress: I2 node close to destination By default, traffic between ingress and egress will be carried by I2 ...
... Ingress: local I2 node Egress: I2 node close to destination By default, traffic between ingress and egress will be carried by I2 ...
Network Types (Cont.)
... have different paths. – Partial remedy to adapting to load changes. – Ensures that messages will be delivered in the order in which they were sent. ...
... have different paths. – Partial remedy to adapting to load changes. – Ensures that messages will be delivered in the order in which they were sent. ...
bigiron 4000, 8000, 15000
... because of the 10/100, Gigabit and 10 Gigabit Ethernet port density, superior serviceability, high availability, security and advanced Layer 2/3 feature sets. With wire-speed, granular rate limiting, service providers can meter bandwidth and use Foundry’s sFlow based on RFC 3176 to provide wire-spee ...
... because of the 10/100, Gigabit and 10 Gigabit Ethernet port density, superior serviceability, high availability, security and advanced Layer 2/3 feature sets. With wire-speed, granular rate limiting, service providers can meter bandwidth and use Foundry’s sFlow based on RFC 3176 to provide wire-spee ...
NFV PM thought experiments
... Of course, many of out previous examples already cast doubt on the meaningfulness of delay If packets are combined and resegmented as in experiment 2 (TCP proxy) then we need to track individual bytes, not packets ...
... Of course, many of out previous examples already cast doubt on the meaningfulness of delay If packets are combined and resegmented as in experiment 2 (TCP proxy) then we need to track individual bytes, not packets ...
Introduction to the PPNCG - University of Manchester
... Les Cottrell Measurements from 34 monitors in 14 countries ...
... Les Cottrell Measurements from 34 monitors in 14 countries ...
Slide 1
... – Users can create sophisticated methods of organizing messages on server – Users can share mailbox in central location Disadvantages – Requires more storage space, processing resources than POP servers – Network managers must watch user allocations closely – IMAP4 server failure • Users cannot acce ...
... – Users can create sophisticated methods of organizing messages on server – Users can share mailbox in central location Disadvantages – Requires more storage space, processing resources than POP servers – Network managers must watch user allocations closely – IMAP4 server failure • Users cannot acce ...