E-Commerce Security
... • Uses two different keys: a public and a private key. • Receiver’s public key must be delivered in advance. • Sender uses receiver’s public key to encrypt the message and receiver uses private key to decrypt the message (Sender can be sure the receiver is the true receiver) • Example: – RSA (Rivest ...
... • Uses two different keys: a public and a private key. • Receiver’s public key must be delivered in advance. • Sender uses receiver’s public key to encrypt the message and receiver uses private key to decrypt the message (Sender can be sure the receiver is the true receiver) • Example: – RSA (Rivest ...
Single Photon Polarization
... 4. Bob receives each bit and does not know the basis used to encode. He also tosses a coin and decides to decode using the basis as decided by coin toss. 5. Half the time Bob’s basis will be the same as Alice’s in which case the qubit received will be the same provided Eve is not intercepting. ...
... 4. Bob receives each bit and does not know the basis used to encode. He also tosses a coin and decides to decode using the basis as decided by coin toss. 5. Half the time Bob’s basis will be the same as Alice’s in which case the qubit received will be the same provided Eve is not intercepting. ...
Lect 1 - Intro
... Data integrity: Assures that information and programs are changed only in a specified and authorized manner System integrity: Assures that a system performs its intended function in an unimpaired manner, free from deliberate or inadvertent unauthorized manipulation of the system ...
... Data integrity: Assures that information and programs are changed only in a specified and authorized manner System integrity: Assures that a system performs its intended function in an unimpaired manner, free from deliberate or inadvertent unauthorized manipulation of the system ...
Chapter 9 Public Key Cryptography and RSA
... 9.1 Principles of Public Key cryptosystems Security of Public Key Schemes like private key schemes brute force exhaustive search attack is always theoretically possible but keys used are too large (>512bits) security relies on a large enough difference in difficulty between easy (en/decrypt) ...
... 9.1 Principles of Public Key cryptosystems Security of Public Key Schemes like private key schemes brute force exhaustive search attack is always theoretically possible but keys used are too large (>512bits) security relies on a large enough difference in difficulty between easy (en/decrypt) ...
security
... – A encodes a message with his/her private key – A sends the message to B – A must also send his/her private key to B (this is the ...
... – A encodes a message with his/her private key – A sends the message to B – A must also send his/her private key to B (this is the ...
Web Security
... – Invented by Netscape and made public domain for everyone’s use – An additional layer to the TCP/IP stack that sits between the Application and Transport layers • ensures that all application data is encrypted but TCP/IP headers are not • usually run on port 443 (default HTTPS port) ...
... – Invented by Netscape and made public domain for everyone’s use – An additional layer to the TCP/IP stack that sits between the Application and Transport layers • ensures that all application data is encrypted but TCP/IP headers are not • usually run on port 443 (default HTTPS port) ...
Web Security
... – Invented by Netscape and made public domain for everyone’s use – An additional layer to the TCP/IP stack that sits between the Application and Transport layers • ensures that all application data is encrypted but TCP/IP headers are not • usually run on port 443 (default HTTPS port) ...
... – Invented by Netscape and made public domain for everyone’s use – An additional layer to the TCP/IP stack that sits between the Application and Transport layers • ensures that all application data is encrypted but TCP/IP headers are not • usually run on port 443 (default HTTPS port) ...
EppDm4_08_04
... The effectiveness of the system is based on the fact that although modern computer algorithms make it quite easy to find two distinct large integers p and q—say on the order of several hundred digits each—that are virtually certain to be prime, even the fastest computers are not currently able to fa ...
... The effectiveness of the system is based on the fact that although modern computer algorithms make it quite easy to find two distinct large integers p and q—say on the order of several hundred digits each—that are virtually certain to be prime, even the fastest computers are not currently able to fa ...
new zealand`s cyber security strategy
... • Introductions and scene setting – John Harvey, DIA • Cyber Security Strategy – Alan Bell, MED • Key Initiatives – Grant Fletcher, GCSB • Questions ...
... • Introductions and scene setting – John Harvey, DIA • Cyber Security Strategy – Alan Bell, MED • Key Initiatives – Grant Fletcher, GCSB • Questions ...
CN 2015 5 - SNGCE DIGITAL LIBRARY
... A security association is simply the bundle of algorithms and parameters (such as keys) that is being used to encrypt and authenticate a particular flow in one direction. IPsec supports two encryption modes: Transport and ...
... A security association is simply the bundle of algorithms and parameters (such as keys) that is being used to encrypt and authenticate a particular flow in one direction. IPsec supports two encryption modes: Transport and ...
Security - UTRGV Faculty Web
... Private IP addresses are not visible from the outside world. It makes sense to use only private IP to secure your computer. When outside communication is needed the private IP is mapped to public IP address using a port number. ...
... Private IP addresses are not visible from the outside world. It makes sense to use only private IP to secure your computer. When outside communication is needed the private IP is mapped to public IP address using a port number. ...
No Slide Title
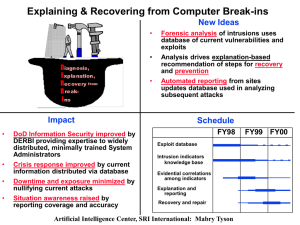
... Automated reporting from sites updates database used in analyzing subsequent attacks ...
... Automated reporting from sites updates database used in analyzing subsequent attacks ...
Adopting Number Sequences for Shielding Information
... Cryptography is the branch of information security. The basic goal of cryptography is to make communication secure in the presence of third party (intruder). Encryption is the mechanism of transforming information into unreadable (cipher) form. This is accomplished for data integrity, forward secrec ...
... Cryptography is the branch of information security. The basic goal of cryptography is to make communication secure in the presence of third party (intruder). Encryption is the mechanism of transforming information into unreadable (cipher) form. This is accomplished for data integrity, forward secrec ...
MT311-14
... In the security policy model, resources can be granted or denied different types of access independently. For example, a file can be a resource, and the read action can be differentiated from the write action. So, you can easily grant read-only access to a particular file. You can do the same with o ...
... In the security policy model, resources can be granted or denied different types of access independently. For example, a file can be a resource, and the read action can be differentiated from the write action. So, you can easily grant read-only access to a particular file. You can do the same with o ...
Chapter 2: Attackers and Their Attacks
... Deface electronic information to spread disinformation and propaganda Deny service to legitimate computer users Commit unauthorized intrusions into systems and networks that result in critical infrastructure outages and corruption of vital data ...
... Deface electronic information to spread disinformation and propaganda Deny service to legitimate computer users Commit unauthorized intrusions into systems and networks that result in critical infrastructure outages and corruption of vital data ...
FTAA Joint Public-Private Sector Committee of Experts
... especially since the discussion centers on the reach and strength of restrictions on the export of encryption technology. Validity of Digital Signatures International business transactions raise questions regarding the conditions and requirements for the recognition, effect and enforceability of dig ...
... especially since the discussion centers on the reach and strength of restrictions on the export of encryption technology. Validity of Digital Signatures International business transactions raise questions regarding the conditions and requirements for the recognition, effect and enforceability of dig ...
Symmetric-Key Cryptography - Sensorweb Research Laboratory
... • Involve multiple stages of substitutions and transpositions • The number of keys used • Referred to as symmetric, single-key, secret-key, or conventional encryption if both sender and receiver use the same key • Referred to as asymmetric, two-key, or public-key encryption if the sender and receive ...
... • Involve multiple stages of substitutions and transpositions • The number of keys used • Referred to as symmetric, single-key, secret-key, or conventional encryption if both sender and receiver use the same key • Referred to as asymmetric, two-key, or public-key encryption if the sender and receive ...
Network Security For Distributed Simulation Systems
... Given Public (Encryption) Key - Difficult to Determine Private (Decryption) Key Degree of Difficulty relates to Number of Bits 1024 bits gives a Reasonable Degree of Security ...
... Given Public (Encryption) Key - Difficult to Determine Private (Decryption) Key Degree of Difficulty relates to Number of Bits 1024 bits gives a Reasonable Degree of Security ...
Implementing Security for Electronic Commerce
... Protecting intranets with firewalls and corporate servers against being attacked through the Internet The role Secure Socket Layer, Secure HTTP and secure electronic transaction protocols play in protecting e-commerce ...
... Protecting intranets with firewalls and corporate servers against being attacked through the Internet The role Secure Socket Layer, Secure HTTP and secure electronic transaction protocols play in protecting e-commerce ...
Tallinn University of Technology Quantum computer impact on
... argument to a function, so a function performed on the superposition of states is in turn performed on each component of the superposition. The larger the number of possible states is, however, the smaller the probability that you will measure any particular state becomes. ...
... argument to a function, so a function performed on the superposition of states is in turn performed on each component of the superposition. The larger the number of possible states is, however, the smaller the probability that you will measure any particular state becomes. ...
Public Key Encryption and Digital Signatures
... – Public Key encryption • does not require communication of a key • security depends on the difficulty of factoring very large numbers (hundreds of digits) ...
... – Public Key encryption • does not require communication of a key • security depends on the difficulty of factoring very large numbers (hundreds of digits) ...
Cryptanalysis

Cryptanalysis (from the Greek kryptós, ""hidden"", and analýein, ""to loosen"" or ""to untie"") is the study of analyzing information systems in order to study the hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown.In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation.Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like the British Bombes and Colossus computers at Bletchley Park in World War II, to the mathematically advanced computerized schemes of the present. Methods for breaking modern cryptosystems often involve solving carefully constructed problems in pure mathematics, the best-known being integer factorization.