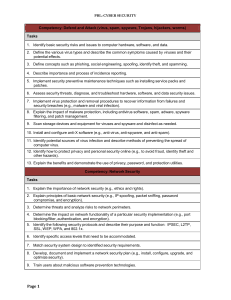
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 7. Identify and analyze environmental hazards (e.g., fire, flood, moisture, temperature, electricity,) and establish environmental security controls to protect and restore. 8. Perform a physical configuration audit. 9. Train and test employees in area of physical security awareness. 10. Describe the ...
... 7. Identify and analyze environmental hazards (e.g., fire, flood, moisture, temperature, electricity,) and establish environmental security controls to protect and restore. 8. Perform a physical configuration audit. 9. Train and test employees in area of physical security awareness. 10. Describe the ...
Indianapolis: ITT - BS Information Systems Security (2016
... **All ITT learner transfer credit evaluations subject to individual transcript review for official transfer credit acceptance. Credit total may be fewer or more than outlined. Capella University Transfer policy can be found http://www.capella.edu/content/dam/capella/PDF/Transfer_Credit_Assessment.pd ...
... **All ITT learner transfer credit evaluations subject to individual transcript review for official transfer credit acceptance. Credit total may be fewer or more than outlined. Capella University Transfer policy can be found http://www.capella.edu/content/dam/capella/PDF/Transfer_Credit_Assessment.pd ...
Protection
... Networks, cloud computing, big data and other high-tech application and development are facing complex network environment ...
... Networks, cloud computing, big data and other high-tech application and development are facing complex network environment ...
Getting Security Right in Wireless Sensor Networks
... Fortunately, there are powerful tools for building secure, robust wireless communications networks. It takes diligence and attention to detail, but there is nothing fundamentally hard about it. Ciphers and Nonces The most basic cryptographic tool is the block cipher. As an example, AES-128 is a part ...
... Fortunately, there are powerful tools for building secure, robust wireless communications networks. It takes diligence and attention to detail, but there is nothing fundamentally hard about it. Ciphers and Nonces The most basic cryptographic tool is the block cipher. As an example, AES-128 is a part ...
3-39 What are presentation graphics programs?
... • What are presentation graphics programs? How are they used? • What is the difference between an integrated package and a software suite? What are the advantages and disadvantages of each? ...
... • What are presentation graphics programs? How are they used? • What is the difference between an integrated package and a software suite? What are the advantages and disadvantages of each? ...
Essentials of Security
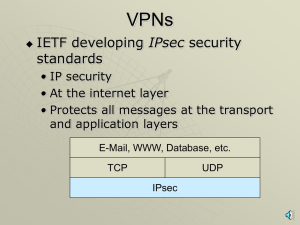
... Identify security risks and threats Analyze and prioritize security risks Security risk tracking, planning, and scheduling ...
... Identify security risks and threats Analyze and prioritize security risks Security risk tracking, planning, and scheduling ...
Security & Privacy on the WWW
... According to Edward Bloustein, privacy is an interest of the human personality. It protects the inviolate personality, the individual's independence, dignity and integrity.[7] According to Ruth Gavison, there are three elements in privacy: secrecy, anonymity and solitude. It is a state which can ...
... According to Edward Bloustein, privacy is an interest of the human personality. It protects the inviolate personality, the individual's independence, dignity and integrity.[7] According to Ruth Gavison, there are three elements in privacy: secrecy, anonymity and solitude. It is a state which can ...
Detailed Overview of Security and Privacy lecture slides
... According to Edward Bloustein, privacy is an interest of the human personality. It protects the inviolate personality, the individual's independence, dignity and integrity.[7] According to Ruth Gavison, there are three elements in privacy: secrecy, anonymity and solitude. It is a state which can ...
... According to Edward Bloustein, privacy is an interest of the human personality. It protects the inviolate personality, the individual's independence, dignity and integrity.[7] According to Ruth Gavison, there are three elements in privacy: secrecy, anonymity and solitude. It is a state which can ...
this list describes some of these commonly used basic tenets
... applications. Installation and maintenance of viable protective software. Proper over-sight of user accounts. Compliance with all applicable regulations regarding the data stored on, or transmitted through, the server. Data Protection Regular Log Review Proper care taken to the physical security and ...
... applications. Installation and maintenance of viable protective software. Proper over-sight of user accounts. Compliance with all applicable regulations regarding the data stored on, or transmitted through, the server. Data Protection Regular Log Review Proper care taken to the physical security and ...
Strategies Simplified Australian Signals Directorate
... Patching protects networks from vulnerabilities not previously identified in the applications. Also known as exploits, these vulnerabilities enable adversaries to execute malicious code, which can result in significant consequences for the organisation. Exploits are so common that adversaries can bu ...
... Patching protects networks from vulnerabilities not previously identified in the applications. Also known as exploits, these vulnerabilities enable adversaries to execute malicious code, which can result in significant consequences for the organisation. Exploits are so common that adversaries can bu ...
abstract - Chennaisunday.com
... (with some variations). As a result, the semantics of NULL in both the SQL standard and the commercial DBMSs is not quite clear; in particular, for IC satisfaction in the presence of NULL. ...
... (with some variations). As a result, the semantics of NULL in both the SQL standard and the commercial DBMSs is not quite clear; in particular, for IC satisfaction in the presence of NULL. ...
Introduction - GMU Computer Science
... • Delivery via web site, e-mail or instant message, the attack asks users to click on a link to “re-validate” or “re-activate” their account. The link displays a believable facsimile of your site and brand to con users into submitting private details • Sends a threatening e-mail to users telling the ...
... • Delivery via web site, e-mail or instant message, the attack asks users to click on a link to “re-validate” or “re-activate” their account. The link displays a believable facsimile of your site and brand to con users into submitting private details • Sends a threatening e-mail to users telling the ...
FEARLESS - Cyber Security Research and Education Institute
... – Privacy Preserving Record Linkage and Mining – Adversarial Data Mining – Secure Data Provenance – Policy and Incentive-based Assured Information ...
... – Privacy Preserving Record Linkage and Mining – Adversarial Data Mining – Secure Data Provenance – Policy and Incentive-based Assured Information ...
Web Security
... • part of javax.net • SSL (and thus HTTPS) permits encrypted traffic to be exchanged between the client and server. – After an SSL client initiates a conversation with an SSL server, the server sends an X.509 certificate back to the client for authentication. The client then checks the validity of t ...
... • part of javax.net • SSL (and thus HTTPS) permits encrypted traffic to be exchanged between the client and server. – After an SSL client initiates a conversation with an SSL server, the server sends an X.509 certificate back to the client for authentication. The client then checks the validity of t ...
Web Security
... • part of javax.net • SSL (and thus HTTPS) permits encrypted traffic to be exchanged between the client and server. – After an SSL client initiates a conversation with an SSL server, the server sends an X.509 certificate back to the client for authentication. The client then checks the validity of t ...
... • part of javax.net • SSL (and thus HTTPS) permits encrypted traffic to be exchanged between the client and server. – After an SSL client initiates a conversation with an SSL server, the server sends an X.509 certificate back to the client for authentication. The client then checks the validity of t ...
D1S1_TSV404_Course_Intro_2011_v1
... ■ Underlying principle: Establishes a perimeter defense for the security domain – Should be defined based on organization’s assets and potential threats to those assets. – Should be defined to providing a high degree of security while still maintaining the connectivity necessary to meet mission ...
... ■ Underlying principle: Establishes a perimeter defense for the security domain – Should be defined based on organization’s assets and potential threats to those assets. – Should be defined to providing a high degree of security while still maintaining the connectivity necessary to meet mission ...
Public Presentation - Academic Conferences
... Only a verifiably secure CDS is evaluatable – On verifiable trusted computing base (TCB) platform – Last coherent codification in TCSEC “Class A1” – System security must be designed in, not bolted on – Includes composition of “partitions” and “subsets” ...
... Only a verifiably secure CDS is evaluatable – On verifiable trusted computing base (TCB) platform – Last coherent codification in TCSEC “Class A1” – System security must be designed in, not bolted on – Includes composition of “partitions” and “subsets” ...
Secure your remote access with VASCO and
... Combining Juniper Networks’ firewalls, VPN solutions and network access security appliances with VASCO’s DIGIPASS strong authentication enhances the security of your network and remote access, while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documen ...
... Combining Juniper Networks’ firewalls, VPN solutions and network access security appliances with VASCO’s DIGIPASS strong authentication enhances the security of your network and remote access, while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documen ...
ws-security-framewor..
... App specific authentication messages App specific credential headers in other messages App maintains its own security domain ...
... App specific authentication messages App specific credential headers in other messages App maintains its own security domain ...
COMPUTER INFORMATION TECHNOLOGY AT NKU
... ‘;master.dbo.xp_c Formats C: drive of database server if you’re mdshell ‘cmd.exe running MS SQL Server and extended format c: /q /yes’ -- procedures aren’t disabled. April 12, 2007 ...
... ‘;master.dbo.xp_c Formats C: drive of database server if you’re mdshell ‘cmd.exe running MS SQL Server and extended format c: /q /yes’ -- procedures aren’t disabled. April 12, 2007 ...
Information Assurance (IA) Framework
... concerns must be addressed in specific testing and certification, for example those in CJCSI 6212.01E, all concerns have to be addressed eventually. One general way to identify all of them includes five primary tenets of Information Assurance: Confidentiality, Integrity, Authentication, Non-repudiat ...
... concerns must be addressed in specific testing and certification, for example those in CJCSI 6212.01E, all concerns have to be addressed eventually. One general way to identify all of them includes five primary tenets of Information Assurance: Confidentiality, Integrity, Authentication, Non-repudiat ...
Next-Generation Secure Computing Base
The Next-Generation Secure Computing Base (NGSCB) (codenamed Palladium and also known as Trusted Windows) is a cancelled software architecture designed by Microsoft which aimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed architecture platforms, such as set-top boxes, while simultaneously preserving the backward compatibility, openness, and flexibility of the Windows operating system. The primary stated objective with NGSCB was to ""protect software from software.""Part of the Trustworthy Computing initiative when unveiled in 2002, NGSCB was expected to be integrated with the Windows Vista operating system, then known by its codename ""Longhorn."" NGSCB relied on hardware designed by members of the Trusted Computing Group to produce a parallel operation environment hosted by a new kernel called the ""Nexus"" that existed alongside Windows and provide new applications with features such as hardware-based process isolation, data encryption based on integrity measurements, authentication of a local or remote machine or software configuration, and encrypted paths for user authentication and graphics output. NGSCB would also facilitate the creation and distribution of rights management policies pertaining to the use of information.The technology was the subject of much controversy during its development, with critics contending that it could be used to impose restrictions on users, enforce vendor lock-in, and undermine fair use rights and open-source software. NGSCB was first demonstrated by Microsoft in 2003 at the Windows Hardware Engineering Conference before undergoing a revision in 2004 that would enable applications written prior to its development to benefit from its functionality. In 2005, reports stated that Microsoft would scale back its plans so that the company could ship its Windows Vista operating system by its target date of 2006. Development of NGSCB spanned almost a decade before its cancellation, one of the lengthiest development periods of a feature intended for the operating system.NGSCB differed from the technologies that Microsoft billed as pillars of Windows Vista during its development—Windows Presentation Foundation, Windows Communication Foundation, and WinFS—in that it was not built upon and did not prioritize .NET managed code during its development. While the technology has not fully materialized, aspects of NGSCB have emerged in Microsoft's BitLocker full disk encryption feature, which can optionally use the Trusted Platform Module to validate the integrity of boot and system files prior to operating system startup; the Measured Boot feature in Windows 8, the certificate attestation features in Windows 8.1, and the Device Guard feature of Windows 10.