ppt
... • UDP is one of the two major transport-layer protocols used in the Internet, the other being TCP. • UDP is the only connectionless transport service. • UDP is less compelx than TCP. “The device at one end of the communication transmits data to the other, without first ensuring that the recipient is ...
... • UDP is one of the two major transport-layer protocols used in the Internet, the other being TCP. • UDP is the only connectionless transport service. • UDP is less compelx than TCP. “The device at one end of the communication transmits data to the other, without first ensuring that the recipient is ...
3Com® SuperStack® 3 Switch 3300 Expandable
... These modules add a fiber Fast Ethernet backbone link to your switched workgroup. The easy-toinstall modules provide full-duplex 200 Mbps throughput over distances up to 2 kilometers of fiber. • The 100BASE-FX dual port module is an excellent choice for resilient connections in mission-critical ...
... These modules add a fiber Fast Ethernet backbone link to your switched workgroup. The easy-toinstall modules provide full-duplex 200 Mbps throughput over distances up to 2 kilometers of fiber. • The 100BASE-FX dual port module is an excellent choice for resilient connections in mission-critical ...
Chapter 7: Secure routing in multi
... • resource consumption can be somewhat decreased by applying the principles of error correcting coding – data packet is coded and the coded packet is split into smaller chunks – a threshold number of chunks is sufficient to reconstruct the entire packet ...
... • resource consumption can be somewhat decreased by applying the principles of error correcting coding – data packet is coded and the coded packet is split into smaller chunks – a threshold number of chunks is sufficient to reconstruct the entire packet ...
Slides - TERENA> Events> tnc2006
... PPP over Ethernet (PPPoE) Separate PPP sessions are established between the Subscriber’s systems (or CPE) and the BBRAS for IPv6 and IPv4 traffic. – Same IPv4/6 address allocation schema as in PPPoA – Sessions may terminate in the LNS in the NSP network (not shown). – If PPP sessions terminate at ...
... PPP over Ethernet (PPPoE) Separate PPP sessions are established between the Subscriber’s systems (or CPE) and the BBRAS for IPv6 and IPv4 traffic. – Same IPv4/6 address allocation schema as in PPPoA – Sessions may terminate in the LNS in the NSP network (not shown). – If PPP sessions terminate at ...
Cache Increases the Capacity of Wireless Networks
... data transmission delay. However, cache is not considered in their studies, and it is not clear how cache affects the capacity of wireless ad hoc networks. In this paper, we study the capacity of wireless ad hoc networks with caching with respect to the cache size of each node (s), the total size of ...
... data transmission delay. However, cache is not considered in their studies, and it is not clear how cache affects the capacity of wireless ad hoc networks. In this paper, we study the capacity of wireless ad hoc networks with caching with respect to the cache size of each node (s), the total size of ...
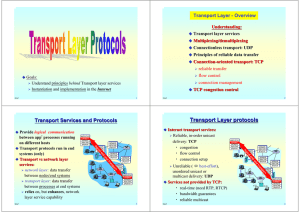
Transport Layer protocols
... Send 1KB pkt every 30.008 msec Æ effective throughput only 267 kbps over 1 Gbps link ¾ network protocol limits use of physical resources a lot! Æ ...
... Send 1KB pkt every 30.008 msec Æ effective throughput only 267 kbps over 1 Gbps link ¾ network protocol limits use of physical resources a lot! Æ ...
Joint Multiple Description Coding and FEC for Delay
... set of L parallel communication links and queues as shown in Fig. 2. Each link has a service rate C bits/sec and a limited buffer with a capacity of B bits. It should be noted that this is different from the assumptions in [5] where an infinite buffer is employed. We only consider wired networks and ...
... set of L parallel communication links and queues as shown in Fig. 2. Each link has a service rate C bits/sec and a limited buffer with a capacity of B bits. It should be noted that this is different from the assumptions in [5] where an infinite buffer is employed. We only consider wired networks and ...
Space Internetworking Architecture 20080716
... In the terrestrial Internet, data reliability is provided by the end systems, primarily using the TCP protocol. If data is lost or corrupted in the network, TCP will detect this and retransmit the data. To ‘hold the gains that have been achieved’, DTN supports a custody transfer mechanism for data r ...
... In the terrestrial Internet, data reliability is provided by the end systems, primarily using the TCP protocol. If data is lost or corrupted in the network, TCP will detect this and retransmit the data. To ‘hold the gains that have been achieved’, DTN supports a custody transfer mechanism for data r ...
Architecture for HomeGate, the Residential Gateway
... circuit mode basic call control. Digital Enhanced Cordless Telecommunications (DECT); Data Services Profile (DSP); Point-to-Point Protocol (PPP) interworking for internet access and general multi-protocol datagram transport Cabled distribution systems for television, sound and interactive multimedia ...
... circuit mode basic call control. Digital Enhanced Cordless Telecommunications (DECT); Data Services Profile (DSP); Point-to-Point Protocol (PPP) interworking for internet access and general multi-protocol datagram transport Cabled distribution systems for television, sound and interactive multimedia ...
EE579T-Class 1C
... • These protocols have become widely used outside the formally-defined Internet • They have some serious flaws, but they ...
... • These protocols have become widely used outside the formally-defined Internet • They have some serious flaws, but they ...
VoIP Performance in SIP-Based Vertical Handovers Between WLAN
... keeps track of the location of mobile stations. The Gateway GSN (GGSN) contains routing information for mobile users and interworks with external packet-switched networks. The GGSN is connected with SGSNs via an IP-based GPRS backbone network. Finally, the Home Location Register (HLR) contains subsc ...
... keeps track of the location of mobile stations. The Gateway GSN (GGSN) contains routing information for mobile users and interworks with external packet-switched networks. The GGSN is connected with SGSNs via an IP-based GPRS backbone network. Finally, the Home Location Register (HLR) contains subsc ...
Securing Wireless Systems
... networking protocols. The idea was to give consumers a more market-friendly name than the technical-sounding 802.11. This family of protocols was created by the Institute of Electrical and Electronics Engineers (IEEE). The IEEE also oversees wired versions of Ethernet such as 802.3. From an equipmen ...
... networking protocols. The idea was to give consumers a more market-friendly name than the technical-sounding 802.11. This family of protocols was created by the Institute of Electrical and Electronics Engineers (IEEE). The IEEE also oversees wired versions of Ethernet such as 802.3. From an equipmen ...
PDF (997 Kbytes) - The Smart Computing Review
... exchanges hello messages among neighbor nodes to keep the messages alive. When no such previous packet transmission exists, each node needs to be activated every time, which leads to a great amount of bandwidth and power consumption. ...
... exchanges hello messages among neighbor nodes to keep the messages alive. When no such previous packet transmission exists, each node needs to be activated every time, which leads to a great amount of bandwidth and power consumption. ...
Chapter 5: Data Link Layer, MAC protocols, and Local Area Networks
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes ➜ “collision”, random access MAC protocol specifies: how to detect collisions (e.g., no Ack, or bad reception) how to recover ...
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes ➜ “collision”, random access MAC protocol specifies: how to detect collisions (e.g., no Ack, or bad reception) how to recover ...
- NTUA
... Summarizing the GÉANT Vision in GN3 • To create an innovative resilient multi-domain hybrid networking environment, using advanced optical transmission & switching technologies • To enable R&E users through their Organizations with flexible, open, interoperable & scalable production quality service ...
... Summarizing the GÉANT Vision in GN3 • To create an innovative resilient multi-domain hybrid networking environment, using advanced optical transmission & switching technologies • To enable R&E users through their Organizations with flexible, open, interoperable & scalable production quality service ...
pdf
... requests the tracker of more peers by sending a tracker ‘handshake’ message, TC advertises itself to the tracker as a seeder with a port number it is listening on (between 6881 and 6889) to attract other peers for incoming connections; the tracker sends back a list of IP addresses and port numbers o ...
... requests the tracker of more peers by sending a tracker ‘handshake’ message, TC advertises itself to the tracker as a seeder with a port number it is listening on (between 6881 and 6889) to attract other peers for incoming connections; the tracker sends back a list of IP addresses and port numbers o ...
Network ID
... Network address • The network address helps the router identify a path within the network cloud. • The router uses the network address to identify the destination network of a packet within an internetwork. • Network address is assigned by higherlevel administrator. Host address is assigned manuall ...
... Network address • The network address helps the router identify a path within the network cloud. • The router uses the network address to identify the destination network of a packet within an internetwork. • Network address is assigned by higherlevel administrator. Host address is assigned manuall ...
Peer-to-peer networks - Pioneers, self-organisation, small
... The peer chooses randomly from the answering peers k as its neighbors. A typical value for k is 5. The Query-message is send to all neighbors and so do they, until peer TTL away is reached. If one of this peers answers with a QuerHit-message a direct connection is established and this is added as ne ...
... The peer chooses randomly from the answering peers k as its neighbors. A typical value for k is 5. The Query-message is send to all neighbors and so do they, until peer TTL away is reached. If one of this peers answers with a QuerHit-message a direct connection is established and this is added as ne ...
Adaptive Fairness through intra-ONU Scheduling for Ethernet
... allocates bandwidth to ONUs through the use of REPORT and GATE messages of MPCP. Within each cycle, ONUs use REPORT messages to report its bandwidth requirements (e.g. buffer occupancy) to the OLT. Upon receiving REPORT messages from the ONUs, the OLT performs the appropriate bandwidth allocation co ...
... allocates bandwidth to ONUs through the use of REPORT and GATE messages of MPCP. Within each cycle, ONUs use REPORT messages to report its bandwidth requirements (e.g. buffer occupancy) to the OLT. Upon receiving REPORT messages from the ONUs, the OLT performs the appropriate bandwidth allocation co ...