Customizable virtual private network service with QoS
... network infrastructure amongst multiple VPNs. The ubiquity of the Internet makes it an ideal infrastructure for providing the VPN service. Fig. 1 illustrates the situation where two dierent VPN topologies are created on top of the same underlying shared network infrastructure. Various forms of priv ...
... network infrastructure amongst multiple VPNs. The ubiquity of the Internet makes it an ideal infrastructure for providing the VPN service. Fig. 1 illustrates the situation where two dierent VPN topologies are created on top of the same underlying shared network infrastructure. Various forms of priv ...
ccna-RoutingTheory
... directly connected networks. We need to configure static routes for networks this router needs to reach. We will need to configure static routes for the other routers as well, as “routing information about a path from one network to another does not provide routing information about the reverse, ...
... directly connected networks. We need to configure static routes for networks this router needs to reach. We will need to configure static routes for the other routers as well, as “routing information about a path from one network to another does not provide routing information about the reverse, ...
AirLive AC.TOP Manual
... The AC.TOP is a ceiling mount wireless multi-function AP based on 1200Mbps 2T2R Wireless AC+ b/g/n MIMO standard radio technologies. It is 2.4G/5G dual band concurrent. The Wireless Access Point is equipped with one Gigabit Auto-sensing Ethernet ports for connecting to LAN and also for cascading to ...
... The AC.TOP is a ceiling mount wireless multi-function AP based on 1200Mbps 2T2R Wireless AC+ b/g/n MIMO standard radio technologies. It is 2.4G/5G dual band concurrent. The Wireless Access Point is equipped with one Gigabit Auto-sensing Ethernet ports for connecting to LAN and also for cascading to ...
Systematic Design of Space-Time Trellis Codes for Wireless
... – The D2D users occupies the vacant cellular spectrum for communication. – completely eliminates cross-layer interference is to divide the licensed spectrum into two parts (orthogonal channel assignment). – a fraction of the subchannels would be used by the cellular users while another fraction woul ...
... – The D2D users occupies the vacant cellular spectrum for communication. – completely eliminates cross-layer interference is to divide the licensed spectrum into two parts (orthogonal channel assignment). – a fraction of the subchannels would be used by the cellular users while another fraction woul ...
Link-State Routing Protocols
... State Packets (LSP) with neighbours which contain -State of each directly connected link -Includes information about neighbors such as neighbor ID, link type, & bandwidth. ...
... State Packets (LSP) with neighbours which contain -State of each directly connected link -Includes information about neighbors such as neighbor ID, link type, & bandwidth. ...
WirelessLANs
... FHSS (Frequency Hopping Spread Spectrum) 2.4 GHz o spreading, de-spreading, signal strength, typically 1 Mbit/s o min. 2.5 frequency hops/s (USA), two-level GFSK modulation ...
... FHSS (Frequency Hopping Spread Spectrum) 2.4 GHz o spreading, de-spreading, signal strength, typically 1 Mbit/s o min. 2.5 frequency hops/s (USA), two-level GFSK modulation ...
PDF
... As an improvement we can let certain hosts forward received data to other hosts. This allows to arrange all hosts in a directed spanning tree over which the data are sent. MPICH-G2 [16] followed this idea by building a multilayer multicast to distinguish wide-area, LAN and local communication. As a ...
... As an improvement we can let certain hosts forward received data to other hosts. This allows to arrange all hosts in a directed spanning tree over which the data are sent. MPICH-G2 [16] followed this idea by building a multilayer multicast to distinguish wide-area, LAN and local communication. As a ...
Avaya Open Networking Adapter
... applications into the Cloud, MPLS connectivity, expensive in comparison with generic high-speed Broadband, becomes increasingly more difficult to justify. Solution: Predicated on the fact that virtually all Branch Office traffic flows to and between remote application systems – either in the corpora ...
... applications into the Cloud, MPLS connectivity, expensive in comparison with generic high-speed Broadband, becomes increasingly more difficult to justify. Solution: Predicated on the fact that virtually all Branch Office traffic flows to and between remote application systems – either in the corpora ...
Slide 1
... Frame size • Different networks use different sizes of frames • Many frames hold about 1500 bytes of data • The sending software breaks up large amounts of data into smaller chunks • The receiving station must then put the chunks back together in the proper order © 2012 The McGraw-Hill Companies, In ...
... Frame size • Different networks use different sizes of frames • Many frames hold about 1500 bytes of data • The sending software breaks up large amounts of data into smaller chunks • The receiving station must then put the chunks back together in the proper order © 2012 The McGraw-Hill Companies, In ...
Document
... RIP: Routing Information Protocol RIP timers Routing-update timer: 30 seconds – random time Route-timeout timer: after timeout -> invalid route Route-flush timer: after timeout -> deletes route ...
... RIP: Routing Information Protocol RIP timers Routing-update timer: 30 seconds – random time Route-timeout timer: after timeout -> invalid route Route-flush timer: after timeout -> deletes route ...
bca501 : core – 18 : computer networks
... hooked onto the next outgoing data frame is called a) piggybacking b) cyclic redundancy check c) fletcher’s checksum d) none of the mentioned Answer: a. 34. Transport layer aggregates data from different applications into a single stream before passing it to a) network layer b) data link layer c) ap ...
... hooked onto the next outgoing data frame is called a) piggybacking b) cyclic redundancy check c) fletcher’s checksum d) none of the mentioned Answer: a. 34. Transport layer aggregates data from different applications into a single stream before passing it to a) network layer b) data link layer c) ap ...
Hacking Wireless Networks
... of 16 Mbps as opposed to the original token ring networks developed by IBM that used shielded twisted pair (STP) cable and ran at 4 or 16 Mbps. ...
... of 16 Mbps as opposed to the original token ring networks developed by IBM that used shielded twisted pair (STP) cable and ran at 4 or 16 Mbps. ...
Технология на програмирането
... Deleting a VLAN If you delete a VLAN and the switch have ports, assigned to it – these ports remains in a non-existing VLAN and are shutdown. The right way is – first to reassign these ports in an existing VLAN, then to delete the VLAN. ...
... Deleting a VLAN If you delete a VLAN and the switch have ports, assigned to it – these ports remains in a non-existing VLAN and are shutdown. The right way is – first to reassign these ports in an existing VLAN, then to delete the VLAN. ...
CIFS Overview: what is CIFS? - London South Bank University
... • The protocol allows a client to manipulate files just as if they were on the local computer. Operations such as read, write, create, delete, and rename are all supported – the only difference being that the files are not on the local computer and are actually on a remote server. • The CIFS protoco ...
... • The protocol allows a client to manipulate files just as if they were on the local computer. Operations such as read, write, create, delete, and rename are all supported – the only difference being that the files are not on the local computer and are actually on a remote server. • The CIFS protoco ...
EPL-Router sorgt für Transparenz und Durchgängigkeit
... Ethernet-Powerlink-segment. The second port is the interface to an IPnetwork, the so-called generic or legacy Ethernet. On the Ethernet Powerlinkside the Ethernet Powerlink-Router acts like any other Ethernet Powerlinkparticipant and has the communication profile for a Controlled Node (CN) implement ...
... Ethernet-Powerlink-segment. The second port is the interface to an IPnetwork, the so-called generic or legacy Ethernet. On the Ethernet Powerlinkside the Ethernet Powerlink-Router acts like any other Ethernet Powerlinkparticipant and has the communication profile for a Controlled Node (CN) implement ...
Chapter 1 Security Issues in the TCP/IP Suite
... For example, an attacker can silence a host A from sending further packets to B by sending a spoofed packet announcing a window size of zero to A as though it originated from B. Note that the attacker’s machine cannot simply be assigned the ip address of another host T, using ifconfig or a similar c ...
... For example, an attacker can silence a host A from sending further packets to B by sending a spoofed packet announcing a window size of zero to A as though it originated from B. Note that the attacker’s machine cannot simply be assigned the ip address of another host T, using ifconfig or a similar c ...
A Traffic-aware Power Management Protocol for
... equivalent from a routing perspective and turning off unnecessary nodes. The network is divided into grids so that all nodes in the adjacent grids can communicate with each other directly. At each point in time, only one node in each grid is active. GPS or other positioning system is required to get ...
... equivalent from a routing perspective and turning off unnecessary nodes. The network is divided into grids so that all nodes in the adjacent grids can communicate with each other directly. At each point in time, only one node in each grid is active. GPS or other positioning system is required to get ...
Power Point Chapter 06 CCNA2
... associated ports for those networks. • Routers use routing protocols to manage information received from other routers and its interfaces. • The routing protocol learns all available routes, places the best routes into the routing table, and removes routes when they are no longer valid. • The router ...
... associated ports for those networks. • Routers use routing protocols to manage information received from other routers and its interfaces. • The routing protocol learns all available routes, places the best routes into the routing table, and removes routes when they are no longer valid. • The router ...
Detecting Wireless LAN MAC Address Spoofing Joshua Wright
... these tools rely on using a faked MAC address, masquerading as an authorized wireless access point or as an authorized client. Using these tools, an attacker can launch denial of service attacks, bypass access control mechanisms, or falsely advertise services to wireless clients. This presents uniqu ...
... these tools rely on using a faked MAC address, masquerading as an authorized wireless access point or as an authorized client. Using these tools, an attacker can launch denial of service attacks, bypass access control mechanisms, or falsely advertise services to wireless clients. This presents uniqu ...
Opportunities and Challenges of Community
... Inexpensive electronically steerable directional antenna or MIMO for range enhancement ...
... Inexpensive electronically steerable directional antenna or MIMO for range enhancement ...
Document
... Sender knows the IP address of the target. IP asks ARP to create ARP request message. It includes sender’s and target’s IP and physical addresses. Target Physical address is all 0s. Message is passed to data link layer, encapsulated in a frame using sender’s physical address. The physical destinatio ...
... Sender knows the IP address of the target. IP asks ARP to create ARP request message. It includes sender’s and target’s IP and physical addresses. Target Physical address is all 0s. Message is passed to data link layer, encapsulated in a frame using sender’s physical address. The physical destinatio ...
Implementing OpenLISP with LISP+ALT
... Figure 2: Growth of the BGP Table - 1994 to Present [8] caused by more provider independent address space that has been given out over the last few years and less provider aggregation. Another factor of table growth is multihoming, where two providers announce the same subnet. BGP was not ment to be ...
... Figure 2: Growth of the BGP Table - 1994 to Present [8] caused by more provider independent address space that has been given out over the last few years and less provider aggregation. Another factor of table growth is multihoming, where two providers announce the same subnet. BGP was not ment to be ...
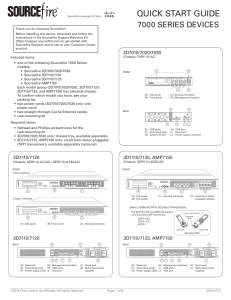
http://www.cisco.com/c/dam/en/us/td/docs/security/sourcefire/3d-system/53/quick-start-guides/QSG-3D7xxx-v53-3-20140311.pdf
... appropriate cables (copper or fiber) in either a passive or inline cabling configuration. The trusted management network (a restricted network protected from unauthorized access) may have a single secure connection to the Internet for security updates and similar functions, but is separate from the ...
... appropriate cables (copper or fiber) in either a passive or inline cabling configuration. The trusted management network (a restricted network protected from unauthorized access) may have a single secure connection to the Internet for security updates and similar functions, but is separate from the ...