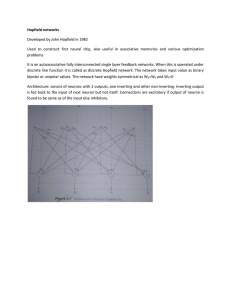
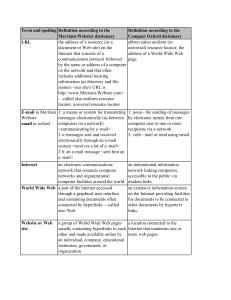
network - CCIT131
... WLAN is more secure compared to LAN (true – false) The Internet is an example of PAN (true – false) Bluetooth is an example of LAN (true – false) ...
... WLAN is more secure compared to LAN (true – false) The Internet is an example of PAN (true – false) Bluetooth is an example of LAN (true – false) ...
Chapter17 - Website Staff UI
... – When two or more computers are interconnected via a communication network ...
... – When two or more computers are interconnected via a communication network ...
NETWORKING LAB -
... Network Interface Card (NIC) - Every computer (and most other devices) is connected to a network through an NIC. In most desktop computers, this is an Ethernet card (normally 10 or 100 Mbps) that is plugged into a slot on the computer's motherboard. Media Access Control (MAC) Address - This is the p ...
... Network Interface Card (NIC) - Every computer (and most other devices) is connected to a network through an NIC. In most desktop computers, this is an Ethernet card (normally 10 or 100 Mbps) that is plugged into a slot on the computer's motherboard. Media Access Control (MAC) Address - This is the p ...
Switches
... Higher-layer switches may also be called routing switches or application switches ...
... Higher-layer switches may also be called routing switches or application switches ...
Chapter One
... Switches Subdivide a network into smaller logical pieces Create multiple, smaller collision domains In a half duplex switched network there are only two devices in each collision domain. In a full-duplex switched environment there is only 1 device in each collision domain (0 % chance of collision) ...
... Switches Subdivide a network into smaller logical pieces Create multiple, smaller collision domains In a half duplex switched network there are only two devices in each collision domain. In a full-duplex switched environment there is only 1 device in each collision domain (0 % chance of collision) ...
Technical Services - Austin Convention Center
... • Multiple high-speed, 100+ mb/sec Internet access connections, running on a Cisco powered gigabit Ethernet infrastructure • Limited complimentary Wireless Internet Access throughout entire facility • 1,280 registered Internet addresses (5 Class C) • 131,072 NATed Internet addresses with ability to ...
... • Multiple high-speed, 100+ mb/sec Internet access connections, running on a Cisco powered gigabit Ethernet infrastructure • Limited complimentary Wireless Internet Access throughout entire facility • 1,280 registered Internet addresses (5 Class C) • 131,072 NATed Internet addresses with ability to ...
Chapter 7 Part 2 Networks
... – An Ethernet is a network named because it uses the Ethernet Protocol as the means or standard by which the nodes on the network communicate. The Ethernet protocol was developed by the Institute of Electrical and Electronics Engineers (IEEE). • Each standard that the IEEE develops is numbered with ...
... – An Ethernet is a network named because it uses the Ethernet Protocol as the means or standard by which the nodes on the network communicate. The Ethernet protocol was developed by the Institute of Electrical and Electronics Engineers (IEEE). • Each standard that the IEEE develops is numbered with ...
05. Example Networks..
... Connection-Oriented Networks: X.25, Frame Relay, and ATM • first example of a connection-oriented network is X.25, which was the first public data network, deployed in the 1970s at a time when telephone service was a ...
... Connection-Oriented Networks: X.25, Frame Relay, and ATM • first example of a connection-oriented network is X.25, which was the first public data network, deployed in the 1970s at a time when telephone service was a ...
Table 9.1 Spelling and definitions.pdf
... 1: noun - the sending of messages by electronic means from one computer user to one or more recipients via a network. 2: verb - mail or send using email. ...
... 1: noun - the sending of messages by electronic means from one computer user to one or more recipients via a network. 2: verb - mail or send using email. ...
classful addressing - E Learning UPN Veteran Yogyakarta
... • Performance can be adversely affected under heavy traffic loads, due to collisions and the resulting retransmissions. A router is used to connect IP networks to minimize the amount of traffic each segment must receive. ...
... • Performance can be adversely affected under heavy traffic loads, due to collisions and the resulting retransmissions. A router is used to connect IP networks to minimize the amount of traffic each segment must receive. ...
MCN 7200 Advanced Internetworking Protocols
... This course assumes the basic knowledge regarding the Internet and its protocols. It offers advanced level treatment of data transport and switching concepts; TCP/IP protocol stack with detailed analysis. It also looks at architectures of network components mainly routers and switches and their type ...
... This course assumes the basic knowledge regarding the Internet and its protocols. It offers advanced level treatment of data transport and switching concepts; TCP/IP protocol stack with detailed analysis. It also looks at architectures of network components mainly routers and switches and their type ...
Mac: new
... add a new node; can add more nodes; Cons: require coordination among the nodes on when to use the bus Pros: high bandwidth and span large distance; Cons: relatively expensive and hard to install; communication among the computers is difficult (require a token – token ring) ...
... add a new node; can add more nodes; Cons: require coordination among the nodes on when to use the bus Pros: high bandwidth and span large distance; Cons: relatively expensive and hard to install; communication among the computers is difficult (require a token – token ring) ...
Telecommunications and Networks
... – Electronic commerce – Enterprise collaboration – Other applications • Business operations, management, strategic objectives ...
... – Electronic commerce – Enterprise collaboration – Other applications • Business operations, management, strategic objectives ...
Telecommunications and Networks
... – Electronic commerce – Enterprise collaboration – Other applications • Business operations, management, strategic objectives ...
... – Electronic commerce – Enterprise collaboration – Other applications • Business operations, management, strategic objectives ...
Communications & Networks
... • Many users can use same document at the same time (workgroup computing) ...
... • Many users can use same document at the same time (workgroup computing) ...
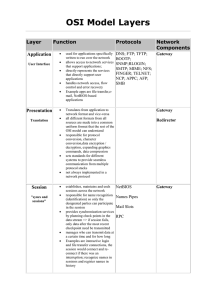
OSI Model Layers
... turns packets into raw bits 100101 Logical Link Control and at the receiving end turns bits into packets. error correction handles data frames between the and flow control Network and Physical layers manages link the receiving end packages raw control and data from the Physical layer into define ...
... turns packets into raw bits 100101 Logical Link Control and at the receiving end turns bits into packets. error correction handles data frames between the and flow control Network and Physical layers manages link the receiving end packages raw control and data from the Physical layer into define ...
MAN Metropolitan Area Network = A metropolitan
... functionality for other programs or devices, called "clients". ISP Internet service provider = An Internet service provider is an organization that provides services for accessing and using the Internet. DIRECTORY Search for UT Austin students, faculty and staff by entering a name, email address, EI ...
... functionality for other programs or devices, called "clients". ISP Internet service provider = An Internet service provider is an organization that provides services for accessing and using the Internet. DIRECTORY Search for UT Austin students, faculty and staff by entering a name, email address, EI ...
network topology
... the access points are connected to a core servers and switch using the primary and secondary cables the last floor there is an IP Tel switch the core switches and the IP Tel switch is connected with the secure router and juniper firewall switch using UTP/C cable. ...
... the access points are connected to a core servers and switch using the primary and secondary cables the last floor there is an IP Tel switch the core switches and the IP Tel switch is connected with the secure router and juniper firewall switch using UTP/C cable. ...