Network review
... • used by hosts, routers, gateways to communication network-level information – error reporting: unreachable host, network, port, protocol ...
... • used by hosts, routers, gateways to communication network-level information – error reporting: unreachable host, network, port, protocol ...
Introduction
... Logically concatenates a set of links to form the abstraction of an end-to-end link Allows an end-system to communicate with any other end-system by computing a route between them Hides individual behavior of datalink layer Provides unique network-wide addresses ...
... Logically concatenates a set of links to form the abstraction of an end-to-end link Allows an end-system to communicate with any other end-system by computing a route between them Hides individual behavior of datalink layer Provides unique network-wide addresses ...
lecture
... send a claim frame that includes the node’s TTRT bid when receive claim frame, update the bid and forward if your claim frame makes it all the way around the ring: • your bid was the lowest ...
... send a claim frame that includes the node’s TTRT bid when receive claim frame, update the bid and forward if your claim frame makes it all the way around the ring: • your bid was the lowest ...
Mobility Management Compromise Proposal
... • Large radio infrastructure vendors run heavy simulations to prove their technology • If a company gets a key patent into the standard, they stand to win big time ...
... • Large radio infrastructure vendors run heavy simulations to prove their technology • If a company gets a key patent into the standard, they stand to win big time ...
3rd Edition: Chapter 4
... Two key router functions: run routing algorithms/protocol (RIP, OSPF, BGP) forwarding datagrams from incoming to outgoing link ...
... Two key router functions: run routing algorithms/protocol (RIP, OSPF, BGP) forwarding datagrams from incoming to outgoing link ...
MakingNetworksWork - Computing Sciences
... • 2 dominate networking models are used to decompose the problem networking: – OSI: Open Systems Interconnection (OSI) networking suite – IEEE 802: family of standards ...
... • 2 dominate networking models are used to decompose the problem networking: – OSI: Open Systems Interconnection (OSI) networking suite – IEEE 802: family of standards ...
LinkStar DVB-S2
... of satellite communications technology, advanced IP routing, quality of service, data acceleration, and compression in two complementary platforms. Your IP applications will seamlessly integrate via satellite through the use of industry standards such as DVB-S, DVB-S2, and DVB-RCS. Enterprise applic ...
... of satellite communications technology, advanced IP routing, quality of service, data acceleration, and compression in two complementary platforms. Your IP applications will seamlessly integrate via satellite through the use of industry standards such as DVB-S, DVB-S2, and DVB-RCS. Enterprise applic ...
social network
... Social Network Analysis: Degree Centrality • Degree centrality is simply the number of direct relationships that an entity has. • An entity with high degree centrality: – Is generally an active player in the network. – Is often a connector or hub in the network. – s not necessarily the most connect ...
... Social Network Analysis: Degree Centrality • Degree centrality is simply the number of direct relationships that an entity has. • An entity with high degree centrality: – Is generally an active player in the network. – Is often a connector or hub in the network. – s not necessarily the most connect ...
T01
... • Ethernet addresses • Every Ethernet network interface card (NIC) is given a unique identifier called a MAC address. • This is assigned by the manufacturer of the card. • The MAC address comprises of a 48-bit number. • The first 24 bits identify the manufacturer • The second half of the address is ...
... • Ethernet addresses • Every Ethernet network interface card (NIC) is given a unique identifier called a MAC address. • This is assigned by the manufacturer of the card. • The MAC address comprises of a 48-bit number. • The first 24 bits identify the manufacturer • The second half of the address is ...
Peer 2 Peer Programming - University of Wisconsin
... The design of simple file-transfer has been used before peer-to-peer was introduced, but it wasn’t until the beginning of Napster that file-transfer among home users became popular. Napster was created by Shawn Fanning in late 1999, while attending Northeastern University in Boston [5]. Napster was ...
... The design of simple file-transfer has been used before peer-to-peer was introduced, but it wasn’t until the beginning of Napster that file-transfer among home users became popular. Napster was created by Shawn Fanning in late 1999, while attending Northeastern University in Boston [5]. Napster was ...
Traffic Measurement and Analysis of Wide Area
... data centres are consolidated to a central location, the WAN links almost become an extension of LAN and as a network is only as fast as its slowest link, it becomes essential to optimize the performance of a WAN link. So, understanding the current WAN link utilization may help us figure out the opt ...
... data centres are consolidated to a central location, the WAN links almost become an extension of LAN and as a network is only as fast as its slowest link, it becomes essential to optimize the performance of a WAN link. So, understanding the current WAN link utilization may help us figure out the opt ...
iUMG Key Features and Benefits Key Fe
... offers an end-to-end packet telephony solution that provides tollquality voice and enhanced services. Because the TG platform supports thousands of DS0s, it can be easily deployed in a nationwide core-packet network to transport voice traffic between central offices. The TG also enhances availabilit ...
... offers an end-to-end packet telephony solution that provides tollquality voice and enhanced services. Because the TG platform supports thousands of DS0s, it can be easily deployed in a nationwide core-packet network to transport voice traffic between central offices. The TG also enhances availabilit ...
Inmarsat BGAN Network Overview
... BGP peering can be run inside the traffic tunnel for up/down state detection. UT address ranges which are live in the GGSN can also be advertised to the DP’s POP via this session. Global IP • Global IP is an feature used when an APN with an identical name is configured in both GGSNs, and the same IP ...
... BGP peering can be run inside the traffic tunnel for up/down state detection. UT address ranges which are live in the GGSN can also be advertised to the DP’s POP via this session. Global IP • Global IP is an feature used when an APN with an identical name is configured in both GGSNs, and the same IP ...
Network
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
1 - Cisco Support Community
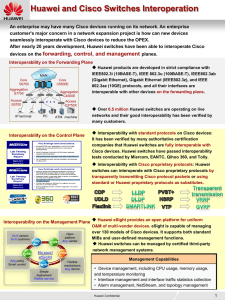
... China Telcom's HQ campus network ODS upgrade project: The gateway originally deployed on Cisco C3560 was moved to the S9300 CSS system newly deployed on the network. The S9300 switches worked as aggregation switches and used CSS technology to improve network reliability. Cisco 3560 and Huawei S9300 ...
... China Telcom's HQ campus network ODS upgrade project: The gateway originally deployed on Cisco C3560 was moved to the S9300 CSS system newly deployed on the network. The S9300 switches worked as aggregation switches and used CSS technology to improve network reliability. Cisco 3560 and Huawei S9300 ...
cdma450 Core Network - CDMA Development Group
... – Push to Talk over Cellular (PoC) being addressed in OMA • With 3GPP2 review and comment ...
... – Push to Talk over Cellular (PoC) being addressed in OMA • With 3GPP2 review and comment ...