Document
... ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Collect some statistics about network usage with the “Statistics ...
... ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Collect some statistics about network usage with the “Statistics ...
DEPARTMENT OF ECE 2-MARK QUESTIONS AND ANSWERS S
... The Application Layer enables the user, whether human or software, to access the network. It provides user interfaces and support for services such as e-mail, shared database management and other types of distributed information services o Network virtual Terminal o File transfer, access and Managem ...
... The Application Layer enables the user, whether human or software, to access the network. It provides user interfaces and support for services such as e-mail, shared database management and other types of distributed information services o Network virtual Terminal o File transfer, access and Managem ...
Chapter 8 Internet Protocols
... IP Fragmentation • In IP, reassembly is at destination only • Uses fields in header — Data Unit Identifier – In order to uniquely identify datagram – all fragments that belong to a datagram share the same identifier 1. Source and destination addresses 2. Upper protocol layer (e.g. TCP) 3. Identific ...
... IP Fragmentation • In IP, reassembly is at destination only • Uses fields in header — Data Unit Identifier – In order to uniquely identify datagram – all fragments that belong to a datagram share the same identifier 1. Source and destination addresses 2. Upper protocol layer (e.g. TCP) 3. Identific ...
SCORE: A Scalable Architecture for Implementing Resource
... IP provides logical address space and a corresponding addressing schema IP address is a globally unique or private number associated with a host network interface Every system which will send packets directly out across the Internet must have a unique IP address IP addresses are based on where stati ...
... IP provides logical address space and a corresponding addressing schema IP address is a globally unique or private number associated with a host network interface Every system which will send packets directly out across the Internet must have a unique IP address IP addresses are based on where stati ...
07-IPheader
... be routed over, decremented by most routers - used to prevent accidental routing loops IP Checksum ...
... be routed over, decremented by most routers - used to prevent accidental routing loops IP Checksum ...
chap1v3sem3
... 10 The network shown in the diagram is having problems routing traffic. It is suspected that the problem is with the addressing scheme. What is the problem with the addressing used in the topology? The address assigned to the Ethernet0 interface of Router1 is a broadcast address for that subnetwork. ...
... 10 The network shown in the diagram is having problems routing traffic. It is suspected that the problem is with the addressing scheme. What is the problem with the addressing used in the topology? The address assigned to the Ethernet0 interface of Router1 is a broadcast address for that subnetwork. ...
Broadcast Address
... Internet and TCP/IP • Internet is a global network of interconnected computers, enabling users to share information along multiple channels. • Majority of widely accessible information on the internet consists of inter-linked hypertext documents and other resources of the World Wide Web (WWW). • Th ...
... Internet and TCP/IP • Internet is a global network of interconnected computers, enabling users to share information along multiple channels. • Majority of widely accessible information on the internet consists of inter-linked hypertext documents and other resources of the World Wide Web (WWW). • Th ...
Giuseppe Razzano , Neeli R. Prasad , Roberto De Paolis
... Hacking a WLAN, the first problem is to locate and detect the wireless network. Beacons sent by APs at predefined intervals are essentially invitations and driving directions that enable the client to easily find the AP and configure the appropriate settings to communicate. WLAN scanners allow users ...
... Hacking a WLAN, the first problem is to locate and detect the wireless network. Beacons sent by APs at predefined intervals are essentially invitations and driving directions that enable the client to easily find the AP and configure the appropriate settings to communicate. WLAN scanners allow users ...
Ad-Hoc Wireless Networks
... IEEE 802.11 Wireless LAN The principles of Wireless Local Area Network (WLAN) are defined in IEEE 802.11 standard • It defines two different topologies: ad-hoc network and infrastructure network ...
... IEEE 802.11 Wireless LAN The principles of Wireless Local Area Network (WLAN) are defined in IEEE 802.11 standard • It defines two different topologies: ad-hoc network and infrastructure network ...
ppt
... • Programming network applications requires knowledge of the protocol and the communication layers. From the perspective of applications networking is a service that allows an application to send and receive data from other computers. • PCs connected to the network have unique addresses/names known ...
... • Programming network applications requires knowledge of the protocol and the communication layers. From the perspective of applications networking is a service that allows an application to send and receive data from other computers. • PCs connected to the network have unique addresses/names known ...
Please note
... moves one space ahead. For this process to complete, how many bytes are transmitted across the network? Please consider the transport and the network layer overheads only, no link later overhead). Assume no optimization is done (each segment is acknowledged separately). Please draw the timeline of e ...
... moves one space ahead. For this process to complete, how many bytes are transmitted across the network? Please consider the transport and the network layer overheads only, no link later overhead). Assume no optimization is done (each segment is acknowledged separately). Please draw the timeline of e ...
network
... Usually, the server has applications and data storage that are shared in common by multiple computer users. A local area network may serve as few as two or three users (for example, in a home network) or as many as thousands of users ...
... Usually, the server has applications and data storage that are shared in common by multiple computer users. A local area network may serve as few as two or three users (for example, in a home network) or as many as thousands of users ...
that enables communication and transmission of data between
... precisely in April 1969 saw the release of the first RFC (Request for Comments) document, which launches a series of technical publications about the Internet. In the early 1970 the ARPANET grew to connect research institutes and laboratories ...
... precisely in April 1969 saw the release of the first RFC (Request for Comments) document, which launches a series of technical publications about the Internet. In the early 1970 the ARPANET grew to connect research institutes and laboratories ...
Lecture 3: Data Link Layer Security
... on the subnet will router through the attacker’s machine – You have to poison the ARP cache of every host on the subnet – Better if targeting a single host on the network – Should not spoof the IP of another client ...
... on the subnet will router through the attacker’s machine – You have to poison the ARP cache of every host on the subnet – Better if targeting a single host on the network – Should not spoof the IP of another client ...
The Internet and the Web
... since the packets are transmitted independently, it is likely that at least part of the message will arrive (even if some failures occur within the network) software at the destination can recognize which packets are missing and request retransmission ...
... since the packets are transmitted independently, it is likely that at least part of the message will arrive (even if some failures occur within the network) software at the destination can recognize which packets are missing and request retransmission ...
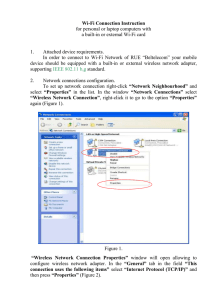
инструкция
... PLEASE NOTE: Should you choose connection to the wireless network “byfly WIFI” and the message “No or limited connectivity” is displayed in the window containing the list of available wireless network connections, or the authorization page fails to download when entering the necessary address in th ...
... PLEASE NOTE: Should you choose connection to the wireless network “byfly WIFI” and the message “No or limited connectivity” is displayed in the window containing the list of available wireless network connections, or the authorization page fails to download when entering the necessary address in th ...
Ch 2: TCP/IP Concepts Review
... Identifies the service that is running Example: HTTP uses port 80 A 16-bit number – 65,536 ports Each TCP packet has a source and destination port Blocking Ports Helps you stop or disable services that are not needed Open ports are an invitation for an attack You can’t block all the ports Th ...
... Identifies the service that is running Example: HTTP uses port 80 A 16-bit number – 65,536 ports Each TCP packet has a source and destination port Blocking Ports Helps you stop or disable services that are not needed Open ports are an invitation for an attack You can’t block all the ports Th ...
An overview
... The header contains sufficient information for implementing the intended services. The header is an overhead to the payload. The payload generally contains a header from another protocol. ...
... The header contains sufficient information for implementing the intended services. The header is an overhead to the payload. The payload generally contains a header from another protocol. ...
VPN, Mobility - CSCI 6433 Internet Protocols
... • Tunnel mode: IPSec protects complete encapsulated IP datagram after IP header is applied. IP datagram is created normally, then AH and ESP headers are added. Usually associated with “bump in the stack” and “bump in the wire” implementations ...
... • Tunnel mode: IPSec protects complete encapsulated IP datagram after IP header is applied. IP datagram is created normally, then AH and ESP headers are added. Usually associated with “bump in the stack” and “bump in the wire” implementations ...
Job Class: 158818 Rev: 04/15 Exempt Page: 1
... Installs, upgrades, and supports network hardware and software needed to manage the campus enterprise backbone network. Installs, upgrades, and supports the campus enterprise wireless network. Implements, upgrades, and monitor the campus virtual private networking services. Works with Systems Admini ...
... Installs, upgrades, and supports network hardware and software needed to manage the campus enterprise backbone network. Installs, upgrades, and supports the campus enterprise wireless network. Implements, upgrades, and monitor the campus virtual private networking services. Works with Systems Admini ...
mMOM: Efficient Mobile Multicast Support Based on the Mobility of
... a mobile node informs its home agent of its careof-address an extension to ICMP Router Discovery, which allows mobile nodes to discover prospective home agents and foreign agents the rules for routing packets to and from mobile nodes, including the specification of one mandatory tunneling mechan ...
... a mobile node informs its home agent of its careof-address an extension to ICMP Router Discovery, which allows mobile nodes to discover prospective home agents and foreign agents the rules for routing packets to and from mobile nodes, including the specification of one mandatory tunneling mechan ...
Midterm Answers
... Protocols: IP and IPX (a Novell network protocol that is not around much any more). ATM also provides some network layer functionality; it's usually considered as lying between layers. You could also mention IPv6, but that's still IP. Transport: ...
... Protocols: IP and IPX (a Novell network protocol that is not around much any more). ATM also provides some network layer functionality; it's usually considered as lying between layers. You could also mention IPv6, but that's still IP. Transport: ...