Adhoc NUC - The Astrophotography Manual
... While at home, the most convenient way to connect to the NUC is via your wireless router. RDP needs the IP address of your NUC. Most routers dynamically assign IP addresses, depending on the order of connection. To fix an IP address, most routers allow you to set a static IP address for a particular ...
... While at home, the most convenient way to connect to the NUC is via your wireless router. RDP needs the IP address of your NUC. Most routers dynamically assign IP addresses, depending on the order of connection. To fix an IP address, most routers allow you to set a static IP address for a particular ...
Microsoft Windows 2003 Server
... The File Sharing wizard allows you first to select the folder you want to share. This folder will be a place on your hard drive that you would like others to see The next screen will ask the Share Name that others will see over the network. Note: The Share Name does not need to be the same as the fo ...
... The File Sharing wizard allows you first to select the folder you want to share. This folder will be a place on your hard drive that you would like others to see The next screen will ask the Share Name that others will see over the network. Note: The Share Name does not need to be the same as the fo ...
Local-Area Networks
... which all computers are connected in a ring or star topology and a bit- or token-passing scheme is used. This prevents the collision of data between two computers that want to send messages at the same time. The Token Ring protocol is the ...
... which all computers are connected in a ring or star topology and a bit- or token-passing scheme is used. This prevents the collision of data between two computers that want to send messages at the same time. The Token Ring protocol is the ...
NETWORKING LAB -
... Network Interface Card (NIC) - Every computer (and most other devices) is connected to a network through an NIC. In most desktop computers, this is an Ethernet card (normally 10 or 100 Mbps) that is plugged into a slot on the computer's motherboard. Media Access Control (MAC) Address - This is the p ...
... Network Interface Card (NIC) - Every computer (and most other devices) is connected to a network through an NIC. In most desktop computers, this is an Ethernet card (normally 10 or 100 Mbps) that is plugged into a slot on the computer's motherboard. Media Access Control (MAC) Address - This is the p ...
Higher Layer Protocols
... • May change the format of the data in the packet or use a different lower‐level protocol suite to transfer from one domain to another • Examples of translator use include: – Convert a video to a lower quality format – If an application‐level firewall prevents the forwarding of ...
... • May change the format of the data in the packet or use a different lower‐level protocol suite to transfer from one domain to another • Examples of translator use include: – Convert a video to a lower quality format – If an application‐level firewall prevents the forwarding of ...
chapterw4
... At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. ...
... At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. ...
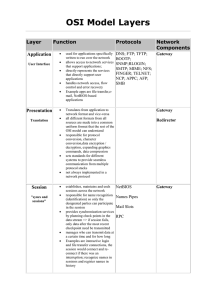
OSI Model Layers
... sets standards for different systems to provide seamless communication from multiple protocol stacks not always implemented in a network protocol establishes, maintains and ends sessions across the network responsible for name recognition (identification) so only the designated parties can participa ...
... sets standards for different systems to provide seamless communication from multiple protocol stacks not always implemented in a network protocol establishes, maintains and ends sessions across the network responsible for name recognition (identification) so only the designated parties can participa ...
networking
... numbers, connected by dots. Each number ranges between 0 at 255. An example number is “148.4.2.231”. • A computer that has an IP address is not necessarily directly connected the Internet. ...
... numbers, connected by dots. Each number ranges between 0 at 255. An example number is “148.4.2.231”. • A computer that has an IP address is not necessarily directly connected the Internet. ...
Slides - Duke Computer Science
... • How should the functionality that controls a network be divided up? • Important: everyone hates net outages • Practical: solutions can be implemented without changing IP or end-hosts • Relevant: trends toward separating decisionmaking from forwarding • Unsolved: problem is not solved by running BG ...
... • How should the functionality that controls a network be divided up? • Important: everyone hates net outages • Practical: solutions can be implemented without changing IP or end-hosts • Relevant: trends toward separating decisionmaking from forwarding • Unsolved: problem is not solved by running BG ...
Click to Principals of Networking notes
... People use networks everyday. Examples of networks are a mail delivery system, a telephone system, a public transportation system, a corporate computer network, and the Internet. Computers can be linked by networks to share data and resources. A network can be as simple as two computers connected by ...
... People use networks everyday. Examples of networks are a mail delivery system, a telephone system, a public transportation system, a corporate computer network, and the Internet. Computers can be linked by networks to share data and resources. A network can be as simple as two computers connected by ...
IP Version 10.0: A Strawman Design Beyond IPv6
... SATCOM, are atypical to the vast majority of networks connected to the Internet. As a result, there were very few vocal proponents advocating the separation of locator and identifier in addresses, or prudence in the size of the new IP header. And this latter aspect, the overhead of header efficiency ...
... SATCOM, are atypical to the vast majority of networks connected to the Internet. As a result, there were very few vocal proponents advocating the separation of locator and identifier in addresses, or prudence in the size of the new IP header. And this latter aspect, the overhead of header efficiency ...
Chapter 1
... • This can be done to an extent by ‘tunneling’. • Make multiple physical layers look like one layer to the IP layer by encapsulating layer ...
... • This can be done to an extent by ‘tunneling’. • Make multiple physical layers look like one layer to the IP layer by encapsulating layer ...
Com811: Building The Mobile Internet
... • This can be done to an extent by ‘tunneling’. • Make multiple physical layers look like one layer to the IP layer by encapsulating layer ...
... • This can be done to an extent by ‘tunneling’. • Make multiple physical layers look like one layer to the IP layer by encapsulating layer ...
3rd Edition: Chapter 2
... Telnet [RFC 854] HTTP [RFC 2616] FTP [RFC 959] proprietary (e.g. Youtube) proprietary (e.g., Skype) ...
... Telnet [RFC 854] HTTP [RFC 2616] FTP [RFC 959] proprietary (e.g. Youtube) proprietary (e.g., Skype) ...
Chapter 3 Physical Components of a Network
... the computer names such as www.cisco.com to the corresponding unique IP address. • Address translations are used each time the Internet is accessed. • The process of translating names to addresses is known as name resolution. ...
... the computer names such as www.cisco.com to the corresponding unique IP address. • Address translations are used each time the Internet is accessed. • The process of translating names to addresses is known as name resolution. ...
Network layer addresses - Computer Science Department | Montana
... • Routing Information Protocol (RIP): is a dynamic distance vector interior routing protocol commonly used on the Internet. – Computers using RIP broadcast routing tables every minute or so. – Now used on simpler networks. • Open Shortest Path First (OSPF): another dynamic interior routing protocol ...
... • Routing Information Protocol (RIP): is a dynamic distance vector interior routing protocol commonly used on the Internet. – Computers using RIP broadcast routing tables every minute or so. – Now used on simpler networks. • Open Shortest Path First (OSPF): another dynamic interior routing protocol ...
Hour 4
... unused and should always have a value of zero. The next bit is called the DF (Don't Fragment) flag. The DF flag signifies whether fragmentation is allowed (value = 0) or not (value = 1), The next bit is the MF (More Fragments) flag, which tells the receiver that more fragments are on the way. When M ...
... unused and should always have a value of zero. The next bit is called the DF (Don't Fragment) flag. The DF flag signifies whether fragmentation is allowed (value = 0) or not (value = 1), The next bit is the MF (More Fragments) flag, which tells the receiver that more fragments are on the way. When M ...
Example # 1
... IPv4 (IP version 4) addresses. The need for more addresses, in addition to other concerns about the IP layer, motivated a new design of the IP layer called the new generation of IP or IPv6 (lP version 6). In this version, the Internet uses 128-bit addresses that give much greater flexibility in addr ...
... IPv4 (IP version 4) addresses. The need for more addresses, in addition to other concerns about the IP layer, motivated a new design of the IP layer called the new generation of IP or IPv6 (lP version 6). In this version, the Internet uses 128-bit addresses that give much greater flexibility in addr ...
Europass Curriculum Vitae
... Responsible for restructuring data network and systems of the largest bank in Angola: • New architecture and concepts introduced: installation and configuration of servers, routers and switches. Redundancy and QoS. • Security: access-lists, VPN, firewall, antivirus, software updates. • WAN and LAN b ...
... Responsible for restructuring data network and systems of the largest bank in Angola: • New architecture and concepts introduced: installation and configuration of servers, routers and switches. Redundancy and QoS. • Security: access-lists, VPN, firewall, antivirus, software updates. • WAN and LAN b ...
No Slide Title
... – Is the successor to the currently used IPv4 – Specification completed in 1994 – Makes improvements to IPv4 (no revolutionary changes) • One (not the only !) feature of IPv6 is a significant increase in of the IP address to 128 bits (16 bytes) • IPv6 will solve – for the foreseeable future – the pr ...
... – Is the successor to the currently used IPv4 – Specification completed in 1994 – Makes improvements to IPv4 (no revolutionary changes) • One (not the only !) feature of IPv6 is a significant increase in of the IP address to 128 bits (16 bytes) • IPv6 will solve – for the foreseeable future – the pr ...
ToddT&R
... terminals) and their peripheral devices are connected, it is called a network. The simplest form of a network is when one computer is connected directly to another computer using a cable. However, a network can also consist of hundreds of computers connected together. The devices used to send data t ...
... terminals) and their peripheral devices are connected, it is called a network. The simplest form of a network is when one computer is connected directly to another computer using a cable. However, a network can also consist of hundreds of computers connected together. The devices used to send data t ...
Document
... The most basic type of client-server architecture employs only two types of nodes: clients and servers This type of architecture is sometimes referred to as two-tier It allows devices to share files and resources Protocol is a convention or standard that controls or enables the connection, com ...
... The most basic type of client-server architecture employs only two types of nodes: clients and servers This type of architecture is sometimes referred to as two-tier It allows devices to share files and resources Protocol is a convention or standard that controls or enables the connection, com ...
William Stallings Data and Computer Communications
... OSPF (open shortest path first): Routing based on number of hops, link speed, congestion ...
... OSPF (open shortest path first): Routing based on number of hops, link speed, congestion ...
Document
... ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Collect some statistics about network usage with the “Statistics ...
... ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Collect some statistics about network usage with the “Statistics ...