Introduction CS 239 Security for Networks and System
... • Some non-wireless destinations might not be prepared to perform crypto – What if wireless user wants protection anyway? • Doesn’t help wireless access point provide exclusive access – Any eavesdropper can use network CS 136, Fall 2013 ...
... • Some non-wireless destinations might not be prepared to perform crypto – What if wireless user wants protection anyway? • Doesn’t help wireless access point provide exclusive access – Any eavesdropper can use network CS 136, Fall 2013 ...
Chapter 7
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
Chapter 7 outline
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
Security in Computer Networks
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
A Traffic-aware Power Management Protocol for
... that the network lifetime can be prolonged. The novelty of the T-GSP compared with the previous work (i.e., GSP) is that it adjusts the variable (p) based on the ongoing traffic to improve the network performance. By introducing a sleep mode into the network, the total energy consumption of the netw ...
... that the network lifetime can be prolonged. The novelty of the T-GSP compared with the previous work (i.e., GSP) is that it adjusts the variable (p) based on the ongoing traffic to improve the network performance. By introducing a sleep mode into the network, the total energy consumption of the netw ...
Reading Report 3 Yin Chen 20 Feb 2004
... Number of results: the size of the total result set. Satisfaction of the query: Rather than returning every result, only notify the user of the first Z results, where Z is some value specified by the user. We say a query is satisfied if Z or more results are returned. Given a sufficiently large Z, t ...
... Number of results: the size of the total result set. Satisfaction of the query: Rather than returning every result, only notify the user of the first Z results, where Z is some value specified by the user. We say a query is satisfied if Z or more results are returned. Given a sufficiently large Z, t ...
Technical Guideline for the implementation of lawful measures for
... Event data (Intercept Related Information or IRI) The call data (known as Intercept Related Information or IRI in Europe and Call Data or CD in the US) consists of information about the targeted communications, like destination of a voice call (e.g., called party’s telephone number), source of a cal ...
... Event data (Intercept Related Information or IRI) The call data (known as Intercept Related Information or IRI in Europe and Call Data or CD in the US) consists of information about the targeted communications, like destination of a voice call (e.g., called party’s telephone number), source of a cal ...
RSM McGladrey - Infosight Solutions Corp
... originally planned. “A reliable and stable be putting in place.” WAN is critical to the design of all the technologies we would be putting in place. We clearly needed to accelerate this part of the project,” says Tim Calahan, Managing Director, RSM McGladrey. In addition to wireless backhaul, RSM Mc ...
... originally planned. “A reliable and stable be putting in place.” WAN is critical to the design of all the technologies we would be putting in place. We clearly needed to accelerate this part of the project,” says Tim Calahan, Managing Director, RSM McGladrey. In addition to wireless backhaul, RSM Mc ...
Lecture 1: Course Introduction and Overview
... – Huge distributed pool of resources extend devices – Traditional computers split into pieces. Wireless keyboards/mice, CPU distributed, storage remote ...
... – Huge distributed pool of resources extend devices – Traditional computers split into pieces. Wireless keyboards/mice, CPU distributed, storage remote ...
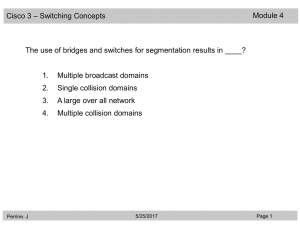
CCNPv5 Module 5 Lesson 1
... Port redirectors can help bypass port filters, routers, and firewalls and may even be encrypted over an SSL tunnel to evade intrusion detection devices. ...
... Port redirectors can help bypass port filters, routers, and firewalls and may even be encrypted over an SSL tunnel to evade intrusion detection devices. ...
Introduction - Communications
... (Note: multiple processes on a host can join. A report is sent only for the first process). • No report is sent when a process leaves a group – Changed in version 2 • A multicast router regularly multicasts an IGMP query to all hosts (group address is set to zero). • A host responds to an IGMP query ...
... (Note: multiple processes on a host can join. A report is sent only for the first process). • No report is sent when a process leaves a group – Changed in version 2 • A multicast router regularly multicasts an IGMP query to all hosts (group address is set to zero). • A host responds to an IGMP query ...
draft-li-idr-cc-bgp-arch-00
... This document introduces an architecture of using BGP for central control. Some use cases under this new framework are also discussed. For specific use cases, making necessary extensions in BGP are required. ...
... This document introduces an architecture of using BGP for central control. Some use cases under this new framework are also discussed. For specific use cases, making necessary extensions in BGP are required. ...
2 Installing the AsantéFAST 10/100 Adapter for NuBus
... the appropriate speed (10Mbps or 100Mbps) without user intervention. If you are initially planning to use the adapter to run at 10Mbps speed, when you are ready to upgrade to 100Mbps (100BASE-TX), it will not be necessary to modify any settings.The same driver can be used in both 10Mbps or 100Mbps s ...
... the appropriate speed (10Mbps or 100Mbps) without user intervention. If you are initially planning to use the adapter to run at 10Mbps speed, when you are ready to upgrade to 100Mbps (100BASE-TX), it will not be necessary to modify any settings.The same driver can be used in both 10Mbps or 100Mbps s ...
Study on Bandwidth Requirement for 88 Smart Schools
... During the pilot project, one of the main components tested is the provision of ICT infrastructure and system. Currently, all the 10,000 schools nationwide are enabled with Internet broadband access through SchoolNet. SchoolNet is an infrastructure project jointly conducted by the MoE and the Minist ...
... During the pilot project, one of the main components tested is the provision of ICT infrastructure and system. Currently, all the 10,000 schools nationwide are enabled with Internet broadband access through SchoolNet. SchoolNet is an infrastructure project jointly conducted by the MoE and the Minist ...
Symbiotic Relationships in Internet Routing Overlays Abstract University of Maryland
... inate among the connections that they allow and would have the ability to explicitly say how much service they want to contribute. Finally, mutual advantage avoids the tragedy of the commons in routing overlays, when only a few, well-connected nodes provide transit. It keeps the trades of connectivi ...
... inate among the connections that they allow and would have the ability to explicitly say how much service they want to contribute. Finally, mutual advantage avoids the tragedy of the commons in routing overlays, when only a few, well-connected nodes provide transit. It keeps the trades of connectivi ...
Chapter 1
... • Static Mapping: • One to one mapping of local and global addresses. • The hosts able to use NAT is limited by the static assignment in the table. ...
... • Static Mapping: • One to one mapping of local and global addresses. • The hosts able to use NAT is limited by the static assignment in the table. ...
Chapter 1 - BRAC University Courses
... • Static Mapping: • One to one mapping of local and global addresses. • The hosts able to use NAT is limited by the static assignment in the table. ...
... • Static Mapping: • One to one mapping of local and global addresses. • The hosts able to use NAT is limited by the static assignment in the table. ...
Document
... An IP datagram contains several fields. The most important are the source and destination addresses of the datagram (IP addresses). The header also contains fields related to fragmentation. The size of a datagram may be too large for some LAN or WAN protocols. In this case, the datagram is divided i ...
... An IP datagram contains several fields. The most important are the source and destination addresses of the datagram (IP addresses). The header also contains fields related to fragmentation. The size of a datagram may be too large for some LAN or WAN protocols. In this case, the datagram is divided i ...
Wireless Application Protocol
... Access) networks to transmit data at up to 384 kilobits per second (kbps). As it was initially developed for GSM systems only, it has also been called GSM384. 1.4.3 General Packet Radio Service (GPRS) -- A packet-linked technology that enables highspeed (up to 171.2 kilobit per second) wireless Inte ...
... Access) networks to transmit data at up to 384 kilobits per second (kbps). As it was initially developed for GSM systems only, it has also been called GSM384. 1.4.3 General Packet Radio Service (GPRS) -- A packet-linked technology that enables highspeed (up to 171.2 kilobit per second) wireless Inte ...
ppt - Worcester Polytechnic Institute
... • COPE Has Ordering Agent – For Each TCP Flow Ending @ Host • Maintains Packet Buffer • Records Last TCP Sequence Number • Will Not Pass On Packets to Transport Layer Until No Hole Exists or Timer Times Out Worcester Polytechnic Institute ...
... • COPE Has Ordering Agent – For Each TCP Flow Ending @ Host • Maintains Packet Buffer • Records Last TCP Sequence Number • Will Not Pass On Packets to Transport Layer Until No Hole Exists or Timer Times Out Worcester Polytechnic Institute ...
ODW_Ch6_PPT_without_Audio
... Communications and Network Technologies: Connecting Through Computers © Paradigm Publishing, Inc. ...
... Communications and Network Technologies: Connecting Through Computers © Paradigm Publishing, Inc. ...
Using SCTP to Improve QoS and Network Fault-
... Packet loss introduced at Traffic Shaping Node causes frames to be dropped 1% to 7% frames were dropped – higher loss for bigger frames ...
... Packet loss introduced at Traffic Shaping Node causes frames to be dropped 1% to 7% frames were dropped – higher loss for bigger frames ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.