Chapter 10: Circuit Switching and Packet Switching Switching
... • Modern digital systems rely on intelligent control of space and time division elements • Use digital time division techniques to set up and maintain virtual circuits • Partition low speed bit stream into pieces that share higher speed stream ...
... • Modern digital systems rely on intelligent control of space and time division elements • Use digital time division techniques to set up and maintain virtual circuits • Partition low speed bit stream into pieces that share higher speed stream ...
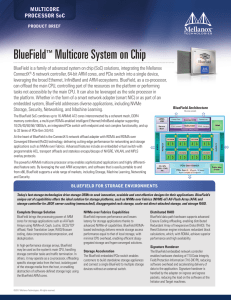
BlueField™ Multicore System on Chip
... The BlueField SoC combines up to 16 ARMv8 A72 cores interconnected by a coherent mesh, DDR4 memory controllers, a multi-port RDMA-enabled intelligent Ethernet/InfiniBand adapter supporting 10/25/40/50/56/100Gb/s, an integrated PCIe switch with endpoint and root complex functionality, and up to 32 la ...
... The BlueField SoC combines up to 16 ARMv8 A72 cores interconnected by a coherent mesh, DDR4 memory controllers, a multi-port RDMA-enabled intelligent Ethernet/InfiniBand adapter supporting 10/25/40/50/56/100Gb/s, an integrated PCIe switch with endpoint and root complex functionality, and up to 32 la ...
in the web page - University of Greenwich
... • Responsible for communicating packets from source to destination • across multiple network hops ...
... • Responsible for communicating packets from source to destination • across multiple network hops ...
snmpintro
... layer 2 stats collected over short time snapshots layer 3 stats the same host 1 by host 2 traffic flow information thresholds - event on too much/too little X ...
... layer 2 stats collected over short time snapshots layer 3 stats the same host 1 by host 2 traffic flow information thresholds - event on too much/too little X ...
Test_King_CompTIA_N1..
... PPTP (Point-to-point Tunneling Protocol) SNMP (Simple Network Management Protocol) TCP/IP (Transmission Control Protocol and Internet Protocol) ...
... PPTP (Point-to-point Tunneling Protocol) SNMP (Simple Network Management Protocol) TCP/IP (Transmission Control Protocol and Internet Protocol) ...
Chapter 7 outline
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
Dell presentation template Standard 4:3 layout
... cash flow for Dell SonicWALL support contracts and subscription services with incoming cash flow from clients. SonicWALL ...
... cash flow for Dell SonicWALL support contracts and subscription services with incoming cash flow from clients. SonicWALL ...
Adopting Ideas from Interplanetary Networking for Sensor
... • Transmission priority affects performance – Want to avoid starvation ...
... • Transmission priority affects performance – Want to avoid starvation ...
Data Center Interconnection with VXLAN
... Most network designers would prefer that data center interconnection over wide area networks (WAN) be performed at layer 3, without layer-2 connectivity spanning data centers. However, application requirements often make it necessary to provide layer-2 interconnection between data centers, with comm ...
... Most network designers would prefer that data center interconnection over wide area networks (WAN) be performed at layer 3, without layer-2 connectivity spanning data centers. However, application requirements often make it necessary to provide layer-2 interconnection between data centers, with comm ...
Network ID
... • Network administrators sometimes need to divide networks, especially large ones, into smaller networks: – Reduce the size of a broadcast domain. – Improve network security. – Implement the hierarchical managements. ...
... • Network administrators sometimes need to divide networks, especially large ones, into smaller networks: – Reduce the size of a broadcast domain. – Improve network security. – Implement the hierarchical managements. ...
Priority-based Time Slot Assignment Algorithm for
... issue in WDMTDM switched optical mesh networks without wavelength conversion capability and proposed an adaptive grooming algorithm to solve the problem. The goal was to efficiently route connection requests with fractional wavelength capacity requirements onto high- capacity wavelengths and to bala ...
... issue in WDMTDM switched optical mesh networks without wavelength conversion capability and proposed an adaptive grooming algorithm to solve the problem. The goal was to efficiently route connection requests with fractional wavelength capacity requirements onto high- capacity wavelengths and to bala ...
ODVA Conformance SIG Test Procedure For Physical Layer, Media
... Figure 5-2 Dominant Bit levels....................................................................................................................... 13 Figure 5-3 Differential Level ..................................................................................................................... ...
... Figure 5-2 Dominant Bit levels....................................................................................................................... 13 Figure 5-3 Differential Level ..................................................................................................................... ...
HPE 5900 Switch Series
... • Access control lists (ACLs) provide IP Layer 3 filtering based on source/destination IP address/subnet and source/ destination TCP/UDP port number • RADIUS/TACACS+ eases switch management security administration by using a password authentication server • Secure Shell encrypts all transmitted data ...
... • Access control lists (ACLs) provide IP Layer 3 filtering based on source/destination IP address/subnet and source/ destination TCP/UDP port number • RADIUS/TACACS+ eases switch management security administration by using a password authentication server • Secure Shell encrypts all transmitted data ...
Network Devices
... • Formally, a switch is just a bridge • Switch looks at ethernet headers (layer 2) – ethernet to ethernet only ...
... • Formally, a switch is just a bridge • Switch looks at ethernet headers (layer 2) – ethernet to ethernet only ...
Document
... To store intermediate sensor readings, packets from other nodes, and so on. Memory To store program code Communication ...
... To store intermediate sensor readings, packets from other nodes, and so on. Memory To store program code Communication ...
Paul Francis, Ramesh Govindan, Flexible Routing and Addressing for a Next Generation IP, SIGCOMM 94, September 1994, London
... IP address space is too small to indefinitely growth ...
... IP address space is too small to indefinitely growth ...
Chapter 7
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
ITN_instructorPPT_Chapter1_final
... occur. It is made up of network components including end devices, intermediate devices, and network media. ...
... occur. It is made up of network components including end devices, intermediate devices, and network media. ...
Introduction CS 239 Security for Networks and System Software
... • Some non-wireless destinations might not be prepared to perform crypto – What if wireless user wants protection anyway? • Doesn’t help wireless access point provide exclusive access – Any eavesdropper can use network CS 136, Fall 2014 ...
... • Some non-wireless destinations might not be prepared to perform crypto – What if wireless user wants protection anyway? • Doesn’t help wireless access point provide exclusive access – Any eavesdropper can use network CS 136, Fall 2014 ...
Chp7
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
Chapter 7 outline
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
Security in Computer Networks
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
... Q: How does receiver determine whether packet is first in a talkspurt? if no loss, receiver looks at successive timestamps. ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.