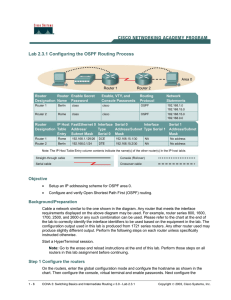
Lab 2.3.1 Configuring the OSPF Routing Process Objective
... In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations for each router class. What is provided are the identifiers for the po ...
... In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations for each router class. What is provided are the identifiers for the po ...
Overview of Internet2 - CITI
... SDN Control Server Performance Node Nx100G Dedicated science switches/servers in labs with high-‐speed storage and network access ...
... SDN Control Server Performance Node Nx100G Dedicated science switches/servers in labs with high-‐speed storage and network access ...
WISPCON-Keeping It Up 2 - Home
... So what do we have? Redundancy at the WPOP (3 separate radios & antennas) ...
... So what do we have? Redundancy at the WPOP (3 separate radios & antennas) ...
Distributed Processing System
... The NGS Program developsTechnology for integrated feedback & control Runtime Compiling System (RCS) and Dynamic Application Composition ...
... The NGS Program developsTechnology for integrated feedback & control Runtime Compiling System (RCS) and Dynamic Application Composition ...
Tricha Anjali of - BWN-Lab
... LSP and lSP Setup Problem - “Optimal Policy for LSP Setup in MPLS Networks,” Computer Networks Journal, June 2002 - “LSP and lSP Setup in GMPLS Networks,” Proceedings of IEEE INFOCOM, March 2004 ...
... LSP and lSP Setup Problem - “Optimal Policy for LSP Setup in MPLS Networks,” Computer Networks Journal, June 2002 - “LSP and lSP Setup in GMPLS Networks,” Proceedings of IEEE INFOCOM, March 2004 ...
end of section
... The Hardware Virtual Private Network (VPN) units shall be KBC Networks models THLK-S2-WB (ThruLink, Standard Capacity, Standalone operation) THLK-S3-WB (ThruLink Standard Capacity, Standalone operation) and THLK-H2-RB (ThruLink, High Capacity, Rack Mount operation). The units shall be either standal ...
... The Hardware Virtual Private Network (VPN) units shall be KBC Networks models THLK-S2-WB (ThruLink, Standard Capacity, Standalone operation) THLK-S3-WB (ThruLink Standard Capacity, Standalone operation) and THLK-H2-RB (ThruLink, High Capacity, Rack Mount operation). The units shall be either standal ...
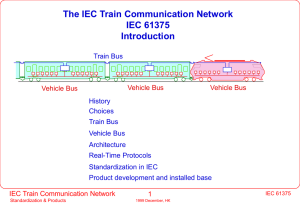
TCN Introduction
... WG22 specified the Multifunction Vehicle Bus as the standard interface to provide plug-compatibility between equipment on board the same vehicle. ...
... WG22 specified the Multifunction Vehicle Bus as the standard interface to provide plug-compatibility between equipment on board the same vehicle. ...
View
... • Other constraints we need to take into account – destination-based routing: not pair-based!
– multiple shortest paths (“equal-cost” paths, ECPs) may
exist and can be used for load-balancing
• But typical equal splitting is used to split traffic among ECPs
for a given destination prefix
...
... • Other constraints we need to take into account – destination-based routing: not
Robustness of the spatial insurance effects of biodiversity to habitat
... compared three patch removal sequences: removing the patch with the lowest betweenness centrality, removing a random patch, and removing the patch with the highest betweenness centrality (Fig. 1). The betweenness centrality of a patch is computed as the proportion of shortest paths between all pairs ...
... compared three patch removal sequences: removing the patch with the lowest betweenness centrality, removing a random patch, and removing the patch with the highest betweenness centrality (Fig. 1). The betweenness centrality of a patch is computed as the proportion of shortest paths between all pairs ...
Introduction to Dynamic Routing Protocol
... With the advent of numerous consumer devices using IP, the IPv4 addressing space is nearly exhausted. Thus IPv6 has emerged. To support the communication based on IPv6, newer versions of the IP routing protocols have been developed (see the IPv6 row in the table). ...
... With the advent of numerous consumer devices using IP, the IPv4 addressing space is nearly exhausted. Thus IPv6 has emerged. To support the communication based on IPv6, newer versions of the IP routing protocols have been developed (see the IPv6 row in the table). ...
TCP, IGP, EGP etc. - La Salle University
... packet is constantly transferred until it reaches its final destination because the routers can not support more than one packet at a time. ...
... packet is constantly transferred until it reaches its final destination because the routers can not support more than one packet at a time. ...
Tackling Security Vulnerabilities in VPN-based Wireless
... experience with telecommuter access to corporate networks over IPSec, and adding wireless access is viewed as only an additional profile for an end-user. Most laptops also have IPSec clients already installed to enable telecommuter access. IPSec secures only IP traffic, but given the access pattern ...
... experience with telecommuter access to corporate networks over IPSec, and adding wireless access is viewed as only an additional profile for an end-user. Most laptops also have IPSec clients already installed to enable telecommuter access. IPSec secures only IP traffic, but given the access pattern ...
THE TCP/IP PROTOCOL SUITE
... intermediate nodes usually only involve the first three layers of TCP/IP (although many of them still have all five layers for other reasons, as we have seen). In TCP/IP, as with most layered protocols, the most fundamental elements of the process of sending and receiving data are collected into the g ...
... intermediate nodes usually only involve the first three layers of TCP/IP (although many of them still have all five layers for other reasons, as we have seen). In TCP/IP, as with most layered protocols, the most fundamental elements of the process of sending and receiving data are collected into the g ...
Cloud-RAN Deployment with CPRI Fronthaul Technology
... The positioning of RE (RRH or RRU) close to an antenna significantly reduces the length of coax cables for the interconnection of RRH and antennas, thereby improving the link budget and user throughput. With CPRI, the link between BBU and RRU can be extended to several miles. This opens new applicat ...
... The positioning of RE (RRH or RRU) close to an antenna significantly reduces the length of coax cables for the interconnection of RRH and antennas, thereby improving the link budget and user throughput. With CPRI, the link between BBU and RRU can be extended to several miles. This opens new applicat ...
Contents - Andrew Noske
... While routers can be used to segment LAN devices, their major use is as WAN devices. Routers have both LAN & WAN interfaces. In fact, WAN technologies are frequently used to connect routers. They communicate with each other by WAN connections, & make up autonomous systems & the backbone of the Inter ...
... While routers can be used to segment LAN devices, their major use is as WAN devices. Routers have both LAN & WAN interfaces. In fact, WAN technologies are frequently used to connect routers. They communicate with each other by WAN connections, & make up autonomous systems & the backbone of the Inter ...
ppt
... • How do we add new features to the network? • Does every router need to support new feature? • Choices • Reprogram all routers active networks • Support new feature within an overlay ...
... • How do we add new features to the network? • Does every router need to support new feature? • Choices • Reprogram all routers active networks • Support new feature within an overlay ...
SW24 User Manual
... This chapter describes the Switch and some background information about Ethernet / Fast: The Switch was designed for easy installation and high performance in an environment where traffic on the network and the number of user increase continuously. The Switch with its small, compact size was specifi ...
... This chapter describes the Switch and some background information about Ethernet / Fast: The Switch was designed for easy installation and high performance in an environment where traffic on the network and the number of user increase continuously. The Switch with its small, compact size was specifi ...
DSL-2640U - D-Link
... Also you can find a specific page via search. To do this, enter the name of the page, wholly or partly, in the search bar in the top part of the web-based interface page, and then select a needed link in the search results. ...
... Also you can find a specific page via search. To do this, enter the name of the page, wholly or partly, in the search bar in the top part of the web-based interface page, and then select a needed link in the search results. ...
Overbot - A botnet protocol based on Kademlia
... that the node is downloading the file. Other peers can use the get_peers RPC to retrieve a set of nodes that are currently downloading a specific file. get_peers is comparable to the FIND_VALUE function in eMule. Unlike eMule, the DHT implementation of Bittorrent restricts the information stored in the ...
... that the node is downloading the file. Other peers can use the get_peers RPC to retrieve a set of nodes that are currently downloading a specific file. get_peers is comparable to the FIND_VALUE function in eMule. Unlike eMule, the DHT implementation of Bittorrent restricts the information stored in the ...
The Internet Motion Sensor: A Distributed Blackhole
... While responses across most or all ports provides insights into potentially unknown threats, we would be remiss if we did not point out that this makes these sensors simple to identify and fingerprint. One main advantage of this system is its focus on globally scoped threats over the activites for i ...
... While responses across most or all ports provides insights into potentially unknown threats, we would be remiss if we did not point out that this makes these sensors simple to identify and fingerprint. One main advantage of this system is its focus on globally scoped threats over the activites for i ...
jxta15
... requires a platform that supports the JRE or JDK 1.3.1 or later. Available on Windows, Solaris, Linux, and ...
... requires a platform that supports the JRE or JDK 1.3.1 or later. Available on Windows, Solaris, Linux, and ...