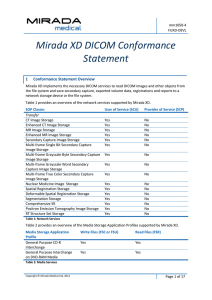
XD 3.6 DICOM Conformance Statement
... techniques, available for use by DICOM applications. Media Application Profile – the specification of DICOM information objects and encoding exchanged on removable media (e.g., CDs) Module – a set of Attributes within an Information Object Definition that are logically related to each other. Example ...
... techniques, available for use by DICOM applications. Media Application Profile – the specification of DICOM information objects and encoding exchanged on removable media (e.g., CDs) Module – a set of Attributes within an Information Object Definition that are logically related to each other. Example ...
jxta15
... requires a platform that supports the JRE or JDK 1.3.1 or later. Available on Windows, Solaris, Linux, and ...
... requires a platform that supports the JRE or JDK 1.3.1 or later. Available on Windows, Solaris, Linux, and ...
The Internet Motion Sensor: A Distributed Blackhole
... While responses across most or all ports provides insights into potentially unknown threats, we would be remiss if we did not point out that this makes these sensors simple to identify and fingerprint. One main advantage of this system is its focus on globally scoped threats over the activites for i ...
... While responses across most or all ports provides insights into potentially unknown threats, we would be remiss if we did not point out that this makes these sensors simple to identify and fingerprint. One main advantage of this system is its focus on globally scoped threats over the activites for i ...
BGP
... AS’s : A set of routers that operate under the same administration and share a common routing strategy. Bgp can be used for routing packets both within and between AS’s Routers that belong to different AS’s and exchange BGP updates are running External BGP.These routers are usually adjacent to each ...
... AS’s : A set of routers that operate under the same administration and share a common routing strategy. Bgp can be used for routing packets both within and between AS’s Routers that belong to different AS’s and exchange BGP updates are running External BGP.These routers are usually adjacent to each ...
Boswarthick_for_IIR_Dubai - Docbox
... TISPAN is progressing the work on Rel-2 concerning the following main new work items: Requirements analysis for FMC (with such bodies as FMCA). Requirements analysis for home networking (in cooperation with such bodies as HGI). Requirements for network capabilities to support IPTV services ( ...
... TISPAN is progressing the work on Rel-2 concerning the following main new work items: Requirements analysis for FMC (with such bodies as FMCA). Requirements analysis for home networking (in cooperation with such bodies as HGI). Requirements for network capabilities to support IPTV services ( ...
Success Probability of Multiple-Preamble Based Single
... D. Trade-off between collision probability and code ambiguity Although Multi-preamble RA can significantly reduce collision probability, this has a trade-off with its code ambiguity. In case of a codeword length of n = 1 (as in LTE) there is no code-ambiguity, and resource utilisation is 1; however, ...
... D. Trade-off between collision probability and code ambiguity Although Multi-preamble RA can significantly reduce collision probability, this has a trade-off with its code ambiguity. In case of a codeword length of n = 1 (as in LTE) there is no code-ambiguity, and resource utilisation is 1; however, ...
Pi: A Practical Incentive Protocol for Delay Tolerant
... [13,14]. For example, in order to conserve power, buffer and computing resources, a selfish DTN node may be reluctant in the cooperation that is not directly beneficial to it, which could make a well designed opportunistic routing useless. Therefore, how to efficiently and effectively resolve the se ...
... [13,14]. For example, in order to conserve power, buffer and computing resources, a selfish DTN node may be reluctant in the cooperation that is not directly beneficial to it, which could make a well designed opportunistic routing useless. Therefore, how to efficiently and effectively resolve the se ...
Case Studies on IP-based Interconnection for Voice Services
... Table 44: Physical IC link and redundancy of the IPvIC – part 1 ...........................................69 Table 45: Physical IC link and redundancy of the IPvIC – part 2 ...........................................70 Table 46: Physical IC link and redundancy of the IPvIC – part 3 ................ ...
... Table 44: Physical IC link and redundancy of the IPvIC – part 1 ...........................................69 Table 45: Physical IC link and redundancy of the IPvIC – part 2 ...........................................70 Table 46: Physical IC link and redundancy of the IPvIC – part 3 ................ ...
Vertical handover criteria and algorithm in IEEE 802.11 and 802.16
... analyzing connection performance and taking handover decisions. The measurement of these parameters is required to satisfy the following properties: i) it should be periodical, in order to continuously monitor the access network condition; ii) it can take place without sending and receiving any data ...
... analyzing connection performance and taking handover decisions. The measurement of these parameters is required to satisfy the following properties: i) it should be periodical, in order to continuously monitor the access network condition; ii) it can take place without sending and receiving any data ...
CRLF - Computer and Internet Architecture Laboratory
... – No error handling (Let TCP catch errors!) – No sequence numbers, so no way to put arriving IP packets in order (Let TCP put the TCP segments these IP packets contain in ...
... – No error handling (Let TCP catch errors!) – No sequence numbers, so no way to put arriving IP packets in order (Let TCP put the TCP segments these IP packets contain in ...
Powerpoint - Purdue University
... Packet, e.g., scheduling, packet discard Performance concerns become on-line High speed = propagation delay much higher than packet transmission time Number of packets in the “pipe” is high Open loop Router-based Reservation Backpressure Sonia Fahmy ...
... Packet, e.g., scheduling, packet discard Performance concerns become on-line High speed = propagation delay much higher than packet transmission time Number of packets in the “pipe” is high Open loop Router-based Reservation Backpressure Sonia Fahmy ...
Border Gateway Protocol (BGP4)
... • BGP Peering sessions are established using the BGP “neighbor” configuration command – External (eBGP) is configured when AS numbers are different – Internal (iBGP) is configured when AS numbers are same ...
... • BGP Peering sessions are established using the BGP “neighbor” configuration command – External (eBGP) is configured when AS numbers are different – Internal (iBGP) is configured when AS numbers are same ...
QoS Requirement of Network Applicationson the Internet.pdf
... of 150 milliseconds. In this paper, we consider the case in which audio and video data are in the same packets. Human Perception of Jitter Jitter is an essential performance parameter of a network intended to support real time sound and image media. Of all information types, real time sound is the m ...
... of 150 milliseconds. In this paper, we consider the case in which audio and video data are in the same packets. Human Perception of Jitter Jitter is an essential performance parameter of a network intended to support real time sound and image media. Of all information types, real time sound is the m ...
Title goes here
... Ingress router upon entry into an MPLS domain Subsequent packets are forwarded strictly according to their labels label is removed by egress LSR Each LSR maintains label to NHLFE mapping giving a set of entries for each FEC. Mapping can be changed for • load balancing over multiple paths • rerouting ...
... Ingress router upon entry into an MPLS domain Subsequent packets are forwarded strictly according to their labels label is removed by egress LSR Each LSR maintains label to NHLFE mapping giving a set of entries for each FEC. Mapping can be changed for • load balancing over multiple paths • rerouting ...
SDN, NFV, OpenFlow, and ForCES - IETF-93 tutorial
... Even adding new instances of well-known services is a time consuming process for conventional networks When a new service types requires new protocols, the timeline is • protocol standardization (often in more than one SDO) • hardware development • interop testing • vendor marketing campaigns and op ...
... Even adding new instances of well-known services is a time consuming process for conventional networks When a new service types requires new protocols, the timeline is • protocol standardization (often in more than one SDO) • hardware development • interop testing • vendor marketing campaigns and op ...
Distributed Firewall
... misbehavior by insiders, there is a tension between internal needs for more connectivity and the difficulty of satisfying such needs with a centralized firewall. IPsec is a protocol suite, recently standardized by the IETF, which provides network-layer security services such as packet confidentialit ...
... misbehavior by insiders, there is a tension between internal needs for more connectivity and the difficulty of satisfying such needs with a centralized firewall. IPsec is a protocol suite, recently standardized by the IETF, which provides network-layer security services such as packet confidentialit ...
S7C9 - Multicasts
... number of members • Supports membership of single host in one or more groups • Upholds multiple data streams at application level for single group address • Supports single group address for multiple applications on host ...
... number of members • Supports membership of single host in one or more groups • Upholds multiple data streams at application level for single group address • Supports single group address for multiple applications on host ...
Chapter 7 - SaigonTech
... • Errors can occur when data is altered in medium – Usually caused by noise or faulty media connections – When the destination computer receives a frame, the CRC is recalculated and compared against the CRC value in the FCS – If values match, the data is assumed to be okay – If values don’t match, t ...
... • Errors can occur when data is altered in medium – Usually caused by noise or faulty media connections – When the destination computer receives a frame, the CRC is recalculated and compared against the CRC value in the FCS – If values match, the data is assumed to be okay – If values don’t match, t ...
IPv6 – the new generation internet
... intervention, seek out a stateless autoconfiguration server and be configured to interoperate. These features make for true plug-and-play network access. Through neighbor discovery, nodes can automatically determine which routers on their links are available and can be reached. Moreover, the assignm ...
... intervention, seek out a stateless autoconfiguration server and be configured to interoperate. These features make for true plug-and-play network access. Through neighbor discovery, nodes can automatically determine which routers on their links are available and can be reached. Moreover, the assignm ...
Examples
... Construction phase 1. Each node tests whether to become CH or not 2. If node becomes CH then it sends cluster advertisement and waits for response 3. If node decides not to be CH then listens for CH advertisements 1. If advertisements from several clusters, choose cluster with lowest CH distance (ho ...
... Construction phase 1. Each node tests whether to become CH or not 2. If node becomes CH then it sends cluster advertisement and waits for response 3. If node decides not to be CH then listens for CH advertisements 1. If advertisements from several clusters, choose cluster with lowest CH distance (ho ...
Development of Network Interface Card (NIC) RT
... Linux is playing a significant role in the embedded applications, and Device drivers take a major responsibility in developing the Linux kernel. This thesis is aimed at the design and implementation of a device driver for Network Interface Card (NIC) RT-8139C to transfer data from PC to the physical ...
... Linux is playing a significant role in the embedded applications, and Device drivers take a major responsibility in developing the Linux kernel. This thesis is aimed at the design and implementation of a device driver for Network Interface Card (NIC) RT-8139C to transfer data from PC to the physical ...
Ch 10-Link State Routing Protocols
... -Cost associated with link -Neighboring routers on the link ...
... -Cost associated with link -Neighboring routers on the link ...