Packet Tracer Network Simulator
... of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the author, nor Packt Publishing and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by th ...
... of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the author, nor Packt Publishing and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by th ...
Chapter 5
... to clients (SOHO network) Configuring the DHCP server – Enter router default IP address and subnet mask for internal interface • IP = 192.168.1.1 • Subnet Mask = 255.255.255.0 –On DHCP screen • check range • number of users • lease time (24 hours by default) ...
... to clients (SOHO network) Configuring the DHCP server – Enter router default IP address and subnet mask for internal interface • IP = 192.168.1.1 • Subnet Mask = 255.255.255.0 –On DHCP screen • check range • number of users • lease time (24 hours by default) ...
Before You Begin: Assign Information Classification
... Bridges and Switches A packet, along with its MAC address information, is called a frame. LANs are often divided into sections called segments bounded by bridges. A bridge has the intelligence to determine if an incoming frame is to be sent to a different segment, or dropped. A bridge has two ...
... Bridges and Switches A packet, along with its MAC address information, is called a frame. LANs are often divided into sections called segments bounded by bridges. A bridge has the intelligence to determine if an incoming frame is to be sent to a different segment, or dropped. A bridge has two ...
ii. 1-wire interface
... The 1-wire technology has emerged from the evolution of the semiconductor technology. It was designated to some specific applications to substitute the identification by paper label based on bar codes for the electronic circuits. Dallas Semiconductor was the first producer which developed a large us ...
... The 1-wire technology has emerged from the evolution of the semiconductor technology. It was designated to some specific applications to substitute the identification by paper label based on bar codes for the electronic circuits. Dallas Semiconductor was the first producer which developed a large us ...
Network Addressing
... to clients (SOHO network) Configuring the DHCP server – Enter router default IP address and subnet mask for internal interface • IP = 192.168.1.1 • Subnet Mask = 255.255.255.0 –On DHCP screen • check range • number of users • lease time (24 hours by default) ...
... to clients (SOHO network) Configuring the DHCP server – Enter router default IP address and subnet mask for internal interface • IP = 192.168.1.1 • Subnet Mask = 255.255.255.0 –On DHCP screen • check range • number of users • lease time (24 hours by default) ...
Link Analysis
... § Let Ii be the set of actors that can reach actor i § The proximity is defined in terms of closeness or distance of the other actors in Ii to i § Let d(j, i) denote the distance (shortest path) from actor j to actor i – This measure is directly proportional to the distance of all the actors ...
... § Let Ii be the set of actors that can reach actor i § The proximity is defined in terms of closeness or distance of the other actors in Ii to i § Let d(j, i) denote the distance (shortest path) from actor j to actor i – This measure is directly proportional to the distance of all the actors ...
Network Addressing - Mt. Hood Community College
... to clients (SOHO network) Configuring the DHCP server – Enter router default IP address and subnet mask for internal interface • IP = 192.168.1.1 • Subnet Mask = 255.255.255.0 –On DHCP screen • check range • number of users • lease time (24 hours by default) ...
... to clients (SOHO network) Configuring the DHCP server – Enter router default IP address and subnet mask for internal interface • IP = 192.168.1.1 • Subnet Mask = 255.255.255.0 –On DHCP screen • check range • number of users • lease time (24 hours by default) ...
A deterministic worst-case message complexity optimal solution for
... To perform cooperative tasks in distributed systems the network nodes have to know which other nodes are participating. Examples for such cooperative tasks range from fundamental problems such as group-based cryptography [19], verifiable secret sharing [7], distributed consensus [22], and broadcastin ...
... To perform cooperative tasks in distributed systems the network nodes have to know which other nodes are participating. Examples for such cooperative tasks range from fundamental problems such as group-based cryptography [19], verifiable secret sharing [7], distributed consensus [22], and broadcastin ...
Note
... To find the type of the address, we need to look at the second hexadecimal digit from the left. If it is even, the address is unicast. If it is odd, the address is multicast. If all digits are F’s, the address is broadcast. Therefore, we have the following: a. This is a unicast address because A in ...
... To find the type of the address, we need to look at the second hexadecimal digit from the left. If it is even, the address is unicast. If it is odd, the address is multicast. If all digits are F’s, the address is broadcast. Therefore, we have the following: a. This is a unicast address because A in ...
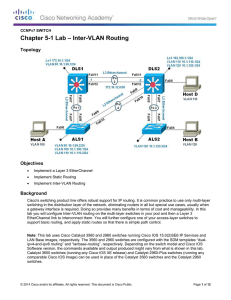
Lab 5-1 Inter-VLAN Routing
... CCNPv7 SWITCH: Lab 5-1 – Inter-VLAN Routing Enter configuration commands, one per line. End with CNTL/Z. ALS1(config)# sdm pref lanbase-routing Changes to the running SDM preferences have been stored, but cannot take effect until the next reload. Use 'show sdm prefer' to see what SDM preference is ...
... CCNPv7 SWITCH: Lab 5-1 – Inter-VLAN Routing Enter configuration commands, one per line. End with CNTL/Z. ALS1(config)# sdm pref lanbase-routing Changes to the running SDM preferences have been stored, but cannot take effect until the next reload. Use 'show sdm prefer' to see what SDM preference is ...
ex4-3-o-can
... • Frame Relay has become the most widely used WAN technology in the world. • Large enterprises, ISPs, and small businesses use Frame Relay, because of its price and flexibility. • Price: • As corporations grow, so does their dependence on timely, reliable data transport. • Leased line facilities bec ...
... • Frame Relay has become the most widely used WAN technology in the world. • Large enterprises, ISPs, and small businesses use Frame Relay, because of its price and flexibility. • Price: • As corporations grow, so does their dependence on timely, reliable data transport. • Leased line facilities bec ...
Adaptive Event Dissemination for Peer-to
... high. Hence, it is necessary to avoid as much as possible redundant transmissions to not congestion the network. The considerations above motivate the need to devise novel, adaptive decentralized algorithms for game events distribution in dynamic P2P systems. In this paper, we propose an adaptive g ...
... high. Hence, it is necessary to avoid as much as possible redundant transmissions to not congestion the network. The considerations above motivate the need to devise novel, adaptive decentralized algorithms for game events distribution in dynamic P2P systems. In this paper, we propose an adaptive g ...
- Transactions on Environment and Electrical Engineering
... The purpose is to calculate the parameters of reliability and losses resulted from the interruptions. Application of Monte Carlo method gives an opportunity to obtained more accurate results using distribution of probabilities and reducing the number of assumptions. For an average electric supply mo ...
... The purpose is to calculate the parameters of reliability and losses resulted from the interruptions. Application of Monte Carlo method gives an opportunity to obtained more accurate results using distribution of probabilities and reducing the number of assumptions. For an average electric supply mo ...
TamVu_TCP_lec_DR13 - Winlab
... Deliver messages in the same order they are sent Messages may be reordered in networks and incurs a long delay. Delivers at most one copy of each message Messages may duplicate in networks. Support arbitrarily large message Network may limit message size. Support synchronization betwee ...
... Deliver messages in the same order they are sent Messages may be reordered in networks and incurs a long delay. Delivers at most one copy of each message Messages may duplicate in networks. Support arbitrarily large message Network may limit message size. Support synchronization betwee ...
Topological Detection on Wormholes in Wireless Ad Hoc and
... mechanisms employed in the network. The attacker can forward each bit of a communication stream over the wormhole directly without breaking into the content of packets. Thus, the attacker does not need to compromise any node and obtain valid network identities to become part of the network. Using th ...
... mechanisms employed in the network. The attacker can forward each bit of a communication stream over the wormhole directly without breaking into the content of packets. Thus, the attacker does not need to compromise any node and obtain valid network identities to become part of the network. Using th ...
Bitcoin Mining Pools: A Cooperative Game Theoretic - CS
... among the pool members. When a pool member finds a successful input (i.e., an input x where h(b(x)) < t) the block is mined and the rewards are distributed among the pool members. As pool participants may be unequal in their computational resources, the rewards are split among them in proportion to ...
... among the pool members. When a pool member finds a successful input (i.e., an input x where h(b(x)) < t) the block is mined and the rewards are distributed among the pool members. As pool participants may be unequal in their computational resources, the rewards are split among them in proportion to ...
Chapter5_24_Nov_2010_v2
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
Adaptive Fairness through intra-ONU Scheduling for Ethernet
... be serviced with differentiated services. These services are classified as follows: Best Effort (BE) ”data” traffic, Assured Forwarding (AF) traffic such as variable-bit-rate (VBR) video stream and Expedited Forwarding (EF) traffic used to emulate point-to-point (P2P) connections or real time servic ...
... be serviced with differentiated services. These services are classified as follows: Best Effort (BE) ”data” traffic, Assured Forwarding (AF) traffic such as variable-bit-rate (VBR) video stream and Expedited Forwarding (EF) traffic used to emulate point-to-point (P2P) connections or real time servic ...
Tor, Attacks Against, and NSA`s Toolbox
... Onion Routing is a technique that allows anonymous communications over a network of computers. In onion routing, messages are routed through a circuit (a path of Tor relays, Figure 1) after encrypted multiple times, like layers of an onion (Figure 2), with the encryption keys of the relays in the ci ...
... Onion Routing is a technique that allows anonymous communications over a network of computers. In onion routing, messages are routed through a circuit (a path of Tor relays, Figure 1) after encrypted multiple times, like layers of an onion (Figure 2), with the encryption keys of the relays in the ci ...
Chapter_7_V6.0_HU
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...