Peer to Peer File Sharing: A Survey
... uses Pastry as its routing scheme Offers persistent storage services for replicated read-only files Owners can insert or reclaim files, but clients can just look up Collection of PAST nodes form an overlay network. A PAST node is at least an access point, but it can also contribute to storage and pa ...
... uses Pastry as its routing scheme Offers persistent storage services for replicated read-only files Owners can insert or reclaim files, but clients can just look up Collection of PAST nodes form an overlay network. A PAST node is at least an access point, but it can also contribute to storage and pa ...
Transport Issues in Ad Hoc and Sensor Networks
... Intended to provide a more reliable method of communication that is not offered by the network layer. Transport layer protocols were initially intended to offer services regardless of the underlying network. Receives data from the user and transmits it to the receiver in order and without erro ...
... Intended to provide a more reliable method of communication that is not offered by the network layer. Transport layer protocols were initially intended to offer services regardless of the underlying network. Receives data from the user and transmits it to the receiver in order and without erro ...
Evaluation of Network Topology Inference in Opaque
... for topology inference [12], [22]. The idea is that a source node sends probing packets to at least two receiver nodes. The receivers measure their individual packet loss rate. From correlations in the loss rates it is then possible to deduce common subpaths between the source and the receivers. Ide ...
... for topology inference [12], [22]. The idea is that a source node sends probing packets to at least two receiver nodes. The receivers measure their individual packet loss rate. From correlations in the loss rates it is then possible to deduce common subpaths between the source and the receivers. Ide ...
IOSR Journal of Computer Science (IOSR-JCE) e-ISSN: 2278-0661, p-ISSN: 2278-8727 PP 58-65 www.iosrjournals.org
... protocol. In DREAM, each node maintains a position database that stores position information about all other nodes within the network. Of course, this approach is not scalable and requires a large number of beacon updates. The position updates could be adapted to the node mobility. However, no detai ...
... protocol. In DREAM, each node maintains a position database that stores position information about all other nodes within the network. Of course, this approach is not scalable and requires a large number of beacon updates. The position updates could be adapted to the node mobility. However, no detai ...
HotStreaming: Enabling Scalable and Quality IPTV Services
... the users is the same to all real-time multimedia applications, including IPTV. Our objective in this work is to develop a scalable networking and video coding platform for quality video broadcasting over the Internet. HotStreaming, the proposed IPTV system, takes 1) the overlay peer-to-peer (overla ...
... the users is the same to all real-time multimedia applications, including IPTV. Our objective in this work is to develop a scalable networking and video coding platform for quality video broadcasting over the Internet. HotStreaming, the proposed IPTV system, takes 1) the overlay peer-to-peer (overla ...
to get the FORTA 155 brochure
... transmission technology works by multiplexing E1/T1 signals onto a single mode optical high-speed network; this will provide a wide range of telephone, data and video services. FORTA 155’s modular design conveniently allows network planning divisions to invest at their own paces. FORTA 155’s Etherne ...
... transmission technology works by multiplexing E1/T1 signals onto a single mode optical high-speed network; this will provide a wide range of telephone, data and video services. FORTA 155’s modular design conveniently allows network planning divisions to invest at their own paces. FORTA 155’s Etherne ...
pptx - UCL Computer Science
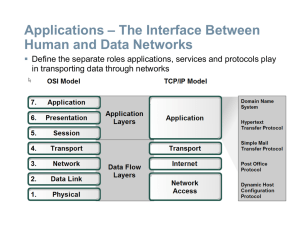
... • IP multicast: Many hosts receive all traffic to a number of hosts (a multicast group) [Slide credit: CMU Network Group] ...
... • IP multicast: Many hosts receive all traffic to a number of hosts (a multicast group) [Slide credit: CMU Network Group] ...
Security Attacks
... Network Layer Two important functions: • routing: determine path from source to dest. • forwarding: move packets from router’s input to output ...
... Network Layer Two important functions: • routing: determine path from source to dest. • forwarding: move packets from router’s input to output ...
Chapter
... • IP address identifies network and host • Classes are based on the number of possible IP addresses in each network within each class • Class A addresses: • First octet identifies the network and last three can be used to identify the host • The second, third and fourth octets are use to identigy cl ...
... • IP address identifies network and host • Classes are based on the number of possible IP addresses in each network within each class • Class A addresses: • First octet identifies the network and last three can be used to identify the host • The second, third and fourth octets are use to identigy cl ...
Learning with Bayesian Networks
... 2. As we’ve already seen using the Bayesian model permits us to update our beliefs based on new data. ...
... 2. As we’ve already seen using the Bayesian model permits us to update our beliefs based on new data. ...
ppt - Calit2
... Essentially, the OptIPuter is a "virtual metacomputer" in which the individual "processors" are widely distributed Linux PC clusters; the "backplane" is provided by Internet Protocol (IP) delivered over multiple dedicated 1-10 Gbps optical wavelengths; and, the "mass storage systems" are large distr ...
... Essentially, the OptIPuter is a "virtual metacomputer" in which the individual "processors" are widely distributed Linux PC clusters; the "backplane" is provided by Internet Protocol (IP) delivered over multiple dedicated 1-10 Gbps optical wavelengths; and, the "mass storage systems" are large distr ...
computer network - CCRI Faculty Web
... Most notebook computers and tablets come with a built-in wireless adapter. A USB wireless adapter can easily be connected to a desktop, smart TV, or game console that does not have one built in. ...
... Most notebook computers and tablets come with a built-in wireless adapter. A USB wireless adapter can easily be connected to a desktop, smart TV, or game console that does not have one built in. ...
Broadband Infraco
... Mandate Broadband Infraco’s legislative mandate is set out in the Broadband Infraco Act No. 33 of 2007 (the “Act”). The main objectives as set out in the Act are to expand the availability and affordability of access to electronic communications; Including but not limited to underdeveloped and un ...
... Mandate Broadband Infraco’s legislative mandate is set out in the Broadband Infraco Act No. 33 of 2007 (the “Act”). The main objectives as set out in the Act are to expand the availability and affordability of access to electronic communications; Including but not limited to underdeveloped and un ...
SLALoM : A Scalable Location Management Scheme for Large Ad
... Any reasonable scheme might work! ...
... Any reasonable scheme might work! ...
Juniper Networks Corporate PowerPoint Template
... • vRouter performs bridging (E-VPN) and routing (L3VPN) • vRouter performs networking services like Security Policies, NAT, Multicast, Mirroring, and Load Balancing • No need for Service Nodes or L2/L3 Gateways for Routing, Broadcast/Multicast, NAT • Routes are automatically leaked into the VRF base ...
... • vRouter performs bridging (E-VPN) and routing (L3VPN) • vRouter performs networking services like Security Policies, NAT, Multicast, Mirroring, and Load Balancing • No need for Service Nodes or L2/L3 Gateways for Routing, Broadcast/Multicast, NAT • Routes are automatically leaked into the VRF base ...
Anue 5200 Series Net Tool Optimizer
... the same packets more than once, they can run more efficiently. ■ Extended Burst Protection ...
... the same packets more than once, they can run more efficiently. ■ Extended Burst Protection ...
Application Layer Functionality and Protocols
... Compare and contrast client server networking with peer-to-peer networking and peer-to-peer applications ...
... Compare and contrast client server networking with peer-to-peer networking and peer-to-peer applications ...
Introduction - Department of Computer Engineering
... each end-end data stream divided into packets user A, B packets share network resources each packet uses full link bandwidth resources used as needed Bandwidth division into “pieces” Dedicated allocation Resource reservation ...
... each end-end data stream divided into packets user A, B packets share network resources each packet uses full link bandwidth resources used as needed Bandwidth division into “pieces” Dedicated allocation Resource reservation ...
1.6M PowerPoint Presentation
... industries like Lucent-Bell Labs, IBM and Thomson. Features: (a) A two-tier laboratory wireless emulator/field trial network test bed to perform cellular (3G & beyond) and WiFi-related experiments on nextgeneration protocols, middleware and applications. (b) Test bed is available both for remote a ...
... industries like Lucent-Bell Labs, IBM and Thomson. Features: (a) A two-tier laboratory wireless emulator/field trial network test bed to perform cellular (3G & beyond) and WiFi-related experiments on nextgeneration protocols, middleware and applications. (b) Test bed is available both for remote a ...
Airborne Networks TIM Why IPv6
... – Without the flow label the classifier must use transport next header value and port numbers • Less efficient (need to parse the option headers) • May be impossible (due to fragmentation or IPsec ESP) • Layer violation may hinder introduction of new transport protocols • IPv6 nodes not providing fl ...
... – Without the flow label the classifier must use transport next header value and port numbers • Less efficient (need to parse the option headers) • May be impossible (due to fragmentation or IPsec ESP) • Layer violation may hinder introduction of new transport protocols • IPv6 nodes not providing fl ...
Home Control Network
... well-defined functional APIs as a device service platform observing LonMark Interoperability Guideline abstraction and representation of application devices supporting zero-configuration compatible with LonTalk network management protocol ...
... well-defined functional APIs as a device service platform observing LonMark Interoperability Guideline abstraction and representation of application devices supporting zero-configuration compatible with LonTalk network management protocol ...