3rd Edition, Chapter 5
... Need G(x) that is unlikely divides T(x) + E(x) We know G(x) | T(x) we need G(x) that is unlikely to divide E(x) for common types of errors ...
... Need G(x) that is unlikely divides T(x) + E(x) We know G(x) | T(x) we need G(x) that is unlikely to divide E(x) for common types of errors ...
Chapter 1: Routing Concepts
... o Local route interfaces - Added to the routing table when an interface is configured. (displayed in IOS 15 or newer for IPv4 routes and all IOS releases for IPv6 routes.) o Directly connected interfaces - Added to the routing table when an interface is configured and active. o Static routes - Added ...
... o Local route interfaces - Added to the routing table when an interface is configured. (displayed in IOS 15 or newer for IPv4 routes and all IOS releases for IPv6 routes.) o Directly connected interfaces - Added to the routing table when an interface is configured and active. o Static routes - Added ...
TN-Lecture8
... • But, what is the difference between DXC and PSTN Digital Switch? • A PSTN Digital Switch: 1.Whether serving the local area, tandem, or toll, sets up a short-term virtual circuit where a connection may last just seconds, minutes, or several hours. 2.The bandwidth of the switched signals is in the r ...
... • But, what is the difference between DXC and PSTN Digital Switch? • A PSTN Digital Switch: 1.Whether serving the local area, tandem, or toll, sets up a short-term virtual circuit where a connection may last just seconds, minutes, or several hours. 2.The bandwidth of the switched signals is in the r ...
CS 291 Special Topics on Network Security
... The sender also needs to maintain this list (node join/leave) Internet solution Multicast address a class D IP address The group of receivers associated with a class D address is referred to as a multicast group How to manage this group? Internet Group Management Protocol A host inform ...
... The sender also needs to maintain this list (node join/leave) Internet solution Multicast address a class D IP address The group of receivers associated with a class D address is referred to as a multicast group How to manage this group? Internet Group Management Protocol A host inform ...
Chapter 8: Advanced Routing Protocols
... • Reliable Transport Protocol (RTP) – Because EIGRP is protocol-independent, it cannot use existing Transport layer protocols to carry its various packet types – Instead, Cisco developed an entirely new layer 4 protocol – RTP can actually provide both reliable and unreliable delivery – Routing table ...
... • Reliable Transport Protocol (RTP) – Because EIGRP is protocol-independent, it cannot use existing Transport layer protocols to carry its various packet types – Instead, Cisco developed an entirely new layer 4 protocol – RTP can actually provide both reliable and unreliable delivery – Routing table ...
TCP/IP Refresher
... Physical Layer: no address necessary Data Link Layer: address must be able to select any host on the network. ...
... Physical Layer: no address necessary Data Link Layer: address must be able to select any host on the network. ...
EE689 Lecture 12
... • Receivers need to receive on their own IP address and on the multicast address ...
... • Receivers need to receive on their own IP address and on the multicast address ...
The 5 MEF Attributes of Carrier Ethernet & Inter
... carrier-class SERVICE defined by five attributes that distinguish Carrier Ethernet from familiar LAN based Ethernet • It brings the compelling business benefit of the Ethernet cost model to achieve significant savings • Standardized Services ...
... carrier-class SERVICE defined by five attributes that distinguish Carrier Ethernet from familiar LAN based Ethernet • It brings the compelling business benefit of the Ethernet cost model to achieve significant savings • Standardized Services ...
Where is the collision domain?
... switch forwards a frame with broadcast address to all devices attached to the whole network (single broadcast domain) Can be used to combine Ethernet segments using different Ethernet technologies (10Base2 and 100BaseT and 10BaseT) because it has buffering capabilities Increases reliability (how?), ...
... switch forwards a frame with broadcast address to all devices attached to the whole network (single broadcast domain) Can be used to combine Ethernet segments using different Ethernet technologies (10Base2 and 100BaseT and 10BaseT) because it has buffering capabilities Increases reliability (how?), ...
Deployment of Private and Hybrid Clouds Using
... • Support for advance reservation of capacity through Haizea ...
... • Support for advance reservation of capacity through Haizea ...
OSI Physical Layer
... level errors. If the bit patterns being transmitted on the media do not create frequent transitions, this synchronization may be lost and individual bit error can occur. © 2007 Cisco Systems, Inc. All rights reserved. ...
... level errors. If the bit patterns being transmitted on the media do not create frequent transitions, this synchronization may be lost and individual bit error can occur. © 2007 Cisco Systems, Inc. All rights reserved. ...
Executive Summary
... Increased executive productivity and timely response. Cisco executives avoided the productivity loss they would have experienced by travelling to a Cisco Media Network studio. Reduced production costs. Using the Cisco intranet for the event eliminated the need to procure and provision satellite conn ...
... Increased executive productivity and timely response. Cisco executives avoided the productivity loss they would have experienced by travelling to a Cisco Media Network studio. Reduced production costs. Using the Cisco intranet for the event eliminated the need to procure and provision satellite conn ...
Transport Layer and Data Center TCP
... Slides used and adapted judiciously from Computer Networking, A Top-Down Approach ...
... Slides used and adapted judiciously from Computer Networking, A Top-Down Approach ...
Which three statements regarding IP multicast addresses are
... Best effort delivery may result in heavy drops on voice applications, which will cause jerky, missed speech patterns that can make the content unintelligible when the drop rate gets too high. Available network bandwidth is overutilized outside of the multicast routing zone because multiple streams o ...
... Best effort delivery may result in heavy drops on voice applications, which will cause jerky, missed speech patterns that can make the content unintelligible when the drop rate gets too high. Available network bandwidth is overutilized outside of the multicast routing zone because multiple streams o ...
How to configure an Anybus PROFIBUS
... Appendix 1 Connecting the bus cable with the D-SUB connector ..............................................................24 Appendix 2 Errors and diagnostics ..............................................................................................................25 The LED:s on the Anybus-S S ...
... Appendix 1 Connecting the bus cable with the D-SUB connector ..............................................................24 Appendix 2 Errors and diagnostics ..............................................................................................................25 The LED:s on the Anybus-S S ...
Interphase 4515 / 4525 / 4575 Manual
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15, Subpart B of the FCC Rules. This equipment generates, uses, and can radiate radio frequency energy. If not installed and used in accordance with the instructions, it may cause interf ...
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15, Subpart B of the FCC Rules. This equipment generates, uses, and can radiate radio frequency energy. If not installed and used in accordance with the instructions, it may cause interf ...
Chapter5-LANs - ECE Users Pages
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host ...
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host ...
ICTs: device to device communication
... http://www.open.edu/openlearn/science-maths-technology/computing-andict/information-and-communication-technologies/icts-device-devicecommunication/content-section-0. There you'll also be able to track your progress via your activity record, which you can use to demonstrate your learning. ...
... http://www.open.edu/openlearn/science-maths-technology/computing-andict/information-and-communication-technologies/icts-device-devicecommunication/content-section-0. There you'll also be able to track your progress via your activity record, which you can use to demonstrate your learning. ...
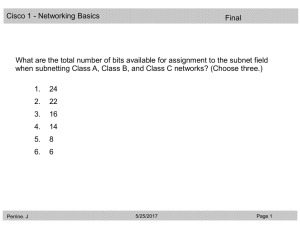
Q1 on FINAL
... Using the IP address 38.159.163.37 with a subnet mask 255.255.255.240, determine the subnetwork address. ...
... Using the IP address 38.159.163.37 with a subnet mask 255.255.255.240, determine the subnetwork address. ...
CloudCmp: Comparing Public Cloud Providers
... perceived performance of these services. For each service, we focus on a few important metrics, e.g., speed of CPU, memory, and disk I/O, scaling latency, storage service response time, time to reach consistency, network latency, and available bandwidth (§3.3). We leverage pre-existing tools specifi ...
... perceived performance of these services. For each service, we focus on a few important metrics, e.g., speed of CPU, memory, and disk I/O, scaling latency, storage service response time, time to reach consistency, network latency, and available bandwidth (§3.3). We leverage pre-existing tools specifi ...
CENT 305 Information Security
... Frequently placed in an unsecured network location, or a DMZ network Can be used to route all internal traffic for web pages via the intermediate proxy server Still widely used for e-commerce, but DMZ networks becoming more commonly used. Can be slower than other types of firewalls. Designed for one ...
... Frequently placed in an unsecured network location, or a DMZ network Can be used to route all internal traffic for web pages via the intermediate proxy server Still widely used for e-commerce, but DMZ networks becoming more commonly used. Can be slower than other types of firewalls. Designed for one ...
VMware Virtual SAN Network Design Guide
... infrastructure. Therefore, the Virtual SAN network must be carefully designed following general vSphere networking best practices in addition to its own. The following sections review general guidelines that should be followed when designing Virtual SAN network. These recommendations do not conflict ...
... infrastructure. Therefore, the Virtual SAN network must be carefully designed following general vSphere networking best practices in addition to its own. The following sections review general guidelines that should be followed when designing Virtual SAN network. These recommendations do not conflict ...
downloading
... d. Reload the system for the firmware to be installed 2. The first goal is to build a hierarchical switched network, so you will use one switch as your aggregation (or backbone) switch, and connect two access switches to it. Follow these instructions to configure each switch: a. The initial configur ...
... d. Reload the system for the firmware to be installed 2. The first goal is to build a hierarchical switched network, so you will use one switch as your aggregation (or backbone) switch, and connect two access switches to it. Follow these instructions to configure each switch: a. The initial configur ...