Chord: A Scalable P2P Lookup Service for Internet Applications
... and leave the system. Previous work on consistent hashing assumed that nodes were aware of most other nodes in the system, making it impractical to scale to large number of nodes. In contrast, each Chord node needs “routing” information about only a few other nodes. Because the routing table is dist ...
... and leave the system. Previous work on consistent hashing assumed that nodes were aware of most other nodes in the system, making it impractical to scale to large number of nodes. In contrast, each Chord node needs “routing” information about only a few other nodes. Because the routing table is dist ...
Q S G UICK
... Standalone High Availability (Proxy-ARP & Router Modes) This HA solution can support 2 to 16 IDP appliances in a load-sharing or hot standby configuration with no additional hardware. You can configure standalone HA solutions using the Appliance Configuration Manager (ACM) in Step 4. For maximum fai ...
... Standalone High Availability (Proxy-ARP & Router Modes) This HA solution can support 2 to 16 IDP appliances in a load-sharing or hot standby configuration with no additional hardware. You can configure standalone HA solutions using the Appliance Configuration Manager (ACM) in Step 4. For maximum fai ...
Chapter 7 - Lehigh CSE
... 7.2 streaming stored audio and video 7.3 making the best out of best effort service 7.4 protocols for real-time interactive applications ...
... 7.2 streaming stored audio and video 7.3 making the best out of best effort service 7.4 protocols for real-time interactive applications ...
J Series Ethernet Radio User Manual
... accompanying documentation and must not be used for any other purpose. All such information remains the property of Trio Datacom Pty Ltd and may not be reproduced, copied, stored on or transferred to any other media or used or distributed in any way save for the express purposes for which it is supp ...
... accompanying documentation and must not be used for any other purpose. All such information remains the property of Trio Datacom Pty Ltd and may not be reproduced, copied, stored on or transferred to any other media or used or distributed in any way save for the express purposes for which it is supp ...
Chapter6
... Switch Configuration Issues: Topology 2 • In Topology 2, the router-on-a-stick routing model has been chosen. However, the F0/5 interface on switch S1 is not configured as a trunk and subsequently left in the default VLAN for the port. •As a result, the router is not able to function correctly becau ...
... Switch Configuration Issues: Topology 2 • In Topology 2, the router-on-a-stick routing model has been chosen. However, the F0/5 interface on switch S1 is not configured as a trunk and subsequently left in the default VLAN for the port. •As a result, the router is not able to function correctly becau ...
OSPF
... the command ip ospf hello-interval. RouterDeadInterval - The period in seconds that the router will wait to hear a Hello from a neighbor before declaring the neighbor down. Cisco ...
... the command ip ospf hello-interval. RouterDeadInterval - The period in seconds that the router will wait to hear a Hello from a neighbor before declaring the neighbor down. Cisco ...
Chapter 7
... 7.2 streaming stored audio and video 7.3 making the best out of best effort service 7.4 protocols for real-time interactive applications ...
... 7.2 streaming stored audio and video 7.3 making the best out of best effort service 7.4 protocols for real-time interactive applications ...
Chord: A Scalable Peer-to-peer Lookup Service for Internet
... The Chord software takes the form of a library to be linked with the client and server applications that use it. The application interacts with Chord in two main ways. First, Chord provides a lookup(key) algorithm that yields the IP address of the node responsible for the key. Second, the Chord soft ...
... The Chord software takes the form of a library to be linked with the client and server applications that use it. The application interacts with Chord in two main ways. First, Chord provides a lookup(key) algorithm that yields the IP address of the node responsible for the key. Second, the Chord soft ...
Link Layer
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) Ethernet upstream HFC 802.11 wireless LAN ...
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) Ethernet upstream HFC 802.11 wireless LAN ...
TOSCA Simple Profile for Network Functions Virtualization
... any patent claims that would necessarily be infringed by implementations of this specification by a patent holder that is not willing to provide a license to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee that produced this specification. OASIS may inclu ...
... any patent claims that would necessarily be infringed by implementations of this specification by a patent holder that is not willing to provide a license to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee that produced this specification. OASIS may inclu ...
ECE544Lec6DR15
... broadcast-and-prune, unidirectional per-source trees, uses unicast routing table (Protocol Independent) ...
... broadcast-and-prune, unidirectional per-source trees, uses unicast routing table (Protocol Independent) ...
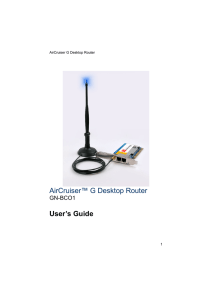
AirCruiser™ G Desktop Router User`s Guide
... unlike any other - there is a blue LED atop the tip which will flash at intervals – fast flashing indicates faster transmissions. It has a beefed up 3dBi gain compared with the 2dBi antennas that are bundled with most standard routers on the market and that translates into better wireless performanc ...
... unlike any other - there is a blue LED atop the tip which will flash at intervals – fast flashing indicates faster transmissions. It has a beefed up 3dBi gain compared with the 2dBi antennas that are bundled with most standard routers on the market and that translates into better wireless performanc ...
The Pulse Protocol: Energy Efficient Infrastructure Access
... Not designed for multi-rate networks A small number of long slow hops provide the minimum hop path These slow transmissions occupy the medium for long times, blocking adjacent ...
... Not designed for multi-rate networks A small number of long slow hops provide the minimum hop path These slow transmissions occupy the medium for long times, blocking adjacent ...
ECE544Lec6DR11
... broadcast-and-prune, unidirectional per-source trees, uses unicast routing table (Protocol Independent) ...
... broadcast-and-prune, unidirectional per-source trees, uses unicast routing table (Protocol Independent) ...
slides - University of California, Berkeley
... sent to unicast address A and broadcast address B to join group G, NIC also listens for packets sent to multicast address G (NIC limits number of groups joined) implemented in hardware, so efficient packet is flooded on all LAN segments, like broadcast can waste bandwidth, but LANs should not be ver ...
... sent to unicast address A and broadcast address B to join group G, NIC also listens for packets sent to multicast address G (NIC limits number of groups joined) implemented in hardware, so efficient packet is flooded on all LAN segments, like broadcast can waste bandwidth, but LANs should not be ver ...
Chap10_Peer-to-Peer_Team4
... Next generation from Napster - true Peer To Peer (P2P) Can handle large files e.g WAV, DVD, FLAC (e.g 1CD = ...
... Next generation from Napster - true Peer To Peer (P2P) Can handle large files e.g WAV, DVD, FLAC (e.g 1CD = ...
MinBD: Minimally-Buffered Deflection Routing for Energy
... yields simpler and more energy-efficient NoC designs: e.g., CHIPPER [12] reduces average network power by 54.9% in a 64-node system compared to a conventional buffered router. Unfortunately, at high network load, deflection routing reduces performance and efficiency. This is because deflections occu ...
... yields simpler and more energy-efficient NoC designs: e.g., CHIPPER [12] reduces average network power by 54.9% in a 64-node system compared to a conventional buffered router. Unfortunately, at high network load, deflection routing reduces performance and efficiency. This is because deflections occu ...
Gnutella - Montclair State University
... Security Risks of Gnutella IP Harvesting • Hackers are always in search for people’s IP addresses. • They continuously search and scan the internet in order to see people’s IP ...
... Security Risks of Gnutella IP Harvesting • Hackers are always in search for people’s IP addresses. • They continuously search and scan the internet in order to see people’s IP ...
English
... Automatically sets the TV to the most suitable energy-saving mode. The concerned items and their current settings are displayed. Select Set to Eco to set them to the energy-saving settings at once. 1. Display the menu with MENU. 2. Select Setup > Eco Navigation with 3. Select Set to Eco with ...
... Automatically sets the TV to the most suitable energy-saving mode. The concerned items and their current settings are displayed. Select Set to Eco to set them to the energy-saving settings at once. 1. Display the menu with MENU. 2. Select Setup > Eco Navigation with 3. Select Set to Eco with ...
MPLS - 中正大學
... Intermediate LSRs make their forwarding decision by label switching on a level m label Ends (LSP Egress) when forwarding decision is made by label switching on a level m-k label (k>0) or when a forwarding decision is made by nonMPLS forwarding procedures The label stack may be popped at the penultim ...
... Intermediate LSRs make their forwarding decision by label switching on a level m label Ends (LSP Egress) when forwarding decision is made by label switching on a level m-k label (k>0) or when a forwarding decision is made by nonMPLS forwarding procedures The label stack may be popped at the penultim ...
Chapter 14
... – Users must be trained to update their antivirus software daily or, at a bare minimum, weekly – Users also must learn how viruses are transmitted between computers – Teach users to scan removable devices with the virus scanning software before using them ...
... – Users must be trained to update their antivirus software daily or, at a bare minimum, weekly – Users also must learn how viruses are transmitted between computers – Teach users to scan removable devices with the virus scanning software before using them ...
For Internal Use Only - Guillevin Industrial Automation Group
... For RSTP ring with 32 switches, Reconfiguration Time = 90 ms detect failure +(40 ms data propagation x No. Switches in longest ...
... For RSTP ring with 32 switches, Reconfiguration Time = 90 ms detect failure +(40 ms data propagation x No. Switches in longest ...
Document
... Recall that in the centralized database, there could be numerous objects. Cost of full scan is prohibitive and update is expensive. Specially designed databases are needed for that purpose. ...
... Recall that in the centralized database, there could be numerous objects. Cost of full scan is prohibitive and update is expensive. Specially designed databases are needed for that purpose. ...
3rd Edition, Chapter 5
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...