Document
... •The time delayed approach includes two basic types Contents of networks: Sequences •Implicit Representation of Time: We combine a memory structure in the input layer of the network Time Delayed I with a static network model Time Delayed II •Explicit Representation of Time: We explicitly Recurrent I ...
... •The time delayed approach includes two basic types Contents of networks: Sequences •Implicit Representation of Time: We combine a memory structure in the input layer of the network Time Delayed I with a static network model Time Delayed II •Explicit Representation of Time: We explicitly Recurrent I ...
Chapter 5
... (bridges and switches too) communication channels that connect adjacent nodes along communication path are links ...
... (bridges and switches too) communication channels that connect adjacent nodes along communication path are links ...
IPv4 Multicast Security: A Network Perspective
... have layer 2 switches between hosts and their routers. Since IGMP is a layer 3 protocol these switches are not aware of the “join”, “leave” and “query” messages being exchanged between the hosts and routers. These switches will be unaware that a host attached to one of its ports desires to receive p ...
... have layer 2 switches between hosts and their routers. Since IGMP is a layer 3 protocol these switches are not aware of the “join”, “leave” and “query” messages being exchanged between the hosts and routers. These switches will be unaware that a host attached to one of its ports desires to receive p ...
Exam : 070-291 Title : Implementing, Managing, and
... B. Change the subnet mask of Certkiller 6 to 255.255.0.0. C. Change the IP address of Certkiller 6 to 10.10.10.3. D. Change the IP address of Certkiller 6 to 10.10.11.3. Answer: B Explanation: Large networks are subdivided to create smaller subnetworks to reduce overall network traffic by keeping lo ...
... B. Change the subnet mask of Certkiller 6 to 255.255.0.0. C. Change the IP address of Certkiller 6 to 10.10.10.3. D. Change the IP address of Certkiller 6 to 10.10.11.3. Answer: B Explanation: Large networks are subdivided to create smaller subnetworks to reduce overall network traffic by keeping lo ...
The Allied Telesis x610 Series is the high performing and... solution for today’s networks, providing an extensive range of
... which delivers the added benefit of reducing costs. Secure Multiple customers can have their own secure virtual network within the same physical infrastructure, as the x610 Series switches are able to divide a single router into multiple independent virtual routing domains. Layer 3 network virtualiz ...
... which delivers the added benefit of reducing costs. Secure Multiple customers can have their own secure virtual network within the same physical infrastructure, as the x610 Series switches are able to divide a single router into multiple independent virtual routing domains. Layer 3 network virtualiz ...
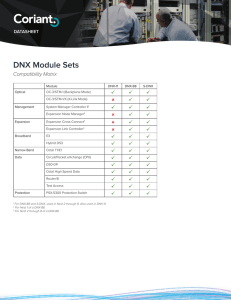
DNX Module Sets
... DNX mid-plane to control modules within the nest and provide several methods for communicating with and controlling the DNX system. The intuitive VT100 terminal interface offers direct or remote connectivity. Remote connections to the System Manager are made using the internal modem, Telnet, or SSH. ...
... DNX mid-plane to control modules within the nest and provide several methods for communicating with and controlling the DNX system. The intuitive VT100 terminal interface offers direct or remote connectivity. Remote connections to the System Manager are made using the internal modem, Telnet, or SSH. ...
DATA-LINK-LAYER - e
... (bridges and switches too) communication channels that connect adjacent nodes along communication path are links ...
... (bridges and switches too) communication channels that connect adjacent nodes along communication path are links ...
data-link layer
... (bridges and switches too) communication channels that connect adjacent nodes along communication path are links ...
... (bridges and switches too) communication channels that connect adjacent nodes along communication path are links ...
- Mitra.ac.in
... (bridges and switches too) communication channels that connect adjacent nodes along communication path are links ...
... (bridges and switches too) communication channels that connect adjacent nodes along communication path are links ...
Chapter 4
... • The VC network came about because of its similarity to telephone networks • But the Internet was connecting complex computers, so the datagram network was created because the computers could handle more complex operations than the routers (recall our IMP friends from Chapter 1) – This also makes i ...
... • The VC network came about because of its similarity to telephone networks • But the Internet was connecting complex computers, so the datagram network was created because the computers could handle more complex operations than the routers (recall our IMP friends from Chapter 1) – This also makes i ...
Seminar Steganography
... Proof of ownership (better watermarking of digital media) Protection of property: physical and intellectual. With advances in Steganography, it is possible that it could be used as a secure transmission medium. ...
... Proof of ownership (better watermarking of digital media) Protection of property: physical and intellectual. With advances in Steganography, it is possible that it could be used as a secure transmission medium. ...
TDC 563-98-301/302, Spring 2002 2-14 TDC 563-98
... the router interfaces inside a particular area. These links are only flooded inside the router's area. •Network Links (NL) are generated by a DR (Designated Router) of a particular segment; these are an indication of the routers connected to that segment. •Summary Links (SL) are the inter-area links ...
... the router interfaces inside a particular area. These links are only flooded inside the router's area. •Network Links (NL) are generated by a DR (Designated Router) of a particular segment; these are an indication of the routers connected to that segment. •Summary Links (SL) are the inter-area links ...
Basic Ethernet/IP Lab
... Important User Information This documentation, whether, illustrative, printed, “online” or electronic (hereinafter “Documentation”) is intended for use only as a learning aid when using Rockwell Automation approved demonstration hardware, software and firmware. The Documentation should only be used ...
... Important User Information This documentation, whether, illustrative, printed, “online” or electronic (hereinafter “Documentation”) is intended for use only as a learning aid when using Rockwell Automation approved demonstration hardware, software and firmware. The Documentation should only be used ...
PXG3.L, PXG3.M BACnet Router
... Support for BBMD (BACnet Broadcast Management Device) Support for Foreign Device Configuration via Xworks Plus or Web browser Access to network statistics via Web browser Firmware update via Ethernet and USB Device LED indication for Ethernet link and activity LED indication for BACnet/LonTalk and B ...
... Support for BBMD (BACnet Broadcast Management Device) Support for Foreign Device Configuration via Xworks Plus or Web browser Access to network statistics via Web browser Firmware update via Ethernet and USB Device LED indication for Ethernet link and activity LED indication for BACnet/LonTalk and B ...
PDF
... Intel disclaims all express and implied warranties, including without limitation, the implied warranties of merchantability, fitness for a particular purpose, and noninfringement, as well as any warranty arising from course of performance, course of dealing, or usage in trade. This document contains ...
... Intel disclaims all express and implied warranties, including without limitation, the implied warranties of merchantability, fitness for a particular purpose, and noninfringement, as well as any warranty arising from course of performance, course of dealing, or usage in trade. This document contains ...
Ipv4-mapped Ipv6 Address Dest. 1.2.3.4 Dest.
... • IPv6 Mobility is based on core features of IPv6 – The base IPv6 was designed to support Mobility – Mobility is not an “Add-on” features • All IPv6 Networks are IPv6-Mobile Ready • All IPv6 nodes are IPv6-Mobile Ready • All IPv6 LANs / Subnets are IPv6 Mobile Ready ...
... • IPv6 Mobility is based on core features of IPv6 – The base IPv6 was designed to support Mobility – Mobility is not an “Add-on” features • All IPv6 Networks are IPv6-Mobile Ready • All IPv6 nodes are IPv6-Mobile Ready • All IPv6 LANs / Subnets are IPv6 Mobile Ready ...
Using Your Gateway WGR
... Now that all the hardware connections have been made, you must configure the access point/router to operate on your network and to connect to the Internet through an ISP. Important ...
... Now that all the hardware connections have been made, you must configure the access point/router to operate on your network and to connect to the Internet through an ISP. Important ...
Tema 1: Tecnologías de red. - GRC
... R&D labs of equipment vendors and ISPs International, but 2/3 United States meetings every four months about 300 companies participating in meetings but Cisco, Ericsson, Lucent, Nokia, etc. send large delegations ...
... R&D labs of equipment vendors and ISPs International, but 2/3 United States meetings every four months about 300 companies participating in meetings but Cisco, Ericsson, Lucent, Nokia, etc. send large delegations ...
tcp/ip routing protocols, rip., etc
... routing domain can be used to allow more than one RIP domain on a campus; more than one routed on a system route tag - AS number, communicate boundary info (not used by RIP) subnet mask - for CIDR, route == (ip, net mask) next hop, ip address for VIA part of route (as opposed to getting it f ...
... routing domain can be used to allow more than one RIP domain on a campus; more than one routed on a system route tag - AS number, communicate boundary info (not used by RIP) subnet mask - for CIDR, route == (ip, net mask) next hop, ip address for VIA part of route (as opposed to getting it f ...
Game Theory application to Networking Research: Part IV.
... • These overlays tend to fully utilize available resource. • So, is there any anarchy? • How do overlay networks co-exist with each other? • What is the implication of interactions? • How to regulate selfish overlay networks via mechanism design? • Can ISPs take advantage of this? ...
... • These overlays tend to fully utilize available resource. • So, is there any anarchy? • How do overlay networks co-exist with each other? • What is the implication of interactions? • How to regulate selfish overlay networks via mechanism design? • Can ISPs take advantage of this? ...
Ubee DDW365 Advanced Wireless Gateway
... Use only the power cable supplied with the device. Do not attach the power supply cable to building surfaces or floorings. Rest the power cable freely without any obstacles. Do not place heavy items on top of the power cable. Do not abuse, step, or walk on the cable. Do not place heavy objects o ...
... Use only the power cable supplied with the device. Do not attach the power supply cable to building surfaces or floorings. Rest the power cable freely without any obstacles. Do not place heavy items on top of the power cable. Do not abuse, step, or walk on the cable. Do not place heavy objects o ...