SEMESTER 1 Chapter 5
... Maintaining up-to-date routing information Choosing the best path to destination networks Ability to find a new best path if the current path is no longer available Data structures - Some routing protocols use tables and/or databases for its operations. This information is kept in RAM, Algorithm- An ...
... Maintaining up-to-date routing information Choosing the best path to destination networks Ability to find a new best path if the current path is no longer available Data structures - Some routing protocols use tables and/or databases for its operations. This information is kept in RAM, Algorithm- An ...
PPT - Pages
... – Some services not feasible • Latency or bandwidth guarantees • Need special support ...
... – Some services not feasible • Latency or bandwidth guarantees • Need special support ...
presentation source
... • Sockets (obviously) have special needs: – establishing a connection – specifying communication endpoint addresses ...
... • Sockets (obviously) have special needs: – establishing a connection – specifying communication endpoint addresses ...
Multi-layer Traffic Engineering in Data-centric Optical
... overprovisioning, some other issues are of importance when designing a proper MTE strategy, some of these conflict with each other, so a trade-off has to be made. As reconfigurations of the logical topology are performed dynamically (i.e., while the network is in full service), each reconfiguration ...
... overprovisioning, some other issues are of importance when designing a proper MTE strategy, some of these conflict with each other, so a trade-off has to be made. As reconfigurations of the logical topology are performed dynamically (i.e., while the network is in full service), each reconfiguration ...
Introduction
... Advantages of Directories Make administration easier. – Change data only once: people, accounts, hosts. ...
... Advantages of Directories Make administration easier. – Change data only once: people, accounts, hosts. ...
Information Networks
... system and applications on a distributed computing system in a network. Middleware services provide a more functional set of application programming interfaces to allow an application to: 1. Locate transparently across the network, thus providing interaction with another service or application 2. Be ...
... system and applications on a distributed computing system in a network. Middleware services provide a more functional set of application programming interfaces to allow an application to: 1. Locate transparently across the network, thus providing interaction with another service or application 2. Be ...
Networking Basics - Undergraduate Research in Consumer
... used by many users, often concurrently ...
... used by many users, often concurrently ...
AbuNawaf
... Social capacity is people's ability to work together to organize public relationships, rather than give responsibility for those relationships wholly to state actors or the flux of market exchange. Ref3: Evaluating Capacity Building and Participatory Development in Community Timber Operations of the ...
... Social capacity is people's ability to work together to organize public relationships, rather than give responsibility for those relationships wholly to state actors or the flux of market exchange. Ref3: Evaluating Capacity Building and Participatory Development in Community Timber Operations of the ...
AW36294299
... In the TCP protocol, packets that are sent to a destination are buffered within the TCP stack and when the stack is full, the packets get sent on to the receiving system. However, the sender can request the receiving system to unload the contents of the buffer before the buffer becomes full by sendi ...
... In the TCP protocol, packets that are sent to a destination are buffered within the TCP stack and when the stack is full, the packets get sent on to the receiving system. However, the sender can request the receiving system to unload the contents of the buffer before the buffer becomes full by sendi ...
Transmission Control Protocol (TCP)
... Hence, IP addresses refer to network connections and not hosts Why will hosts have multiple network connections? ...
... Hence, IP addresses refer to network connections and not hosts Why will hosts have multiple network connections? ...
Lecture 5 - Lyle School of Engineering
... Messages are constant length - depends on number of links per router, but does not depend on network size Routing updates are sent only for significant changes OSPF allows hierarchical routing - network is divided into areas, which reduces routing traffic ...
... Messages are constant length - depends on number of links per router, but does not depend on network size Routing updates are sent only for significant changes OSPF allows hierarchical routing - network is divided into areas, which reduces routing traffic ...
Ethernet basics
... • There is only so much available bandwidth, in some instances it can be dynamic • An overabundance of data on the network, not only affects the infrastructure equipment tasked with its distribution, but also the end devices or nodes meant to receive it. • Once a node has been overwhelmed, it needs ...
... • There is only so much available bandwidth, in some instances it can be dynamic • An overabundance of data on the network, not only affects the infrastructure equipment tasked with its distribution, but also the end devices or nodes meant to receive it. • Once a node has been overwhelmed, it needs ...
www2004.org
... which block is to be fetched from which neighbor. A simple scheduling algorithm is given as below, where the demanded blocks is transferred from the neighbors in a round-robin fashion. This enables balanced data delivery among the neighbors. Moreover, during streaming, a node should also notify all ...
... which block is to be fetched from which neighbor. A simple scheduling algorithm is given as below, where the demanded blocks is transferred from the neighbors in a round-robin fashion. This enables balanced data delivery among the neighbors. Moreover, during streaming, a node should also notify all ...
Routing Protocol vs. Routed Protocol
... – This should only occur during initial startup of routers, but can also be an issue on unstable networks. ...
... – This should only occur during initial startup of routers, but can also be an issue on unstable networks. ...
IOSR Journal of Electronics and Communication Engineering (IOSRJECE)
... Ad-hoc On-demand distance vector (AODV) [12, 13] is another variant of classical distance vector routing algorithm, a confluence of both DSDV [9] and DSR [14]. It shares DSR‟s on-demand characteristics hence discovers routes whenever it is needed via a similar route discovery process. However, AODV ...
... Ad-hoc On-demand distance vector (AODV) [12, 13] is another variant of classical distance vector routing algorithm, a confluence of both DSDV [9] and DSR [14]. It shares DSR‟s on-demand characteristics hence discovers routes whenever it is needed via a similar route discovery process. However, AODV ...
Berkeley NOW - Computer Science Division
... Wealth of Research Challenges • Large numbers of highly constrained (energy & capability), connected devices ...
... Wealth of Research Challenges • Large numbers of highly constrained (energy & capability), connected devices ...
ANOMALY NETWORK INTRUSION DETECTION SYSTEM BASED
... to have lower detection performance than SOM. The second category is recurrent and adaptive neural-net-based IDSs, this category includes systems built on recurrent and adaptive neural nets such as ELMAN and CMAC. By getting feedback from its output or its protected system, the neural net preserves ...
... to have lower detection performance than SOM. The second category is recurrent and adaptive neural-net-based IDSs, this category includes systems built on recurrent and adaptive neural nets such as ELMAN and CMAC. By getting feedback from its output or its protected system, the neural net preserves ...
International Telecommunication Union
... Portals—Connections between two cooperating sets of Systems (two Portals) are supported, in contrast to Link Aggregation, so that connectivity between two networks can be maintained despite the failure of an entire System (and its connected links) belonging to a Portal. Compatibility—A multi-System ...
... Portals—Connections between two cooperating sets of Systems (two Portals) are supported, in contrast to Link Aggregation, so that connectivity between two networks can be maintained despite the failure of an entire System (and its connected links) belonging to a Portal. Compatibility—A multi-System ...
Document
... – At the PBX, use a butt set to isolate crosstalk to determine whether the problem is within or outside the building • Securing connections with a punchdown tool – Poorly closed connections or improperly set lines can cause line noise • Checking for line noise – Use a digital multimeter to measure f ...
... – At the PBX, use a butt set to isolate crosstalk to determine whether the problem is within or outside the building • Securing connections with a punchdown tool – Poorly closed connections or improperly set lines can cause line noise • Checking for line noise – Use a digital multimeter to measure f ...
(775) 720-5071 [email protected] HomePNA RELEASES
... SAN RAMON, Calif. – Nov. 7, 2006 – HomePNA announced today the release of HomePNA 3.1, a home networking specification that increases data rates over existing home wiring to 320 Megabits per second. Building on the industry-leading HomePNA 3.0 specification, it enables service providers to simultane ...
... SAN RAMON, Calif. – Nov. 7, 2006 – HomePNA announced today the release of HomePNA 3.1, a home networking specification that increases data rates over existing home wiring to 320 Megabits per second. Building on the industry-leading HomePNA 3.0 specification, it enables service providers to simultane ...
Dell SonicWALL Application Risk Management Report (SWARM)
... Microsoft Terminal Services also known as Remote Desktop Services extends distributed computing by allowing PCs to operate in a server-based computing environment. Remote Desktop Services are crossplatform functional. MySQL Server MySQL is a relational database management system that runs as a serve ...
... Microsoft Terminal Services also known as Remote Desktop Services extends distributed computing by allowing PCs to operate in a server-based computing environment. Remote Desktop Services are crossplatform functional. MySQL Server MySQL is a relational database management system that runs as a serve ...
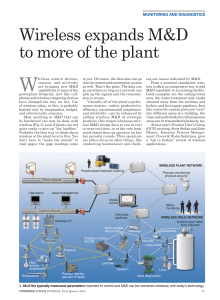
Wireless Expands M D to More of the Plant
... into the control and automation system as well. That’s the point. The data can go anywhere as long as a network can pick up the signals and the transmission is secure. Virtually all of the plant’s performance metrics—safety, productivity, efficiency, environmental compliance, and reliability—can be ...
... into the control and automation system as well. That’s the point. The data can go anywhere as long as a network can pick up the signals and the transmission is secure. Virtually all of the plant’s performance metrics—safety, productivity, efficiency, environmental compliance, and reliability—can be ...
lan
... • No AP (i.e., base station) • wireless hosts communicate with each other – to get packet from wireless host A to B may need to route through wireless hosts X,Y,Z • Applications: – “laptop” meeting in conference room, car – interconnection of “personal” devices – battlefield • IETF MANET (Mobile Ad ...
... • No AP (i.e., base station) • wireless hosts communicate with each other – to get packet from wireless host A to B may need to route through wireless hosts X,Y,Z • Applications: – “laptop” meeting in conference room, car – interconnection of “personal” devices – battlefield • IETF MANET (Mobile Ad ...