Proceedings of USITS ’03: 4th USENIX Symposium on Internet Technologies and Systems
... long-distance link is successful. However as noted above in Section 3.1, some of these connections in fact are rejected because the intended target of the link is \saturated" with 2k incoming links. We account for this implementation detail by noting that provided k = O(1), the fraction of such reje ...
... long-distance link is successful. However as noted above in Section 3.1, some of these connections in fact are rejected because the intended target of the link is \saturated" with 2k incoming links. We account for this implementation detail by noting that provided k = O(1), the fraction of such reje ...
ex2-4-o-can
... • Router 1 sends an update to Router 2 that Network A is available and Router 2 updates its routing table with the information. • Router 2 recognizes a change in topology. • This would normally trigger an update to neighbouring routers and cause a routing loop. • With split horizon enabled, Router 2 ...
... • Router 1 sends an update to Router 2 that Network A is available and Router 2 updates its routing table with the information. • Router 2 recognizes a change in topology. • This would normally trigger an update to neighbouring routers and cause a routing loop. • With split horizon enabled, Router 2 ...
Congestion
... more work (retrans) for given “goodput” unneeded retransmissions: link carries multiple copies of pkt ...
... more work (retrans) for given “goodput” unneeded retransmissions: link carries multiple copies of pkt ...
atm98-786
... Don’t have to provision default routed path to carry a lot of traffic – more of the traffic can be carried on short-cut as needed ...
... Don’t have to provision default routed path to carry a lot of traffic – more of the traffic can be carried on short-cut as needed ...
AG31238244
... forwards data for the other nodes in the networks that may not be within wireless transmission range. Routing in the mobile ad hoc networks faces challenges due to mobility of the nodes a large number of nodes, and communication between nodes resource constrained like energy and bandwidth [1][9]. Th ...
... forwards data for the other nodes in the networks that may not be within wireless transmission range. Routing in the mobile ad hoc networks faces challenges due to mobility of the nodes a large number of nodes, and communication between nodes resource constrained like energy and bandwidth [1][9]. Th ...
SWITCH Ch 1
... individual line modules of Catalyst switches to hardware-switch packets in a distributed manner. ...
... individual line modules of Catalyst switches to hardware-switch packets in a distributed manner. ...
Peer-to-Peer Overlay Broker Networks in an Event
... (3) Single Bootstrap Broker. Ideally, when a new event broker is added to the system, it should only be necessary to provide a single address of an already existing broker. The new event broker will then use this broker to bootstrap its set of neighbouring brokers according to the other requirements ...
... (3) Single Bootstrap Broker. Ideally, when a new event broker is added to the system, it should only be necessary to provide a single address of an already existing broker. The new event broker will then use this broker to bootstrap its set of neighbouring brokers according to the other requirements ...
The Internet and Its Uses
... (MPLS) protocol. MPLS is increasingly being deployed by service providers to provide an economical solution to carry circuit-switched as well as packet-switched network traffic. It can operate over any existing infrastructure, such as IP, Frame Relay, ATM, or Ethernet. It sits between Layer 2 and La ...
... (MPLS) protocol. MPLS is increasingly being deployed by service providers to provide an economical solution to carry circuit-switched as well as packet-switched network traffic. It can operate over any existing infrastructure, such as IP, Frame Relay, ATM, or Ethernet. It sits between Layer 2 and La ...
Avaya Open Networking Adapter
... many of which require at least some degree of mobility. These end-point devices may themselves necessitate and include security considerations, such as authentication and encryption. However, in the context of certain environments, the broader network needs to be protected from potential threats ema ...
... many of which require at least some degree of mobility. These end-point devices may themselves necessitate and include security considerations, such as authentication and encryption. However, in the context of certain environments, the broader network needs to be protected from potential threats ema ...
SWITCH Ch 1 - House of Technology
... individual line modules of Catalyst switches to hardware-switch packets in a distributed manner. ...
... individual line modules of Catalyst switches to hardware-switch packets in a distributed manner. ...
Energy Saving in Automotive E/E Architectures
... White Paper: Energy Saving in Automotive E/E Architectures, December 2012 ...
... White Paper: Energy Saving in Automotive E/E Architectures, December 2012 ...
ex2-5-o-can
... Advantages of Auto-Summarization • Smaller routing updates are sent and received, ...
... Advantages of Auto-Summarization • Smaller routing updates are sent and received, ...
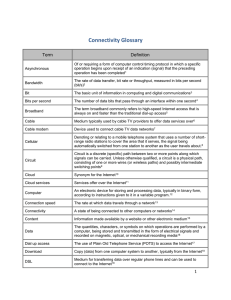
Connectivity Glossary
... The term broadband commonly refers to high-speed Internet access that is always on and faster than the traditional dial-up access5 ...
... The term broadband commonly refers to high-speed Internet access that is always on and faster than the traditional dial-up access5 ...
The Hidden Cost of Hidden Terminals
... (DCF) is a medium access control (MAC) layer random access protocol based on carrier sense multiple access with collision avoidance (CSMA/CA). Due to the apparent “fair” nature of the CSMA/CA random access scheme, it is widely assumed that long term channel access fairness is guaranteed in 802.11 WL ...
... (DCF) is a medium access control (MAC) layer random access protocol based on carrier sense multiple access with collision avoidance (CSMA/CA). Due to the apparent “fair” nature of the CSMA/CA random access scheme, it is widely assumed that long term channel access fairness is guaranteed in 802.11 WL ...
- Muhazam
... incoming packet, instead of all of them • Selection can be random or round robin • Can select outgoing path based on probability calculation • No network info needed • Route is typically not least cost nor minimum hop CO1 ...
... incoming packet, instead of all of them • Selection can be random or round robin • Can select outgoing path based on probability calculation • No network info needed • Route is typically not least cost nor minimum hop CO1 ...
Troubleshooting Scenario Two
... – “Our Web server is sluggish!” • Connect from another location • If connection is also slow, problem with server • Check server logs for changes • Run Performance Monitor and compare new logs with previously established baseline logs • If connection from other location OK, run TRACERT command from ...
... – “Our Web server is sluggish!” • Connect from another location • If connection is also slow, problem with server • Check server logs for changes • Run Performance Monitor and compare new logs with previously established baseline logs • If connection from other location OK, run TRACERT command from ...
south africa`s alluvial diamond deposits
... Small miners have to multi-task and manage all aspects of their businesses alone Require reliable modern geological information ...
... Small miners have to multi-task and manage all aspects of their businesses alone Require reliable modern geological information ...
CHAPTER TWO NEURAL NETWORKS 2.1 Overview
... In fact, the neurons are five or six times slower than current of silicon gates. The modern computer easily outperforms the human in reprogrammable, repetitive computations quickly than human do, but in real applications such as understanding, perception, speech, which human being almost effortlessl ...
... In fact, the neurons are five or six times slower than current of silicon gates. The modern computer easily outperforms the human in reprogrammable, repetitive computations quickly than human do, but in real applications such as understanding, perception, speech, which human being almost effortlessl ...
Authentication
... “Network name services shall be configured to provide Internet users with generic names to accessible internal systems while serving meaning full names to internal, organizational users.” “Network addresses shall be predefined for every system and network device and may be preloaded or resolved when ...
... “Network name services shall be configured to provide Internet users with generic names to accessible internal systems while serving meaning full names to internal, organizational users.” “Network addresses shall be predefined for every system and network device and may be preloaded or resolved when ...
IOSR Journal of Computer Science (IOSR-JCE) e-ISSN: 2278-0661, p-ISSN: 2278-8727 PP 15-19 www.iosrjournals.org
... Comparison of the WebSocket protocol with the traditional method like Polling and HTTP long Polling shows the benefits it offers in terms of latency and network utilization. With polling, the browser sends HTTP requests at regular intervals and immediately receives a response. This technique was the ...
... Comparison of the WebSocket protocol with the traditional method like Polling and HTTP long Polling shows the benefits it offers in terms of latency and network utilization. With polling, the browser sends HTTP requests at regular intervals and immediately receives a response. This technique was the ...
ppt - Applied Crypto Group at Stanford University
... If packets are lost, assume congestion Reduce transmission rate by half, repeat If loss stops, increase rate very slowly Design assumes routers blindly obey this policy ...
... If packets are lost, assume congestion Reduce transmission rate by half, repeat If loss stops, increase rate very slowly Design assumes routers blindly obey this policy ...
IM7200-L Cellular Addendum
... Watchdog “Keep Alive” This watchdog can be used to force a clean restart of the cellular modem and its services to work around any carrier issues (e.g. to prevent your carrier from disconnecting the cellular connection during idle periods). This service periodically pings a nominated IP address. Eac ...
... Watchdog “Keep Alive” This watchdog can be used to force a clean restart of the cellular modem and its services to work around any carrier issues (e.g. to prevent your carrier from disconnecting the cellular connection during idle periods). This service periodically pings a nominated IP address. Eac ...
SEMESTER 1 Chapter 5
... Maintaining up-to-date routing information Choosing the best path to destination networks Ability to find a new best path if the current path is no longer available Data structures - Some routing protocols use tables and/or databases for its operations. This information is kept in RAM, Algorithm- An ...
... Maintaining up-to-date routing information Choosing the best path to destination networks Ability to find a new best path if the current path is no longer available Data structures - Some routing protocols use tables and/or databases for its operations. This information is kept in RAM, Algorithm- An ...